Documents
March 2013 Watchlisting Guidance
July 23, 2014

OFFICIAL USE ONLWSENSITWE SECURITY INFORMAITON
March 2013
WATCHLISTING
GUIDANCE
UNCLASSIFIEDHFOR OFFICIAL USE ONLWSENSITIVE INFORMAITON
WARNING: This reccrd ccntains Sensitive Security that is under 49 CFR
parts '15 and 1520. Ne part ct this reccrd be discicsed tc without a ?need tc
knew", as defined in 4Q C-FH parts 15 and 1520, except with the written permissicn cf the
Administratcr cf the Security Administraticn er the Secretary' ct
Unauthcriaed release may result in civil penalty cr cther acticn. LLB. gcuernment agencies,
pubiic is gcverned by 5 USE. 552 and 49 GFH parts 15 and 152D.
OFFICIAL USE ONLWSENSITWE SECURITY INFORMAITON
March 2013
WATCHLISTING
GUIDANCE
UNCLASSIFIEDHFOR OFFICIAL USE ONLWSENSITIVE INFORMAITON
WARNING: This reccrd ccntains Sensitive Security that is under 49 CFR
parts '15 and 1520. Ne part ct this reccrd be discicsed tc without a ?need tc
knew", as defined in 4Q C-FH parts 15 and 1520, except with the written permissicn cf the
Administratcr cf the Security Administraticn er the Secretary' ct
Unauthcriaed release may result in civil penalty cr cther acticn. LLB. gcuernment agencies,
pubiic is gcverned by 5 USE. 552 and 49 GFH parts 15 and 152D.

OFFICIAL USE SECURITY INFORMATION
2013 WATCHLISTIN GUIDANCE
TABLE OF CONTENTS
CHAPTER I: WATCHLISTING PROCESS AND PROCEDURES ..5
I. INTRODUCTION ..5
II. WATCHLISTING AUTHORITIES ..6
CONSTITUTIONALLY PROTECTED ACTIVITIES .. I0
IV. WATCHLISTING POLICIES .. I
V. WATCHLISTING STANDARD: IDENTIFYING AND SUBSTANTIVE
DEROGATORY CRITERIA .. I2
VI. WATCHLISTING PROCESS OVERVIEW .. I3
VII. ROLES AND RESPONSIBILITES FOR TIIE WATCHLISTING AND SCREENING
COMMUNITY .. I6
QUALITY CONTROL MEASURES .. I 7
IX. NOMINATION PROCEDURES ..20
X. PROCEDURES TO REMOVE AN INDIVIDUAL FROM THE WATCI-IIJST
XI. REDRESS PROCEDURES ..28
XII. PERIODIC REVIEW OF THE WATCHLISTING GUIDANCE ..29
CHAPTER 2: MINIMUM IDENTIFYING CRITERIA ..30
I. BIOMETRIC NOMINATIONS .. 30
II. MINIMUM BIOGRAPHIC NOMINATION REQUIREMENT ..30
MINIMUM BIOGRAPHIC INFORMATION REQUIRED FOR EXCEPTIONS TO THE
UN CLASSIF OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
Page 1
OFFICIAL USE SECURITY INFORMATION
2013 WATCHLISTIN GUIDANCE
TABLE OF CONTENTS
CHAPTER I: WATCHLISTING PROCESS AND PROCEDURES ..5
I. INTRODUCTION ..5
II. WATCHLISTING AUTHORITIES ..6
CONSTITUTIONALLY PROTECTED ACTIVITIES .. I0
IV. WATCHLISTING POLICIES .. I
V. WATCHLISTING STANDARD: IDENTIFYING AND SUBSTANTIVE
DEROGATORY CRITERIA .. I2
VI. WATCHLISTING PROCESS OVERVIEW .. I3
VII. ROLES AND RESPONSIBILITES FOR TIIE WATCHLISTING AND SCREENING
COMMUNITY .. I6
QUALITY CONTROL MEASURES .. I 7
IX. NOMINATION PROCEDURES ..20
X. PROCEDURES TO REMOVE AN INDIVIDUAL FROM THE WATCI-IIJST
XI. REDRESS PROCEDURES ..28
XII. PERIODIC REVIEW OF THE WATCHLISTING GUIDANCE ..29
CHAPTER 2: MINIMUM IDENTIFYING CRITERIA ..30
I. BIOMETRIC NOMINATIONS .. 30
II. MINIMUM BIOGRAPHIC NOMINATION REQUIREMENT ..30
MINIMUM BIOGRAPHIC INFORMATION REQUIRED FOR EXCEPTIONS TO THE
UN CLASSIF OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
Page 1
OFFICIAL USE SECURITY INFORMATION
MINIMUM SUBSTANTIVE DEROGATORY STANDARDS FOR TERRORIST
WATCHLISTING ..32
CHAPTER 3: MINIMUM SUBSTANTIVE DEROGATORY CRITERIA ..33
I. INTRODUCTION AND PURPOSE ..33
II. REASONABLE SUSPICION ..33
KNOWN TERRORISTS ..35
IV. SUSPECTED TERRORISTS .. 37
V. EXCEPTIONS TO SUPPORT IMMIGRATION AND VISA SCREENING ACTIVITIES
BY DHS AND DOS ..42
VI. SPECIAL CONSIDERATIONS ..45
VII. EXAMPLES OF TERRORISM TERRORIST ACTIVITIES ..47
CHAPTER 4: NO FLY, SELECTEE AND EXPANDED SELECTEE LISTS
IMPLEMENTATION GUIDANCEBACKGROUND ..50
II. PRE-CON DITIONS FOR PLACEMENT ON THE NO FLY OR SELECTEE LIST. 50
NO FLY LIST CRITERIA ..5I
IV. FURTHER CLARIFICATION OF NO FLY CRITERIA ..51
V. SELECTEE LIST CRITERIA ..54
VI. EXPANDED SELECTEE LIST CRITERIA ..54
VII. ACTIONS BASED UPON POSITIVE MATCHES TO THE NO FLY, SELECTEE, OR
EXPANDED SELECTEE LISTS ..54
IMPLEMENTATION GUIDELINES ..55
OR OFFICIAL USE SECURITY INFORMATION
Page 2
OFFICIAL USE SECURITY INFORMATION
MINIMUM SUBSTANTIVE DEROGATORY STANDARDS FOR TERRORIST
WATCHLISTING ..32
CHAPTER 3: MINIMUM SUBSTANTIVE DEROGATORY CRITERIA ..33
I. INTRODUCTION AND PURPOSE ..33
II. REASONABLE SUSPICION ..33
KNOWN TERRORISTS ..35
IV. SUSPECTED TERRORISTS .. 37
V. EXCEPTIONS TO SUPPORT IMMIGRATION AND VISA SCREENING ACTIVITIES
BY DHS AND DOS ..42
VI. SPECIAL CONSIDERATIONS ..45
VII. EXAMPLES OF TERRORISM TERRORIST ACTIVITIES ..47
CHAPTER 4: NO FLY, SELECTEE AND EXPANDED SELECTEE LISTS
IMPLEMENTATION GUIDANCEBACKGROUND ..50
II. PRE-CON DITIONS FOR PLACEMENT ON THE NO FLY OR SELECTEE LIST. 50
NO FLY LIST CRITERIA ..5I
IV. FURTHER CLARIFICATION OF NO FLY CRITERIA ..51
V. SELECTEE LIST CRITERIA ..54
VI. EXPANDED SELECTEE LIST CRITERIA ..54
VII. ACTIONS BASED UPON POSITIVE MATCHES TO THE NO FLY, SELECTEE, OR
EXPANDED SELECTEE LISTS ..54
IMPLEMENTATION GUIDELINES ..55
OR OFFICIAL USE SECURITY INFORMATION
Page 2
OR OFFICIAL USE SECURITY INFORMATION
IX. SPECIAL SITUATIONS ..56
X. NOMINATIONS THAT ARE SUITABLE FOR EITIIER TI IE NO
FLY OR THE SELECTEE LIST .. 57
CHAPTER 5: ENCOUNTER MANAGEMENT AND ANALYSIS ..58
I. INTRODUCTION AND PURPOSE .. 58
II. PROCESSING TERRORISM INFORMATION FROM ENCOUNTERS WITH
POSITIVELY IDENTIFIED KNOWN OR SUSPECTED TERRORISTS .. 59
CATEGORIES OF TERRORISM INFORMATION FROM ENCOUNTERS WITH
POSITIVELY IDENTIFIED KNOWN OR SUSPECTED TERRORISTS OF
POTENTIAL INTEREST .. 65
IV. ENCOUNTER MANAGEMENT ACTIONS ..69
V. ROLES AND RESPONSIBILITIES FOR UPDATING EXISTING KNOWN OR
SUSPECTED TERRORIST RECORDS AND NOMINATING NEW KNOWN OR
BASED ON INFORMATION FROM POSITIVE
ENCOUNTERS .. 7]
VI. RESPONSIBILITY T0 COORDINATE ANY ACTIONS CONTEMPLATED BASED
ON INFORMATION FROM ENCOUNTERS WITII A KNOWN OR SUSPECTED
TERRORIST ..73
VII. EXAMPLES OF TERRORISM INFORMATION TYPICALI.Y AVAILABLE FROM
ENCOUNTERS .. 74
OBTAINING ENCOUNTER INFORMATION THROUGH DAILY
ENCOUNTER REPORTS .. 77
APPENDIX 1: DEFINITIONS
APPENDIX 2: HSPD-6
APPENDIX 3: TSC MOU
APPENDIX 4: ADDENDUM TO TSC MOU
UN OR OFFICIAL USE SECURITY INFORMATION
Page I 3
OR OFFICIAL USE SECURITY INFORMATION
IX. SPECIAL SITUATIONS ..56
X. NOMINATIONS THAT ARE SUITABLE FOR EITIIER TI IE NO
FLY OR THE SELECTEE LIST .. 57
CHAPTER 5: ENCOUNTER MANAGEMENT AND ANALYSIS ..58
I. INTRODUCTION AND PURPOSE .. 58
II. PROCESSING TERRORISM INFORMATION FROM ENCOUNTERS WITH
POSITIVELY IDENTIFIED KNOWN OR SUSPECTED TERRORISTS .. 59
CATEGORIES OF TERRORISM INFORMATION FROM ENCOUNTERS WITH
POSITIVELY IDENTIFIED KNOWN OR SUSPECTED TERRORISTS OF
POTENTIAL INTEREST .. 65
IV. ENCOUNTER MANAGEMENT ACTIONS ..69
V. ROLES AND RESPONSIBILITIES FOR UPDATING EXISTING KNOWN OR
SUSPECTED TERRORIST RECORDS AND NOMINATING NEW KNOWN OR
BASED ON INFORMATION FROM POSITIVE
ENCOUNTERS .. 7]
VI. RESPONSIBILITY T0 COORDINATE ANY ACTIONS CONTEMPLATED BASED
ON INFORMATION FROM ENCOUNTERS WITII A KNOWN OR SUSPECTED
TERRORIST ..73
VII. EXAMPLES OF TERRORISM INFORMATION TYPICALI.Y AVAILABLE FROM
ENCOUNTERS .. 74
OBTAINING ENCOUNTER INFORMATION THROUGH DAILY
ENCOUNTER REPORTS .. 77
APPENDIX 1: DEFINITIONS
APPENDIX 2: HSPD-6
APPENDIX 3: TSC MOU
APPENDIX 4: ADDENDUM TO TSC MOU
UN OR OFFICIAL USE SECURITY INFORMATION
Page I 3

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
APPENDIX 5: INFORMATION SHARING MOU
APPENDIX 6: EXECUTIVE ORDER 13388
APPENDIX 7: PROTOCOL ON TERRORIST NOMINATIONS
APPENDIX 8: REDRESS MOU
APPENDIX 9: PRESIDENTIAL MEMORANDUM REGARDING 12/25/2009 TERRORIST
ATTACK
APPENDIX 10: ACRONYMS AND ABBREVIATIONS
APPENDIX 11: SUMMARY OF CHANGES AND UPDATES FROM THE 2010
WATCHIJISTING GUIDANCE
OR OFFICIAL USE SECURITY INFORMATION
Page 4
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
APPENDIX 5: INFORMATION SHARING MOU
APPENDIX 6: EXECUTIVE ORDER 13388
APPENDIX 7: PROTOCOL ON TERRORIST NOMINATIONS
APPENDIX 8: REDRESS MOU
APPENDIX 9: PRESIDENTIAL MEMORANDUM REGARDING 12/25/2009 TERRORIST
ATTACK
APPENDIX 10: ACRONYMS AND ABBREVIATIONS
APPENDIX 11: SUMMARY OF CHANGES AND UPDATES FROM THE 2010
WATCHIJISTING GUIDANCE
OR OFFICIAL USE SECURITY INFORMATION
Page 4

OFFICIAL USE SECURITY INFORMATION
CHAPTER 1: WATCHLISTING PROCESS AND PROCEDURES
I. INTRODUCTION
1.1 A key foundation for screening is the U.S. Govemment?s TERRORIST
watchlisting process managed by the Terrorist Screening Center (TSC). The TSC was
established by the Attorney General, acting through the Director of the Federal Bureau of
Investigation (FBI), and in coordination with the Secretary of State, the Secretary of
Homeland Security, and the then Director of Central Intelligence for the Intelligence
Community The TSC is supported by the National Counterterrorism Center (NCTC),
the Department of State (DOS), the Department of Homeland Security (Dl IS), the 1C, the
Law Enforcement Agencies, Regulatory Agencies and Diplomatic Bureaus. The TSC has
created and maintains the Terrorist Screening Database (TSDB) or Terrorist Watchlist to serve
as the U.S. Government's consolidated watchlist for TERRORISM SCREENING INFORMATION.
l.2 The current TERRORIST watchlisting process supports the U.S. Government?s efforts to combat
TERRORISM by: (I) consolidating the U.S. Government?s Terrorist Watchlist in the (2)
helping SCREENERS and intelligence agencies accurately identify individuals on the Terrorist
Watchlist; (3) providing SCREENERS with information to help them respond appropriately
during ENCOUNTERS with KNOWN or SUSPECTED and, (4) subsequently collecting
information about the KNOWN or SUSPECTED TERRORIST for use in assessing threats and
conducting investigations.2 The collected information may be incorporated into the Terrorist
Identities Datamart Environment (TIDE) and TSDB to enhance the records of KNOWN or
SUSPECTEI) and may be made available to the wider watchlisting and screening
communities. Today, the TSDB also includes information about certain foreign nationals who
are associated with TERRORISM, TERRORIST ACTIVITY, or KNOWN or SUSPECTED
but for whom there is insuf?cient DEROGATORY INFORMATION to be independently
watchlisted. This may include certain immediate family members of KNOWN or SUSPECTED
TERRORISTS, or known associates of or SUSPECTED TERRORISTS. These additional
categories of records (also known as exceptions to the REASONABLE SUSPICION standard) are
maintained to support immigration and screening activities primarily conducted by DOS and
DHS.
I See Appendix 1, Definitions for words or phrases appearing in all capitalized letters throughout this Watchlisting
Guidance.
2 A SCREENER is a Department or Agency that is authorized to conduct TERRORISM screening to determine if an
individual is a possible match to a KNOWN or SUSPECTED TERRORIST in the TSDB. The term is used
throughout this document as a general reference to a government of?cial who compares an individual?s information
with information in the TSDB to determine if an individual is in the TSDB. Certain SCREENERS have components
which perform both screening and law enforcement duties and law enforcement of?cials who engage in such activities
may normally describe their targeting or other actions in this context as other than "screening." For ease of reference,
government of?cials who compare an individual?s information with information in the TSDB will be referred to in the
Guidance as The internal guidance set forth herein is not intended to create or confer any rights,
privileges, or bene?ts in any matter, case, or proceeding. See United States v. Caceres, 440 U.S. 74l.
See Chapter 3, Section V, infra, for more details. Aside from these limited exceptions, references to the TSDB in this
Watchlisting Guidance denote the TSDB as containing information about KNOWN or SUSPECTED
OR OFFICIAL USE SECURITY INFORMATION
Page 5
OFFICIAL USE SECURITY INFORMATION
CHAPTER 1: WATCHLISTING PROCESS AND PROCEDURES
I. INTRODUCTION
1.1 A key foundation for screening is the U.S. Govemment?s TERRORIST
watchlisting process managed by the Terrorist Screening Center (TSC). The TSC was
established by the Attorney General, acting through the Director of the Federal Bureau of
Investigation (FBI), and in coordination with the Secretary of State, the Secretary of
Homeland Security, and the then Director of Central Intelligence for the Intelligence
Community The TSC is supported by the National Counterterrorism Center (NCTC),
the Department of State (DOS), the Department of Homeland Security (Dl IS), the 1C, the
Law Enforcement Agencies, Regulatory Agencies and Diplomatic Bureaus. The TSC has
created and maintains the Terrorist Screening Database (TSDB) or Terrorist Watchlist to serve
as the U.S. Government's consolidated watchlist for TERRORISM SCREENING INFORMATION.
l.2 The current TERRORIST watchlisting process supports the U.S. Government?s efforts to combat
TERRORISM by: (I) consolidating the U.S. Government?s Terrorist Watchlist in the (2)
helping SCREENERS and intelligence agencies accurately identify individuals on the Terrorist
Watchlist; (3) providing SCREENERS with information to help them respond appropriately
during ENCOUNTERS with KNOWN or SUSPECTED and, (4) subsequently collecting
information about the KNOWN or SUSPECTED TERRORIST for use in assessing threats and
conducting investigations.2 The collected information may be incorporated into the Terrorist
Identities Datamart Environment (TIDE) and TSDB to enhance the records of KNOWN or
SUSPECTEI) and may be made available to the wider watchlisting and screening
communities. Today, the TSDB also includes information about certain foreign nationals who
are associated with TERRORISM, TERRORIST ACTIVITY, or KNOWN or SUSPECTED
but for whom there is insuf?cient DEROGATORY INFORMATION to be independently
watchlisted. This may include certain immediate family members of KNOWN or SUSPECTED
TERRORISTS, or known associates of or SUSPECTED TERRORISTS. These additional
categories of records (also known as exceptions to the REASONABLE SUSPICION standard) are
maintained to support immigration and screening activities primarily conducted by DOS and
DHS.
I See Appendix 1, Definitions for words or phrases appearing in all capitalized letters throughout this Watchlisting
Guidance.
2 A SCREENER is a Department or Agency that is authorized to conduct TERRORISM screening to determine if an
individual is a possible match to a KNOWN or SUSPECTED TERRORIST in the TSDB. The term is used
throughout this document as a general reference to a government of?cial who compares an individual?s information
with information in the TSDB to determine if an individual is in the TSDB. Certain SCREENERS have components
which perform both screening and law enforcement duties and law enforcement of?cials who engage in such activities
may normally describe their targeting or other actions in this context as other than "screening." For ease of reference,
government of?cials who compare an individual?s information with information in the TSDB will be referred to in the
Guidance as The internal guidance set forth herein is not intended to create or confer any rights,
privileges, or bene?ts in any matter, case, or proceeding. See United States v. Caceres, 440 U.S. 74l.
See Chapter 3, Section V, infra, for more details. Aside from these limited exceptions, references to the TSDB in this
Watchlisting Guidance denote the TSDB as containing information about KNOWN or SUSPECTED
OR OFFICIAL USE SECURITY INFORMATION
Page 5

OR OFFICIAL USE SECURITY INFORMATION
L3
1.4
II.
1.5
L6
This Watchlisting Guidance has been developed to help standardize the watchlisting
community?s nomination and screening processes. lt is important to remember, however, that
watchlisting is not an exact science. There are inherent limitations in any primarily name-
based system and analytic judgments may differ regarding whether subjective criteria have
been met. Given these realities, the US Government?s watchlisting process attempts to
safeguard the American people from a TERRORIST attack while safeguarding privacy, civil
rights and civil liberties.
Thus, when reasonable minds eculd disagree on a record, a NOMINATOR will make a
determination in favor of sending the nomination to NCTC for consideration and additional
review. The TSC has the ?nal decision authority regarding watchlisting determinations and
will add an individual?s name to the TSDB, consistent with TSC Actions and Processes as
further described in Paragraph 1.56.
WATCHLISTING AUTHORITIES
On September 16, 2003, the President issued Homeland Security Presidential Directive 6
(HSPD-6), which directed the Attorney General to ?establish an organization to consolidate
the US. Government?s approach to TERRORISM SCREENING and provide for the appropriate
and lawful use of TERRORIST INFORMATION in screening processes.?4 TERRORIST
INFORMATION was speci?cally de?ned to mean ?information about individuals known or
apprOpriately suspected to be or have been engaged in conduct constituting, in preparation for,
in aid of, or related to HSPD-6 also directed the heads of Executive
Departments and Agencies to provide to NCTC on an on?going basis, ?all appropriate
TERRORIST INFORMATION in their possession, custody, or control,? to the extent permitted by
law.
The intent of was to consolidate all TERRORISM INFORMATION at the Terrorist Threat
Integration Center - whose functions were assumed by NCTC5 in a classi?ed
database that would then extract Unclassi?ed, For Of?cial Use Only TERRORIST
IDENTIFIERS for passage to the new organization created by the Attorney General. Thus,
concurrent with the issuance of HSPD-6, the TSC was established via the Memorandum of
Understanding on the Integration and Use of Screening Information to Protect Against
Terrorism (TSC MOU), which was signed by the Attorney General, the Secretaries of State
and Homeland Security, and the Director of Central Intelligence (on behalf of the lC).6
4 See Appendix 2, HSPD-6.
5 See FN 8, infra.
See Appendix 3, see also Appendix 4, Addendum to the TSC MOU. In 2004, the Secretaries of State,
Treasury, and Defense also became signatories to the Memorandum of Understanding between the Intelligence
Community, Federal Law Enforcement Agencies, and the Department of Homeland Security Concerning Information
Sharing, dated March 4, 2003 (Information Sharing MOU). By doing so, they agreed that all provisions of the TSC
MOU and the Information Sharing MOU apply to all entities that are or become a part of their respective Departments.
OR OFFICIAL USE ON SECURITY INFORMATION
Page I 6
OR OFFICIAL USE SECURITY INFORMATION
L3
1.4
II.
1.5
L6
This Watchlisting Guidance has been developed to help standardize the watchlisting
community?s nomination and screening processes. lt is important to remember, however, that
watchlisting is not an exact science. There are inherent limitations in any primarily name-
based system and analytic judgments may differ regarding whether subjective criteria have
been met. Given these realities, the US Government?s watchlisting process attempts to
safeguard the American people from a TERRORIST attack while safeguarding privacy, civil
rights and civil liberties.
Thus, when reasonable minds eculd disagree on a record, a NOMINATOR will make a
determination in favor of sending the nomination to NCTC for consideration and additional
review. The TSC has the ?nal decision authority regarding watchlisting determinations and
will add an individual?s name to the TSDB, consistent with TSC Actions and Processes as
further described in Paragraph 1.56.
WATCHLISTING AUTHORITIES
On September 16, 2003, the President issued Homeland Security Presidential Directive 6
(HSPD-6), which directed the Attorney General to ?establish an organization to consolidate
the US. Government?s approach to TERRORISM SCREENING and provide for the appropriate
and lawful use of TERRORIST INFORMATION in screening processes.?4 TERRORIST
INFORMATION was speci?cally de?ned to mean ?information about individuals known or
apprOpriately suspected to be or have been engaged in conduct constituting, in preparation for,
in aid of, or related to HSPD-6 also directed the heads of Executive
Departments and Agencies to provide to NCTC on an on?going basis, ?all appropriate
TERRORIST INFORMATION in their possession, custody, or control,? to the extent permitted by
law.
The intent of was to consolidate all TERRORISM INFORMATION at the Terrorist Threat
Integration Center - whose functions were assumed by NCTC5 in a classi?ed
database that would then extract Unclassi?ed, For Of?cial Use Only TERRORIST
IDENTIFIERS for passage to the new organization created by the Attorney General. Thus,
concurrent with the issuance of HSPD-6, the TSC was established via the Memorandum of
Understanding on the Integration and Use of Screening Information to Protect Against
Terrorism (TSC MOU), which was signed by the Attorney General, the Secretaries of State
and Homeland Security, and the Director of Central Intelligence (on behalf of the lC).6
4 See Appendix 2, HSPD-6.
5 See FN 8, infra.
See Appendix 3, see also Appendix 4, Addendum to the TSC MOU. In 2004, the Secretaries of State,
Treasury, and Defense also became signatories to the Memorandum of Understanding between the Intelligence
Community, Federal Law Enforcement Agencies, and the Department of Homeland Security Concerning Information
Sharing, dated March 4, 2003 (Information Sharing MOU). By doing so, they agreed that all provisions of the TSC
MOU and the Information Sharing MOU apply to all entities that are or become a part of their respective Departments.
OR OFFICIAL USE ON SECURITY INFORMATION
Page I 6

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.8
L9
Under HSPD-6, consistent with the US. Constitution and applicable laws, including those
protecting the rights of all Americans, the TSC was to develop and maintain an unclassi?ed
database containing the most thorough, accurate, and current identity information possible
about KNOWN or SUSPECTED TERRORISTS. The TSC created the TSDB to meet these goals.7
The TSDB is also known as the Terrorist Watchlist. The TSDB receives TERRORIST
IDENTIFIERS from two sources: TIDE provides information concerning KNOWN or
SUSPECTED international TERRORISTS and the Terrorist Review and Examinations Unit
(TREX) provides the identities of KNOWN or SUSPECTED domestic TERRORISTS who have no
link to international TERRORISM. TIDE contains identifying and substantive
DEROGATORY INFORMATION on KNOWN or SUSPECTED international TERRORISTS and the
Sentinel system contains supporting information regarding purely domestic TERRORISTS.
Pursuant to Paragraph (2) of HSPD-6, the NCTC is mandated to ?provide with access
to all apprOpriate information or intelligence in the custody, possession, or control
that requires to perform its functions.? ful?lls this function by providing
TSDB with information about KNOWN or SUSPECTED TERRORISTS from
TIDE and by providing access to TIDE Online, a read?only copy of the TIDE database, to
those in the watchlisting community who require access.
establishment by the President was codified by section I02l of the Intelligence
Reform and Terrorism Prevention Act of 2004 Pursuant to IRTPA, NCTC shall
?serve as the central and shared knowledge bank on KNOWN and SUSPECTEI) and
international terror groups.? In addition, NCTC ?may, consistent with applicable law, the
direction of the President, and guidelines referred to in [the statute], receive intelligence
pertaining exclusively to domestic counterterrorism from any Federal, State, or local
government or other source necessary to fulfill its responsibilities and retain and disseminate
such intelligence??
l.9.l All Departments and Agencies are required to provide NCTC with all TERRORISM
INFORMATION. Due to the amount of information involved, only a subset of this
information is provided in the NCTC prescribed format designed to facilitate direct
ingestion into the TIDE. NOMINATING DEPARTMENTS and AGENCIES, however, should
remain focused on reviewing and watchlisting TERRORISM INFORMATION from datasets
most likely to contain information about KNOWN or SUSPECTED TERRORISTS.
Addendum to the TSC MOU, which superseded Addendum A, incorporates by reference all provisions of the
Information Sharing MOU. See Appendix 5.
7 The TSDB consolidates the US. Govemment?s TERRORISM screening and lookout databases into a single integrated
TERRORIST identities database.
3 NCTC initially was created by Executive Order l3354 (August 27, 2004) to serve as the primary organization in the
.S. Government for analyzing and integrating all intelligence possessed or acquired by the US. Government
pertaining to TERRORISM and counterterrorism, excepting purely domestic counterterrorism information. Executive
Order 13354 was revoked by Executive Order 13470 (July 30, 2008) after NCTC was codi?ed in IRTPA section 102].
9 In addition to the provision of domestic KNOWN or SUSPECTED TERRORISTS directly to the TSC, the TREX unit
also provides the identities of international KNOWN or SUSPECTED TERRORISTS to NCTC for inclusion in TIDE.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 7
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.8
L9
Under HSPD-6, consistent with the US. Constitution and applicable laws, including those
protecting the rights of all Americans, the TSC was to develop and maintain an unclassi?ed
database containing the most thorough, accurate, and current identity information possible
about KNOWN or SUSPECTED TERRORISTS. The TSC created the TSDB to meet these goals.7
The TSDB is also known as the Terrorist Watchlist. The TSDB receives TERRORIST
IDENTIFIERS from two sources: TIDE provides information concerning KNOWN or
SUSPECTED international TERRORISTS and the Terrorist Review and Examinations Unit
(TREX) provides the identities of KNOWN or SUSPECTED domestic TERRORISTS who have no
link to international TERRORISM. TIDE contains identifying and substantive
DEROGATORY INFORMATION on KNOWN or SUSPECTED international TERRORISTS and the
Sentinel system contains supporting information regarding purely domestic TERRORISTS.
Pursuant to Paragraph (2) of HSPD-6, the NCTC is mandated to ?provide with access
to all apprOpriate information or intelligence in the custody, possession, or control
that requires to perform its functions.? ful?lls this function by providing
TSDB with information about KNOWN or SUSPECTED TERRORISTS from
TIDE and by providing access to TIDE Online, a read?only copy of the TIDE database, to
those in the watchlisting community who require access.
establishment by the President was codified by section I02l of the Intelligence
Reform and Terrorism Prevention Act of 2004 Pursuant to IRTPA, NCTC shall
?serve as the central and shared knowledge bank on KNOWN and SUSPECTEI) and
international terror groups.? In addition, NCTC ?may, consistent with applicable law, the
direction of the President, and guidelines referred to in [the statute], receive intelligence
pertaining exclusively to domestic counterterrorism from any Federal, State, or local
government or other source necessary to fulfill its responsibilities and retain and disseminate
such intelligence??
l.9.l All Departments and Agencies are required to provide NCTC with all TERRORISM
INFORMATION. Due to the amount of information involved, only a subset of this
information is provided in the NCTC prescribed format designed to facilitate direct
ingestion into the TIDE. NOMINATING DEPARTMENTS and AGENCIES, however, should
remain focused on reviewing and watchlisting TERRORISM INFORMATION from datasets
most likely to contain information about KNOWN or SUSPECTED TERRORISTS.
Addendum to the TSC MOU, which superseded Addendum A, incorporates by reference all provisions of the
Information Sharing MOU. See Appendix 5.
7 The TSDB consolidates the US. Govemment?s TERRORISM screening and lookout databases into a single integrated
TERRORIST identities database.
3 NCTC initially was created by Executive Order l3354 (August 27, 2004) to serve as the primary organization in the
.S. Government for analyzing and integrating all intelligence possessed or acquired by the US. Government
pertaining to TERRORISM and counterterrorism, excepting purely domestic counterterrorism information. Executive
Order 13354 was revoked by Executive Order 13470 (July 30, 2008) after NCTC was codi?ed in IRTPA section 102].
9 In addition to the provision of domestic KNOWN or SUSPECTED TERRORISTS directly to the TSC, the TREX unit
also provides the identities of international KNOWN or SUSPECTED TERRORISTS to NCTC for inclusion in TIDE.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 7

OR OFFICIAL USE SECURITY INFORMATION
1.10 On August 27, 2004, the President issued Homeland Security Presidential Directive 1
1.12
1.13
1.14
1), which ?builds upon to enhance screening to more
effectively detect and interdict SUSPECTED TERRORISTS and TERRORIST ACTIVITIES. 1
de?nes as ?individuals known or reasonably suspected to be or have
been engaged in conduct constituting, in preparation for, in aid of, or related to TERRORISM . . .
and TERRORIST
To enhance information sharing, another key component of the consolidated terrorist
watchlisting system, the President issued Executive Order 13388, which provides that the
head of each Agency that possesses or acquires TERRORISM INFORMATION shall give
access to that information to the head of each other Agency that has counterterrorism
functions.l0
On June 5, 2008, the President issued Homeland Security Presidential Directive 24 (HSPD-
24) to further build upon the TERRORIST screening policies announced in HSPD-6 and HSPD-
to protect the nation from by enhancing the use of biometrics. In
the President directed that?. . . agencies, shall, to the fullest extent permitted by law, make
available to other agencies all biometric and associated biographic and contextual information
associated with persons for whom there is an articulable and reasonable basis for suspicion
that they pose a threat to national security? (emphasis added). HSPD-24 underscores the
value of biometrics in achieving effective TERRORISM screening and emphasizes the need for a
layered approach to identi?cation and screening of individuals, as no single mechanism is
suf?cient.
The relevant TERRORISM screening Presidential Directives use words and phrases to describe a
KNOWN or SUSPECTED TERRORIST subject to TERRORIST screening without de?ning them:
?appropriately suspected?
(HSPD-6), ?reasonably suspected? and ?articulable and reasonable basis for
suspicion? (HSPD-24). Thus, previous watchlisting guidance supplied de?nitions of key
terms and the standard that would apply to terrorist watchlisting decisions.
Neither HSPD-6 nor SPD-I 1 de?nes and/0r TERRORIST While
federal law contains numerous de?nitions of ?terrorism??, for watchlisting purposes under
this Guidance, and/or TERRORIST combine elements from various
federal de?nitions and are considered to:
1.14.1 involve Violent acts or acts dangerous to human life, property, or infrastructure
'0 See Appendix 6, Executive Order 13388.
See 50 U.S.C. 1801(c) (Foreign Intelligence Surveillance Act de?nition of ?intemational terrorism?);
Immigration and Nationality Act (INA) [8 U.S.C. I (de?ning ?terrorist activity?);
INA 212(a)(3)(B)(iv) [8 U.S.C. (de?ning to ?engage in terrorist activity?); 18 U.S.C. 2331(1)
(de?ning ?international terrorism?); 18 U.S.C. 2332(b) (de?ning ?federal crime of terrorism?); Executive Order 13224,
66 Fed. Reg. 49079 (September 23, 2001) (de?ning ?terrorism?).
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 8
OR OFFICIAL USE SECURITY INFORMATION
1.10 On August 27, 2004, the President issued Homeland Security Presidential Directive 1
1.12
1.13
1.14
1), which ?builds upon to enhance screening to more
effectively detect and interdict SUSPECTED TERRORISTS and TERRORIST ACTIVITIES. 1
de?nes as ?individuals known or reasonably suspected to be or have
been engaged in conduct constituting, in preparation for, in aid of, or related to TERRORISM . . .
and TERRORIST
To enhance information sharing, another key component of the consolidated terrorist
watchlisting system, the President issued Executive Order 13388, which provides that the
head of each Agency that possesses or acquires TERRORISM INFORMATION shall give
access to that information to the head of each other Agency that has counterterrorism
functions.l0
On June 5, 2008, the President issued Homeland Security Presidential Directive 24 (HSPD-
24) to further build upon the TERRORIST screening policies announced in HSPD-6 and HSPD-
to protect the nation from by enhancing the use of biometrics. In
the President directed that?. . . agencies, shall, to the fullest extent permitted by law, make
available to other agencies all biometric and associated biographic and contextual information
associated with persons for whom there is an articulable and reasonable basis for suspicion
that they pose a threat to national security? (emphasis added). HSPD-24 underscores the
value of biometrics in achieving effective TERRORISM screening and emphasizes the need for a
layered approach to identi?cation and screening of individuals, as no single mechanism is
suf?cient.
The relevant TERRORISM screening Presidential Directives use words and phrases to describe a
KNOWN or SUSPECTED TERRORIST subject to TERRORIST screening without de?ning them:
?appropriately suspected?
(HSPD-6), ?reasonably suspected? and ?articulable and reasonable basis for
suspicion? (HSPD-24). Thus, previous watchlisting guidance supplied de?nitions of key
terms and the standard that would apply to terrorist watchlisting decisions.
Neither HSPD-6 nor SPD-I 1 de?nes and/0r TERRORIST While
federal law contains numerous de?nitions of ?terrorism??, for watchlisting purposes under
this Guidance, and/or TERRORIST combine elements from various
federal de?nitions and are considered to:
1.14.1 involve Violent acts or acts dangerous to human life, property, or infrastructure
'0 See Appendix 6, Executive Order 13388.
See 50 U.S.C. 1801(c) (Foreign Intelligence Surveillance Act de?nition of ?intemational terrorism?);
Immigration and Nationality Act (INA) [8 U.S.C. I (de?ning ?terrorist activity?);
INA 212(a)(3)(B)(iv) [8 U.S.C. (de?ning to ?engage in terrorist activity?); 18 U.S.C. 2331(1)
(de?ning ?international terrorism?); 18 U.S.C. 2332(b) (de?ning ?federal crime of terrorism?); Executive Order 13224,
66 Fed. Reg. 49079 (September 23, 2001) (de?ning ?terrorism?).
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 8

OR OFFICIAL USE SECURITY INFORMATION
which may be a violation of US. law, or may have been, if those acts were committed in
the United States; and,
1.14.2 appear to be intended?
1.14.2.1 to intimidate or coerce a civilian population;
1.14.2.2 to in?uence the policy of a government by intimidation or coercion; or,
1.14.2.3 to affect the conduct of a government by mass destruction, assassination,
kidnapping, or hostage-taking.
1.15 This includes activities that facilitate or support TERRORISM and/or TERRORIST ACTIVITIES such
as providing a safe house, transportation, communications, funds, transfer of funds or other
material bene?t, false documentation or identi?cation, weapons (including chemical,
biological, or radiological weapons), explosives, or training for the commission of an act of
TERRORISM and/or TERRORIST ACTIVITY.
1.16 HSPD-24 speaks in terms of ?articulable and reasonable basis for suspicion? to describe a
KNOWN or SUSPECTED TERRORIST who should be watchlisted and represents the President?s
most recent explanation concerning US. policy regarding the individuals who pose a threat to
national security and should be screened to better protect the American people. Accordingly,
that standard has been adopted and is clarified in this Watchlisting Guidance in Chapter 3,
Section II.
1.17 On December 16, 2005, in accordance with section 1016 of IRTPA, the President issued a
Memorandum for the Heads of Executive Departments and Agencies prescribing the
guidelines and requirements in support of the creation and implementation of the Information
Sharing Environment (ISE). In Guideline 5 of that Memorandum, the President directed, as
he had earlier in Executive Order 13353 that the information privacy rights and other legal
rights of Americans must be protected and that guidelines be deveIOped and approved to
ensure that ?such rights are protected in the development and use of the In December
2006, the President approved for issuance the ISE Privacy Guidelines by the Program
Manager. '3
1.18 A second addendum to the TSC MOU, Addendum M, which supplements and incorporates
by reference all provisions of the TSC MOU, superseded Addendum A and became effective
on January 18, 2007. The Directors of National Intelligence, NCTC, and the TSC joined as
signatories in Addendum B. Paragraph 7 of Addendum introduces the term TERRORIST
IDENTIFIERS to more clearly describe the type of TERRORIST identity elements that are deemed
12 See Executive Order 13353, Establishing the President?s Board on Safeguarding Americans' Civil Liberties (August
27, 2004).
'3 See Guidelines to Ensure that Information Privacy and other Legal Rights of Americans are Protected in the
Development and Use of the Information Sharing Environment (December, 2006).
'4 See Appendix 4, Addendum to the TSC MOU.
UN OR OFFICIAL USE SECURITY INFORMATION
Page 9
OR OFFICIAL USE SECURITY INFORMATION
which may be a violation of US. law, or may have been, if those acts were committed in
the United States; and,
1.14.2 appear to be intended?
1.14.2.1 to intimidate or coerce a civilian population;
1.14.2.2 to in?uence the policy of a government by intimidation or coercion; or,
1.14.2.3 to affect the conduct of a government by mass destruction, assassination,
kidnapping, or hostage-taking.
1.15 This includes activities that facilitate or support TERRORISM and/or TERRORIST ACTIVITIES such
as providing a safe house, transportation, communications, funds, transfer of funds or other
material bene?t, false documentation or identi?cation, weapons (including chemical,
biological, or radiological weapons), explosives, or training for the commission of an act of
TERRORISM and/or TERRORIST ACTIVITY.
1.16 HSPD-24 speaks in terms of ?articulable and reasonable basis for suspicion? to describe a
KNOWN or SUSPECTED TERRORIST who should be watchlisted and represents the President?s
most recent explanation concerning US. policy regarding the individuals who pose a threat to
national security and should be screened to better protect the American people. Accordingly,
that standard has been adopted and is clarified in this Watchlisting Guidance in Chapter 3,
Section II.
1.17 On December 16, 2005, in accordance with section 1016 of IRTPA, the President issued a
Memorandum for the Heads of Executive Departments and Agencies prescribing the
guidelines and requirements in support of the creation and implementation of the Information
Sharing Environment (ISE). In Guideline 5 of that Memorandum, the President directed, as
he had earlier in Executive Order 13353 that the information privacy rights and other legal
rights of Americans must be protected and that guidelines be deveIOped and approved to
ensure that ?such rights are protected in the development and use of the In December
2006, the President approved for issuance the ISE Privacy Guidelines by the Program
Manager. '3
1.18 A second addendum to the TSC MOU, Addendum M, which supplements and incorporates
by reference all provisions of the TSC MOU, superseded Addendum A and became effective
on January 18, 2007. The Directors of National Intelligence, NCTC, and the TSC joined as
signatories in Addendum B. Paragraph 7 of Addendum introduces the term TERRORIST
IDENTIFIERS to more clearly describe the type of TERRORIST identity elements that are deemed
12 See Executive Order 13353, Establishing the President?s Board on Safeguarding Americans' Civil Liberties (August
27, 2004).
'3 See Guidelines to Ensure that Information Privacy and other Legal Rights of Americans are Protected in the
Development and Use of the Information Sharing Environment (December, 2006).
'4 See Appendix 4, Addendum to the TSC MOU.
UN OR OFFICIAL USE SECURITY INFORMATION
Page 9

OR OFFICIAL USE SECURITY INFORMATION
without regard to the classi?cation of the source material from which it is drawn.
TERRORIST include those listed in Addendum names and aliases; dates of
birth; places of birth; unique identifying numbers; passport information; countries of origin
and nationality; physical identi?ers; known locations; photographs or renderings; ?ngerprints
or other biometric data; employment data; license plate numbers; and any other TERRORIST
IDENTIFIERS that ORIGINATORS speci?cally provide for passage to the TSC). For example,
email addresses and phone numbers are increasingly useful for screening purposes.
ORIGINATORS should mark email addresses and phone numbers as whenever
possible and pass these TERRORIST IDENTIFIERS to NCTC to forward to the TSC for inclusion
in TSDB. are encouraged to provide all relevant and unclassi?ed information,
to include social media information when appropriate.
CONSTITUTIONALLY PROTECTED ACTIVITIES
1.19 First Amendment. First Amendment protected activity alone shall not be the basis for
nominating an individual for inclusion on the Terrorist Watchlist.l5 The following are
examples of protected Constitutional activities:
1.19.1 Free Speech. The exercise of free speech, guaranteed by the U.S. Constitution,
includes more than simply speaking on a controversial topic in the town square. It
includes such symbolic or other written, oral and expressive activities as carrying
placards in a parade, sending letters to a newspaper editor, wearing a tee shirt with a
political message, placing a bumper sticker critical of the President on one?s car, and
publishing books or articles. The common thread in these examples is conveying a
public message or an idea through words or deeds. Speech that may be repugnant to
ideas of the majority may still be protected by the U.S. Constitution. For the purpose of
this Watchlisting Guidance, the right of protected free speech under the U.S.
Constitution applies to U.S. PERSONS wherever they are located and to non~ U.S. PERSONS
located inside the United States. The right of protected free speech, however, is not
unlimited and may not extend to some lawless action.
1.19.2 Exercise of Religion. The free exercise of religion covers any form of worship of a
deity even forms that are not widely known or practiced as well as the right not to
worship any deity. Protected religious exercise also extends to dress that is worn or food
that is eaten for a religious purpose, attendance at a facility used for religious practice,
observance of the Sabbath, raising money for evangelical or missionary purposes, and
proselytizing.
1.19.3 Freedom of the Press. Freedom of the press includes such matters as reasonable
access to news-making events, the making of documentaries, and the posting of ?blogs.?
'5 The First Amendment does not apply to non?U.S. PERSONS outside the United States. Before submitting nominations,
NOMINATORS may consult with their Department or Agency counsel to determine whether a speci?c person is a U.S.
PERSON and whether the questioned activity is entitled to First Amendment protection.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Pagel 10
OR OFFICIAL USE SECURITY INFORMATION
without regard to the classi?cation of the source material from which it is drawn.
TERRORIST include those listed in Addendum names and aliases; dates of
birth; places of birth; unique identifying numbers; passport information; countries of origin
and nationality; physical identi?ers; known locations; photographs or renderings; ?ngerprints
or other biometric data; employment data; license plate numbers; and any other TERRORIST
IDENTIFIERS that ORIGINATORS speci?cally provide for passage to the TSC). For example,
email addresses and phone numbers are increasingly useful for screening purposes.
ORIGINATORS should mark email addresses and phone numbers as whenever
possible and pass these TERRORIST IDENTIFIERS to NCTC to forward to the TSC for inclusion
in TSDB. are encouraged to provide all relevant and unclassi?ed information,
to include social media information when appropriate.
CONSTITUTIONALLY PROTECTED ACTIVITIES
1.19 First Amendment. First Amendment protected activity alone shall not be the basis for
nominating an individual for inclusion on the Terrorist Watchlist.l5 The following are
examples of protected Constitutional activities:
1.19.1 Free Speech. The exercise of free speech, guaranteed by the U.S. Constitution,
includes more than simply speaking on a controversial topic in the town square. It
includes such symbolic or other written, oral and expressive activities as carrying
placards in a parade, sending letters to a newspaper editor, wearing a tee shirt with a
political message, placing a bumper sticker critical of the President on one?s car, and
publishing books or articles. The common thread in these examples is conveying a
public message or an idea through words or deeds. Speech that may be repugnant to
ideas of the majority may still be protected by the U.S. Constitution. For the purpose of
this Watchlisting Guidance, the right of protected free speech under the U.S.
Constitution applies to U.S. PERSONS wherever they are located and to non~ U.S. PERSONS
located inside the United States. The right of protected free speech, however, is not
unlimited and may not extend to some lawless action.
1.19.2 Exercise of Religion. The free exercise of religion covers any form of worship of a
deity even forms that are not widely known or practiced as well as the right not to
worship any deity. Protected religious exercise also extends to dress that is worn or food
that is eaten for a religious purpose, attendance at a facility used for religious practice,
observance of the Sabbath, raising money for evangelical or missionary purposes, and
proselytizing.
1.19.3 Freedom of the Press. Freedom of the press includes such matters as reasonable
access to news-making events, the making of documentaries, and the posting of ?blogs.?
'5 The First Amendment does not apply to non?U.S. PERSONS outside the United States. Before submitting nominations,
NOMINATORS may consult with their Department or Agency counsel to determine whether a speci?c person is a U.S.
PERSON and whether the questioned activity is entitled to First Amendment protection.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Pagel 10

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.20
IV.
1.21
1.22
1.19.4 Freedom of Peaceful Assembly. Freedom of peaceful assembly, often called the
right to freedom of association, includes gathering with others to protest government
action, or to rally or demonstrate in favor of, or in opposition to, a social cause. The
right to peaceful assembly includes more than just public demonstrations it includes,
as well, the posting of group websites on the 1nternet, recruiting others to a lawful cause,
marketing a message, and fundraising, which all are protected First Amendment
activities if they are conducted in support of an organizational, political, religious, or
social cause.
1.19.5 Petition the Government for of Grievances. The right to petition the
government for redress of grievances includes, for example, writing letters to Congress,
carrying a placard outside the city hall that delivers a political message, recruiting others
to one?s cause, and lobbying Congress or an Executive Agency for a particular result.
Equal Protection. The Equal Protection Clause of the US. Constitution provides in part that:
?No State shall make or enforce any law which shall deny to any person within its
jurisdiction the equal protection of the laws.? The US. Supreme Court has made it clear that
this applies as well to the of?cial acts of US. Government personnel. Nominations, therefore,
shall not be based solely on race, ethnicity, national origin, or religious affiliation. Any
activities relating to this Guidance that are based solely on such considerations are invidious
by de?nition, and therefore, unconstitutional.
WATCHLISTING POLICIES
Watchlisting Disclosures. The general policy of the US. Government is to neither con?rm
nor deny an individual?s watchlist status. In addition to the provisions in Addendum 8 to the
TSC MOU, which require NOMINATOR approval before TSDB information can be used in any
process that might result in public disclosure, the 2007 Memorandum of Understanding on
Terrorist Watchlist Redress Procedures MOU) '6 requires SCREENERS to contact the
TSC if it receives a request for information or records that might reveal an individual?s
watchlist status. Approval would also be required from any entity which provided
information used by a NOMINATOR during a nomination. Per the MOU, ORIGINATING
and NOMINATING AGENCIES are obligated to support SCREENER determinations both at the
administrative level and in litigation and provide appropriate information, including
unclassi?ed substitutes as necessary. TSC, in conjunction with NCTC, the NOMINATORS, and
the Department of Justice (DOJ), as appropriate, will ensure that representations regarding an
individual?s potential watchlist status are properly coordinated and approved.
Legal or Use Restrictions. Because information in the TSDB comes overwhelmingly from
intelligence sources and methods or sensitive law enforcement techniques, Paragraph 12 of
See Appendix 8, Redress MOU.
OR OFFICIAL USE SECURITY INFORMATION
Pagel 11
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.20
IV.
1.21
1.22
1.19.4 Freedom of Peaceful Assembly. Freedom of peaceful assembly, often called the
right to freedom of association, includes gathering with others to protest government
action, or to rally or demonstrate in favor of, or in opposition to, a social cause. The
right to peaceful assembly includes more than just public demonstrations it includes,
as well, the posting of group websites on the 1nternet, recruiting others to a lawful cause,
marketing a message, and fundraising, which all are protected First Amendment
activities if they are conducted in support of an organizational, political, religious, or
social cause.
1.19.5 Petition the Government for of Grievances. The right to petition the
government for redress of grievances includes, for example, writing letters to Congress,
carrying a placard outside the city hall that delivers a political message, recruiting others
to one?s cause, and lobbying Congress or an Executive Agency for a particular result.
Equal Protection. The Equal Protection Clause of the US. Constitution provides in part that:
?No State shall make or enforce any law which shall deny to any person within its
jurisdiction the equal protection of the laws.? The US. Supreme Court has made it clear that
this applies as well to the of?cial acts of US. Government personnel. Nominations, therefore,
shall not be based solely on race, ethnicity, national origin, or religious affiliation. Any
activities relating to this Guidance that are based solely on such considerations are invidious
by de?nition, and therefore, unconstitutional.
WATCHLISTING POLICIES
Watchlisting Disclosures. The general policy of the US. Government is to neither con?rm
nor deny an individual?s watchlist status. In addition to the provisions in Addendum 8 to the
TSC MOU, which require NOMINATOR approval before TSDB information can be used in any
process that might result in public disclosure, the 2007 Memorandum of Understanding on
Terrorist Watchlist Redress Procedures MOU) '6 requires SCREENERS to contact the
TSC if it receives a request for information or records that might reveal an individual?s
watchlist status. Approval would also be required from any entity which provided
information used by a NOMINATOR during a nomination. Per the MOU, ORIGINATING
and NOMINATING AGENCIES are obligated to support SCREENER determinations both at the
administrative level and in litigation and provide appropriate information, including
unclassi?ed substitutes as necessary. TSC, in conjunction with NCTC, the NOMINATORS, and
the Department of Justice (DOJ), as appropriate, will ensure that representations regarding an
individual?s potential watchlist status are properly coordinated and approved.
Legal or Use Restrictions. Because information in the TSDB comes overwhelmingly from
intelligence sources and methods or sensitive law enforcement techniques, Paragraph 12 of
See Appendix 8, Redress MOU.
OR OFFICIAL USE SECURITY INFORMATION
Pagel 11

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Addendum to the TSC requires that any recipient of information from the TSDB
seeking to use TERRORIST identity information in any legal or administrative process or
proceeding obtain NOMINATOR approval before doing so. Approval from the entity which
provided the information, if other than the NOMINATOR, is also required. Additionally,
information from Foreign Intelligence Surveillance Act (PISA) collections may only be used
in a proceeding with the advance authorization of the Attorney General. Therefore, any
SCREENER seeking to use TSDB information in any process or proceeding must contact TSC
so that TSC can assist in obtaining approval from the NOMINATOR, owner of the information,
or Attorney General, as required.
1.23 in addition to the foregoing restrictions, there are restrictions on sharing information with
foreign governments. Any TERRORIST IDENTIFIER (as described in Addendum to the TSC
MOU) will be deemed and shared with the watchlisting community and foreign
governments for watchlisting purposes pursuant to the terms of the TSC MOU. Accordingly,
NOMINATORS should include, as appropriate, TERRORIST IDENTIFIERS in documents that contain
non-releasable warnings a report is not releasable to countries), unless the
TERRORIST IDENTIFIERS are restricted by some other authority that limits dissemination. If U.S.
PERSON information is otherwise authorized for release to the foreign government, the non-
releasable warning is disabled to allow dissemination of the information.
V. WATCHLISTING STANDARD: IDENTIFYING AND SUBSTANTIVE
DEROGATORY CRITERIA
1.24 Before a KNOWN or is added to the Terrorist Watchlist, TSC reviews
the nomination to determine whether it meets the following minimum identifying criteria and
minimum substantive derogatory criteria for inclusion in the TSDB.
l.24.l Minimum Identifying Criteria. Each nomination must contain minimum
identifying criteria for inclusion into the TSDB. Without this minimum identifying data,
the nomination is not eligible for inclusion into the TSDB, or any of the
supported systems. Chapter 2 sets forth guidance regarding both the minimum
identifying biometric and biographic criteria for inclusion into the TSDB. Although
accepts records containing less than these minimum criteria, such records will not
be exported either to the TSDB for watchlisting or to the various supported systems used
by the SCREENERS absent an exception described in the Watchlisting Guidance.
1.24.2 Minimum Substantive Derogatory Criteria. In addition to the minimum
identifying criteria, nominations to the TSDB are accepted based on a REASONABLE
that the individual is a KNOWN or SUSPECFED derived from the
See Appendix 4, Addendum to the 13c: MOU.
OFFICIAL USE SECURITY INFORMATION
Page 1 l2
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Addendum to the TSC requires that any recipient of information from the TSDB
seeking to use TERRORIST identity information in any legal or administrative process or
proceeding obtain NOMINATOR approval before doing so. Approval from the entity which
provided the information, if other than the NOMINATOR, is also required. Additionally,
information from Foreign Intelligence Surveillance Act (PISA) collections may only be used
in a proceeding with the advance authorization of the Attorney General. Therefore, any
SCREENER seeking to use TSDB information in any process or proceeding must contact TSC
so that TSC can assist in obtaining approval from the NOMINATOR, owner of the information,
or Attorney General, as required.
1.23 in addition to the foregoing restrictions, there are restrictions on sharing information with
foreign governments. Any TERRORIST IDENTIFIER (as described in Addendum to the TSC
MOU) will be deemed and shared with the watchlisting community and foreign
governments for watchlisting purposes pursuant to the terms of the TSC MOU. Accordingly,
NOMINATORS should include, as appropriate, TERRORIST IDENTIFIERS in documents that contain
non-releasable warnings a report is not releasable to countries), unless the
TERRORIST IDENTIFIERS are restricted by some other authority that limits dissemination. If U.S.
PERSON information is otherwise authorized for release to the foreign government, the non-
releasable warning is disabled to allow dissemination of the information.
V. WATCHLISTING STANDARD: IDENTIFYING AND SUBSTANTIVE
DEROGATORY CRITERIA
1.24 Before a KNOWN or is added to the Terrorist Watchlist, TSC reviews
the nomination to determine whether it meets the following minimum identifying criteria and
minimum substantive derogatory criteria for inclusion in the TSDB.
l.24.l Minimum Identifying Criteria. Each nomination must contain minimum
identifying criteria for inclusion into the TSDB. Without this minimum identifying data,
the nomination is not eligible for inclusion into the TSDB, or any of the
supported systems. Chapter 2 sets forth guidance regarding both the minimum
identifying biometric and biographic criteria for inclusion into the TSDB. Although
accepts records containing less than these minimum criteria, such records will not
be exported either to the TSDB for watchlisting or to the various supported systems used
by the SCREENERS absent an exception described in the Watchlisting Guidance.
1.24.2 Minimum Substantive Derogatory Criteria. In addition to the minimum
identifying criteria, nominations to the TSDB are accepted based on a REASONABLE
that the individual is a KNOWN or SUSPECFED derived from the
See Appendix 4, Addendum to the 13c: MOU.
OFFICIAL USE SECURITY INFORMATION
Page 1 l2

UN OR OFFICIAL USE SECURITY INFORMATION
VI.
1.25
I .26
.27
totality of the information reviewed for nomination. '8 To demonstrate that the
nomination has suf?cient indieia of reliability to support this REASONABLE SUSPICION
determination, NOMINATING AGENCIES should implement processes designed to ensure
that nominations are free from errors, that recalled or revised information is reviewed
regularly, and that necessary corrections to nominations based on those
revisions/retractions are made. NOMINATING AGENCIES should, to the extent possible
given the nature of the reporting, verify the accuracy and reliability of the information
included in nominations. In some cases, the NOMINATING AGENCY may not be able to
evaluate the reliability of the information received; however, in such situations, the
NOMINATING AGENCY can ensure that the information provided is an accurate
representation of the information obtained. Chapter 3 sets forth further guidance
regarding the application of the REASONABLE SUSPICION standard to TSDB nominations.
WATCHLISTING PROCESS OVERVIEW
The authorities referenced in Section [1 of this Chapter created the framework for the
watchlisting enterprise by combining various functions of existing government entities and
joining them to new organizations with counterterrorism responsibilities. The resulting
watchlisting enterprise consists of ORIGINATORS, NOMINATORS, AGGREGATORS, SCREENERS
and encountering agencies that are supported by the community?wide collection, nomination,
and consolidation processes.
ORIGINATORS, NOMINATORS, AGGREGATORS, and SCREENERS. All Executive Departments
and Agencies have responsibility for collecting, collating, and sharing TERRORISM
INFORMATION to support the watchlisting process. They are called ORIGINATORS because they
initially collect and identify information supporting the conclusion that an individual is a
KNOWN or SUSPECTED TERRORIST. An ORIGINATOR is the Department or Agency that has
appropriate subject matter interest and classi?cation authority and collects TERRORISM
INFORMATION raw information) and disseminates it or TERRORIST IDENTIFIERS to other
US. Government entities via an intelligence report ?nished intelligence) or other
mechanism. In general, when an ORIGINATOR has identi?ed international TERRORISM
INFORMATION and determines that information should be provided to NCTC, the ORIGINATOR
takes on the NOMINATOR role. A NOMINATOR is a Federal Department or Agency that has
information to indicate that an individual meets the criteria for a KNOWN or SUSPECTED
TERRORIST and nominates that individual to TIDE and the TSDB based on information that
originated with that Agency.
While all NOMINATORS have the duty of upholding informational standards, the NCTC and
TSC are responsible for ensuring data quality and the integrity of their respective
repositories. and TSC are themselves potential NOMINATORS. from the
'8 Please note that there are also certain exceptions to the minimum biographic information and minimum substantive
derogatory criteria required for Terrorist Watchlist nominations that support immigration and visa screening activities
conducted by DHS and DOS. See Chapter 2, Section Ill and Chapter 3, Section V.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Pagel l3
UN OR OFFICIAL USE SECURITY INFORMATION
VI.
1.25
I .26
.27
totality of the information reviewed for nomination. '8 To demonstrate that the
nomination has suf?cient indieia of reliability to support this REASONABLE SUSPICION
determination, NOMINATING AGENCIES should implement processes designed to ensure
that nominations are free from errors, that recalled or revised information is reviewed
regularly, and that necessary corrections to nominations based on those
revisions/retractions are made. NOMINATING AGENCIES should, to the extent possible
given the nature of the reporting, verify the accuracy and reliability of the information
included in nominations. In some cases, the NOMINATING AGENCY may not be able to
evaluate the reliability of the information received; however, in such situations, the
NOMINATING AGENCY can ensure that the information provided is an accurate
representation of the information obtained. Chapter 3 sets forth further guidance
regarding the application of the REASONABLE SUSPICION standard to TSDB nominations.
WATCHLISTING PROCESS OVERVIEW
The authorities referenced in Section [1 of this Chapter created the framework for the
watchlisting enterprise by combining various functions of existing government entities and
joining them to new organizations with counterterrorism responsibilities. The resulting
watchlisting enterprise consists of ORIGINATORS, NOMINATORS, AGGREGATORS, SCREENERS
and encountering agencies that are supported by the community?wide collection, nomination,
and consolidation processes.
ORIGINATORS, NOMINATORS, AGGREGATORS, and SCREENERS. All Executive Departments
and Agencies have responsibility for collecting, collating, and sharing TERRORISM
INFORMATION to support the watchlisting process. They are called ORIGINATORS because they
initially collect and identify information supporting the conclusion that an individual is a
KNOWN or SUSPECTED TERRORIST. An ORIGINATOR is the Department or Agency that has
appropriate subject matter interest and classi?cation authority and collects TERRORISM
INFORMATION raw information) and disseminates it or TERRORIST IDENTIFIERS to other
US. Government entities via an intelligence report ?nished intelligence) or other
mechanism. In general, when an ORIGINATOR has identi?ed international TERRORISM
INFORMATION and determines that information should be provided to NCTC, the ORIGINATOR
takes on the NOMINATOR role. A NOMINATOR is a Federal Department or Agency that has
information to indicate that an individual meets the criteria for a KNOWN or SUSPECTED
TERRORIST and nominates that individual to TIDE and the TSDB based on information that
originated with that Agency.
While all NOMINATORS have the duty of upholding informational standards, the NCTC and
TSC are responsible for ensuring data quality and the integrity of their respective
repositories. and TSC are themselves potential NOMINATORS. from the
'8 Please note that there are also certain exceptions to the minimum biographic information and minimum substantive
derogatory criteria required for Terrorist Watchlist nominations that support immigration and visa screening activities
conducted by DHS and DOS. See Chapter 2, Section Ill and Chapter 3, Section V.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Pagel l3

OR OFFICIAL USE SECURITY INFORMATION
1.28
.29
1.30
l.3l
NCTC may discover an individual who is eligible for watchlisting while reviewing all?source
information. In these cases, NCTC will request that the ORIGINATOR submit a
nomination for inclusion into or, on a limited basis or during exigent circumstances,
NCTC may update TIDE directly with a disseminated report and notice to the
In instances where disseminated reporting is used to enhance NCTC
will provide notice back to the collecting agency via TIDE. TSC may also nominate
TERRORISM INFORMATION received pursuant to TERRORISM screening conducted by foreign
governments.
NCTC and are responsible for reviewing both newly nominated individuals, as well as
subsets of existing records, to determine if additional and/or enhancement (research) is
required to locate missing information critical to the watchlisting process. In some cases, this
will require research to locate additional DEROGATORY INFORMATION to meet the minimum
substantive derogatory criteria for watchlisting. In other cases, this will require research to
locate additional biographic or biometric identifiers, in order to provide a comprehensive
record maximizing the probability of con?rming a POSITIVE MATCH to an identity contained in
the TSDB.
AGGREGATORS are those who receive and hold TERRORISM INFORMATION and certain other
INFORMATION they are authorized to receive and retain. For example, two of
main statutory missions are to serve as the (1) central and shared knowledge bank on
KNOWN or SUSPECTED TERRORISTS and (2) primary organization in the US. Government for
analyzing and integrating all intelligence information possessed or acquired by the US.
Government pertaining to TERRORISM and counterterrorism. '9
TSC takes on the role of an AGGREGATOR when a KNOWN or SUSPECTEI) TERRORIST is
encountered and the individual?s record is enhanced or updated with
information. As noted in Paragraphs and 1.7, the TSC manages the watchlisting process
and plays a key role in helping Departments and Agencies determine whether an ENCOUNTER
with a member of the public is one with a KNOWN or SUSPECTED TERRORIST. Additional
TERRORISM INFORMATION or TERRORIST IDENTIFIERS are generated during ENCOUNTERS and the
Encounter Management Application uses that information to update records of
KNOWN or SUSPECTED TERRORISTS.
SCREENERS vet against the TSDB to determine if an individual is a possible match to a KNOWN
or SUSPECTED in the TSDB. SCREENERS can include federal, state, local, tribal,
territorial, or foreign governments and certain private entities. Screening Of?cials include
homeland security of?cers, consular affairs of?cers, transportation safety personnel, and
of?cials of foreign governments with whom the United States has entered into a TERRORISM
SCREENING INFORMATION sharing agreement pursuant to HSPD-6. Certain Departments and
Agencies have components which perform both screening and law enforcement duties. If a
?9 See 50 use. ?404o.
2? EMA is an application used by the TSC to administer ENCOUNTER information.
OR OFFICIAL USE SECURITY INFORMATION
Page I I4
OR OFFICIAL USE SECURITY INFORMATION
1.28
.29
1.30
l.3l
NCTC may discover an individual who is eligible for watchlisting while reviewing all?source
information. In these cases, NCTC will request that the ORIGINATOR submit a
nomination for inclusion into or, on a limited basis or during exigent circumstances,
NCTC may update TIDE directly with a disseminated report and notice to the
In instances where disseminated reporting is used to enhance NCTC
will provide notice back to the collecting agency via TIDE. TSC may also nominate
TERRORISM INFORMATION received pursuant to TERRORISM screening conducted by foreign
governments.
NCTC and are responsible for reviewing both newly nominated individuals, as well as
subsets of existing records, to determine if additional and/or enhancement (research) is
required to locate missing information critical to the watchlisting process. In some cases, this
will require research to locate additional DEROGATORY INFORMATION to meet the minimum
substantive derogatory criteria for watchlisting. In other cases, this will require research to
locate additional biographic or biometric identifiers, in order to provide a comprehensive
record maximizing the probability of con?rming a POSITIVE MATCH to an identity contained in
the TSDB.
AGGREGATORS are those who receive and hold TERRORISM INFORMATION and certain other
INFORMATION they are authorized to receive and retain. For example, two of
main statutory missions are to serve as the (1) central and shared knowledge bank on
KNOWN or SUSPECTED TERRORISTS and (2) primary organization in the US. Government for
analyzing and integrating all intelligence information possessed or acquired by the US.
Government pertaining to TERRORISM and counterterrorism. '9
TSC takes on the role of an AGGREGATOR when a KNOWN or SUSPECTEI) TERRORIST is
encountered and the individual?s record is enhanced or updated with
information. As noted in Paragraphs and 1.7, the TSC manages the watchlisting process
and plays a key role in helping Departments and Agencies determine whether an ENCOUNTER
with a member of the public is one with a KNOWN or SUSPECTED TERRORIST. Additional
TERRORISM INFORMATION or TERRORIST IDENTIFIERS are generated during ENCOUNTERS and the
Encounter Management Application uses that information to update records of
KNOWN or SUSPECTED TERRORISTS.
SCREENERS vet against the TSDB to determine if an individual is a possible match to a KNOWN
or SUSPECTED in the TSDB. SCREENERS can include federal, state, local, tribal,
territorial, or foreign governments and certain private entities. Screening Of?cials include
homeland security of?cers, consular affairs of?cers, transportation safety personnel, and
of?cials of foreign governments with whom the United States has entered into a TERRORISM
SCREENING INFORMATION sharing agreement pursuant to HSPD-6. Certain Departments and
Agencies have components which perform both screening and law enforcement duties. If a
?9 See 50 use. ?404o.
2? EMA is an application used by the TSC to administer ENCOUNTER information.
OR OFFICIAL USE SECURITY INFORMATION
Page I I4
OR OFFICIAL USE SECURITY INFORMATION
1.32
SCREENER believes an individual may be on the Watchlist, the screener contacts the
Terrorist Screening Operations Center (TSOC). The TSOC will determine whether the
individual the SCREENER has encountered is, in fact, a POSITIVE MATCH to the individual who
is on the Terrorist Watchlist. The TSOC may also notify the Counterterrorism Division
(CTD) that there has been a positive ENCOUNTER with a watchlisted subject. Terrorist
Screening Operations Unit (TSOU) coordinates the appropriate operational response to the
ENCOUNTER. Based on the TERRORISM INFORMATION made available by the ORIGINATING
AGENCY, the SCREENER will take action based upon its speci?c authorities requiring
additional screening at an airport checkpoint, denying a visa application, determining
admissibility into the United States) and follow appropriate ENCOUNTER procedures, as set
forth in Chapter 5.
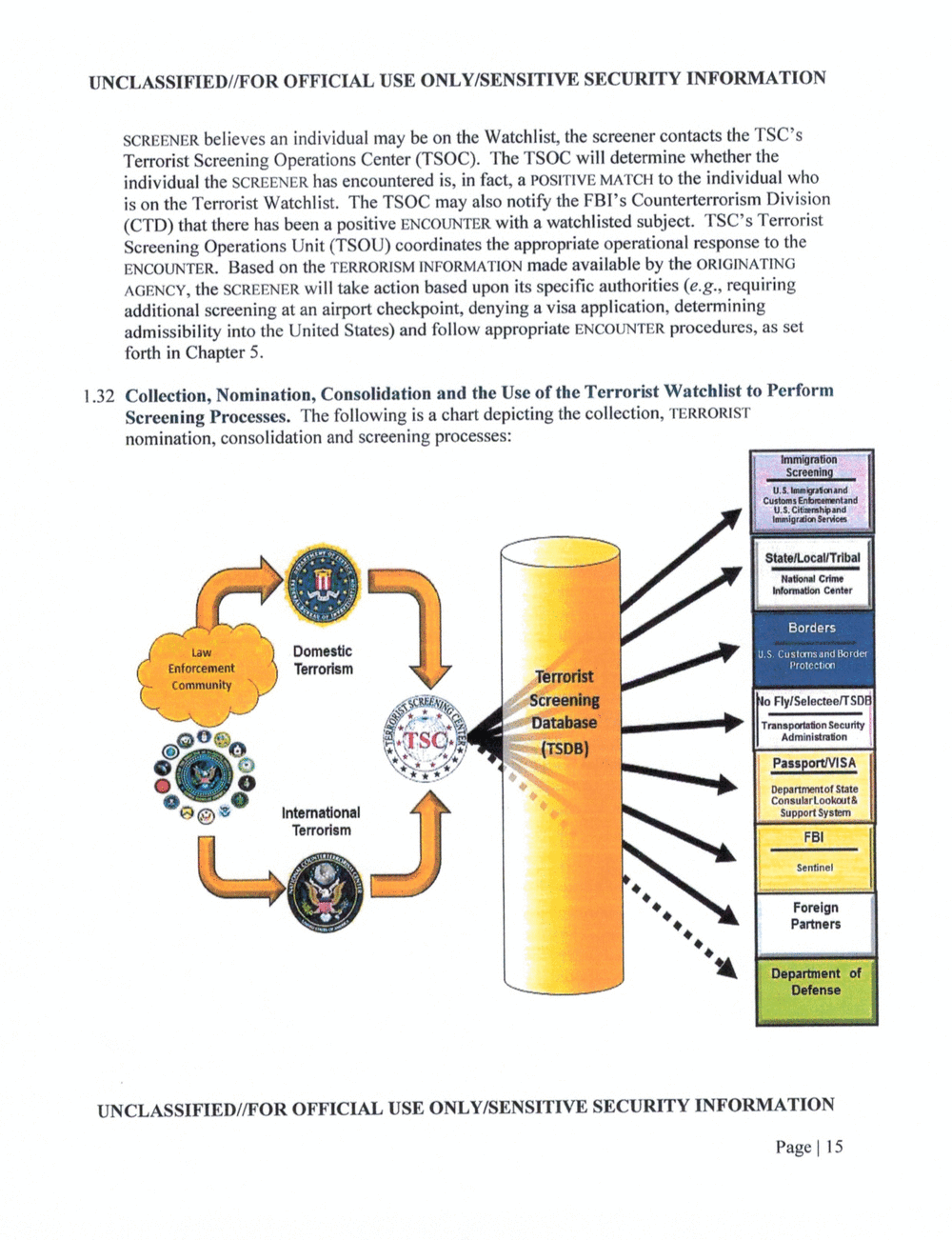
Collection, Nomination, Consolidation and the Use of the Terrorist Watchlist to Perform
Screening Processes. The following is a chart depicting the collection,
nomination, consolidation and screening processes:
Borders
Domestic
Terrorlem
nulli?
l'ulv
F:uupuh&m5umnwi
SA
Departmental sme
Coneulertookwt?
- Support Syehm
Pee:
lnteme?donel
Terrorlem
FBI
Sentinel
OR OFFICIAL USE SECURITY INFORMATION
Pagel l5
OR OFFICIAL USE SECURITY INFORMATION
1.32
SCREENER believes an individual may be on the Watchlist, the screener contacts the
Terrorist Screening Operations Center (TSOC). The TSOC will determine whether the
individual the SCREENER has encountered is, in fact, a POSITIVE MATCH to the individual who
is on the Terrorist Watchlist. The TSOC may also notify the Counterterrorism Division
(CTD) that there has been a positive ENCOUNTER with a watchlisted subject. Terrorist
Screening Operations Unit (TSOU) coordinates the appropriate operational response to the
ENCOUNTER. Based on the TERRORISM INFORMATION made available by the ORIGINATING
AGENCY, the SCREENER will take action based upon its speci?c authorities requiring
additional screening at an airport checkpoint, denying a visa application, determining
admissibility into the United States) and follow appropriate ENCOUNTER procedures, as set
forth in Chapter 5.
Collection, Nomination, Consolidation and the Use of the Terrorist Watchlist to Perform
Screening Processes. The following is a chart depicting the collection,
nomination, consolidation and screening processes:
Borders
Domestic
Terrorlem
nulli?
l'ulv
F:uupuh&m5umnwi
SA
Departmental sme
Coneulertookwt?
- Support Syehm
Pee:
lnteme?donel
Terrorlem
FBI
Sentinel
OR OFFICIAL USE SECURITY INFORMATION
Pagel l5

OR OFFICIAL USE SECURITY INFORMATION
1.33 The arrows fade inside the TSDB cylinder because not every nomination from NCTC (for
international TERRORISM) or the FBI (for domestic TERRORISM) is exported from the TSDB to
SCREENERS (represented by the multi-colored blocks at the far right of the chart).21 For
example, certain categories of individuals that do not meet the minimum identifying criteria
(see Chapter 2, Section II) or the REASONABLE SUSPICION standard (see Chapter 3, Section II)
can be watchlisted to support immigration and visa screening activities by DHS and DOS (see
Chapter 3, Section V) but are not exported to state/local/tribal SCREENERS or foreign partners.
Similarly, when ORIGINATORS provide FRAGMENTARY INFORMATION to NCTC for inclusion in
TIDE, such information will not be exported from TIDE to the TSDB, unless the NOMINATING
AGENCY believes there is REASONABLE to believe that the individual is a KNOWN or
SUSPECTED TERRORIST. FRAGMENTARY INFORMATION is provided to NCTC where it can be
further analyzed, connected to existing information, and added to TIDE for export to TSDB
because NCTC, and not individual ORIGINATORS, has access to all the information available to
the US. Government on a KNOWN or TERRORIST.
VII. ROLES AND RESPONSIBILITES FOR THE WATCHLISTING AND SCREENING
COMMUNITY
1.34 Delineation of roles and responsibilities of NOMINATING AGENCIES, SCREENERS, NCTC, and
the TSC is critical to provide for an efTective and efficient integrated Terrorist Watchlist
enterprise. While HSPD-6 describes the broad mandate of developing an integrated watchlist
system, and the TSC MOU provides a level of detail needed to ful?ll that mandate, further
clari?cation is required to ensure there are neither gaps in the nomination process, nor
wasteful redundancies.
1.35 Pursuant to Departments and Agencies in the Executive Branch are required, to the
extent permitted by law, to provide TERRORIST INFORMATION to NCTC. This process will be
accomplished either through direct nomination to NCTC, or through a speci?c component
designated by a Federal Department or Agency head for doing so all DOJ components
are directed to nominate through the DHS Intelligence and Analysis has oversight
responsibility for all DHS nominations). Except as detailed in the sections applicable to
expedited nominations (see Paragraphs 1.58 and 1.59), NOMINATING AGENCIES will endeavor
to provide comprehensive nominations and include the maximum amount of identifying and
DEROGATORY INFORMATION.22 NOMINATING DEPARTMENTS AND AGENCIES should prioritize
2' The Terrorist Screening Database Annex to the FBI Memorandum of Understanding with Department of Defense
(DOD), signed February 22, 2012, established as a screening agency customer of the TSC. The dashed line in the
latter chart represents that DOD is ?nalizing procedures to receive and use information from the TSDB for its screening
recesses.
g2 In May 2010, the Deputies asked that NOMINATING AGENCIES ?ensure that nominations are comprehensive and
include the maximum amount of identifying and DEROGATORY In 2012, the Interagency Policy
Committee in coordination with NOMINATORS, SCREENERS, NCTC and TSC, developed a prioritized list of data
identi?ers that are critical to screening and identity resolution activities. This Identity Resolution and Enhancement
Tiers document is available on Watchlisting Community of Interest portal on the Joint Worldwide Intelligence
Communications System (.IWICS).
OR OFFICIAL USE SECURITY INFORMATION
Page 16
OR OFFICIAL USE SECURITY INFORMATION
1.33 The arrows fade inside the TSDB cylinder because not every nomination from NCTC (for
international TERRORISM) or the FBI (for domestic TERRORISM) is exported from the TSDB to
SCREENERS (represented by the multi-colored blocks at the far right of the chart).21 For
example, certain categories of individuals that do not meet the minimum identifying criteria
(see Chapter 2, Section II) or the REASONABLE SUSPICION standard (see Chapter 3, Section II)
can be watchlisted to support immigration and visa screening activities by DHS and DOS (see
Chapter 3, Section V) but are not exported to state/local/tribal SCREENERS or foreign partners.
Similarly, when ORIGINATORS provide FRAGMENTARY INFORMATION to NCTC for inclusion in
TIDE, such information will not be exported from TIDE to the TSDB, unless the NOMINATING
AGENCY believes there is REASONABLE to believe that the individual is a KNOWN or
SUSPECTED TERRORIST. FRAGMENTARY INFORMATION is provided to NCTC where it can be
further analyzed, connected to existing information, and added to TIDE for export to TSDB
because NCTC, and not individual ORIGINATORS, has access to all the information available to
the US. Government on a KNOWN or TERRORIST.
VII. ROLES AND RESPONSIBILITES FOR THE WATCHLISTING AND SCREENING
COMMUNITY
1.34 Delineation of roles and responsibilities of NOMINATING AGENCIES, SCREENERS, NCTC, and
the TSC is critical to provide for an efTective and efficient integrated Terrorist Watchlist
enterprise. While HSPD-6 describes the broad mandate of developing an integrated watchlist
system, and the TSC MOU provides a level of detail needed to ful?ll that mandate, further
clari?cation is required to ensure there are neither gaps in the nomination process, nor
wasteful redundancies.
1.35 Pursuant to Departments and Agencies in the Executive Branch are required, to the
extent permitted by law, to provide TERRORIST INFORMATION to NCTC. This process will be
accomplished either through direct nomination to NCTC, or through a speci?c component
designated by a Federal Department or Agency head for doing so all DOJ components
are directed to nominate through the DHS Intelligence and Analysis has oversight
responsibility for all DHS nominations). Except as detailed in the sections applicable to
expedited nominations (see Paragraphs 1.58 and 1.59), NOMINATING AGENCIES will endeavor
to provide comprehensive nominations and include the maximum amount of identifying and
DEROGATORY INFORMATION.22 NOMINATING DEPARTMENTS AND AGENCIES should prioritize
2' The Terrorist Screening Database Annex to the FBI Memorandum of Understanding with Department of Defense
(DOD), signed February 22, 2012, established as a screening agency customer of the TSC. The dashed line in the
latter chart represents that DOD is ?nalizing procedures to receive and use information from the TSDB for its screening
recesses.
g2 In May 2010, the Deputies asked that NOMINATING AGENCIES ?ensure that nominations are comprehensive and
include the maximum amount of identifying and DEROGATORY In 2012, the Interagency Policy
Committee in coordination with NOMINATORS, SCREENERS, NCTC and TSC, developed a prioritized list of data
identi?ers that are critical to screening and identity resolution activities. This Identity Resolution and Enhancement
Tiers document is available on Watchlisting Community of Interest portal on the Joint Worldwide Intelligence
Communications System (.IWICS).
OR OFFICIAL USE SECURITY INFORMATION
Page 16

OR OFFICIAL USE SECURITY INFORMATION
1.36
1.37
1.38
L39
1 .40
the identi?cation of new KNOWN or SUSPECTED TERRORISTS who meet the REASONABLE
SUSPICION standard, along with the identifying and DEROGATORY INFORMATION most useful to
watchlisting, and screening effort, as well as assisting in identity resolution.
Each Department or Agency that nominates a KNOWN or SUSPECTED TERRORIST to NCTC for
watchlisting is under a continuing obligation to provide NCTC with newly identi?ed
DEROGATORY INFORMATION or exculpatory information obtained by that Department or
Agency. Each Department or Agency also has the responsibility to provide NCTC with newly
identi?ed identifying and DEROGATORY INFORMATION obtained from their Department or
Agency, regardless if they were the original NOMINATING AGENCY.
With the noted exception of the Visa Viper Program, Departments and Agencies should not
nominate KNOWN or SUSPECTED TERRORISTS to based on information that they do not
originate without first coordinating with the ORIGINATOR.
QUALITY CONTROL MEASURES
In order to produce and maintain the most reliable and accurate information in TIDE, TSDB,
and screening databases, quality control is considered a responsibility of all entities.
NOMINATING DEPARTMENTS AND AGENCIES must establish and maintain processes, including
appropriate training and guidance, to ensure information transmitted to NCTC is consistent
with the source of the information.
HSPD-6 Requirements. HSPD-6 requires the TSC to maintain thorough, accurate, and
current information concerning KNOWN or SUSPECTED TERRORISTS. For watchlisting purposes,
?current? means information that the NOMINATING AGENCY reasonably believes is valid and
accurate. The requirement that information be current does not necessarily preclude
information that is several years old from being included in the TSDB if there is no reason to
believe the information may have changed g, information regarding an individual?s date of
birth or TERRORIST ACTIVITY was collected 20 years ago but has not been superseded by
additional information is still relevant). NOMINATORS should consider the date of the
DEROGATORY INFORMATION in the context of analyzing the overall quality of the data, as well
as the severity of the threat, to determine whether the individual warrants watchlisting. The
date of the DEROGATORY INFORMATION may refer to both the date the information is collected
(such as a report that was collected 50 years ago) as well as the date of the information that is
referenced in the reporting (such as a recent report that references an event that occurred 50
years ago).
TSC MOU Obligations. Paragraph 15 of the TSC MOU provides that the TSC ?will
determine, according to criteria established jointly with the entity responsible for each
supported system, which supported screening processes will query that entry in the
consolidated TERRORIST screening database.? Pursuant to that paragraph, the TSC is required
to ?make these determinations based on criteria and procedures developed in coordination
with the Parties to this Memorandum and in consultation with the heads of appropriate Federal
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page] l7
OR OFFICIAL USE SECURITY INFORMATION
1.36
1.37
1.38
L39
1 .40
the identi?cation of new KNOWN or SUSPECTED TERRORISTS who meet the REASONABLE
SUSPICION standard, along with the identifying and DEROGATORY INFORMATION most useful to
watchlisting, and screening effort, as well as assisting in identity resolution.
Each Department or Agency that nominates a KNOWN or SUSPECTED TERRORIST to NCTC for
watchlisting is under a continuing obligation to provide NCTC with newly identi?ed
DEROGATORY INFORMATION or exculpatory information obtained by that Department or
Agency. Each Department or Agency also has the responsibility to provide NCTC with newly
identi?ed identifying and DEROGATORY INFORMATION obtained from their Department or
Agency, regardless if they were the original NOMINATING AGENCY.
With the noted exception of the Visa Viper Program, Departments and Agencies should not
nominate KNOWN or SUSPECTED TERRORISTS to based on information that they do not
originate without first coordinating with the ORIGINATOR.
QUALITY CONTROL MEASURES
In order to produce and maintain the most reliable and accurate information in TIDE, TSDB,
and screening databases, quality control is considered a responsibility of all entities.
NOMINATING DEPARTMENTS AND AGENCIES must establish and maintain processes, including
appropriate training and guidance, to ensure information transmitted to NCTC is consistent
with the source of the information.
HSPD-6 Requirements. HSPD-6 requires the TSC to maintain thorough, accurate, and
current information concerning KNOWN or SUSPECTED TERRORISTS. For watchlisting purposes,
?current? means information that the NOMINATING AGENCY reasonably believes is valid and
accurate. The requirement that information be current does not necessarily preclude
information that is several years old from being included in the TSDB if there is no reason to
believe the information may have changed g, information regarding an individual?s date of
birth or TERRORIST ACTIVITY was collected 20 years ago but has not been superseded by
additional information is still relevant). NOMINATORS should consider the date of the
DEROGATORY INFORMATION in the context of analyzing the overall quality of the data, as well
as the severity of the threat, to determine whether the individual warrants watchlisting. The
date of the DEROGATORY INFORMATION may refer to both the date the information is collected
(such as a report that was collected 50 years ago) as well as the date of the information that is
referenced in the reporting (such as a recent report that references an event that occurred 50
years ago).
TSC MOU Obligations. Paragraph 15 of the TSC MOU provides that the TSC ?will
determine, according to criteria established jointly with the entity responsible for each
supported system, which supported screening processes will query that entry in the
consolidated TERRORIST screening database.? Pursuant to that paragraph, the TSC is required
to ?make these determinations based on criteria and procedures developed in coordination
with the Parties to this Memorandum and in consultation with the heads of appropriate Federal
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page] l7

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Departments and Agencies based on factors, including but not limited to, the following:
1.40.] the nature of the person?s association with
1.40.2 the quality of the data, including credibility, reliability, and extent of
corroboration; and,
1.40.3 the extent of uniquely identifying data. . . 3?23
1.41 Provide Guidance and Training. Each Agency will provide guidance on the watchlisting
business process. will receive periodic refresher training, as needed.
1.42 AGENCY Procedures. Each NOMINATOR providing international TERRORIST
watchlisting nominations to NCTC is responsible for the accuracy of its information and has a
continuing responsibility to notify NCTC 01' any changes that affect the validity or reliability
ofsuch information.24 NCTC will review each nomination for TERRORIST
watchlisting prior to its inclusion into and its export to the TSDB.
1.43 Each NOMINATING AGENCY should implement processes designed to ensure that nominations
are free from errors, that recalled or revised information is reviewed regularly, and that
necessary corrections to nominations based on those revisions/retractions are made.
NOMINATING AGENCIES should, to the extent possible given the nature of the reporting, verify
the accuracy and reliability of the information included in nominations. The following
represents the type of processes that each NOMINATING AGENCY shall develop that are tailored
to each Agency?s particular mission and operational environment:
1.43.1 Develop Adequate Factual Predicate. Each NOMINATING AGENCY will seek to
obtain as much INFORMATION and identifying information as practicable
concerning the KNOWN or SUSPECTED who is being nominated.
1.43.2 Provide Guidance and Training. Each NOMINATING AGENCY will provide guidance
on the TERRORIST watchlisting nomination process and ensure that involved in
the nomination process are trained on a periodic basis.
1.43.3 Require Quality Assurance Review. Each NOMINATING AGENCY will use a quality
assurance process to review nominations for accuracy prior to forwarding the
information to NCTC.
1.43.4 Heightened Review for us. PERSONS. The nominations of US. PERSONS require
23 See Appendix 3, TSC MOU.
"4 PUREI..Y DOMESTIC TERRORISM INFORMATION is provided directly subject to the same
conditions applicable to the nomination procedures for those associated with international TERRORISM.
UN OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
Pagel 18
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Departments and Agencies based on factors, including but not limited to, the following:
1.40.] the nature of the person?s association with
1.40.2 the quality of the data, including credibility, reliability, and extent of
corroboration; and,
1.40.3 the extent of uniquely identifying data. . . 3?23
1.41 Provide Guidance and Training. Each Agency will provide guidance on the watchlisting
business process. will receive periodic refresher training, as needed.
1.42 AGENCY Procedures. Each NOMINATOR providing international TERRORIST
watchlisting nominations to NCTC is responsible for the accuracy of its information and has a
continuing responsibility to notify NCTC 01' any changes that affect the validity or reliability
ofsuch information.24 NCTC will review each nomination for TERRORIST
watchlisting prior to its inclusion into and its export to the TSDB.
1.43 Each NOMINATING AGENCY should implement processes designed to ensure that nominations
are free from errors, that recalled or revised information is reviewed regularly, and that
necessary corrections to nominations based on those revisions/retractions are made.
NOMINATING AGENCIES should, to the extent possible given the nature of the reporting, verify
the accuracy and reliability of the information included in nominations. The following
represents the type of processes that each NOMINATING AGENCY shall develop that are tailored
to each Agency?s particular mission and operational environment:
1.43.1 Develop Adequate Factual Predicate. Each NOMINATING AGENCY will seek to
obtain as much INFORMATION and identifying information as practicable
concerning the KNOWN or SUSPECTED who is being nominated.
1.43.2 Provide Guidance and Training. Each NOMINATING AGENCY will provide guidance
on the TERRORIST watchlisting nomination process and ensure that involved in
the nomination process are trained on a periodic basis.
1.43.3 Require Quality Assurance Review. Each NOMINATING AGENCY will use a quality
assurance process to review nominations for accuracy prior to forwarding the
information to NCTC.
1.43.4 Heightened Review for us. PERSONS. The nominations of US. PERSONS require
23 See Appendix 3, TSC MOU.
"4 PUREI..Y DOMESTIC TERRORISM INFORMATION is provided directly subject to the same
conditions applicable to the nomination procedures for those associated with international TERRORISM.
UN OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
Pagel 18

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
special considerations and procedures.25 See Paragraph 3.15.
1.43.5 U.S. PERSON Determinations. NOMINATORS must take reasonable steps to determine
whether an individual is a US. PERSON.
1.43.6 U.S. PERSON Review and Confirmation. Nominations of PERSONS to the
Terrorist Watchlist shall be reviewed by the NOMINATING legal counsel or a
designated reviewer to con?rm that the REASONABLE SUSPICION standard has been met
or that the nomination meets an exception to the REASONABLE SUSPICION standard, and
to ensure that the nomination conforms to Agency specific U.S. PERSON authorities and
guidelines.
1.43.7 Reliability and Accuracy Limitations. Nominations will include any limitations on
the reliability or accuracy of the information.
1.43.8 Periodic Reviews. The AGENCY will conduct periodic reviews of their
nominations of US. PERSONS to the Terrorist Watchlist, at minimum on an annual basis,
when there is no corresponding FBI investigation to ensure that the US. PERSON
continues to meet watchlisting criteria.
1.43.9 Redress Procedures. As per the establishment of a formal watchlist redress process
(see Chapter 1, Section X1), entities involved in the watchlisting process shall establish
internal reviews and redress procedures.
1.44 Each AGENCY will have procedures that facilitate the prevention, identification,
and correction of any errors in information that is shared as part of the watchlisting process.
Procedures will include the review of retractions and/or corrections of information that may
have been used to support a nomination. In cases where a retraction or other information has
become available, the NOMINATING AGENCY will send a watchlist removal request or
modi?cation, as appropriate, to NCT C. Each NOMINATING AGENCY must provide notice of
any errors or outdated information to NCTC immediately unless there is an articulated reason
why such noti?cation could not be made immediately. NCTC will process and transmit to
TSC such corrections upon receipt.
1.45 NCTC Review. in addition to review by NCTC NCTC will employ a quality
control process to ensure that all standards and appropriate procedures have been employed,
the data is accurate, and the presentation of the material is clear, concise, and complies with
established de?nitions and conventions. NCTC must also have processes and procedures in
place to ensure the information documented in and provided to the TSC is accurately
transcribed. NCTC shall ensure there is a process in place for review and/or auditing of
records.
See Executive Order 12333, as amended, and 5 use. 552a(e)(7).
OFFICIAL USE SECURITY INFORMATION
Page 19
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
special considerations and procedures.25 See Paragraph 3.15.
1.43.5 U.S. PERSON Determinations. NOMINATORS must take reasonable steps to determine
whether an individual is a US. PERSON.
1.43.6 U.S. PERSON Review and Confirmation. Nominations of PERSONS to the
Terrorist Watchlist shall be reviewed by the NOMINATING legal counsel or a
designated reviewer to con?rm that the REASONABLE SUSPICION standard has been met
or that the nomination meets an exception to the REASONABLE SUSPICION standard, and
to ensure that the nomination conforms to Agency specific U.S. PERSON authorities and
guidelines.
1.43.7 Reliability and Accuracy Limitations. Nominations will include any limitations on
the reliability or accuracy of the information.
1.43.8 Periodic Reviews. The AGENCY will conduct periodic reviews of their
nominations of US. PERSONS to the Terrorist Watchlist, at minimum on an annual basis,
when there is no corresponding FBI investigation to ensure that the US. PERSON
continues to meet watchlisting criteria.
1.43.9 Redress Procedures. As per the establishment of a formal watchlist redress process
(see Chapter 1, Section X1), entities involved in the watchlisting process shall establish
internal reviews and redress procedures.
1.44 Each AGENCY will have procedures that facilitate the prevention, identification,
and correction of any errors in information that is shared as part of the watchlisting process.
Procedures will include the review of retractions and/or corrections of information that may
have been used to support a nomination. In cases where a retraction or other information has
become available, the NOMINATING AGENCY will send a watchlist removal request or
modi?cation, as appropriate, to NCT C. Each NOMINATING AGENCY must provide notice of
any errors or outdated information to NCTC immediately unless there is an articulated reason
why such noti?cation could not be made immediately. NCTC will process and transmit to
TSC such corrections upon receipt.
1.45 NCTC Review. in addition to review by NCTC NCTC will employ a quality
control process to ensure that all standards and appropriate procedures have been employed,
the data is accurate, and the presentation of the material is clear, concise, and complies with
established de?nitions and conventions. NCTC must also have processes and procedures in
place to ensure the information documented in and provided to the TSC is accurately
transcribed. NCTC shall ensure there is a process in place for review and/or auditing of
records.
See Executive Order 12333, as amended, and 5 use. 552a(e)(7).
OFFICIAL USE SECURITY INFORMATION
Page 19

OR OFFICIAL USE SECURITY INFORMATION
I .46
IX.
1.47
1.48
TSC Review. TSC personnel will review the nominations received as described in Paragraph
1.56. TSC personnel evaluate whether nominations meet watchlisting standards and weigh, as
appropriate, all-source analysis before accepting or rejecting a nomination. The TSC has a
critical role to play in quality control, as the TSC review is the last step before any record
(including a biometric nomination where no name is available) is sent to various screening
systems. As with NCTC, the TSC should ensure there is a process in place for review and/or
auditing of TSC nominations and TSC records.
NOMINATION PROCEDURES
Distinctions between U.S. PERSONS under Executive Order 12333 and Aliens under the
Immigration and Nationality Act. This Watchlisting Guidance generally adopts the
de?nition of U.S. PERSON from Executive Order 12333 (as amended) for nomination
procedures. Executive Order 12333 defines a U.S. PERSON as United States citizen, an alien
known by the intelligence clement concerned to be a permanent resident alien, an
unincorporated association substantially composed of United States citizens or permanent
resident aliens, or a corporation incorporated in the United States, except for a corporation
directed or controlled by a foreign government or governments.? The Watchlisting Guidance
also contains certain exceptions to the minimum substantive derogatory standards for
TERRORIST watchlisting that support immigration and visa screening activities by the DHS and
DOS to determine whether ineligibilities exist for admission to the United States or visa
adjudication pursuant to the Immigration and Nationality Act (INA). Because the INA
defines ?aliens? as any person not a citizen or national of the United States, the INA
admissibility provisions also apply to Lawful Permanent Residents (LPRs), in certain
circumstances, who are considered U.S. PERSONS under Executive Order 12333.
Consequently, NCTC developed a mechanism in TIDE to identify and distinguish U.S.
citizens from non-U.S. citizens in order to further distinguish between ?aliens? under the
and U.S. PERSONS under Executive Order 12333.26
Nominations Procedures. As mentioned in Paragraph 1.26, when an
ORIGINATOR becomes a NOMINATOR, it prepares a nomination document and forwards it to
NCTC through the NOMINATOR tool.
1.48.1 As a general rule, NCTC will attach all disseminated communications (cables or
forms) to the TERRORIST identities record as a ?source? document, which will be
available on NCTC Current or the Joint Worldwide Intelligence Communications
System (.IWICS) to individuals who have been granted access to TIDE.
1.48.2 Because NCTC is the conduit for passing international TERRORISM INFORMATION to
TSC for TERRORISM screening purposes, there is no longer a need to send watchlist
requests to multiple Government Agencies. By sending a Terrorist Watchlist
nomination cable to NCTC, all potential U.S. Government TERRORISM screening
26 See 101(a)(3) [8 U.S.C.
UNCLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
Page 20
OR OFFICIAL USE SECURITY INFORMATION
I .46
IX.
1.47
1.48
TSC Review. TSC personnel will review the nominations received as described in Paragraph
1.56. TSC personnel evaluate whether nominations meet watchlisting standards and weigh, as
appropriate, all-source analysis before accepting or rejecting a nomination. The TSC has a
critical role to play in quality control, as the TSC review is the last step before any record
(including a biometric nomination where no name is available) is sent to various screening
systems. As with NCTC, the TSC should ensure there is a process in place for review and/or
auditing of TSC nominations and TSC records.
NOMINATION PROCEDURES
Distinctions between U.S. PERSONS under Executive Order 12333 and Aliens under the
Immigration and Nationality Act. This Watchlisting Guidance generally adopts the
de?nition of U.S. PERSON from Executive Order 12333 (as amended) for nomination
procedures. Executive Order 12333 defines a U.S. PERSON as United States citizen, an alien
known by the intelligence clement concerned to be a permanent resident alien, an
unincorporated association substantially composed of United States citizens or permanent
resident aliens, or a corporation incorporated in the United States, except for a corporation
directed or controlled by a foreign government or governments.? The Watchlisting Guidance
also contains certain exceptions to the minimum substantive derogatory standards for
TERRORIST watchlisting that support immigration and visa screening activities by the DHS and
DOS to determine whether ineligibilities exist for admission to the United States or visa
adjudication pursuant to the Immigration and Nationality Act (INA). Because the INA
defines ?aliens? as any person not a citizen or national of the United States, the INA
admissibility provisions also apply to Lawful Permanent Residents (LPRs), in certain
circumstances, who are considered U.S. PERSONS under Executive Order 12333.
Consequently, NCTC developed a mechanism in TIDE to identify and distinguish U.S.
citizens from non-U.S. citizens in order to further distinguish between ?aliens? under the
and U.S. PERSONS under Executive Order 12333.26
Nominations Procedures. As mentioned in Paragraph 1.26, when an
ORIGINATOR becomes a NOMINATOR, it prepares a nomination document and forwards it to
NCTC through the NOMINATOR tool.
1.48.1 As a general rule, NCTC will attach all disseminated communications (cables or
forms) to the TERRORIST identities record as a ?source? document, which will be
available on NCTC Current or the Joint Worldwide Intelligence Communications
System (.IWICS) to individuals who have been granted access to TIDE.
1.48.2 Because NCTC is the conduit for passing international TERRORISM INFORMATION to
TSC for TERRORISM screening purposes, there is no longer a need to send watchlist
requests to multiple Government Agencies. By sending a Terrorist Watchlist
nomination cable to NCTC, all potential U.S. Government TERRORISM screening
26 See 101(a)(3) [8 U.S.C.
UNCLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
Page 20

OFFICIAL USE SECURITY INFORMATION
responsibilities should be accounted for.
1.48.3 The has approved a Protocol to govern nominations for its non-FBI
components, which requires components to provide the FBI with all TERRORISM
The FBI is reSponsible for submitting watchlisting nominations based
on information received from other components pursuant to the nomination
procedures.
1.48.4 DHS has designated the Under Secretary for l&A as the Executive Agent for
centralized TERRORIST watchlisting process and he/she shall be responsible for providing
a DHS wide-mechanism for nominating all identifying or DEROGATORY INFORMATION
about KNOWN or SUSPECTED TERRORISTS to TIDE. DHS l&A is also responsible for
providing training/certi?cation programs to the components.
1.49 In providing information to NCTC for inclusion into TIDE, the is responsible for
determining whether it may, by law, provide the information to NCTC, in accordance with
section 1021 of IRTPA. This information shall be provided with any applicable caveats
or dissemination controls, which will be re?ected in TIDE. The biographic and biometric
identifiers derived from this information will be deemed for passage to TSDB
unless the ORIGINATOR designates them as Restricted,? as outlined in Addendum to
the TSC MOU.
1.50 NCTC Actions and Processes. NCTC reviews TERRORIST nominations from Federal
Departments or Agencies (NOMINATORS) as described in Paragraph 1.28.
1.51 In determining whether an individual is a KNOWN or SUSPECTED TERRORIST, NCTC will rely
on the designation of provided by the NOMINATOR as presumptively
valid. This presumption can be overcome if NCTC has Specific and credible information
within its possession that such designation is not appropriate, at which point NCTC will
provide such information to the NOMINATOR.
1.52 In reviewing whether to include the TERRORISM INFORMATION about the KNOWN or SUSPECTED
TERRORIST in TIDE, NCTC reviews the totality of information. The totalin of information is
evaluated based on the experience of the reviewer, and the facts and rational inferences that
may be drawn from those facts, including past conduct, current actions, and credible
intelligence concerning future conduct. As part of this review, NCTC will determine if the
information pertains to, or is related to, TERRORISM. TIDE includes TERRORISM INFORMATION
on KNOWN or SUSPECTED and may include additional TERRORISM INFORMATION
beyond what meets the minimum substantive derogatory and identifying criteria required for
nominations to the TSDB, as described in Paragraph 1.24. Upon conclusion of
review, NCTC will either accept or reject the nomination:
2" See Appendix 7, Protocol on Terrorist Nominations.
OR OFFICIAL USE SECURITY INFORMATION
Page 1 21
OFFICIAL USE SECURITY INFORMATION
responsibilities should be accounted for.
1.48.3 The has approved a Protocol to govern nominations for its non-FBI
components, which requires components to provide the FBI with all TERRORISM
The FBI is reSponsible for submitting watchlisting nominations based
on information received from other components pursuant to the nomination
procedures.
1.48.4 DHS has designated the Under Secretary for l&A as the Executive Agent for
centralized TERRORIST watchlisting process and he/she shall be responsible for providing
a DHS wide-mechanism for nominating all identifying or DEROGATORY INFORMATION
about KNOWN or SUSPECTED TERRORISTS to TIDE. DHS l&A is also responsible for
providing training/certi?cation programs to the components.
1.49 In providing information to NCTC for inclusion into TIDE, the is responsible for
determining whether it may, by law, provide the information to NCTC, in accordance with
section 1021 of IRTPA. This information shall be provided with any applicable caveats
or dissemination controls, which will be re?ected in TIDE. The biographic and biometric
identifiers derived from this information will be deemed for passage to TSDB
unless the ORIGINATOR designates them as Restricted,? as outlined in Addendum to
the TSC MOU.
1.50 NCTC Actions and Processes. NCTC reviews TERRORIST nominations from Federal
Departments or Agencies (NOMINATORS) as described in Paragraph 1.28.
1.51 In determining whether an individual is a KNOWN or SUSPECTED TERRORIST, NCTC will rely
on the designation of provided by the NOMINATOR as presumptively
valid. This presumption can be overcome if NCTC has Specific and credible information
within its possession that such designation is not appropriate, at which point NCTC will
provide such information to the NOMINATOR.
1.52 In reviewing whether to include the TERRORISM INFORMATION about the KNOWN or SUSPECTED
TERRORIST in TIDE, NCTC reviews the totality of information. The totalin of information is
evaluated based on the experience of the reviewer, and the facts and rational inferences that
may be drawn from those facts, including past conduct, current actions, and credible
intelligence concerning future conduct. As part of this review, NCTC will determine if the
information pertains to, or is related to, TERRORISM. TIDE includes TERRORISM INFORMATION
on KNOWN or SUSPECTED and may include additional TERRORISM INFORMATION
beyond what meets the minimum substantive derogatory and identifying criteria required for
nominations to the TSDB, as described in Paragraph 1.24. Upon conclusion of
review, NCTC will either accept or reject the nomination:
2" See Appendix 7, Protocol on Terrorist Nominations.
OR OFFICIAL USE SECURITY INFORMATION
Page 1 21

OR OFFICIAL USE ON SECURITY INFORMATION
1.52.1 Accept Nomination. If a nomination contains TERRORISM INFORMATION, NCTC
will create or enhance the associated TIDE record with the data contained in the
nomination. If the minimum substantive derogatory and identifying criteria are met,
NCTC will forward the TERRORIST IDENTIFIERS to the TSC for placement in TSDB with
the watchlist recommendation.
1.52.2 Reject Nomination. If a nomination does not contain TERRORISM INFORMATION,
NCTC may reject the nomination. NCTC will review rejected nominations and search
holdings for additional data that may support a TERRORISM INFORMATION ?nding. If no
information is found to support the nomination, NCTC will notify the NOMINATING
AGENCY of the rejection.
1.53 Types of records in TIDE. There are two types of records in TIDE:
1.53.1 TERRORIST Records. The vast majority of records in TIDE are for KNOWN or
SUSPECTEI) international TERRORISTS. These records are labeled Only a
small percentage of TERRORIST records in TIDE concern U.S. PERSONS.
1.53.2 Records. A small percentage of records in TIDE are identi?ed and
labeled 28 These records are generally of familial family members
or associates of KNOWN or SUSPECTED TERRORISTS and assist DOS and DHS in, for
example, adjudicating visas and immigration processing, or assist the 1C in tracking
KNOWN These include:
1.53.2.1 Alien Spouses and Children of TERRORISTS. Based on section
of the INA, alien spouses and children of TERRORISTS may be
inadmissible to the United States.29 TIDE exports records pertaining to alien
spouses and children of alien international TERRORISTS (also known as TIDE
Category Code 17) to support immigration and visa screening activities by DOS
and
1.53.2.2 Other Relatives. TIDE also includes records of
individuals who have a close relationship to a KNOWN or SUSPECTED international
28 TIDE records for non-U.S. citizens, including LPRs, with insuf?cient DEROGATORY INFORMATION to meet the
REASONABLE SUSPICION standard (TIDE Category Code 99) and records relating to an individual who has a defined
relationship with the KNOWN or SUSPECTED TERRORIST, but whose involvement with the KNOWN or SUSPECTED
activities is unknown (TIDE Category Code 50) are exported to the TSDB as TSDB exceptions to the
REASONABLE SUSPICION standard. Additionally, individuals described by sources as ?extremists?,
?jihadists?, ?militants?, ?mujahideen? or ?insurgents? (TIDE Category Code 03, also referred to as a ?labels plus?
nomination) will be accepted into the TSDB as exceptions for export to DHS and DOS for immigration and border
processing. See Paragraph 3.14.6. A complete list of TIDE Category Codes can found under the ?Watchlisting Criteria
Guidance? section on the Intelink website at
29 ?Any alien who. . . . is the spouse or child of an alien who is inadmissible under this subparagraph, if the activity
causing the alien to be found inadmissible occurred within the last 5 years, is inadmissible." See INA
[8 U.S.C.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 22
OR OFFICIAL USE ON SECURITY INFORMATION
1.52.1 Accept Nomination. If a nomination contains TERRORISM INFORMATION, NCTC
will create or enhance the associated TIDE record with the data contained in the
nomination. If the minimum substantive derogatory and identifying criteria are met,
NCTC will forward the TERRORIST IDENTIFIERS to the TSC for placement in TSDB with
the watchlist recommendation.
1.52.2 Reject Nomination. If a nomination does not contain TERRORISM INFORMATION,
NCTC may reject the nomination. NCTC will review rejected nominations and search
holdings for additional data that may support a TERRORISM INFORMATION ?nding. If no
information is found to support the nomination, NCTC will notify the NOMINATING
AGENCY of the rejection.
1.53 Types of records in TIDE. There are two types of records in TIDE:
1.53.1 TERRORIST Records. The vast majority of records in TIDE are for KNOWN or
SUSPECTEI) international TERRORISTS. These records are labeled Only a
small percentage of TERRORIST records in TIDE concern U.S. PERSONS.
1.53.2 Records. A small percentage of records in TIDE are identi?ed and
labeled 28 These records are generally of familial family members
or associates of KNOWN or SUSPECTED TERRORISTS and assist DOS and DHS in, for
example, adjudicating visas and immigration processing, or assist the 1C in tracking
KNOWN These include:
1.53.2.1 Alien Spouses and Children of TERRORISTS. Based on section
of the INA, alien spouses and children of TERRORISTS may be
inadmissible to the United States.29 TIDE exports records pertaining to alien
spouses and children of alien international TERRORISTS (also known as TIDE
Category Code 17) to support immigration and visa screening activities by DOS
and
1.53.2.2 Other Relatives. TIDE also includes records of
individuals who have a close relationship to a KNOWN or SUSPECTED international
28 TIDE records for non-U.S. citizens, including LPRs, with insuf?cient DEROGATORY INFORMATION to meet the
REASONABLE SUSPICION standard (TIDE Category Code 99) and records relating to an individual who has a defined
relationship with the KNOWN or SUSPECTED TERRORIST, but whose involvement with the KNOWN or SUSPECTED
activities is unknown (TIDE Category Code 50) are exported to the TSDB as TSDB exceptions to the
REASONABLE SUSPICION standard. Additionally, individuals described by sources as ?extremists?,
?jihadists?, ?militants?, ?mujahideen? or ?insurgents? (TIDE Category Code 03, also referred to as a ?labels plus?
nomination) will be accepted into the TSDB as exceptions for export to DHS and DOS for immigration and border
processing. See Paragraph 3.14.6. A complete list of TIDE Category Codes can found under the ?Watchlisting Criteria
Guidance? section on the Intelink website at
29 ?Any alien who. . . . is the spouse or child of an alien who is inadmissible under this subparagraph, if the activity
causing the alien to be found inadmissible occurred within the last 5 years, is inadmissible." See INA
[8 U.S.C.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 22

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
TERRORIST but are not alien spouses or children of a For instance, the
father or brother of a TERRORIST could have a record in TIDE (also known as TIDE
Category Code 160). Thus, these ?other relatives? could be U.S. PERSONS or non?
U.S. PERSONS. Identi?ers for these other relations reside in TIDE but are not
exported to the TSC for watchlisting, absent independent DEROGATORY
INFORMATION. Instead, these records may be retained in TIDE for analytic
purposes;
l.53.2.3 Passports. Unrecovered lost or stolen passports in the hands of international
TERRORISTS (also known as TIDE Category Code 89);
1.53.2.4 Associates. Individuals who have a de?ned relationship with the KNOWN or
SUSPECTED TERRORIST, but whose involvement with the KNOWN or SUSPECTED
activities is unknown (also known as TIDE Category Code 50);
1.53.2.5 Individuals with a Possible Nexus to TERRORISM. Individuals with a
possible nexus to TERRORISM and/or TERRORIST ACTIVITY but for whom additional
DEROGATORY INFORMATION is needed to meet the REASONABLE SUSPICION standard
(also known as TIDE Category Code 99).
[.54 Identification of U.S. PERSON Status in TIDE. NCTC will review the totality of
information available on a subject to discern U.S. PERSON status prior to creating or
enhancing a record in TIDE, whenever possible. For existing TIDE records, this status is
available to the analyst in the first ?eld ofthe TIDE record. In case of external
nominations or ENIIANCEMENTS from the IC, the standard nomination template provides a
means for NOMINATORS to identify U.S. PERSON status pursuant to Executive Order l2333
and the Agency?s speci?c guidelines. The U.S. PERSON status field on the standard
nomination template is a required ?eld and it is the responsibility of each NOMINATING
AGENCY to ensure the ?eld is properly annotated in accordance with established policy.
1.55 Types of Records in TIDE and the TSDB. Not all records in TIDE are included in the
TSDB. For example, records with FRAGMENTARY INFORMATION that do not meet the
minimum derogatory standard or records that do not meet identifying information criteria
remain in TIDE and are not included in the TSDB, absent direction for temporary, threat
based categories pursuant to Paragraph 1.59.30 The nominations process for TIDE records
that will be considered for entry in the TSDB begins with an automated data transfer process
that moves an individual TIDE record containing the identity of a KNOWN or SUSPECTED
TERRORIST or other exportable category or record nominated for watchlisting to the TSDB.
1.56 TSC Actions and Processes. The Single Review Queue (SRQ) enables the
Nominations and Data Integrity Unit (N DIU) to review each KNOWN or SUSPECTIED
30 Certain categories of records (see Paragraph 1.53.2) or nominations to the No Fly and Selectee List
based on an expedited waiver of ?full date of birth? requirement (see Paragraph 4. I 8) may also be eligible for inclusion
in the TSDB.
OR OFFICIAL USE SECURITY INFORMATION
Page 23
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
TERRORIST but are not alien spouses or children of a For instance, the
father or brother of a TERRORIST could have a record in TIDE (also known as TIDE
Category Code 160). Thus, these ?other relatives? could be U.S. PERSONS or non?
U.S. PERSONS. Identi?ers for these other relations reside in TIDE but are not
exported to the TSC for watchlisting, absent independent DEROGATORY
INFORMATION. Instead, these records may be retained in TIDE for analytic
purposes;
l.53.2.3 Passports. Unrecovered lost or stolen passports in the hands of international
TERRORISTS (also known as TIDE Category Code 89);
1.53.2.4 Associates. Individuals who have a de?ned relationship with the KNOWN or
SUSPECTED TERRORIST, but whose involvement with the KNOWN or SUSPECTED
activities is unknown (also known as TIDE Category Code 50);
1.53.2.5 Individuals with a Possible Nexus to TERRORISM. Individuals with a
possible nexus to TERRORISM and/or TERRORIST ACTIVITY but for whom additional
DEROGATORY INFORMATION is needed to meet the REASONABLE SUSPICION standard
(also known as TIDE Category Code 99).
[.54 Identification of U.S. PERSON Status in TIDE. NCTC will review the totality of
information available on a subject to discern U.S. PERSON status prior to creating or
enhancing a record in TIDE, whenever possible. For existing TIDE records, this status is
available to the analyst in the first ?eld ofthe TIDE record. In case of external
nominations or ENIIANCEMENTS from the IC, the standard nomination template provides a
means for NOMINATORS to identify U.S. PERSON status pursuant to Executive Order l2333
and the Agency?s speci?c guidelines. The U.S. PERSON status field on the standard
nomination template is a required ?eld and it is the responsibility of each NOMINATING
AGENCY to ensure the ?eld is properly annotated in accordance with established policy.
1.55 Types of Records in TIDE and the TSDB. Not all records in TIDE are included in the
TSDB. For example, records with FRAGMENTARY INFORMATION that do not meet the
minimum derogatory standard or records that do not meet identifying information criteria
remain in TIDE and are not included in the TSDB, absent direction for temporary, threat
based categories pursuant to Paragraph 1.59.30 The nominations process for TIDE records
that will be considered for entry in the TSDB begins with an automated data transfer process
that moves an individual TIDE record containing the identity of a KNOWN or SUSPECTED
TERRORIST or other exportable category or record nominated for watchlisting to the TSDB.
1.56 TSC Actions and Processes. The Single Review Queue (SRQ) enables the
Nominations and Data Integrity Unit (N DIU) to review each KNOWN or SUSPECTIED
30 Certain categories of records (see Paragraph 1.53.2) or nominations to the No Fly and Selectee List
based on an expedited waiver of ?full date of birth? requirement (see Paragraph 4. I 8) may also be eligible for inclusion
in the TSDB.
OR OFFICIAL USE SECURITY INFORMATION
Page 23

OR OFFICIAL USE SECURITY INFORMATION
record nomination to ensure it meets the watchlisting standard.31 The SRQ also helps ensure
that all quali?ed records are made available to the appropriate SCREENERS for use in
TERRORISM screening. During the SRQ process, every request to add, modify, or delete a
TSDB record is reviewed by a TSC analyst to ensure the accuracy of watchlisting records and
the removal of inaccurate records from TSDB.
1.56.1 Within the NDIU, experienced and/or designated Agency
representatives serve as Subject Matter Experts (SMEs) with respect to speci?c
databases No Fly or Selectee List) that receive TSDB data for TERRORISM
screening purposes. The currently has four types of SMEs who specialize in the
information/systems from their respective organizations: DHS/Transportation Security
Administration (TSA) for the No Fly, Selectee and Expanded Selectee Lists, FBI for
National Crime Information Center or SUSPECTED TERRORIST File
(KSTF), DOS for the Consular Consolidated Database and DHS for TECS (and
its components) and the Automated Targeting System (ATS). SM Es provide guidance
regarding their speci?c information/systems to the TSC and watchlisting standards to
their Agencies. In some cases, the SME coordinates the data export to the supported
system, provides feedback to NOMINATORS, and responds to inquiries regarding their
supported system from other TSC customer Agencies.
1.56.2 Upon the conclusion of review, TSC will either accept or reject the
nomination:
1.56.2.1 Accept Nomination. Consistent with Paragraphs (7) and (8) of Addendum
to the TSC MOU, if a nomination contains the minimum substantive derogatory
criteria and the minimum identifying information, TSC will create a TSDB record,
include the TERRORIST from the TIDE record, and export the TSDB
record to its supported systems databases and systems eligible to receive
records from the TSDB) for the bene?t of SCREENERS that conduct TERRORISM
screening. The current supported systems include, but are not limited to, the
following:
1.56.2.1.1
1.56.2. .2 DOS Consular Lookout and Support System and
1.56.213 DHS Watchlisting Service (WLS) TECS, ATS, Secure Flight);
1.56.214 TSA Transportation Security Vetting Center;
1.56.215 of Intelligence Analysis
1.56.2.1.6 Tipoff United States Canada
3' See Chapter 1, Section supra.
3? CCD is an application used by DOS to administer its visa and passport applications.
UN CLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
Page 24
OR OFFICIAL USE SECURITY INFORMATION
record nomination to ensure it meets the watchlisting standard.31 The SRQ also helps ensure
that all quali?ed records are made available to the appropriate SCREENERS for use in
TERRORISM screening. During the SRQ process, every request to add, modify, or delete a
TSDB record is reviewed by a TSC analyst to ensure the accuracy of watchlisting records and
the removal of inaccurate records from TSDB.
1.56.1 Within the NDIU, experienced and/or designated Agency
representatives serve as Subject Matter Experts (SMEs) with respect to speci?c
databases No Fly or Selectee List) that receive TSDB data for TERRORISM
screening purposes. The currently has four types of SMEs who specialize in the
information/systems from their respective organizations: DHS/Transportation Security
Administration (TSA) for the No Fly, Selectee and Expanded Selectee Lists, FBI for
National Crime Information Center or SUSPECTED TERRORIST File
(KSTF), DOS for the Consular Consolidated Database and DHS for TECS (and
its components) and the Automated Targeting System (ATS). SM Es provide guidance
regarding their speci?c information/systems to the TSC and watchlisting standards to
their Agencies. In some cases, the SME coordinates the data export to the supported
system, provides feedback to NOMINATORS, and responds to inquiries regarding their
supported system from other TSC customer Agencies.
1.56.2 Upon the conclusion of review, TSC will either accept or reject the
nomination:
1.56.2.1 Accept Nomination. Consistent with Paragraphs (7) and (8) of Addendum
to the TSC MOU, if a nomination contains the minimum substantive derogatory
criteria and the minimum identifying information, TSC will create a TSDB record,
include the TERRORIST from the TIDE record, and export the TSDB
record to its supported systems databases and systems eligible to receive
records from the TSDB) for the bene?t of SCREENERS that conduct TERRORISM
screening. The current supported systems include, but are not limited to, the
following:
1.56.2.1.1
1.56.2. .2 DOS Consular Lookout and Support System and
1.56.213 DHS Watchlisting Service (WLS) TECS, ATS, Secure Flight);
1.56.214 TSA Transportation Security Vetting Center;
1.56.215 of Intelligence Analysis
1.56.2.1.6 Tipoff United States Canada
3' See Chapter 1, Section supra.
3? CCD is an application used by DOS to administer its visa and passport applications.
UN CLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
Page 24

OR OFFICIAL USE SECURITY INFORMATION
1.56.2.1 .7 Tipoff Australia Counterterrorism lnformation Control System
(TACTICS).
1.56.2.2 Reject Nomination. lfa nomination lacks either the minimum substantive
derogatory criteria or the minimum identifying information, and is not an
exception to those requirements TIDE Category Codes 50 or 99 as described
in Paragraph 1.53.2), TSC will reject the nomination and notify NCTC directly of
its determination or coordinate with NCTC to notify the NOMINATOR of its
determination. Records nominated to TIDE that are ineligible for
watchlisting may remain in TIDE until additional information is obtained to
warrant either watchlisting or removal from TIDE. NCTC will review all-
source information for additional identifying or substantive DEROGATORY
INFORMATION. If additional information is discovered, NCTC will enhance the
TIDE record and submit the record to TSC for inclusion in the TSDB. The TIDE
record will be reviewed again by the TSC to determine whether it is eligible for
watchlisting in TSDB and export to certain supported screening systems.33
1.57 The number of supported systems will continue to grow as TSC, DHS, and DOS
expand their domestic and international outreach efforts and ?nalize additional agreements to
exchange TERRORISM SCREENING INFORMATION. TSC has modi?ed the TSDB so that certain
customers may query the TSDB remotely instead of receiving exports of TSDB data to their
own systems.
1.58 Expedited Nomination Procedures for Individual Nominations. lfexigent
circumstances exist (imminent travel and/or threat) where an individual nomination into the
TSDB needs to be expedited after normal duty hours, a NOMINATOR, with coordination from
NCTC, may contact the TSOC directly. If a NOMINATOR coordinated with NCTC, the
nomination will be received TSDB and the TSOC Watch
Commander will coordinate with a NDIU Senior Analyst to process the nomination. A
may also contact the TSC directly and provide all relevant information using the
following process:
1.58.1 The must first contact the TSOC at 866?- (toll free number) or
at571--
1.58.2 The NOMINATOR will be instructed by a TSOC Specialist on how to telephonically
complete a Terrorist Screening Center Expedited Nomination Request Form.
1.58.3 In addition to basic identifying information, the will be requested to
provide a 24/7 point of contact should the KNOWN or SUSPECTED TERRORIST be
encountered by a SCREENER.
33 See Paragraph 1.24.2 supra.
UNCLASSIF IEDIIF OR OFFICIAL USE SECURITY INFORMATION
Page 25
OR OFFICIAL USE SECURITY INFORMATION
1.56.2.1 .7 Tipoff Australia Counterterrorism lnformation Control System
(TACTICS).
1.56.2.2 Reject Nomination. lfa nomination lacks either the minimum substantive
derogatory criteria or the minimum identifying information, and is not an
exception to those requirements TIDE Category Codes 50 or 99 as described
in Paragraph 1.53.2), TSC will reject the nomination and notify NCTC directly of
its determination or coordinate with NCTC to notify the NOMINATOR of its
determination. Records nominated to TIDE that are ineligible for
watchlisting may remain in TIDE until additional information is obtained to
warrant either watchlisting or removal from TIDE. NCTC will review all-
source information for additional identifying or substantive DEROGATORY
INFORMATION. If additional information is discovered, NCTC will enhance the
TIDE record and submit the record to TSC for inclusion in the TSDB. The TIDE
record will be reviewed again by the TSC to determine whether it is eligible for
watchlisting in TSDB and export to certain supported screening systems.33
1.57 The number of supported systems will continue to grow as TSC, DHS, and DOS
expand their domestic and international outreach efforts and ?nalize additional agreements to
exchange TERRORISM SCREENING INFORMATION. TSC has modi?ed the TSDB so that certain
customers may query the TSDB remotely instead of receiving exports of TSDB data to their
own systems.
1.58 Expedited Nomination Procedures for Individual Nominations. lfexigent
circumstances exist (imminent travel and/or threat) where an individual nomination into the
TSDB needs to be expedited after normal duty hours, a NOMINATOR, with coordination from
NCTC, may contact the TSOC directly. If a NOMINATOR coordinated with NCTC, the
nomination will be received TSDB and the TSOC Watch
Commander will coordinate with a NDIU Senior Analyst to process the nomination. A
may also contact the TSC directly and provide all relevant information using the
following process:
1.58.1 The must first contact the TSOC at 866?- (toll free number) or
at571--
1.58.2 The NOMINATOR will be instructed by a TSOC Specialist on how to telephonically
complete a Terrorist Screening Center Expedited Nomination Request Form.
1.58.3 In addition to basic identifying information, the will be requested to
provide a 24/7 point of contact should the KNOWN or SUSPECTED TERRORIST be
encountered by a SCREENER.
33 See Paragraph 1.24.2 supra.
UNCLASSIF IEDIIF OR OFFICIAL USE SECURITY INFORMATION
Page 25

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.58.4 Within 72 hours of contacting the TSOC, the NOMINATOR must provide appropriate
follow-up documentation that articulates, through either classi?ed or unclassi?ed means,
the substantive DEROGATORY INFORMATION used to establish the basis for TERRORIST
watchlisting.
I .59 Expedited Nomination Procedures for Temporary, Threat-Based Categories. This
provision is intended to enable categories of individuals to be temporarily upgraded in
watchlist status based on current and credible intelligence information or a particular threat
stream that indicates a certain category of individuals may be used to conduct an act of
domestic or international TERRORISM. This temporary, threat-based expedited upgrade (TB U)
is made at the direction of the Assistant to the President for Homeland Security and
Counterterrorism or his/her designee (Appropriate Of?cial) and should be narrowly tailored to
address the threat.
1.59.1 The goal of this provision is to fashion a watchlisting response that is appropriate to
the nature, speci?city, and severity of the threat. To achieve this goal, in addition to
verifying the credibility of the threat intelligence, due consideration should be given to:
i.59.l.l The harm to public safety posed by the threat;
1.59.! .2 The clarity and speci?city of the information giving rise to the threat as to
time, place, method, and identity of the suspected perpetrators;
1.59.1.3 The anticipated impact on international and domestic travel, civil liberties,
and foreign relations; and,
l.59.l .4 The best available screening tools, other than the No Fly or Selectee Lists,
given the type and speci?city of identi?ers and travel data.
l.59.2 When necessitated by exigent circumstances, and where there is current and credible
intelligence information or a particular threat stream that indicates a certain category of
individuals may be used to conduct an act of domestic or international TERRORISM, the
Appropriate Of?cial may direct the TSC and NCTC to place categories of individuals
from TIDE or TSDB on the No Fly List, Selectee List, or into the TSDB for up to 72
hours before concurrence is obtained from the Deputies or Principals Committee. To the
extent practicable, the initial direction to NCTC and TSC from the Appropriate Of?cial
will be in writing. Absent DEROGATORY INFORMATION supporting individual nomination
or watchlist upgrade, if written concurrence is not obtained within 72 hours of the initial
direction to and NCTC, the will automatically remove any individuals added
to the No Fly List, Selectee List, or TSDB pursuant to the TBU,.until such written
direction is received.
I593 The addition of categories of individuals to the No Fly List, Selectee List, or TSDB
pursuant to Paragraph 1.59.2 shall be effected for a period of time, consistent with the
OR OFFICIAL USE SECURITY INFORMATION
Page 26
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.58.4 Within 72 hours of contacting the TSOC, the NOMINATOR must provide appropriate
follow-up documentation that articulates, through either classi?ed or unclassi?ed means,
the substantive DEROGATORY INFORMATION used to establish the basis for TERRORIST
watchlisting.
I .59 Expedited Nomination Procedures for Temporary, Threat-Based Categories. This
provision is intended to enable categories of individuals to be temporarily upgraded in
watchlist status based on current and credible intelligence information or a particular threat
stream that indicates a certain category of individuals may be used to conduct an act of
domestic or international TERRORISM. This temporary, threat-based expedited upgrade (TB U)
is made at the direction of the Assistant to the President for Homeland Security and
Counterterrorism or his/her designee (Appropriate Of?cial) and should be narrowly tailored to
address the threat.
1.59.1 The goal of this provision is to fashion a watchlisting response that is appropriate to
the nature, speci?city, and severity of the threat. To achieve this goal, in addition to
verifying the credibility of the threat intelligence, due consideration should be given to:
i.59.l.l The harm to public safety posed by the threat;
1.59.! .2 The clarity and speci?city of the information giving rise to the threat as to
time, place, method, and identity of the suspected perpetrators;
1.59.1.3 The anticipated impact on international and domestic travel, civil liberties,
and foreign relations; and,
l.59.l .4 The best available screening tools, other than the No Fly or Selectee Lists,
given the type and speci?city of identi?ers and travel data.
l.59.2 When necessitated by exigent circumstances, and where there is current and credible
intelligence information or a particular threat stream that indicates a certain category of
individuals may be used to conduct an act of domestic or international TERRORISM, the
Appropriate Of?cial may direct the TSC and NCTC to place categories of individuals
from TIDE or TSDB on the No Fly List, Selectee List, or into the TSDB for up to 72
hours before concurrence is obtained from the Deputies or Principals Committee. To the
extent practicable, the initial direction to NCTC and TSC from the Appropriate Of?cial
will be in writing. Absent DEROGATORY INFORMATION supporting individual nomination
or watchlist upgrade, if written concurrence is not obtained within 72 hours of the initial
direction to and NCTC, the will automatically remove any individuals added
to the No Fly List, Selectee List, or TSDB pursuant to the TBU,.until such written
direction is received.
I593 The addition of categories of individuals to the No Fly List, Selectee List, or TSDB
pursuant to Paragraph 1.59.2 shall be effected for a period of time, consistent with the
OR OFFICIAL USE SECURITY INFORMATION
Page 26

UN OR OFFICIAL USE SECURITY INFORMATION
nature of the threat involved, not to exceed 30 days but may be renewed for additional
30-day periods upon written approval of the Deputies or Principals Committee. A
is valid until the threat no longer exists. To the extent that such threat recedes or is
otherwise mitigated prior to the expiration of 30 days or during any extension approved
by the Deputies or Principals Committee, TSC and and members of the
watchlisting community shall immediately request of the Deputies or Principals
Committee to downgrade these TBUs to their original or appropriate status. A11 threat-
based records transmitted through automated mechanisms (122., WLS, CCD) will include
a indicator? at the message level to differentiate this category of records from
non-TBU records and to provide the directive for which the record is upgraded.
1.59.4 Until such time as the Deputies or Principals provide additional, written guidance,
DOS will defer visa actions with respect to these expedited upgrades in watchlist status.
1.59.5 Departments and Agencies will advise the Deputies or Principals of other
consequences that may result from a change in watchlist status and seek guidance as to
how to proceed.
1.59.6 After these categorical moves are accomplished or renewed, there will be an
expedited procedure for the review of all U. S. PERSONS that are part of the TBU to ensure
their watchlisting status is appropriate (including whether continued categorical
watchlisting may be warranted based on the nature of the threat).
1.60 Arbitration of Watchlisting Disputes. lfa NOMINATOR wishes to dispute
watchlisting determination, it may contact NCTC (for international nominations)
to discuss the watchlisting status and/or submit additional substantive derogatory and
identifying information to support its initial nomination. Additional information provided to
NCTC by a NOMINATOR will be passed to the TSC for review and ?nal watchlisting
determination. In the case of an BI dispute over the watchlisting determination of an
international nomination, a case agent must contact the TSC.
1.61 In the case of domestic TERRORIST nominations, if the FBI wishes to dispute
watchlisting determination, it may contact the TSC to discuss the watchlisting status and/or
submit additional substantive derogatory and identifying information to support its initial
nomination.
X. PROCEDURES TO REMOVE AN INDIVIDUAL FROM THE WATCHLIST
1.62 A NOMINATOR desiring to remove an international TERRORIST identity record previously
nominated to TIDE should contact NCTC and provide writtenjustification for the request.
NCTC will process the request when received. NCTC will be the ?nal arbiter of
whether the identity is removed from TIDE and TSC will be the ?nal arbiter of whether
IDENTIFIERS are removed from TSDB.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 27
UN OR OFFICIAL USE SECURITY INFORMATION
nature of the threat involved, not to exceed 30 days but may be renewed for additional
30-day periods upon written approval of the Deputies or Principals Committee. A
is valid until the threat no longer exists. To the extent that such threat recedes or is
otherwise mitigated prior to the expiration of 30 days or during any extension approved
by the Deputies or Principals Committee, TSC and and members of the
watchlisting community shall immediately request of the Deputies or Principals
Committee to downgrade these TBUs to their original or appropriate status. A11 threat-
based records transmitted through automated mechanisms (122., WLS, CCD) will include
a indicator? at the message level to differentiate this category of records from
non-TBU records and to provide the directive for which the record is upgraded.
1.59.4 Until such time as the Deputies or Principals provide additional, written guidance,
DOS will defer visa actions with respect to these expedited upgrades in watchlist status.
1.59.5 Departments and Agencies will advise the Deputies or Principals of other
consequences that may result from a change in watchlist status and seek guidance as to
how to proceed.
1.59.6 After these categorical moves are accomplished or renewed, there will be an
expedited procedure for the review of all U. S. PERSONS that are part of the TBU to ensure
their watchlisting status is appropriate (including whether continued categorical
watchlisting may be warranted based on the nature of the threat).
1.60 Arbitration of Watchlisting Disputes. lfa NOMINATOR wishes to dispute
watchlisting determination, it may contact NCTC (for international nominations)
to discuss the watchlisting status and/or submit additional substantive derogatory and
identifying information to support its initial nomination. Additional information provided to
NCTC by a NOMINATOR will be passed to the TSC for review and ?nal watchlisting
determination. In the case of an BI dispute over the watchlisting determination of an
international nomination, a case agent must contact the TSC.
1.61 In the case of domestic TERRORIST nominations, if the FBI wishes to dispute
watchlisting determination, it may contact the TSC to discuss the watchlisting status and/or
submit additional substantive derogatory and identifying information to support its initial
nomination.
X. PROCEDURES TO REMOVE AN INDIVIDUAL FROM THE WATCHLIST
1.62 A NOMINATOR desiring to remove an international TERRORIST identity record previously
nominated to TIDE should contact NCTC and provide writtenjustification for the request.
NCTC will process the request when received. NCTC will be the ?nal arbiter of
whether the identity is removed from TIDE and TSC will be the ?nal arbiter of whether
IDENTIFIERS are removed from TSDB.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 27

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.63 If the NOMINATOR requesting removal of an international TERRORIST identity record from
TIDE is the only NOMINATOR to have provided information on that record, the removal request
will be immediately processed by NCTC. The removal information is then sent to the TSC,
which, in turn, makes a determination regarding removal of the TERRORIST identity from the
TSDB.
1.64 If multiple NOMINATORS have provided information on an international identity
record, NCTC will coordinate with all relevant parties in an attempt to reach a consensus on
the TERRORIST identity?s most appropriate watchlisting status.
l.64.l If the multiple NOMINATORS arrive at a consensus that the watchlisted identity is not
reasonably suspected of engaging in TERRORISM and/or TERRORIST ACTIVITIES, or an
applicable exception, the identity is removed from the TSDB and TIDE. In certain
circumstances, NCTC may retain records in TIDE to prevent inappropriate re-
watchlisting.
1.64.2 If the multiple NOMINATORS cannot arrive at a consensus regarding the watchlisting
status of an identity, TSC may decide to remove the identity from the TSDB, but NCTC
may retain the identity in TIDE.
1.64.3 For cases in which the FBI has conducted an investigation on an individual
(independently nominated by another NOMINATOR) and has concluded that the
watchlisted individual is not a KNOWN or SUSPECTED the individual may be
removed from the TSDB.34 In such cases, the TERRORIST IDENTIFIERS from the Bl?s
investigation may be used to supplement the TIDE record.
1.65 The FBI will review domestic TERRORIST identity removal requests according to applicable
FBI procedures.
[.66 TSC has an established, on-going process to review every record in the TSDB in accordance
with Paragraph of the TSC MOU and its mission under IISPD-6 to maintain the most
thorough, accurate, and current information in the TSDB. If TSC determines that the
watchlisting standards are not met for an individual record, TSC will remove the record from
the TSDB, in coordination with the NOMINATING AGENCY.
XI. REDRESS PROCEDURES
l.67 In January 2005, the TSC established a formal watchlist redress process that allows Agencies
After an FBI determination that the individual is not a KNOWN or SUSPECTED NCTC may determine-
based on a independent nomination- that the individual should remain in TIDE as records that have been
fully vetted and should not be screened against (TIDE Category Code 140), the individual be watchlisted based upon the
independent determination that the individual is a KNOWN or SUSPECTED TERRORIST or that the individual
warrants watchlisting based upon an exception to the REASONABLE SUSPICION standard.
UN OR OFFICIAL USE SECURITY INFORMATION
Page I 28
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.63 If the NOMINATOR requesting removal of an international TERRORIST identity record from
TIDE is the only NOMINATOR to have provided information on that record, the removal request
will be immediately processed by NCTC. The removal information is then sent to the TSC,
which, in turn, makes a determination regarding removal of the TERRORIST identity from the
TSDB.
1.64 If multiple NOMINATORS have provided information on an international identity
record, NCTC will coordinate with all relevant parties in an attempt to reach a consensus on
the TERRORIST identity?s most appropriate watchlisting status.
l.64.l If the multiple NOMINATORS arrive at a consensus that the watchlisted identity is not
reasonably suspected of engaging in TERRORISM and/or TERRORIST ACTIVITIES, or an
applicable exception, the identity is removed from the TSDB and TIDE. In certain
circumstances, NCTC may retain records in TIDE to prevent inappropriate re-
watchlisting.
1.64.2 If the multiple NOMINATORS cannot arrive at a consensus regarding the watchlisting
status of an identity, TSC may decide to remove the identity from the TSDB, but NCTC
may retain the identity in TIDE.
1.64.3 For cases in which the FBI has conducted an investigation on an individual
(independently nominated by another NOMINATOR) and has concluded that the
watchlisted individual is not a KNOWN or SUSPECTED the individual may be
removed from the TSDB.34 In such cases, the TERRORIST IDENTIFIERS from the Bl?s
investigation may be used to supplement the TIDE record.
1.65 The FBI will review domestic TERRORIST identity removal requests according to applicable
FBI procedures.
[.66 TSC has an established, on-going process to review every record in the TSDB in accordance
with Paragraph of the TSC MOU and its mission under IISPD-6 to maintain the most
thorough, accurate, and current information in the TSDB. If TSC determines that the
watchlisting standards are not met for an individual record, TSC will remove the record from
the TSDB, in coordination with the NOMINATING AGENCY.
XI. REDRESS PROCEDURES
l.67 In January 2005, the TSC established a formal watchlist redress process that allows Agencies
After an FBI determination that the individual is not a KNOWN or SUSPECTED NCTC may determine-
based on a independent nomination- that the individual should remain in TIDE as records that have been
fully vetted and should not be screened against (TIDE Category Code 140), the individual be watchlisted based upon the
independent determination that the individual is a KNOWN or SUSPECTED TERRORIST or that the individual
warrants watchlisting based upon an exception to the REASONABLE SUSPICION standard.
UN OR OFFICIAL USE SECURITY INFORMATION
Page I 28

OR OFFICIAL USE SECURITY INFORMATION
that use TSDB data during a TERRORISM screening process to refer individuals? complaints to
the TSC if it appears the complaints may be related to the watchlisting process. The goal of
the watchlist redress process is to provide for timely and fair review of individuals?
complaints and to identify and correct any errors in the TSDB.
L68 The watchlist redress process is a multi?Agency process involving the DHS, TSC, NCTC,
NOMINATORS, and SCREENERS. On September 19, 2007, Agencies participating in the
watchlist redress process executed the Redress MOU to set forth a coordinated redress process
to respond to individual complaints about adverse screening experiences.?
L69 Redress Of?ce is responsible for receiving, tracking, and researching watchlist-related
complaints that SCREENERS refer to TSC. For each redress complaint received, the Redress
Of?ce conducts an in-depth analysis to determine if the person?s complaint is related to a
TSDB record, including a determination of whether the complainant is the watchlisted
individual or merely a near-match to a watchlist record. if the complainant is the watchlisted
individual, the Redress Of?ce will determine whether the watchlisted individual still
meets all the watchlisting criteria.
1.70 For each complaint, the TSC Redress Of?ce coordinates with the (via NCTC
when the NOMINATOR is not the FBI), who assists in the evaluation of the complaint to ensure
the most current, accurate, and thorough information available is used to review the person?s
watchlist status. Where appropriate and warranted by the current information and applicable
criteria, a person?s watchlist status may be adjusted downgraded from the No Fly to
Selectee List or the person?s identity may be removed entirely from the TSDB). If the redress
complaint was referred to the TSC from the DHS Traveler Redress Inquiry Program (DHS
TRIP), the individual?s adjusted watchlist status will be provided to DHS TRIP for issuance of
an appropriate response.
l.7l DHS TRIP is a single point of contact for individuals who have inquiries or seek resolution
regarding dif?culties they experience during their travel screening or inspection at, for
example, transportation hubs like airports, or when crossing US. borders. The DHS TRIP
website is DHS TRIP ensures a thorough review is completed by
consulting and sharing information with other DHS Components and other Agencies, as
appropriate, to address the issues identi?ed by the complainant.
XII. PERIODIC REVIEW OF THE WATCHLISTING GUIDANCE
1.72 This Watchlisting Guidance shall be reviewed no less than every two years following the
conclusion of the previous review, or as needed.
35 See Appendix 8, Redress see also FN l6, supra.
OR OFFICIAL USE SECURITY INFORMATION
Page 29
OR OFFICIAL USE SECURITY INFORMATION
that use TSDB data during a TERRORISM screening process to refer individuals? complaints to
the TSC if it appears the complaints may be related to the watchlisting process. The goal of
the watchlist redress process is to provide for timely and fair review of individuals?
complaints and to identify and correct any errors in the TSDB.
L68 The watchlist redress process is a multi?Agency process involving the DHS, TSC, NCTC,
NOMINATORS, and SCREENERS. On September 19, 2007, Agencies participating in the
watchlist redress process executed the Redress MOU to set forth a coordinated redress process
to respond to individual complaints about adverse screening experiences.?
L69 Redress Of?ce is responsible for receiving, tracking, and researching watchlist-related
complaints that SCREENERS refer to TSC. For each redress complaint received, the Redress
Of?ce conducts an in-depth analysis to determine if the person?s complaint is related to a
TSDB record, including a determination of whether the complainant is the watchlisted
individual or merely a near-match to a watchlist record. if the complainant is the watchlisted
individual, the Redress Of?ce will determine whether the watchlisted individual still
meets all the watchlisting criteria.
1.70 For each complaint, the TSC Redress Of?ce coordinates with the (via NCTC
when the NOMINATOR is not the FBI), who assists in the evaluation of the complaint to ensure
the most current, accurate, and thorough information available is used to review the person?s
watchlist status. Where appropriate and warranted by the current information and applicable
criteria, a person?s watchlist status may be adjusted downgraded from the No Fly to
Selectee List or the person?s identity may be removed entirely from the TSDB). If the redress
complaint was referred to the TSC from the DHS Traveler Redress Inquiry Program (DHS
TRIP), the individual?s adjusted watchlist status will be provided to DHS TRIP for issuance of
an appropriate response.
l.7l DHS TRIP is a single point of contact for individuals who have inquiries or seek resolution
regarding dif?culties they experience during their travel screening or inspection at, for
example, transportation hubs like airports, or when crossing US. borders. The DHS TRIP
website is DHS TRIP ensures a thorough review is completed by
consulting and sharing information with other DHS Components and other Agencies, as
appropriate, to address the issues identi?ed by the complainant.
XII. PERIODIC REVIEW OF THE WATCHLISTING GUIDANCE
1.72 This Watchlisting Guidance shall be reviewed no less than every two years following the
conclusion of the previous review, or as needed.
35 See Appendix 8, Redress see also FN l6, supra.
OR OFFICIAL USE SECURITY INFORMATION
Page 29

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.
2.l
2.2
2.3
2.4
CHAPTER 2: MINIMUM IDENTIFYING CRITERIA
BIOMETRIC NOMINATIONS
Biometric information refers to the measurable biological (anatomical or physiological) and
behavioral characteristics that can be used for recognition. Examples include facial
photographs, ?ngerprints, iris scans, digital images, latent prints, DNA and gait. A biometric
is sufficient to meet the minimum identifying criteria for nominations to the TIDE
and/or the TSDB, provided that the nomination also meets the minimum substantive
derogatory criteria, or one of the exceptions. Biometric nominations without minimum
biographic information will be provided only to those SCREENERS that have the technical
capability to screen against or otherwise make assessments using the biometrics.
Notwithstanding the above, all NOMINATORS are encouraged to include all available associated
biographic information with any biometric nomination.
MINIMUM NOMINATION REQUIREMENT
NOMINATORs shall provide NCTC, for inclusion into
INFORMATION that suggests an individual may have a nexus to TERRORISM and/or TERRORIST
ACTIVITIES and any additional information that will facilitate identi?cation of these
individuals. Nominations to TIDE under this section will be considered for inclusion in the
TSDB if the NOMINATING AGENCY believes there is REASONABLE to believe that the
individual is a KNOWN or SUSPECTED TERRORIST.
Nominations of individuals based on FRAGMENTARY INFORMATION who fail to meet the
minimum identifying criteria for nomination to TSDB should be provided to NCTC for
inclusion in TIDE when there is DEROGATORY INFORMATION suggesting that the
individual is associated with TERRORISM and the NOMINATING AGENCY determines that
there are suf?cient identi?ers for possibly facilitating a match to existing TIDE records.
Unless otherwise directed, NOMINATING AGENCIES should prioritize the nominations of
individuals who satisfy the minimum identifying criteria before addressing nominations
based on FRAGMENTARY INFORMATION.
SCREENER Discretion. As appropriate, SCREENERS have the discretion to decide not to
include in their screening systems common names received from the TSDB, where
insufficient identifying information exists for identi?cation.
TSDB. Nominations to the TSDB must include a last name. NOMINATING AGENCIES should
also provide any additional identifying information available. in addition to a last name,
nominations must include:
2.4.1 ?rst name;
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 30
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
1.
2.l
2.2
2.3
2.4
CHAPTER 2: MINIMUM IDENTIFYING CRITERIA
BIOMETRIC NOMINATIONS
Biometric information refers to the measurable biological (anatomical or physiological) and
behavioral characteristics that can be used for recognition. Examples include facial
photographs, ?ngerprints, iris scans, digital images, latent prints, DNA and gait. A biometric
is sufficient to meet the minimum identifying criteria for nominations to the TIDE
and/or the TSDB, provided that the nomination also meets the minimum substantive
derogatory criteria, or one of the exceptions. Biometric nominations without minimum
biographic information will be provided only to those SCREENERS that have the technical
capability to screen against or otherwise make assessments using the biometrics.
Notwithstanding the above, all NOMINATORS are encouraged to include all available associated
biographic information with any biometric nomination.
MINIMUM NOMINATION REQUIREMENT
NOMINATORs shall provide NCTC, for inclusion into
INFORMATION that suggests an individual may have a nexus to TERRORISM and/or TERRORIST
ACTIVITIES and any additional information that will facilitate identi?cation of these
individuals. Nominations to TIDE under this section will be considered for inclusion in the
TSDB if the NOMINATING AGENCY believes there is REASONABLE to believe that the
individual is a KNOWN or SUSPECTED TERRORIST.
Nominations of individuals based on FRAGMENTARY INFORMATION who fail to meet the
minimum identifying criteria for nomination to TSDB should be provided to NCTC for
inclusion in TIDE when there is DEROGATORY INFORMATION suggesting that the
individual is associated with TERRORISM and the NOMINATING AGENCY determines that
there are suf?cient identi?ers for possibly facilitating a match to existing TIDE records.
Unless otherwise directed, NOMINATING AGENCIES should prioritize the nominations of
individuals who satisfy the minimum identifying criteria before addressing nominations
based on FRAGMENTARY INFORMATION.
SCREENER Discretion. As appropriate, SCREENERS have the discretion to decide not to
include in their screening systems common names received from the TSDB, where
insufficient identifying information exists for identi?cation.
TSDB. Nominations to the TSDB must include a last name. NOMINATING AGENCIES should
also provide any additional identifying information available. in addition to a last name,
nominations must include:
2.4.1 ?rst name;
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 30

OR OFFICIAL USE SECURITY INFORMATION
2.4.2 Or any one of the following additional identi?ers:
2.4.2.1 Full date of birth (eight digit format);
2.4.2.2 PaSSport number (with or without country of issuance);
2.4.2.3 Unique identifying numbers such as alien registration numbers, visa numbers,
and social security numbers;
2.4.2.4 Telephone number(s)36;
2.4.2.5 E-mail address(es)37;
2.4.2.6 License plate number(s).
2.4.3 Or any two of the following additional identi?ers?:
2.4.3.1 Country of citizenship, if different from place of birth;
2.4.3.2 Place of birth (city or country), if different from country of citizenship;
2.4.3.3 Circa or partial date of birth (partial: e. 1960; or range: e. g, 1960-1965);
2.4.3.4 Full name of an immediate family member parent, spouse, sibling, or
children);
2.4.3.5 Occupation or current employer;
2.4.3.6 Speci?c degrees received;
2.4.3.7 Schools attended;
2.4.3.8 Physical identifiers such as race, height, or weight;
2.4.3.9 Unique physical identi?ers such as scars, marks or tattoos;
2.4.3.10 Street address or other suf?ciently speci?c location information.
3" Only unclassi?ed phone numbers that are authorized for passage to TSC pursuant to Paragraph 7(m) of Addendum [3
to the TSC MOU, will be included in TSDB. See Appendix 4. Unclassi?ed phone numbers will only be provided to
those SCREENERS that have the technical capability to receive this data.
37 Only unclassi?ed email addresses that are authorized for passage to TSC pursuant to Paragraph 7(m) of Addendum
of the TSC MOU will be included in TSDB. See Appendix 4. Unclassi?ed email addresses will only be provided to
those SCREENERS that have the technical capability to receive this data.
38 As required here, there must be two distinct identi?ers that must be suf?ciently speci?c to account for the large
number of possible matches common identi?ers may produce. For example, if one identi?er is rather common
physical identi?ers), the other identi?er must be more speci?c to permit the screening of?cial to successfully match a
record with an individual. As a further example, a nomination with the last name listed as Khan, location listed as
Kabul, Afghanistan, and occupation listed as a baker alone would be insuf?cient for screening purposes because it is
highly unlikely a successful match could be made against such data. However, a nomination with the name listed as R.
Khan, location listed as residence of 123 Sunshine Street, Kabul, Afghanistan, and occupation listed as a baker at ABC
Bakery, would be suf?cient for screening purposes.
OR OFFICIAL USE SECURITY INFORMATION
Page I 3]
OR OFFICIAL USE SECURITY INFORMATION
2.4.2 Or any one of the following additional identi?ers:
2.4.2.1 Full date of birth (eight digit format);
2.4.2.2 PaSSport number (with or without country of issuance);
2.4.2.3 Unique identifying numbers such as alien registration numbers, visa numbers,
and social security numbers;
2.4.2.4 Telephone number(s)36;
2.4.2.5 E-mail address(es)37;
2.4.2.6 License plate number(s).
2.4.3 Or any two of the following additional identi?ers?:
2.4.3.1 Country of citizenship, if different from place of birth;
2.4.3.2 Place of birth (city or country), if different from country of citizenship;
2.4.3.3 Circa or partial date of birth (partial: e. 1960; or range: e. g, 1960-1965);
2.4.3.4 Full name of an immediate family member parent, spouse, sibling, or
children);
2.4.3.5 Occupation or current employer;
2.4.3.6 Speci?c degrees received;
2.4.3.7 Schools attended;
2.4.3.8 Physical identifiers such as race, height, or weight;
2.4.3.9 Unique physical identi?ers such as scars, marks or tattoos;
2.4.3.10 Street address or other suf?ciently speci?c location information.
3" Only unclassi?ed phone numbers that are authorized for passage to TSC pursuant to Paragraph 7(m) of Addendum [3
to the TSC MOU, will be included in TSDB. See Appendix 4. Unclassi?ed phone numbers will only be provided to
those SCREENERS that have the technical capability to receive this data.
37 Only unclassi?ed email addresses that are authorized for passage to TSC pursuant to Paragraph 7(m) of Addendum
of the TSC MOU will be included in TSDB. See Appendix 4. Unclassi?ed email addresses will only be provided to
those SCREENERS that have the technical capability to receive this data.
38 As required here, there must be two distinct identi?ers that must be suf?ciently speci?c to account for the large
number of possible matches common identi?ers may produce. For example, if one identi?er is rather common
physical identi?ers), the other identi?er must be more speci?c to permit the screening of?cial to successfully match a
record with an individual. As a further example, a nomination with the last name listed as Khan, location listed as
Kabul, Afghanistan, and occupation listed as a baker alone would be insuf?cient for screening purposes because it is
highly unlikely a successful match could be made against such data. However, a nomination with the name listed as R.
Khan, location listed as residence of 123 Sunshine Street, Kabul, Afghanistan, and occupation listed as a baker at ABC
Bakery, would be suf?cient for screening purposes.
OR OFFICIAL USE SECURITY INFORMATION
Page I 3]

OR OFFICIAL USE SECURITY INFORMATION
2.5
2.6
MINIMUM BIOGRAPHIC INFORMATION REQUIRED FOR EXCEPTIONS TO THE
MINIMUM SUBSTANTIVE DEROGATORY STANDARDS FOR TERRORIST
WATCHLISTING
There are certain exceptions to the minimum substantive derogatory standards for TERRORIST
watchlisting that support immigration and visa screening activities by DHS and DOS.39
Examples of these categories of records include, but may not be limited to, records relating to
an individual who has a de?ned relationship with the KNOWN or TERRORIST, but
whose involvement with the KNOWN or SUSPECTED activities is unknown (TIDE
Category Code 50) and those with insuf?cient INFORMATION TO meet the
REASONABLE SUSPICION standard for watchlisting (TIDE Category Code 99).
NOMINATING AGENCIES should provide all additional identifying information available. All
nominations under this section must include a full name (?rst name, last name) and one of
the following identi?ers:
2.6.1 Full date of birth;
2.6.2 Full passport number (with or without country of issuance);
2.6.3 Unique identifying numbers such as alien registration numbers, visa numbers, and social
security account numbers;
2.6.4 Telephone number(s);
2.6.5 Email address(es);
2.6.6 License plate number(s);
2.6.7 Biometrics, such as facial image, iris scans or ?ngerprints.
39 See Chapter 3, Section V.
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 32
OR OFFICIAL USE SECURITY INFORMATION
2.5
2.6
MINIMUM BIOGRAPHIC INFORMATION REQUIRED FOR EXCEPTIONS TO THE
MINIMUM SUBSTANTIVE DEROGATORY STANDARDS FOR TERRORIST
WATCHLISTING
There are certain exceptions to the minimum substantive derogatory standards for TERRORIST
watchlisting that support immigration and visa screening activities by DHS and DOS.39
Examples of these categories of records include, but may not be limited to, records relating to
an individual who has a de?ned relationship with the KNOWN or TERRORIST, but
whose involvement with the KNOWN or SUSPECTED activities is unknown (TIDE
Category Code 50) and those with insuf?cient INFORMATION TO meet the
REASONABLE SUSPICION standard for watchlisting (TIDE Category Code 99).
NOMINATING AGENCIES should provide all additional identifying information available. All
nominations under this section must include a full name (?rst name, last name) and one of
the following identi?ers:
2.6.1 Full date of birth;
2.6.2 Full passport number (with or without country of issuance);
2.6.3 Unique identifying numbers such as alien registration numbers, visa numbers, and social
security account numbers;
2.6.4 Telephone number(s);
2.6.5 Email address(es);
2.6.6 License plate number(s);
2.6.7 Biometrics, such as facial image, iris scans or ?ngerprints.
39 See Chapter 3, Section V.
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 32

OR OFFICIAL USE SECURITY INFORMATION
I.
3.1
3.2
II.
3.3
3.4
CHAPTER 3: MINIMUM SUBSTANTIVE DEROGATORY CRITERIA
INTRODUCTION AND PURPOSE
TSC issued an updated US. Government Protocol Regarding Terrorist Nominations on
February 25, 2009, that included an appendix identifying the minimum substantive derogatory
criteria for acceptance of KNOWN or SUSPECTED TERRORIST nominations into the TSDB.
Based on the attempted terror attack of December 25, 2009, the Watchlisting Guidance was
reviewed to determine whether adjustments were needed. The revised guidance was approved
by the White House Deputies Committee on May 25, 2010 and issued to the watchlisting
community on July 16, 2010, after a multi-agency classi?cation review.
This Chapter of the Watchlisting Guidance has been updated to reflect the watchlisting
community?s experiences with the Guidance since issuance in July of 20] 0 by the Deputies
Committee. One of the more notable changes of this updated version of the Watchlisting
Guidance is the restructuring of instances for when PARTICULARIZED
INFORMATION is required. Another notable change includes the re-introduction of guidance
relative to the TERRORIST facilitators or supporters from an earlier version of the Watchlisting
Guidance and the inclusion of additional exceptions to the minimum substantive derogatory
standards for TERRORIST watchlisting that support immigration and visa screening activities of
the DOS and DHS.
REASONABLE SUSPICION
For purposes of watchlisting an individual to the TSDB, the should determine
whether there is REASONABLE SUSPICION that an individual is a KNOWN or SUSPECTED
TERRORIST.40
REASONABLE SUSPICION. To meet the REASONABLE SUSPICION standard, the
based on the totality of the circumstances, must rely upon articulable intelligence or
information which, taken together with rational inferences from those facts, reasonably
warrants a determination that an individual is known or suspected to be or has been knowingly
engaged in conduct constituting, in preparation for, in aid of, or related to TERRORISM and/or
TERRORIST ACTIVITIES. There must be an objective factual basis for the NOMINATOR to believe
that the individual is a KNOWN or TERRORIST. Mere guesses or hunches are not
suf?cient to constitute a REASONABLE SUSPICION that an individual is a KNOWN or
TERRORIST. Reporting of suspicious activity alone that does not meet the REASONABLE
SUSPICION standard set forth herein is not a suf?cient basis to watchlist an individual. The
facts, however, given fair consideration, should sensibly lead to the conclusion that an
individual is, or has, engaged in TERRORISM and/or ACTIVITIES.
4? ln instances where REASONABLE is not found, NOMINATORS should also determine whether the individual
should be nominated to support immigration and visa screening by DHS and DOS (see Chapter 3, Section V).
OR OFFICIAL USE SECURITY INFORMATION
Page 33
OR OFFICIAL USE SECURITY INFORMATION
I.
3.1
3.2
II.
3.3
3.4
CHAPTER 3: MINIMUM SUBSTANTIVE DEROGATORY CRITERIA
INTRODUCTION AND PURPOSE
TSC issued an updated US. Government Protocol Regarding Terrorist Nominations on
February 25, 2009, that included an appendix identifying the minimum substantive derogatory
criteria for acceptance of KNOWN or SUSPECTED TERRORIST nominations into the TSDB.
Based on the attempted terror attack of December 25, 2009, the Watchlisting Guidance was
reviewed to determine whether adjustments were needed. The revised guidance was approved
by the White House Deputies Committee on May 25, 2010 and issued to the watchlisting
community on July 16, 2010, after a multi-agency classi?cation review.
This Chapter of the Watchlisting Guidance has been updated to reflect the watchlisting
community?s experiences with the Guidance since issuance in July of 20] 0 by the Deputies
Committee. One of the more notable changes of this updated version of the Watchlisting
Guidance is the restructuring of instances for when PARTICULARIZED
INFORMATION is required. Another notable change includes the re-introduction of guidance
relative to the TERRORIST facilitators or supporters from an earlier version of the Watchlisting
Guidance and the inclusion of additional exceptions to the minimum substantive derogatory
standards for TERRORIST watchlisting that support immigration and visa screening activities of
the DOS and DHS.
REASONABLE SUSPICION
For purposes of watchlisting an individual to the TSDB, the should determine
whether there is REASONABLE SUSPICION that an individual is a KNOWN or SUSPECTED
TERRORIST.40
REASONABLE SUSPICION. To meet the REASONABLE SUSPICION standard, the
based on the totality of the circumstances, must rely upon articulable intelligence or
information which, taken together with rational inferences from those facts, reasonably
warrants a determination that an individual is known or suspected to be or has been knowingly
engaged in conduct constituting, in preparation for, in aid of, or related to TERRORISM and/or
TERRORIST ACTIVITIES. There must be an objective factual basis for the NOMINATOR to believe
that the individual is a KNOWN or TERRORIST. Mere guesses or hunches are not
suf?cient to constitute a REASONABLE SUSPICION that an individual is a KNOWN or
TERRORIST. Reporting of suspicious activity alone that does not meet the REASONABLE
SUSPICION standard set forth herein is not a suf?cient basis to watchlist an individual. The
facts, however, given fair consideration, should sensibly lead to the conclusion that an
individual is, or has, engaged in TERRORISM and/or ACTIVITIES.
4? ln instances where REASONABLE is not found, NOMINATORS should also determine whether the individual
should be nominated to support immigration and visa screening by DHS and DOS (see Chapter 3, Section V).
OR OFFICIAL USE SECURITY INFORMATION
Page 33

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.5
3.6
3.8
3.9
Due Weight. In determining whether a REASONABLE SUSPICION exists, due weight should be
given to the speci?c reasonable inferences that a NOMINATOR is entitled to draw fTom the facts
in light of his/her experience and not on unfounded suspicions or hunches. Although
irrefutable evidence or concrete facts are not necessary, to be reasonable, suspicion should be
as clear and as fully developed as circumstances permit. For additional guidance regarding
the nomination of PERSONS, see Paragraph 3.l5.
NOMINATORS shall not nominate an individual based on source reporting that NOMINATING
personnel identify as, or know to be, unreliable or not credible. Single source information,
including but not limited to ?walk-in?, ?write-in?, or postings on social media sites, however,
should not automatically be discounted merely because of the manner in which it was
received. Instead, the NOMINATING AGENCY should evaluate the credibility of the source, as
well as the nature and speci?city of the information, and nominate even if that source is
uncorroborated, assuming the information supports a REASONABLE SUSPICION that the
individual is a KNOWN or SUSPECTED TERRORIST or there is another basis for watchlisting the
individual.
Criteria and Data Quality. To demonstrate that the nomination has suf?cient indicia of
reliability to support a REASONABLE SUSPICION determination, NOMINATING AGENCIES should
incorporate processes designed to ensure that nominations are free of errors, and to the extent
possible given the nature of the reporting, have not come from sources known or determined
to be unreliable. NOMINATING AGENCIES should, to the extent possible, verify the accuracy
and reliability of the information included in nominations. In addition to ensuring that
nominations are free from errors, NOMINATING AGENCIES should implement procedures
designed to ensure that recalled or revised information is reviewed regularly, and that
necessary corrections to nominations based on those revisions/retractions are made.
DEROGATORY INFORMATION. PARTICULARIZED DEROGATORY
INFORMATION is the type of information relied on to determine whether REASONABLE
SUSPICION is met. This is information that demonstrates the nature of an individual?s or
group?s association with TERRORISM and/or TERRORIST ACTIVITIES that is descriptive and
speci?c to an event or activity, and is more than a label. For example, ?Subject provides
false travel documentation for Al-Qaida operatives? is PARTICULARIZED DEROGATORY
INFORMATION, whereas ?Subject is a supporter,? standing alone, is not considered
PARTICULA RIZED DEROGATORY INFORMATION.
Potential Behavioral Indicators. In making a REASONABLE SUSPICION determination,
NOMINATORS should consider behavioral indicators known to be associated with particular
KNOWN or SUSPECTED The following is a list of a few examples of those
indicators. It is not an exclusive list and it includes activity that may have innocent
explanations wholly unrelated to TERRORISM. Furthermore, some activities conducted by US
PERSONS or activities taking place within the United States, may be an exercise of rights
guaranteed by the First Amendment. Watchlisting an individual for engaging solely in
OFFICIAL USE SECURITY INFORMATION
Page 34
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.5
3.6
3.8
3.9
Due Weight. In determining whether a REASONABLE SUSPICION exists, due weight should be
given to the speci?c reasonable inferences that a NOMINATOR is entitled to draw fTom the facts
in light of his/her experience and not on unfounded suspicions or hunches. Although
irrefutable evidence or concrete facts are not necessary, to be reasonable, suspicion should be
as clear and as fully developed as circumstances permit. For additional guidance regarding
the nomination of PERSONS, see Paragraph 3.l5.
NOMINATORS shall not nominate an individual based on source reporting that NOMINATING
personnel identify as, or know to be, unreliable or not credible. Single source information,
including but not limited to ?walk-in?, ?write-in?, or postings on social media sites, however,
should not automatically be discounted merely because of the manner in which it was
received. Instead, the NOMINATING AGENCY should evaluate the credibility of the source, as
well as the nature and speci?city of the information, and nominate even if that source is
uncorroborated, assuming the information supports a REASONABLE SUSPICION that the
individual is a KNOWN or SUSPECTED TERRORIST or there is another basis for watchlisting the
individual.
Criteria and Data Quality. To demonstrate that the nomination has suf?cient indicia of
reliability to support a REASONABLE SUSPICION determination, NOMINATING AGENCIES should
incorporate processes designed to ensure that nominations are free of errors, and to the extent
possible given the nature of the reporting, have not come from sources known or determined
to be unreliable. NOMINATING AGENCIES should, to the extent possible, verify the accuracy
and reliability of the information included in nominations. In addition to ensuring that
nominations are free from errors, NOMINATING AGENCIES should implement procedures
designed to ensure that recalled or revised information is reviewed regularly, and that
necessary corrections to nominations based on those revisions/retractions are made.
DEROGATORY INFORMATION. PARTICULARIZED DEROGATORY
INFORMATION is the type of information relied on to determine whether REASONABLE
SUSPICION is met. This is information that demonstrates the nature of an individual?s or
group?s association with TERRORISM and/or TERRORIST ACTIVITIES that is descriptive and
speci?c to an event or activity, and is more than a label. For example, ?Subject provides
false travel documentation for Al-Qaida operatives? is PARTICULARIZED DEROGATORY
INFORMATION, whereas ?Subject is a supporter,? standing alone, is not considered
PARTICULA RIZED DEROGATORY INFORMATION.
Potential Behavioral Indicators. In making a REASONABLE SUSPICION determination,
NOMINATORS should consider behavioral indicators known to be associated with particular
KNOWN or SUSPECTED The following is a list of a few examples of those
indicators. It is not an exclusive list and it includes activity that may have innocent
explanations wholly unrelated to TERRORISM. Furthermore, some activities conducted by US
PERSONS or activities taking place within the United States, may be an exercise of rights
guaranteed by the First Amendment. Watchlisting an individual for engaging solely in
OFFICIAL USE SECURITY INFORMATION
Page 34

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
constitutionally protected activities is prohibited.? For these reasons, it is critical that each of
these activities?as with all possible indicators of TERRORIST be judged in
isolation. Each must be viewed in the context in which it occurs and considered in
combination with all other known information to ensure that any nomination based in whole
or in part on this behavior comports with the standards set forth above:
3.9.1 Attendance at training camps known to the IC as facilitating TERRORIST
3.9.2 Attendance at schools/institutions identi?ed by the as teaching an ideology that
includes thejusti?cation of the unlawful use of violence or violent extremism;
3.9.3 Repeated contact with individuals identi?ed by the 1C as teaching or espousing an
ideology that includes the justi?cation of the unlawful use of violence or violent
extremism; or,
3.9.4 Travel for no known lawful or legitimate purpose to a locus of ACTIVITY.
KNOWN TERRORISTS
3.l0 De?nitions.
3.10.1 KNOWN A KNOWN TERRORIST is an individual whom the US.
Government knows is engaged, has been engaged, or who intends to engage in
TERRORISM and/or TERRORIST ACTIVITY, including an individual who has been
charged, arrested, indicted, or convicted for a crime related to TERRORISM by US.
Government or foreign government authorities; or identi?ed as a TERRORIST or
member of a designated foreign terrorist organization pursuant to statute, Executive
Order or international legal obligation pursuant to a United Nations Security Council
Resolution.
3.10.2 TERRORISM and/or ACTIVITIES. In general, TERRORISM and/or
TERRORIST ACTIVITIES are acts that: involve violent acts or acts dangerous to human
life, property, or infrastructure that may be a violation of US. law, or may have been, if
those acts were committed in the United States; and, appear intended to intimidate or
coerce a civilian population, in?uence the policy of a government by intimidation or
coercion, or affect the conduct of government by mass destruction, assassination,
kidnapping, or hostage-taking. This includes activities that facilitate or support
4? See Chapter 1, Section
?2 Attendance at TERRORIST training camps alone meets the REASONABLE standard. Note that under the WA
section 212 U.S.C. an alien who has received military-type training (as
de?ned in section 2339D(c)(1) of Title l8, United States Code) from or on behalf of any organization that, at the time
the training was received, was a terrorist organization as de?ned in clause is inadmissible. Note also that 18 U.S.C.
section 23390 criminalizes receiving military type training from a designated foreign terrorist organization.
OFFICIAL USE SECURITY INFORMATION
Page 35
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
constitutionally protected activities is prohibited.? For these reasons, it is critical that each of
these activities?as with all possible indicators of TERRORIST be judged in
isolation. Each must be viewed in the context in which it occurs and considered in
combination with all other known information to ensure that any nomination based in whole
or in part on this behavior comports with the standards set forth above:
3.9.1 Attendance at training camps known to the IC as facilitating TERRORIST
3.9.2 Attendance at schools/institutions identi?ed by the as teaching an ideology that
includes thejusti?cation of the unlawful use of violence or violent extremism;
3.9.3 Repeated contact with individuals identi?ed by the 1C as teaching or espousing an
ideology that includes the justi?cation of the unlawful use of violence or violent
extremism; or,
3.9.4 Travel for no known lawful or legitimate purpose to a locus of ACTIVITY.
KNOWN TERRORISTS
3.l0 De?nitions.
3.10.1 KNOWN A KNOWN TERRORIST is an individual whom the US.
Government knows is engaged, has been engaged, or who intends to engage in
TERRORISM and/or TERRORIST ACTIVITY, including an individual who has been
charged, arrested, indicted, or convicted for a crime related to TERRORISM by US.
Government or foreign government authorities; or identi?ed as a TERRORIST or
member of a designated foreign terrorist organization pursuant to statute, Executive
Order or international legal obligation pursuant to a United Nations Security Council
Resolution.
3.10.2 TERRORISM and/or ACTIVITIES. In general, TERRORISM and/or
TERRORIST ACTIVITIES are acts that: involve violent acts or acts dangerous to human
life, property, or infrastructure that may be a violation of US. law, or may have been, if
those acts were committed in the United States; and, appear intended to intimidate or
coerce a civilian population, in?uence the policy of a government by intimidation or
coercion, or affect the conduct of government by mass destruction, assassination,
kidnapping, or hostage-taking. This includes activities that facilitate or support
4? See Chapter 1, Section
?2 Attendance at TERRORIST training camps alone meets the REASONABLE standard. Note that under the WA
section 212 U.S.C. an alien who has received military-type training (as
de?ned in section 2339D(c)(1) of Title l8, United States Code) from or on behalf of any organization that, at the time
the training was received, was a terrorist organization as de?ned in clause is inadmissible. Note also that 18 U.S.C.
section 23390 criminalizes receiving military type training from a designated foreign terrorist organization.
OFFICIAL USE SECURITY INFORMATION
Page 35

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
TERRORISM and/or ACTIVITIES.43
3.1 1 Types of KNOWN TERRORISTS for Whom REASONABLE SUSPICION is Established by
Recognized Authority and for Whom Particularized Derogatory Information is Not
Required.
3.1 1.1 Arrested or Convicted lndividuals who have been arrested or
convicted for TERRORIST ACTIVITY are considered KNOWN TERRORISTS who should be
nominated. The arrest or conviction is presumed to meet the REASONABLE SUSPICION
standard for watchlisting unless there is reason to believe that the information is
questionable faulty or erroneous), of dubious origin poison pen, source
known to be unreliable, or politically motivated) or the result of an unreliable process
conviction by a court that does not adhere to minimally acceptable due process
standards). Nominations should include the charge, location, and date of the arrest or
conviction, if available.
3.1 1.2 Individuals Identi?ed Pursuant to Statute or Executive Order.? Pursuant to
Executive Order 13224, as amended, ?Blocking Property and Prohibiting Transactions
with Persons who Commit, Threaten to Commit, or Support Terrorism,? Executive
Order 12947, as amended, ?Prohibiting Transactions with Terrorists Who Threaten to
Disrupt the Middle East Peace Process,? and section 302 of the Antiterrorism and
Effective Death Penalty Act of 1996 (AEDPA), the US. Department of the Treasury?s
Of?ce of Foreign Assets Control (OFAC) publishes, updates, and maintains an
integrated and comprehensive list of designated parties with whom U.S. PERSONS are
prohibited from providing services or conducting transactions and whose assets are
blocked. The names on this list include persons designated under country-based and
list-based economic sanctions programs, as well as individuals and entities designated
under the various Executive Orders and Statutes aimed at TERRORISM. Persons
designated under Executive Order 13224, Executive Order 12947, or the AEDPA are
included on this integrated and comprehensive list and are ?Specially Designated Global
Terrorists? ?Specially Designated Terrorists? (SDTs), or ?Foreign Terrorist
?3 TERRORISM and/or TERRORIST ACTIVITIES include acts that the actor knows or reasonably should know affords
material support to any individual who the actor knows or reasonably should know, has committed or plans to commit a
terrorist activity, to a terrorist organization or to any member of such an organization. Material support includes
providing a safe house, transportation, communications, funds, transfer of funds or other material benefit, false
documentation or identi?cation, weapons (including chemical, biological, or radiological weapons), explosives, or
training for the commission of an act of and/or TERRORIST
?4 See Paragraph 3.13.1 for situations involving individuals who are acquitted or against whom charges are dismissed
for a crime related to TERRORISM.
?5 These authorities generally authorize the Secretary of State (in consultation with either the Secretary of the Treasury,
the Attorney General, the Secretary of? Homeland Security, or a combination thereof) to designate and block the assets
of foreign individuals and entities that commit, or pose a signi?cant risk of committing, acts of TERRORISM that threaten
the security of US. nationals or the national security, foreign policy, or economy of the United States. Additionally,
leaders or members of a Foreign Terrorist Organization (PTO), an Specially Designated Global Terrorist (SDGT) under
Executive Order 13224, or an organization named to the Terrorist Exclusion List (TEL) may be designated as a terrorist
organization by the Secretary of State for immigration purposes pursuant to section 212(a)(3)(B)(vi)(11) [8 U.S.C.
1
OR OFFICIAL USE SECURITY INFORMATION
Page 36
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
TERRORISM and/or ACTIVITIES.43
3.1 1 Types of KNOWN TERRORISTS for Whom REASONABLE SUSPICION is Established by
Recognized Authority and for Whom Particularized Derogatory Information is Not
Required.
3.1 1.1 Arrested or Convicted lndividuals who have been arrested or
convicted for TERRORIST ACTIVITY are considered KNOWN TERRORISTS who should be
nominated. The arrest or conviction is presumed to meet the REASONABLE SUSPICION
standard for watchlisting unless there is reason to believe that the information is
questionable faulty or erroneous), of dubious origin poison pen, source
known to be unreliable, or politically motivated) or the result of an unreliable process
conviction by a court that does not adhere to minimally acceptable due process
standards). Nominations should include the charge, location, and date of the arrest or
conviction, if available.
3.1 1.2 Individuals Identi?ed Pursuant to Statute or Executive Order.? Pursuant to
Executive Order 13224, as amended, ?Blocking Property and Prohibiting Transactions
with Persons who Commit, Threaten to Commit, or Support Terrorism,? Executive
Order 12947, as amended, ?Prohibiting Transactions with Terrorists Who Threaten to
Disrupt the Middle East Peace Process,? and section 302 of the Antiterrorism and
Effective Death Penalty Act of 1996 (AEDPA), the US. Department of the Treasury?s
Of?ce of Foreign Assets Control (OFAC) publishes, updates, and maintains an
integrated and comprehensive list of designated parties with whom U.S. PERSONS are
prohibited from providing services or conducting transactions and whose assets are
blocked. The names on this list include persons designated under country-based and
list-based economic sanctions programs, as well as individuals and entities designated
under the various Executive Orders and Statutes aimed at TERRORISM. Persons
designated under Executive Order 13224, Executive Order 12947, or the AEDPA are
included on this integrated and comprehensive list and are ?Specially Designated Global
Terrorists? ?Specially Designated Terrorists? (SDTs), or ?Foreign Terrorist
?3 TERRORISM and/or TERRORIST ACTIVITIES include acts that the actor knows or reasonably should know affords
material support to any individual who the actor knows or reasonably should know, has committed or plans to commit a
terrorist activity, to a terrorist organization or to any member of such an organization. Material support includes
providing a safe house, transportation, communications, funds, transfer of funds or other material benefit, false
documentation or identi?cation, weapons (including chemical, biological, or radiological weapons), explosives, or
training for the commission of an act of and/or TERRORIST
?4 See Paragraph 3.13.1 for situations involving individuals who are acquitted or against whom charges are dismissed
for a crime related to TERRORISM.
?5 These authorities generally authorize the Secretary of State (in consultation with either the Secretary of the Treasury,
the Attorney General, the Secretary of? Homeland Security, or a combination thereof) to designate and block the assets
of foreign individuals and entities that commit, or pose a signi?cant risk of committing, acts of TERRORISM that threaten
the security of US. nationals or the national security, foreign policy, or economy of the United States. Additionally,
leaders or members of a Foreign Terrorist Organization (PTO), an Specially Designated Global Terrorist (SDGT) under
Executive Order 13224, or an organization named to the Terrorist Exclusion List (TEL) may be designated as a terrorist
organization by the Secretary of State for immigration purposes pursuant to section 212(a)(3)(B)(vi)(11) [8 U.S.C.
1
OR OFFICIAL USE SECURITY INFORMATION
Page 36

OR OFFICIAL USE SECURITY INFORMATION
Organizations? (FTOs), respectively, and should be nominated accordingly.46
NOMINATORS should regularly check the Specially Designated Nationals List (SDNL) as
individuals are added and drOpped as new information becomes available.
Individuals Identi?ed as TERRORISTS Pursuant to a United Nations Security
Council Resolutions (UNSCR) Concerning Al-Qaida and Associated Individuals
and Entities. Under UNSCR resolution 1267 (1999), modi?ed and strengthened by
subsequent resolutions, including resolutions 1333 (2000), 1390 (2002), 1445 (2003),
1526 (2004), 1617 (2005), 1735 (2006), 1822 (2008), 1904 (2009), and resolution 1989
(201 sanctions measures now apply to designated individuals and entities associated
with Al?Qaida, wherever located. The names of the targeted individuals and entities are
placed on the Al-Qaida Sanctions List.47 Under the UNSCR sanctions regime, the
United States has an international legal obligation to prevent the entry into or transit
through its territory of designated individuals listed on the Al-Qaida Sanctions List.48
should regularly check the Al-Qaida Sanctions List as individuals are
added and dropped as new information becomes available.
3.11.4 Individuals Identified as TERRORISTS Pursuant to the National Intelligence
Priorities Framework of Counterterrorism. Members of groups (not support entities)
that are identi?ed on the National Intelligence Priorities Framework of
Counterterrorism, are presumed to meet the REASONABLE standard
so long as the group name is not just a regional or activity-based characterization.
Neutral associations such as janitorial, repair, or delivery services of commercial goods
do not meet the REASONABLE SUSPICION standard.
IV. SUSPECTED TERRORISTS
3.12 De?nition.
3.12.1 A SUSPECTED is an individual who is REASONABLY SUSPECTED to be, or
has been, engaged in conduct constituting, in preparation for, in aid of, or related to
TERRORISM and/or TERRORIST ACTIVITIES based on an articulable and REASONABLE
3.13 Types of SUSPECTED
4? The comprehensive list of and is accessible through the OFAC website at the following URL:
?7 Narrative summaries of the reasons for listing individuals, groups, undertakings and entities on the Al-Qaida
Sanctions List (where available) can be found at the following URL:
mittces/l
48 Many persons designated under UNSCR l267 and Executive Order 13224 are or have been engaged in financial
support, facilitation, and other activities in support of TERRORISM. They o?en, however, do not meet the current criteria
for placement on the No Fly List. and DOS will review the information provided about these individuals and take
actions, as appropriate.
OR OFFICIAL USE SECURITY INFORMATION
Page 37
OR OFFICIAL USE SECURITY INFORMATION
Organizations? (FTOs), respectively, and should be nominated accordingly.46
NOMINATORS should regularly check the Specially Designated Nationals List (SDNL) as
individuals are added and drOpped as new information becomes available.
Individuals Identi?ed as TERRORISTS Pursuant to a United Nations Security
Council Resolutions (UNSCR) Concerning Al-Qaida and Associated Individuals
and Entities. Under UNSCR resolution 1267 (1999), modi?ed and strengthened by
subsequent resolutions, including resolutions 1333 (2000), 1390 (2002), 1445 (2003),
1526 (2004), 1617 (2005), 1735 (2006), 1822 (2008), 1904 (2009), and resolution 1989
(201 sanctions measures now apply to designated individuals and entities associated
with Al?Qaida, wherever located. The names of the targeted individuals and entities are
placed on the Al-Qaida Sanctions List.47 Under the UNSCR sanctions regime, the
United States has an international legal obligation to prevent the entry into or transit
through its territory of designated individuals listed on the Al-Qaida Sanctions List.48
should regularly check the Al-Qaida Sanctions List as individuals are
added and dropped as new information becomes available.
3.11.4 Individuals Identified as TERRORISTS Pursuant to the National Intelligence
Priorities Framework of Counterterrorism. Members of groups (not support entities)
that are identi?ed on the National Intelligence Priorities Framework of
Counterterrorism, are presumed to meet the REASONABLE standard
so long as the group name is not just a regional or activity-based characterization.
Neutral associations such as janitorial, repair, or delivery services of commercial goods
do not meet the REASONABLE SUSPICION standard.
IV. SUSPECTED TERRORISTS
3.12 De?nition.
3.12.1 A SUSPECTED is an individual who is REASONABLY SUSPECTED to be, or
has been, engaged in conduct constituting, in preparation for, in aid of, or related to
TERRORISM and/or TERRORIST ACTIVITIES based on an articulable and REASONABLE
3.13 Types of SUSPECTED
4? The comprehensive list of and is accessible through the OFAC website at the following URL:
?7 Narrative summaries of the reasons for listing individuals, groups, undertakings and entities on the Al-Qaida
Sanctions List (where available) can be found at the following URL:
mittces/l
48 Many persons designated under UNSCR l267 and Executive Order 13224 are or have been engaged in financial
support, facilitation, and other activities in support of TERRORISM. They o?en, however, do not meet the current criteria
for placement on the No Fly List. and DOS will review the information provided about these individuals and take
actions, as appropriate.
OR OFFICIAL USE SECURITY INFORMATION
Page 37

UN CLASSIF OFFICIAL USE ON SITIVE SECURITY INFORMATION
3. 3.l Individuals Who are Acquitted or for Whom Charges are Dismissed. An
individual who is acquitted or against whom charges are dismissed for a crime related to
TERRORISM may nevertheless meet the REASONABLE standard and
appropriately remain on, or be nominated to, the Terrorist Watchlist.49 Each case should
be evaluated based on the facts of the underlying activities, the circumstances
surrounding the acquittal or dismissal, and all known DEROGATORY INFORMATION to
determine if the individual should remain on the Terrorist Watchlist.
3.13.2 Individuals Identified as TERRORISTS Pursuant to Other Internal Department or
Agency Processes. Departments or Agencies that nominate individuals associated with
a terrorist group that is not designated by Statute or Executive Order (see Paragraph
3.1 1.2) or groups that fall outside of the construct (see Paragraph 3.1 1.4) must
have internal processes to review the activities Of TERRORISTS and terrorist
organizations. 80 long as a Department?s or Agency?s internal process has determined
that a group is engaging in TERRORISM and/or ACTIVITIES, REASONABLE
SUSPICION can be met for members of the group, or active participants in, that group?s
ACTIVITIES. Departments and Agencies that use this clause to recommend
subjects for watchlisting are required to provide written notice to NCTC and TSC (an
email will suf?ce) of the Department or Agency?s determination. While members or
active participants Of such groups may be nominated without PARTICULARIZED
DEROGATORY INFORMATION, the watchlisting of an individual pursuant to this clause
must be based on the determination by a Department or Agency?s internal processes that
the group is engaging in TERRORISM and/or TERRORIST ACTIVITIES. Neutral associations
like janitorial, repair, or delivery services Of commercial goods do not meet the
REASONABLE SUSPICION standard.
3.13.3 Individuals Identi?ed as Pursuant to Agreements by US.
Government Agencies/Foreign Governments for Sharing of TERRORIST Identity
Data. The US. Government may enter into agreements with foreign governments for
the sharing Of identity information. Pursuant to such agreements, data will
be provided to the TSC for TERRORIST screening, as required under The
Information Sharing and Access (ISA) lnteragency Policy Committee or an IPC-
designated interagency body, will make a determination, country by country, prior to the
?nal agreement on whether the data provided will (I) be presumed to meet the standard
for inclusion in or (2) undergo the Foreign Partner Vetting Process.
3. 3.4 Individuals Identi?ed as Associates or Af?liates of KNOWN or
TERRORISTS or TERRORIST Cells or Networks.50 Individuals who are associated or
affiliated with a KNOWN or SUSPECTED TERRORIST, or TIERRORIST cells or networks
should be nominated when there is PARTICULARIZED DEROGATORY INFORMATION
49 Because the REASONABLE SUSPICION standard required for watchlisting is lower than that required for a criminal
conviction beyond a reasonable doubt), an individual that is acquitted or for whom charges are dismissed may
qualify for watchlisting based on the facts and circumstances surrounding the acquittal or dismissal.
50 This section applies as well to persons ?linked to,? ?related? and other similar descriptOrs to a KNOWN or
TERRORIST, TERRORIST cells or networks.
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 38
UN CLASSIF OFFICIAL USE ON SITIVE SECURITY INFORMATION
3. 3.l Individuals Who are Acquitted or for Whom Charges are Dismissed. An
individual who is acquitted or against whom charges are dismissed for a crime related to
TERRORISM may nevertheless meet the REASONABLE standard and
appropriately remain on, or be nominated to, the Terrorist Watchlist.49 Each case should
be evaluated based on the facts of the underlying activities, the circumstances
surrounding the acquittal or dismissal, and all known DEROGATORY INFORMATION to
determine if the individual should remain on the Terrorist Watchlist.
3.13.2 Individuals Identified as TERRORISTS Pursuant to Other Internal Department or
Agency Processes. Departments or Agencies that nominate individuals associated with
a terrorist group that is not designated by Statute or Executive Order (see Paragraph
3.1 1.2) or groups that fall outside of the construct (see Paragraph 3.1 1.4) must
have internal processes to review the activities Of TERRORISTS and terrorist
organizations. 80 long as a Department?s or Agency?s internal process has determined
that a group is engaging in TERRORISM and/or ACTIVITIES, REASONABLE
SUSPICION can be met for members of the group, or active participants in, that group?s
ACTIVITIES. Departments and Agencies that use this clause to recommend
subjects for watchlisting are required to provide written notice to NCTC and TSC (an
email will suf?ce) of the Department or Agency?s determination. While members or
active participants Of such groups may be nominated without PARTICULARIZED
DEROGATORY INFORMATION, the watchlisting of an individual pursuant to this clause
must be based on the determination by a Department or Agency?s internal processes that
the group is engaging in TERRORISM and/or TERRORIST ACTIVITIES. Neutral associations
like janitorial, repair, or delivery services Of commercial goods do not meet the
REASONABLE SUSPICION standard.
3.13.3 Individuals Identi?ed as Pursuant to Agreements by US.
Government Agencies/Foreign Governments for Sharing of TERRORIST Identity
Data. The US. Government may enter into agreements with foreign governments for
the sharing Of identity information. Pursuant to such agreements, data will
be provided to the TSC for TERRORIST screening, as required under The
Information Sharing and Access (ISA) lnteragency Policy Committee or an IPC-
designated interagency body, will make a determination, country by country, prior to the
?nal agreement on whether the data provided will (I) be presumed to meet the standard
for inclusion in or (2) undergo the Foreign Partner Vetting Process.
3. 3.4 Individuals Identi?ed as Associates or Af?liates of KNOWN or
TERRORISTS or TERRORIST Cells or Networks.50 Individuals who are associated or
affiliated with a KNOWN or SUSPECTED TERRORIST, or TIERRORIST cells or networks
should be nominated when there is PARTICULARIZED DEROGATORY INFORMATION
49 Because the REASONABLE SUSPICION standard required for watchlisting is lower than that required for a criminal
conviction beyond a reasonable doubt), an individual that is acquitted or for whom charges are dismissed may
qualify for watchlisting based on the facts and circumstances surrounding the acquittal or dismissal.
50 This section applies as well to persons ?linked to,? ?related? and other similar descriptOrs to a KNOWN or
TERRORIST, TERRORIST cells or networks.
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 38

OR OFFICIAL USE SECURITY INFORMATION
regarding the context of the relationship that gives rise to a REASONABLE SUSPICION that
the individual is engaging or has engaged in conduct constituting, in preparation for, in
aid of, or related to TERRORISM and/or TERRORIST ACTIVITIES. Neutral associations such
as janitorial, repair, or delivery services of commercial goods are not sufficient.
Information about the pertinent activities of the KNOWN or SUSPECTED TERRORIST,
TERRORIST cell or network should be included in the nomination. These nominations
should include context or content to demonstrate the membership, association, or
af?liation to the KNOWN or SUSPECTRD TERRORIST, TERRORIST cell or network.
Individuals who merely ?may be? members, associates or af?liates to a terrorist
organization may not be accepted into the TSDB, unless the REASONABLE SUSPICION
standard is met and PARTICULARIZED DEROGATORY INFORMATION accompanies the
nomination.
3.13.4.1 Inferences that Support REASONABLE SUSPICION. REASONABLE SUSPICION
may be rationally inferred from the context of the relationship with the KNOWN or
SUSPECTED TERRORIST. The following factors should be considered when
determining whether REASONABLE SUSPICION may be inferred:
3.13.4.1 .l The nature of the activity engaged in with the KNOWN or
3.13.4.1 .2 The frequency, duration, or manner of their contact;
3.13.4.1 .3 A close, continuing, or direct relationship with a KNOWN or
SUSPECTED TERRORIST that reasonably suggests the individual is knowingly
involved in or willfully supporting the KNOWN or SUSPECTED
TERRORIST Ol?,
3.13.4.1.4 Other malevolent or illicit factors that can be articulated that would
support a REASONABLE SUSPICION that the individual is engaging in
TERRORISM and/or TERRORIST ACTIVITIES.
3. I 3.5 Individuals Identi?ed as TERRORIST Facilitators. TERRORIST facilitators are
presumed to meet the REASONABLE SUSPICION standard. The nomination should include
PARTICULARIZED DEROGATORY INFORMATION concerning the type of ?facilitation?
involved and the role of the facilitator when this information is known. Individuals who
are considered facilitators include, but are not limited to, financial fundraisers, document
forgers, travel facilitators, money launderers, and arms merchants. There must be
REASONABLE SUSPICION that the facilitator knew that his or her actions would aid in the
furtherance of TERRORISM and/or TERRORIST ACTIVITIES.
3.13.5.1 Criminal Activity Supporting TERRORISM. If intelligence or information
indicates that the individual is engaging in criminal activity related to smuggling,
providing safe houses, forging documents, or any other support to TERRORISTS or
terrorist groups, NOMINATORS should presume that the individual is knowingly
engaging in criminal activity that supports TERRORISM and/ or TERRORIST
OR OFFICIAL USE SECURITY INFORMATION
Page 39
OR OFFICIAL USE SECURITY INFORMATION
regarding the context of the relationship that gives rise to a REASONABLE SUSPICION that
the individual is engaging or has engaged in conduct constituting, in preparation for, in
aid of, or related to TERRORISM and/or TERRORIST ACTIVITIES. Neutral associations such
as janitorial, repair, or delivery services of commercial goods are not sufficient.
Information about the pertinent activities of the KNOWN or SUSPECTED TERRORIST,
TERRORIST cell or network should be included in the nomination. These nominations
should include context or content to demonstrate the membership, association, or
af?liation to the KNOWN or SUSPECTRD TERRORIST, TERRORIST cell or network.
Individuals who merely ?may be? members, associates or af?liates to a terrorist
organization may not be accepted into the TSDB, unless the REASONABLE SUSPICION
standard is met and PARTICULARIZED DEROGATORY INFORMATION accompanies the
nomination.
3.13.4.1 Inferences that Support REASONABLE SUSPICION. REASONABLE SUSPICION
may be rationally inferred from the context of the relationship with the KNOWN or
SUSPECTED TERRORIST. The following factors should be considered when
determining whether REASONABLE SUSPICION may be inferred:
3.13.4.1 .l The nature of the activity engaged in with the KNOWN or
3.13.4.1 .2 The frequency, duration, or manner of their contact;
3.13.4.1 .3 A close, continuing, or direct relationship with a KNOWN or
SUSPECTED TERRORIST that reasonably suggests the individual is knowingly
involved in or willfully supporting the KNOWN or SUSPECTED
TERRORIST Ol?,
3.13.4.1.4 Other malevolent or illicit factors that can be articulated that would
support a REASONABLE SUSPICION that the individual is engaging in
TERRORISM and/or TERRORIST ACTIVITIES.
3. I 3.5 Individuals Identi?ed as TERRORIST Facilitators. TERRORIST facilitators are
presumed to meet the REASONABLE SUSPICION standard. The nomination should include
PARTICULARIZED DEROGATORY INFORMATION concerning the type of ?facilitation?
involved and the role of the facilitator when this information is known. Individuals who
are considered facilitators include, but are not limited to, financial fundraisers, document
forgers, travel facilitators, money launderers, and arms merchants. There must be
REASONABLE SUSPICION that the facilitator knew that his or her actions would aid in the
furtherance of TERRORISM and/or TERRORIST ACTIVITIES.
3.13.5.1 Criminal Activity Supporting TERRORISM. If intelligence or information
indicates that the individual is engaging in criminal activity related to smuggling,
providing safe houses, forging documents, or any other support to TERRORISTS or
terrorist groups, NOMINATORS should presume that the individual is knowingly
engaging in criminal activity that supports TERRORISM and/ or TERRORIST
OR OFFICIAL USE SECURITY INFORMATION
Page 39

OR OFFICIAL USE SECURITY INFORMATION
In these circumstances, REASONABLE SUSPICION is based on the
TERRORIST criminal activity and should be described in the nomination.
3.13.6 Individuals who Incite Others to Commit Acts of inciting an
individual to commit an act of TERRORISM and/or TERRORIST ACTIVITIES under
circumstances that indicate an intention to cause death or serious bodily harm is
considered engaging in TERRORIST ACTIVITY and is suf?cient to meet the REASONABLE
SUSPICION standard. The nomination should include PARTICULARIZED DEROOATORY
INFORMATION concerning the type of ?incitement? involved and the role of the
individual when this information is known. Normally, speech will not rise to the level of
?inciting? unless there is a clear link between the speech and an actual effort to
undertake the TERRORIST ACTIVITY. The individual may have incited TERRORIST
ACTIVITY, even if a terrorist attack does not actually occur because an attempt to
commit such activity is thwarted). Speech advocating a violent or dangerous TERRORIST
ACTIVITY is incitement if such advocacy is directed to incitinzg or producing imminent
lawless action and is likely to incite or produce such action.5
3.13.7 Individuals Who Solicit Others to Engage in TERRORIST ACTIVITIES. In an
individual capacity or as a member Of an organization, any individual who solicits
another to engage in a ACTIVITY and/or for membership in a terrorist
organization is considered to be engaging in ACTIVITY. Nominations that
include PARTICULARIZED DEROGATORY INFORMATION concerning the type of solicitation
involved and the role of the individual are sufficient to meet the REASONABLE SUSPICION
standard. An individual may fall outside the scope of engaging in the solicitation of an
individual for membership in a terrorist organization if there is information that
demonstrates that the individual did not know and should not have reasonably known
that the organization was a terrorist organization.
3.13.8 Individuals Identi?ed as Sympathizers and Supporters of a Designated Terrorist
Organizations? Sympathizers and supporters of a designated terrorist organization
(DTO) (see Paragraph 3.1 1.2) may be watchlisted when the REASONABLE SUSPICION
standard is met, and the nomination includes PARTICULARIZED DEROGATORY
INFORMATION concerning the how the individual?s activities warrant watchlisting, as
opposed to information about why the organization is a DTO.
3.13.8.1 A sympathizer or supporter of TERRORISM should be nominated if the support
is Operational in nature. If support is merely ideological, the individual should not
be nominated.
5 For situations where there is no DEROGATORY INFORMATION, individuals may be watchlisted as an
exception to the REASONABLE SUSPICION standard. See Paragraph 3.14.3.
52 Ashcroft v. Free Speech Coalition, 535 US. 234, 122 1389 (2002); 9 AM 40.32 N25, ?Advocacy of Terrorism
Not Always Exclusionary."
5?1 For situations where there is no PARTICULARIZED INFORMATION, supporters of a designated terrorist
organization (DTO) may be watchlisted as an exception to the REASONABLE SUSPICION standard. See Paragraph 3.14.4.
OR OFFICIAL USE SECURITY INFORMATION
Page 40
OR OFFICIAL USE SECURITY INFORMATION
In these circumstances, REASONABLE SUSPICION is based on the
TERRORIST criminal activity and should be described in the nomination.
3.13.6 Individuals who Incite Others to Commit Acts of inciting an
individual to commit an act of TERRORISM and/or TERRORIST ACTIVITIES under
circumstances that indicate an intention to cause death or serious bodily harm is
considered engaging in TERRORIST ACTIVITY and is suf?cient to meet the REASONABLE
SUSPICION standard. The nomination should include PARTICULARIZED DEROOATORY
INFORMATION concerning the type of ?incitement? involved and the role of the
individual when this information is known. Normally, speech will not rise to the level of
?inciting? unless there is a clear link between the speech and an actual effort to
undertake the TERRORIST ACTIVITY. The individual may have incited TERRORIST
ACTIVITY, even if a terrorist attack does not actually occur because an attempt to
commit such activity is thwarted). Speech advocating a violent or dangerous TERRORIST
ACTIVITY is incitement if such advocacy is directed to incitinzg or producing imminent
lawless action and is likely to incite or produce such action.5
3.13.7 Individuals Who Solicit Others to Engage in TERRORIST ACTIVITIES. In an
individual capacity or as a member Of an organization, any individual who solicits
another to engage in a ACTIVITY and/or for membership in a terrorist
organization is considered to be engaging in ACTIVITY. Nominations that
include PARTICULARIZED DEROGATORY INFORMATION concerning the type of solicitation
involved and the role of the individual are sufficient to meet the REASONABLE SUSPICION
standard. An individual may fall outside the scope of engaging in the solicitation of an
individual for membership in a terrorist organization if there is information that
demonstrates that the individual did not know and should not have reasonably known
that the organization was a terrorist organization.
3.13.8 Individuals Identi?ed as Sympathizers and Supporters of a Designated Terrorist
Organizations? Sympathizers and supporters of a designated terrorist organization
(DTO) (see Paragraph 3.1 1.2) may be watchlisted when the REASONABLE SUSPICION
standard is met, and the nomination includes PARTICULARIZED DEROGATORY
INFORMATION concerning the how the individual?s activities warrant watchlisting, as
opposed to information about why the organization is a DTO.
3.13.8.1 A sympathizer or supporter of TERRORISM should be nominated if the support
is Operational in nature. If support is merely ideological, the individual should not
be nominated.
5 For situations where there is no DEROGATORY INFORMATION, individuals may be watchlisted as an
exception to the REASONABLE SUSPICION standard. See Paragraph 3.14.3.
52 Ashcroft v. Free Speech Coalition, 535 US. 234, 122 1389 (2002); 9 AM 40.32 N25, ?Advocacy of Terrorism
Not Always Exclusionary."
5?1 For situations where there is no PARTICULARIZED INFORMATION, supporters of a designated terrorist
organization (DTO) may be watchlisted as an exception to the REASONABLE SUSPICION standard. See Paragraph 3.14.4.
OR OFFICIAL USE SECURITY INFORMATION
Page 40

UN OR OFFICIAL USE SECURITY INFORMATION
3. 3.9 Individuals Identi?ed as FOREIGN FIGHTERS. FOREIGN FIGHTERS are de?ned as
nationals of one country who travel or attempt to travel to another country to participate
in TERRORISM and/or TERRORIST ACTIVITIES, and to the extent possible, the nomination
should include PARTICULARIZED DEROGATORY INFORMATION. Behavior that quali?es as
PARTICULARIZED DEROGATORY INFORMATION is the travel to a foreign country to
participate in TERRORISM and/or TERRORIST ACTIVITIES.
3. 3.9.l A person is not considered a FOREIGN FIGHTER when he or she traveled from
Country A to Country for reasons enrolling in school).
lnferences that someone is a FOREIGN FIGHTER may not be drawn solely from
biographic facts that indicate a person was born in one country and is found in a
different country and suspected to be participating in TERRORISM and/or TERRORIST
ACTIVITIES.
3.13.10 Special Consideration for Individuals Involved with
Weapons. lndividuals who possess, handle, use, manufacture, sell, or transfer
Improvised Explosive Devices Explosiver Formed Penetrators (EFP),
Radiological Dispersion Devices (RDD), or improvised chemical, biological,
radiological, or nuclear (CBRN) devices, are presumed to meet the REASONABLE
SUSPICION standard due to the inherently dangerous nature of these items or when it can
reasonably be inferred from the context that there is a connection to TERRORISM and/or
TERRORIST ACTIVITIES lraq, presence of other KNOWN or SUSPECTED
previous attacks on or threats to U.S. Forces).
3.13.] Targets of Raids Conducted by the U.S. Military or the Intelligence
Community. REASONABLE SUSPICION is presumed where an individual was identi?ed as
the target of a raid to disrupt a FTO. When an individual is identi?ed by discovery of
information found during the course of such a raid conducted by the U.S. Military or the
1C, however, REASONABLE is met where the available PARTICULARIZED
DEROGATORY INFORMATION explains why he or she can be reasonably suspected of
engaging or having engaged in conduct constituting, in preparation for, in aid of, or
related to TERRORISM and/or TERRORIST ACTIVITY. If there is no
INFORMATION on the individual for whom information was discovered
during the raid, he or She should not be nominated.
3.13.12 Individuals Identi?ed as TERRORISTS via Documentation or Media Exploitation
Efforts. Any individuals identi?ed in documents or media otherwise captured by U.S.
or allied forces or obtained from a NOMINATING AGENCY must have a connection to
TERRORISM and/or TERRORIST ACTIVITIES in order to be nominated to the Terrorist
Watchlist. REASONABLE SUSPICION for an individual to be nominated from document
and media exploitation (DOMEX) materials may be established either by the content or
context of the DOMEX, or other sources. Nominations under this section must include
DEROGATORY INFORMATION. For example, REASONABLE SUSPICION for
watchlisting can be met based on the acquisition of documents/media identifying a
person from the counterterrorism operation that targeted the residence of Al-Qaida
OFFICIAL USE SECURITY INFORMATION
Page 4
UN OR OFFICIAL USE SECURITY INFORMATION
3. 3.9 Individuals Identi?ed as FOREIGN FIGHTERS. FOREIGN FIGHTERS are de?ned as
nationals of one country who travel or attempt to travel to another country to participate
in TERRORISM and/or TERRORIST ACTIVITIES, and to the extent possible, the nomination
should include PARTICULARIZED DEROGATORY INFORMATION. Behavior that quali?es as
PARTICULARIZED DEROGATORY INFORMATION is the travel to a foreign country to
participate in TERRORISM and/or TERRORIST ACTIVITIES.
3. 3.9.l A person is not considered a FOREIGN FIGHTER when he or she traveled from
Country A to Country for reasons enrolling in school).
lnferences that someone is a FOREIGN FIGHTER may not be drawn solely from
biographic facts that indicate a person was born in one country and is found in a
different country and suspected to be participating in TERRORISM and/or TERRORIST
ACTIVITIES.
3.13.10 Special Consideration for Individuals Involved with
Weapons. lndividuals who possess, handle, use, manufacture, sell, or transfer
Improvised Explosive Devices Explosiver Formed Penetrators (EFP),
Radiological Dispersion Devices (RDD), or improvised chemical, biological,
radiological, or nuclear (CBRN) devices, are presumed to meet the REASONABLE
SUSPICION standard due to the inherently dangerous nature of these items or when it can
reasonably be inferred from the context that there is a connection to TERRORISM and/or
TERRORIST ACTIVITIES lraq, presence of other KNOWN or SUSPECTED
previous attacks on or threats to U.S. Forces).
3.13.] Targets of Raids Conducted by the U.S. Military or the Intelligence
Community. REASONABLE SUSPICION is presumed where an individual was identi?ed as
the target of a raid to disrupt a FTO. When an individual is identi?ed by discovery of
information found during the course of such a raid conducted by the U.S. Military or the
1C, however, REASONABLE is met where the available PARTICULARIZED
DEROGATORY INFORMATION explains why he or she can be reasonably suspected of
engaging or having engaged in conduct constituting, in preparation for, in aid of, or
related to TERRORISM and/or TERRORIST ACTIVITY. If there is no
INFORMATION on the individual for whom information was discovered
during the raid, he or She should not be nominated.
3.13.12 Individuals Identi?ed as TERRORISTS via Documentation or Media Exploitation
Efforts. Any individuals identi?ed in documents or media otherwise captured by U.S.
or allied forces or obtained from a NOMINATING AGENCY must have a connection to
TERRORISM and/or TERRORIST ACTIVITIES in order to be nominated to the Terrorist
Watchlist. REASONABLE SUSPICION for an individual to be nominated from document
and media exploitation (DOMEX) materials may be established either by the content or
context of the DOMEX, or other sources. Nominations under this section must include
DEROGATORY INFORMATION. For example, REASONABLE SUSPICION for
watchlisting can be met based on the acquisition of documents/media identifying a
person from the counterterrorism operation that targeted the residence of Al-Qaida
OFFICIAL USE SECURITY INFORMATION
Page 4

OR OFFICIAL USE SECURITY INFORMATION
leader Usama bin Laden on May 2, 201 1.54 Likewise, individuals listed on a roster of an
IED cell could be nominated solely on the presence of their name on the list. An
identity from a captured passport, however, would only be watchlisted if additional
reporting documents REASONABLE SUSPICION to believe that the individual is connected
to TERRORISM and/or TERRORIST ACTIVITY.
3.13.13 LONE WOLVES. Because the focus is on the individual?s conduct,
should be nominated when DEROGATORY
INFORMATION and their actions support a REASONABLE that they are engaged
in, or have engaged in, TERRORISM and/or ACTIVITIES. No present known
af?liation with a terror group, organization, or cell is required but prior af?liations, if
they exist, may be taken into account for supporting a rational inference that the
individual is reasonably suspected of engaging in TERRORISM and/or
ACTIVITIES.
V. EXCEPTIONS TO SUPPORT IMMIGRATION AND VISA SCREENING
ACTIVITIES BY DHS AND DOS
3.14 TSDB Minimum Substantive Derogatory Exceptions to Support Immigration and Visa
Screening Activities by the DHS and DOS. The Watchlisting Guidance contains certain
exceptions to the minimum substantive derogatory criteria for watchlisting that
support immigration and visa screening activities by the DHS and DOS to determine whether
grounds exist to deny admission of aliens to the United States (including denials of visas) or to
deny other immigration bene?ts pursuant to the INA.55 DEROGATORY
INFORMATION is not required for nominations made pursuant to the following sections.
Because the INA de?nes ?aliens? as ?any person not a citizen or national of the United
States?56, the admissibility provisions also apply to LPRs, in certain circumstances
including those described in INA section U.S.C. lOl(a)(l who are
considered as U.S. PERSONS under Executive Order 12333. Consequently, NCTC developed a
mechanism in TIDE to identify and distinguish U.S. citizens from non?U.S. citizens in order
to further distinguish between ?aliens? under the INA and U.S. PERSONS under Executive
Order 12333. The following subsections are exceptions to the REASONABLE
standard and will only be transmitted to CLASS (via the DOS CCD) and WLS
to support immigration and visa screening processes.
5? Such documents/media, however, still need to be reviewed to ensure that innocent individuals are not erroneously
watchlisted.
5? INA section SC. I sets forth several grounds for inadmissibility based on terrorist
activities, which is de?ned in INA section U.S.C. 1 For example, INA section
212(a)(3)(B)(i)(Vll) states that any alien who ?endorses or espouses terrorist activity or persuades others to endorse or
espouse terrorist activity or support a terrorist organization? is inadmissible to the United States. 8 U.S.C.
All other uses of the term ?terrorist activities? within this Watchlisting Guidance that do not
speci?cally reference the INA follow the de?nition outlined in Chapter 1 and Appendix 1.
5 See INA U.S.C.
OFFICIAL USE ON SECURITY INFORMATION
Page 42
OR OFFICIAL USE SECURITY INFORMATION
leader Usama bin Laden on May 2, 201 1.54 Likewise, individuals listed on a roster of an
IED cell could be nominated solely on the presence of their name on the list. An
identity from a captured passport, however, would only be watchlisted if additional
reporting documents REASONABLE SUSPICION to believe that the individual is connected
to TERRORISM and/or TERRORIST ACTIVITY.
3.13.13 LONE WOLVES. Because the focus is on the individual?s conduct,
should be nominated when DEROGATORY
INFORMATION and their actions support a REASONABLE that they are engaged
in, or have engaged in, TERRORISM and/or ACTIVITIES. No present known
af?liation with a terror group, organization, or cell is required but prior af?liations, if
they exist, may be taken into account for supporting a rational inference that the
individual is reasonably suspected of engaging in TERRORISM and/or
ACTIVITIES.
V. EXCEPTIONS TO SUPPORT IMMIGRATION AND VISA SCREENING
ACTIVITIES BY DHS AND DOS
3.14 TSDB Minimum Substantive Derogatory Exceptions to Support Immigration and Visa
Screening Activities by the DHS and DOS. The Watchlisting Guidance contains certain
exceptions to the minimum substantive derogatory criteria for watchlisting that
support immigration and visa screening activities by the DHS and DOS to determine whether
grounds exist to deny admission of aliens to the United States (including denials of visas) or to
deny other immigration bene?ts pursuant to the INA.55 DEROGATORY
INFORMATION is not required for nominations made pursuant to the following sections.
Because the INA de?nes ?aliens? as ?any person not a citizen or national of the United
States?56, the admissibility provisions also apply to LPRs, in certain circumstances
including those described in INA section U.S.C. lOl(a)(l who are
considered as U.S. PERSONS under Executive Order 12333. Consequently, NCTC developed a
mechanism in TIDE to identify and distinguish U.S. citizens from non?U.S. citizens in order
to further distinguish between ?aliens? under the INA and U.S. PERSONS under Executive
Order 12333. The following subsections are exceptions to the REASONABLE
standard and will only be transmitted to CLASS (via the DOS CCD) and WLS
to support immigration and visa screening processes.
5? Such documents/media, however, still need to be reviewed to ensure that innocent individuals are not erroneously
watchlisted.
5? INA section SC. I sets forth several grounds for inadmissibility based on terrorist
activities, which is de?ned in INA section U.S.C. 1 For example, INA section
212(a)(3)(B)(i)(Vll) states that any alien who ?endorses or espouses terrorist activity or persuades others to endorse or
espouse terrorist activity or support a terrorist organization? is inadmissible to the United States. 8 U.S.C.
All other uses of the term ?terrorist activities? within this Watchlisting Guidance that do not
speci?cally reference the INA follow the de?nition outlined in Chapter 1 and Appendix 1.
5 See INA U.S.C.
OFFICIAL USE ON SECURITY INFORMATION
Page 42

OR OFFICIAL USE SECURITY INFORMATION
3.14.1 Spouses and Children. Spouses and children57 of a KNOWN or SUSPECTED alien
TERRORIST cannot be considered TERRORISTS without a REASONABLE SUSPICION that they
are engaging or have engaged in conduct constitutin in preparation For, in aid of, or
related to TERRORISM and/or TERRORIST ACTIVITIES. The INA provides that the alien
spouse or alien child of an alien who is inadmissible for certain speci?ed reasons
relating to terrorist activities, ifthe activity causing the alien to be found inadmissible
occurred within the last ?ve (5) years, is inadmissible.59 An alien spouse or child of an
alien who is believed to be inadmissible under the INA for terrorist activities should be
nominated. No additional DEROGATORY INFORMATION (in addition to familial relation)
is required for nomination under this section, if the individual meets the below
quali?cations.
3.14.1.1 To qualify for watchlisting, alien spouses and children ofa KNOWN or
TERRORIST must:
3.14.111 Be an alien (not a US. citizen or national), which includes and,
3.14.1 .l .2 Be an unmarried child under the age of2l or a spouse of an alien.
3.14.1.2 Ex-spouses, widows, or widowers should not be nominated unless there is a
REASONABLE SUSPICION to believe that they themselves are engaging or have
engaged in conduct constituting, in preparation for, in aid of, or related to
TERRORISM and/or TERRORIST ACTIVITIES. Deceased spouses should not be
nominated unless they are specifically covered in Paragraph 3.17.
3.14.1.3 Once a spouse or child no longer meets the de?nitional requirements under
this section, such an individual should no longer be watchlisted unless there is a
REASONABLE SUSPICION to believe that the individual is engaging in TERRORISM
and/or TERRORIST ACTIVITIES. For example, if a child reaches the age of 21 and
there is REASONABLE SUSPICION to believe he or she was knowingly involved in
ACTIVITY by providing material support to a FTO, he or she can remain
watchlisted based upon this DEROGATORY INFORMATION. On the other hand, once
a child of a KNOWN or SUSPECTED TERRORIST turns 2l years of age, the individual
should no longer be watchlisted under this exception because he or she is not
considered a child of the KNOWN or SUSPECTED and additional
DEROGATORY INFORMATION would be needed to meet the REASONABLE SUSPICION
standard.
57 The INA de?nes ?child? as ?an unmarried person under 21 years ofage. . . INA U.S.C. lOl(b)(l
58 The discussion in Paragraph 3.14.1 is limited exclusively to spouses and children; all other family members
(including mothers, fathers, sisters and brothers) should be nominated for inclusion in the TSDB only if there is
DEROGATORY INFORMATION that the individual has a close connection to a KNOWN or TERRORIST and that
connection meets the REASONABLE SUSPICION standard. Absent independent DEROOATORY INFORMATION, records for
these individuals may be retained in TIDE for analytic purposes. See Paragraph 1.53.2.2 for treatment of these other
family members as records that may reside in TIDE for analytic purposes but are not exported to the
TSDB (known as TIDE Category Code 160).
59 See INA U.S.C. While this provision does not apply when the activity
causing the alien to be found inadmissible occurred more than 5 years before the spouse or child?s admissibility is being
considered, the analysis of the time limit's application will be determined by SCREENERS upon ENCOUNTER.
UNCLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
Page 43
OR OFFICIAL USE SECURITY INFORMATION
3.14.1 Spouses and Children. Spouses and children57 of a KNOWN or SUSPECTED alien
TERRORIST cannot be considered TERRORISTS without a REASONABLE SUSPICION that they
are engaging or have engaged in conduct constitutin in preparation For, in aid of, or
related to TERRORISM and/or TERRORIST ACTIVITIES. The INA provides that the alien
spouse or alien child of an alien who is inadmissible for certain speci?ed reasons
relating to terrorist activities, ifthe activity causing the alien to be found inadmissible
occurred within the last ?ve (5) years, is inadmissible.59 An alien spouse or child of an
alien who is believed to be inadmissible under the INA for terrorist activities should be
nominated. No additional DEROGATORY INFORMATION (in addition to familial relation)
is required for nomination under this section, if the individual meets the below
quali?cations.
3.14.1.1 To qualify for watchlisting, alien spouses and children ofa KNOWN or
TERRORIST must:
3.14.111 Be an alien (not a US. citizen or national), which includes and,
3.14.1 .l .2 Be an unmarried child under the age of2l or a spouse of an alien.
3.14.1.2 Ex-spouses, widows, or widowers should not be nominated unless there is a
REASONABLE SUSPICION to believe that they themselves are engaging or have
engaged in conduct constituting, in preparation for, in aid of, or related to
TERRORISM and/or TERRORIST ACTIVITIES. Deceased spouses should not be
nominated unless they are specifically covered in Paragraph 3.17.
3.14.1.3 Once a spouse or child no longer meets the de?nitional requirements under
this section, such an individual should no longer be watchlisted unless there is a
REASONABLE SUSPICION to believe that the individual is engaging in TERRORISM
and/or TERRORIST ACTIVITIES. For example, if a child reaches the age of 21 and
there is REASONABLE SUSPICION to believe he or she was knowingly involved in
ACTIVITY by providing material support to a FTO, he or she can remain
watchlisted based upon this DEROGATORY INFORMATION. On the other hand, once
a child of a KNOWN or SUSPECTED TERRORIST turns 2l years of age, the individual
should no longer be watchlisted under this exception because he or she is not
considered a child of the KNOWN or SUSPECTED and additional
DEROGATORY INFORMATION would be needed to meet the REASONABLE SUSPICION
standard.
57 The INA de?nes ?child? as ?an unmarried person under 21 years ofage. . . INA U.S.C. lOl(b)(l
58 The discussion in Paragraph 3.14.1 is limited exclusively to spouses and children; all other family members
(including mothers, fathers, sisters and brothers) should be nominated for inclusion in the TSDB only if there is
DEROGATORY INFORMATION that the individual has a close connection to a KNOWN or TERRORIST and that
connection meets the REASONABLE SUSPICION standard. Absent independent DEROOATORY INFORMATION, records for
these individuals may be retained in TIDE for analytic purposes. See Paragraph 1.53.2.2 for treatment of these other
family members as records that may reside in TIDE for analytic purposes but are not exported to the
TSDB (known as TIDE Category Code 160).
59 See INA U.S.C. While this provision does not apply when the activity
causing the alien to be found inadmissible occurred more than 5 years before the spouse or child?s admissibility is being
considered, the analysis of the time limit's application will be determined by SCREENERS upon ENCOUNTER.
UNCLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
Page 43

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.14.2 Endorsers and Espousers. An alien who endorses or espouses TERRORIST ACTIVITY
or persuades others to endorse or espouse TERRORIST ACTIVITY or support a terrorist
organization may be inadmissible under the INA and should be nominated.
3.14.3 Incitement. Inciting an individual to commit an act of TERRORISM and/or TERRORIST
ACTIVITY under circumstances that indicate an intention to cause death or serious bodily
harm is considered engaging in TERRORISTACTIVITY. The individual may be
inadmissible under the INA and should be nominated.
3.14.4 Supporters of a Designated Terrorist Organization. Supporters of a DTO may be
inadmissible under the INA and should be nominated if the support is operational in
nature. If support is merely ideological, the individual should not be nominated.
3.14.5 Representatives. Representatives of terrorist organizations and representatives
of any political, social or other group that endorses or espouses TERRORIST ACTIVITY
may be inadmissible under the INA and should be nominated. Representatives include
an of?cer, of?cial, or Spokesman of an organization, and any person who directs,
counsels, commands, or induces an organization to engage in TERRORIST ACTIVITY.
Neither membership in, nor association with, the organization or group is required.
3.14.6 TERRORISTS, Extremists, Jihadists, Militants, Mujahideen or Insurgents.60
Nominations of individuals described by sources as ?extremists?,
?jihadists?, ?militants?, ?mujahideen? or ?insurgents?6 (an exclusive list) will be
accepted into the TSDB as exceptions for export to WLS and
VISA and CLASS-PASSPORT for immigration and border processing when the
following four conditions apply:
3.14.6.1 The individual is a not a US. Citizen or National g, the individual is a
foreign national or a
3.14.6.2 The context suggests a nexus to
3.14.6.3 Adequate identi?ers are available to permit identi?cation?; and,
3.14.6.4 The information has been evaluated as being credible.
3.14.6.5 It is important to recognize that some activities associated with extreme
political or religious views expressed by aliens in the United States may constitute
the exercise of rights guaranteed by the First Amendment the rights to free
speech, assembly and religious exercise)? Therefore, someone so labeled based
60 This exception is commonly referred to as ?label plus? nomination.
6' Insurgency is de?ned as an ?organized movement" aimed at the overthrow of a constituted government through the
use of subversion and armed con?ict.
62 An adequate identi?er is a biometric, or a last name, ?rst name and any one of the additional identifiers listed in
Chapter 2, Section 11.
63 See Chapter 1, Section 111 concerning constitutionally protected activities.
OFFICIAL USE SECURITY INFORMATION
Page 44
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.14.2 Endorsers and Espousers. An alien who endorses or espouses TERRORIST ACTIVITY
or persuades others to endorse or espouse TERRORIST ACTIVITY or support a terrorist
organization may be inadmissible under the INA and should be nominated.
3.14.3 Incitement. Inciting an individual to commit an act of TERRORISM and/or TERRORIST
ACTIVITY under circumstances that indicate an intention to cause death or serious bodily
harm is considered engaging in TERRORISTACTIVITY. The individual may be
inadmissible under the INA and should be nominated.
3.14.4 Supporters of a Designated Terrorist Organization. Supporters of a DTO may be
inadmissible under the INA and should be nominated if the support is operational in
nature. If support is merely ideological, the individual should not be nominated.
3.14.5 Representatives. Representatives of terrorist organizations and representatives
of any political, social or other group that endorses or espouses TERRORIST ACTIVITY
may be inadmissible under the INA and should be nominated. Representatives include
an of?cer, of?cial, or Spokesman of an organization, and any person who directs,
counsels, commands, or induces an organization to engage in TERRORIST ACTIVITY.
Neither membership in, nor association with, the organization or group is required.
3.14.6 TERRORISTS, Extremists, Jihadists, Militants, Mujahideen or Insurgents.60
Nominations of individuals described by sources as ?extremists?,
?jihadists?, ?militants?, ?mujahideen? or ?insurgents?6 (an exclusive list) will be
accepted into the TSDB as exceptions for export to WLS and
VISA and CLASS-PASSPORT for immigration and border processing when the
following four conditions apply:
3.14.6.1 The individual is a not a US. Citizen or National g, the individual is a
foreign national or a
3.14.6.2 The context suggests a nexus to
3.14.6.3 Adequate identi?ers are available to permit identi?cation?; and,
3.14.6.4 The information has been evaluated as being credible.
3.14.6.5 It is important to recognize that some activities associated with extreme
political or religious views expressed by aliens in the United States may constitute
the exercise of rights guaranteed by the First Amendment the rights to free
speech, assembly and religious exercise)? Therefore, someone so labeled based
60 This exception is commonly referred to as ?label plus? nomination.
6' Insurgency is de?ned as an ?organized movement" aimed at the overthrow of a constituted government through the
use of subversion and armed con?ict.
62 An adequate identi?er is a biometric, or a last name, ?rst name and any one of the additional identifiers listed in
Chapter 2, Section 11.
63 See Chapter 1, Section 111 concerning constitutionally protected activities.
OFFICIAL USE SECURITY INFORMATION
Page 44

OR OFFICIAL USE SECURITY INFORMATION
in part on this type of constitutionally protected activity, must have other
substantive DEROGATORY INFORMATION indicative of TERRORIST intent. As
previously noted, nominations may not be made based solely on protected activity.
3.14.7 Additional Derogatory Information Required (TIDE Category Code 99s and
50s). NCTC will retain a record in TIDE if it is determined that the information pertains
to, or is related to, TERRORISM.64 However, if a record involving an alien, which
includes LPRS, does not contain sufficient DEROGATORY INFORMATION to meet any of
the aforementioned exceptions to the REASONABLE SUSPICION standard for
inclusion, NCTC will generally designate the record as a Category Code 99 (the TIDE
category code ?applied when DEROGATORY INFORMATION does not meet the
REASONABLE SUSPICION standard for watchlisting because it is very limited or of
suspected reliability but there is a possible nexus to or a Category Code 50
(the TIDE category code applied when an individual has a de?ned relationship with the
KNOWN or SUSPECTED TERRORIST, but whose involvement with the KNOWN or SUSPECTEO
activities is unknown)?, making it available for export to TSDB for use by
DOS and DHS for visa adjudication and immigration processing.
VI. SPECIAL CONSIDERATIONS
3.15 Nominations of us. PERSONS. Nominations of U.S. PERSONS, in accordance with the Attorney
General approved procedures applicable to each element of the 1C66, will be made pursuant to
the procedures set forth below to ensure compliance with this REASONABLE SUSPICION
standard. Nominations of U.S. PERSONS shall be made based on information from sources of
known reliability or where there exists additional corroboration or context supporting
REASONABLE SUSPICION. NOMINATING AGENCIES will review information on us. PERSONS
pursuant to procedures set forth below consistent with the nature of the reporting supporting
the nomination and the protection of sources and methods.
3. I 5.1 Special handling is warranted for US. PERSONS nominated for watchlisting, especially
by an Agency other than the FBI. To ensure compliance with the Watchlisting Guidance
that the REASONABLE SUSPICION standard exists for us. PERSONS in the TSDB, as well as
to ensure proper interagency coordination, a formal process has been implemented that:
3.15.1.1 Ensures the FBI is aware of us. PERSONS nominated by any other Department
or Agency;
6? See Paragraph 1.26.
65 See 28, supra.
66 The referenced procedures are those approved for each element of the 1C pursuant to Executive Order 12333, as
amended, which states in relevant part, ?Elements of the Intelligence Community are authorized to collect, retain, or
disseminate information concerning United States persons only in accordance with procedures established by the head
of the Intelligence Community element concerned or by the head of a Department c0ntaining such element and
approved by the Attorney General, consistent with the authorities provided by part 1 of this Order alter consultation
with the Director.? See Executive Order 12333, Paragraph 2.3, as amended by Executive Order 13618 (July 6, 2012).
OR OFFICIAL USE ON SECURITY INFORMATION
Page 45
OR OFFICIAL USE SECURITY INFORMATION
in part on this type of constitutionally protected activity, must have other
substantive DEROGATORY INFORMATION indicative of TERRORIST intent. As
previously noted, nominations may not be made based solely on protected activity.
3.14.7 Additional Derogatory Information Required (TIDE Category Code 99s and
50s). NCTC will retain a record in TIDE if it is determined that the information pertains
to, or is related to, TERRORISM.64 However, if a record involving an alien, which
includes LPRS, does not contain sufficient DEROGATORY INFORMATION to meet any of
the aforementioned exceptions to the REASONABLE SUSPICION standard for
inclusion, NCTC will generally designate the record as a Category Code 99 (the TIDE
category code ?applied when DEROGATORY INFORMATION does not meet the
REASONABLE SUSPICION standard for watchlisting because it is very limited or of
suspected reliability but there is a possible nexus to or a Category Code 50
(the TIDE category code applied when an individual has a de?ned relationship with the
KNOWN or SUSPECTED TERRORIST, but whose involvement with the KNOWN or SUSPECTEO
activities is unknown)?, making it available for export to TSDB for use by
DOS and DHS for visa adjudication and immigration processing.
VI. SPECIAL CONSIDERATIONS
3.15 Nominations of us. PERSONS. Nominations of U.S. PERSONS, in accordance with the Attorney
General approved procedures applicable to each element of the 1C66, will be made pursuant to
the procedures set forth below to ensure compliance with this REASONABLE SUSPICION
standard. Nominations of U.S. PERSONS shall be made based on information from sources of
known reliability or where there exists additional corroboration or context supporting
REASONABLE SUSPICION. NOMINATING AGENCIES will review information on us. PERSONS
pursuant to procedures set forth below consistent with the nature of the reporting supporting
the nomination and the protection of sources and methods.
3. I 5.1 Special handling is warranted for US. PERSONS nominated for watchlisting, especially
by an Agency other than the FBI. To ensure compliance with the Watchlisting Guidance
that the REASONABLE SUSPICION standard exists for us. PERSONS in the TSDB, as well as
to ensure proper interagency coordination, a formal process has been implemented that:
3.15.1.1 Ensures the FBI is aware of us. PERSONS nominated by any other Department
or Agency;
6? See Paragraph 1.26.
65 See 28, supra.
66 The referenced procedures are those approved for each element of the 1C pursuant to Executive Order 12333, as
amended, which states in relevant part, ?Elements of the Intelligence Community are authorized to collect, retain, or
disseminate information concerning United States persons only in accordance with procedures established by the head
of the Intelligence Community element concerned or by the head of a Department c0ntaining such element and
approved by the Attorney General, consistent with the authorities provided by part 1 of this Order alter consultation
with the Director.? See Executive Order 12333, Paragraph 2.3, as amended by Executive Order 13618 (July 6, 2012).
OR OFFICIAL USE ON SECURITY INFORMATION
Page 45

OFFICIAL USE SECURITY INFORMATION
3.16
3.l7
3. 5.1 .2 Requires review of the watchlist nomination decision and concurrence by the
TSC that REASONABLE SUSPICION exists for watchlisting;
3.15.1.3 Ensures there is interagency awareness of all U.S. PERSON nominations (FBI
or otherwise); and,
3.15.1.4 Ensures there is U.S. Government coordination in the investigation and/or
intelligence gathering on these individuals, including strategies for engagement
with foreign partners if required.
3. I 5.2 NCTC should include in U.S. PERSONS who are under lntemational TERRORISM
Preliminary Investigation by the but who have not been deemed to meet the
REASONABLE SUSPICION standard and U.S. PERSONS with a nexus to TERRORISM, but for
whom there is insuf?cient DEROGATORY INFORMATION to support entry in TSDB. These
TIDE records on U.S. PERSONS will not be provided to TSC for export via the TSDB
unless approved of as an exception to the REASONABLE SUSPICION standard pursuant to
Section in this Chapter of the Watehlisting Guidance, infra, or as part of a
pursuant to Paragraph 1.59 of the Watehlisting Guidance.
3. 5.3 For U.S. PERSONS nominated by other Government Agencies who are not under Bl
investigation, NCTC receive, process, and export these subjects for inclusion in
the TSDB, as appropriate under current procedures. As part of the processing, NCT
identify and share these U.S. PERSON identi?ers with the Bl?s Foreign Terrorist
Tracking Task Force for assessment, and notifying the Bl case agent of the
inclusion.
Political Figures or Purposes. Heads of State or other Government Officials should be
nominated when there is PARTICULARIZED DEROGATORY INFORMATION to support a
REASONABLE SUSPICION to believe the individual is engaging or has engaged in conduct
constituting, in preparation for, in aid of, or related to TERRORISM and/or TERRORIST
ACTIVITIES. Waivers or other appropriate action can be requested from U.S. Customs and
Border Protection (CBP) in coordination with DOS to facilitate the travel of a properly
watchlisted Head of State or other government officials to the extent necessary.
3.16.] Watehlisting an individual is prohibited based on political purposes, retaliation, or
any other reason unconnected to the REASONABLE SUSPICION standard.
Identities of Deceased Individuals.
3.17.] The TSDB will not include identity information of KNOWN or SUSPECTED
that are con?rmed dead?57 unless:
67 Subjects are considered ?con?rmed dead? under the following circumstances:
a.
The subject?s death became a high pro?le case in the public sphere media footage con?rming suicide
bombers? deaths, 9/ hijackers, death of Abu Musaq al Zarqawi); or,
b. Reporting on the subject?s death has been comborated by at least two credible sources United States or
?friendly? foreign government, fully-vetted asset).
OFFICIAL USE SECURITY INFORMATION
Page 46
OFFICIAL USE SECURITY INFORMATION
3.16
3.l7
3. 5.1 .2 Requires review of the watchlist nomination decision and concurrence by the
TSC that REASONABLE SUSPICION exists for watchlisting;
3.15.1.3 Ensures there is interagency awareness of all U.S. PERSON nominations (FBI
or otherwise); and,
3.15.1.4 Ensures there is U.S. Government coordination in the investigation and/or
intelligence gathering on these individuals, including strategies for engagement
with foreign partners if required.
3. I 5.2 NCTC should include in U.S. PERSONS who are under lntemational TERRORISM
Preliminary Investigation by the but who have not been deemed to meet the
REASONABLE SUSPICION standard and U.S. PERSONS with a nexus to TERRORISM, but for
whom there is insuf?cient DEROGATORY INFORMATION to support entry in TSDB. These
TIDE records on U.S. PERSONS will not be provided to TSC for export via the TSDB
unless approved of as an exception to the REASONABLE SUSPICION standard pursuant to
Section in this Chapter of the Watehlisting Guidance, infra, or as part of a
pursuant to Paragraph 1.59 of the Watehlisting Guidance.
3. 5.3 For U.S. PERSONS nominated by other Government Agencies who are not under Bl
investigation, NCTC receive, process, and export these subjects for inclusion in
the TSDB, as appropriate under current procedures. As part of the processing, NCT
identify and share these U.S. PERSON identi?ers with the Bl?s Foreign Terrorist
Tracking Task Force for assessment, and notifying the Bl case agent of the
inclusion.
Political Figures or Purposes. Heads of State or other Government Officials should be
nominated when there is PARTICULARIZED DEROGATORY INFORMATION to support a
REASONABLE SUSPICION to believe the individual is engaging or has engaged in conduct
constituting, in preparation for, in aid of, or related to TERRORISM and/or TERRORIST
ACTIVITIES. Waivers or other appropriate action can be requested from U.S. Customs and
Border Protection (CBP) in coordination with DOS to facilitate the travel of a properly
watchlisted Head of State or other government officials to the extent necessary.
3.16.] Watehlisting an individual is prohibited based on political purposes, retaliation, or
any other reason unconnected to the REASONABLE SUSPICION standard.
Identities of Deceased Individuals.
3.17.] The TSDB will not include identity information of KNOWN or SUSPECTED
that are con?rmed dead?57 unless:
67 Subjects are considered ?con?rmed dead? under the following circumstances:
a.
The subject?s death became a high pro?le case in the public sphere media footage con?rming suicide
bombers? deaths, 9/ hijackers, death of Abu Musaq al Zarqawi); or,
b. Reporting on the subject?s death has been comborated by at least two credible sources United States or
?friendly? foreign government, fully-vetted asset).
OFFICIAL USE SECURITY INFORMATION
Page 46

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.17.1.l PARTICULARJZED DEROGATORY INFORMATION supports a REASONABLE
SUSPICION that an existing KNOWN or SUSPECTED TERRORIST is using that identity
information; or,
3.17.1.2 A recognized terrorist organization"8 collects KNOWN or SUSPECTED TERRORIST
identity information for use by its members in preparing for or committing
TERRORIST acts and identity or travel documents related to a deceased KNOWN
or SUSPECTED TERRORIST of that organization) have not been recovered. ?Trusted
travel documents? include all documents used for border crossings.
3.17.2 NOMINATING AGENCIES will share information regarding a watchlisted or nominated
individual?s deceased status under Addendum of the TSC MOU, section (?Any
other TERRORISM INFORMATION that ORIGINATORS speci?cally provide for passage to the
NCTC will export deceased status to the TSC, and the TSC will export deceased
status to end user screening systems. NOMINATING AGENCIES will mark deceased status
information Restricted? in cases where the status, because of sensitive sourcing,
should not be forwarded to the TSC. TIDE restricted information will not be exported to
the TSC. When a nomination is made on a deceased person in accordance with this
paragraph, the status indicator within TIDE that is exported to the TSC will be marked
to re?ect that the person is deceased.
VII. EXAMPLES OF TERRORISM TERRORIST ACTIVITIES
3.18 Examples of TERRORISM and/or TERRORIST ACTIVITIES may generally include conduct
intended to intimidate, coerce, in?uence, or affect civilian populations or government policy
consisting of:
3.18.1 destruction of aircraft or aircra? facilities (I 8 U.S.C. 32);
3.18.2 violence at international airports (18 U.S.C. 37);
3.18.3 biological weapons (I 8 U.S.C. 175 or l75b);
3.18.4 variola virus (18 U.S.C. l75c);
3.18.5 chemical weapons (I 8 U.S.C. 229);
3.18.6 assassination and kidnapping of Congressional Members, Cabinet Of?cials, and
Supreme Court Justices(18 U.S.C. 351 or
3.18.7 nuclear materials (18 U.S.C. 831);
3.18.8 participation in nuclear and weapons of mass destruction threats to the United States
(18 U.S.C. 832);
3.18.9 plastic explosives (l8 U.S.C. 842(m) or footnote
3.18.10 arson and bombing of Government property risking or causing death (18 U.S.C.
344(0(2) or
3.18.1 I arson and bombing of property used in interstate commerce (18 U.S.C. 844(i));
?58 A classi?ed list of recognized terrorist organizations that are known to reuse TERRORIST identity information is
available on the Watchlisting Community of Interest portal on NCTC Current.
OR OFFICIAL USE SIT IVE SECURITY INFORMATION
Page 47
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.17.1.l PARTICULARJZED DEROGATORY INFORMATION supports a REASONABLE
SUSPICION that an existing KNOWN or SUSPECTED TERRORIST is using that identity
information; or,
3.17.1.2 A recognized terrorist organization"8 collects KNOWN or SUSPECTED TERRORIST
identity information for use by its members in preparing for or committing
TERRORIST acts and identity or travel documents related to a deceased KNOWN
or SUSPECTED TERRORIST of that organization) have not been recovered. ?Trusted
travel documents? include all documents used for border crossings.
3.17.2 NOMINATING AGENCIES will share information regarding a watchlisted or nominated
individual?s deceased status under Addendum of the TSC MOU, section (?Any
other TERRORISM INFORMATION that ORIGINATORS speci?cally provide for passage to the
NCTC will export deceased status to the TSC, and the TSC will export deceased
status to end user screening systems. NOMINATING AGENCIES will mark deceased status
information Restricted? in cases where the status, because of sensitive sourcing,
should not be forwarded to the TSC. TIDE restricted information will not be exported to
the TSC. When a nomination is made on a deceased person in accordance with this
paragraph, the status indicator within TIDE that is exported to the TSC will be marked
to re?ect that the person is deceased.
VII. EXAMPLES OF TERRORISM TERRORIST ACTIVITIES
3.18 Examples of TERRORISM and/or TERRORIST ACTIVITIES may generally include conduct
intended to intimidate, coerce, in?uence, or affect civilian populations or government policy
consisting of:
3.18.1 destruction of aircraft or aircra? facilities (I 8 U.S.C. 32);
3.18.2 violence at international airports (18 U.S.C. 37);
3.18.3 biological weapons (I 8 U.S.C. 175 or l75b);
3.18.4 variola virus (18 U.S.C. l75c);
3.18.5 chemical weapons (I 8 U.S.C. 229);
3.18.6 assassination and kidnapping of Congressional Members, Cabinet Of?cials, and
Supreme Court Justices(18 U.S.C. 351 or
3.18.7 nuclear materials (18 U.S.C. 831);
3.18.8 participation in nuclear and weapons of mass destruction threats to the United States
(18 U.S.C. 832);
3.18.9 plastic explosives (l8 U.S.C. 842(m) or footnote
3.18.10 arson and bombing of Government property risking or causing death (18 U.S.C.
344(0(2) or
3.18.1 I arson and bombing of property used in interstate commerce (18 U.S.C. 844(i));
?58 A classi?ed list of recognized terrorist organizations that are known to reuse TERRORIST identity information is
available on the Watchlisting Community of Interest portal on NCTC Current.
OR OFFICIAL USE SIT IVE SECURITY INFORMATION
Page 47

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.18.12 killing or attempted killing during an attack on a Federal facility with a dangerous
weapon (18 U.S.C. 930(0));
3.18.13 conspiracy to murder, kidnap, or maim persons abroad (18 U.S.C.
3.18.14 damaging a protected computer used in interstate or foreign commerce or that is used
exclusively by a ?nancial institution or the United States Government (18 U.S.C.
lO30(a)(1); 18 U.S.C. 1030(a)(5)(A)(i) resulting in damage as de?ned in
lO30(a)(5)(B)(ii) through
3.18.15 killing or attempted killing of of?cers and employees ofthe United States (18 U.S.C.
1 1 14);
3.18.16 murder or manslaughter of foreign of?cials, of?cial guests, or internationally
protected persons (18 U.S.C. 1 I 16);
3.18.17 hostage taking (18 U.S.C. 1203);
3.18.18 damage to Government property (18 U.S.C. 1361);
3.18.19 destruction of communication lines, stations, or systems (18 U.S.C. 1362);
3.18.20 injury to U.S. aircraft or vessels (18 U.S.C. 1363);
3.18.21 injury to U.S. diplomatic, consular, military, or other property (18 U.S.C. 1363);
3.18.22 destruction of an energy facility (18 U.S.C. 1366(a));
3.18.23 Presidential and Presidential Staff assassination and kidnapping (18 U.S.C. 1751(a),
(0), 0r
3.18.24 acts of violence against railroad carriers and against mass transportation systems on
land, on water, or through the air (18 U.S.C. 1992);
3.18.25 destruction of national defense materials, premises, or utilities (18 U.S.C. 2115; 18
U.S.C. 2156);
3.18.26 violence against maritime navigation (seizing a ship by force, destroying a ship or
damaging its navigation systems) (18 U.S.C. 2280);
3.18.27 violence against maritime ?xed platforms (an arti?cial island, installation or
structure permanently attached to the sea-bed for the purpose of exploration or
exploitation of resources or for other economic purposes (18 U.S.C. 2281);
3.18.28 homicides and other violence against U.S. nationals occurring outside of the United
States (18 U.S.C. 2332);
3.18.29 the use of weapons of mass destruction (18 .S.C. 2332a);
3.18.30 acts of TERRORISM transcending national boundaries (18 U.S.C. 2332b);
3.18.31 bombing of public places and facilities (18 U.S.C. 2332f);
3.18.32 producing, transferring, or threatening to use missile systems designed to destroy
aircraft (18 U.S.C. 2332g);
3.18.33 producing, transferring, or threatening to use radiological dispersal devices (18
U.S.C. 2332h);
3.18.34 harboring TERRORISTS (18 U.S.C. 2339);
3.18.35 providing material support to TERRORISTS (18 U.S.C.
3.18.36 providing material support to terrorist organizations (18 U.S.C.
3.18.37 ?nancing TERRORISM (18 U.S.C.
3.18.38 receiving military-type training from a PTO (18 U.S.C.
3.18.39 torture (18 U.S.C.
3.18.40 developing, transferring, possessing, or threatening to use atomic weapons (42
U.S.C. 2122);
OR OFFICIAL USE SECURITY INFORMATION
Page 48
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
3.18.12 killing or attempted killing during an attack on a Federal facility with a dangerous
weapon (18 U.S.C. 930(0));
3.18.13 conspiracy to murder, kidnap, or maim persons abroad (18 U.S.C.
3.18.14 damaging a protected computer used in interstate or foreign commerce or that is used
exclusively by a ?nancial institution or the United States Government (18 U.S.C.
lO30(a)(1); 18 U.S.C. 1030(a)(5)(A)(i) resulting in damage as de?ned in
lO30(a)(5)(B)(ii) through
3.18.15 killing or attempted killing of of?cers and employees ofthe United States (18 U.S.C.
1 1 14);
3.18.16 murder or manslaughter of foreign of?cials, of?cial guests, or internationally
protected persons (18 U.S.C. 1 I 16);
3.18.17 hostage taking (18 U.S.C. 1203);
3.18.18 damage to Government property (18 U.S.C. 1361);
3.18.19 destruction of communication lines, stations, or systems (18 U.S.C. 1362);
3.18.20 injury to U.S. aircraft or vessels (18 U.S.C. 1363);
3.18.21 injury to U.S. diplomatic, consular, military, or other property (18 U.S.C. 1363);
3.18.22 destruction of an energy facility (18 U.S.C. 1366(a));
3.18.23 Presidential and Presidential Staff assassination and kidnapping (18 U.S.C. 1751(a),
(0), 0r
3.18.24 acts of violence against railroad carriers and against mass transportation systems on
land, on water, or through the air (18 U.S.C. 1992);
3.18.25 destruction of national defense materials, premises, or utilities (18 U.S.C. 2115; 18
U.S.C. 2156);
3.18.26 violence against maritime navigation (seizing a ship by force, destroying a ship or
damaging its navigation systems) (18 U.S.C. 2280);
3.18.27 violence against maritime ?xed platforms (an arti?cial island, installation or
structure permanently attached to the sea-bed for the purpose of exploration or
exploitation of resources or for other economic purposes (18 U.S.C. 2281);
3.18.28 homicides and other violence against U.S. nationals occurring outside of the United
States (18 U.S.C. 2332);
3.18.29 the use of weapons of mass destruction (18 .S.C. 2332a);
3.18.30 acts of TERRORISM transcending national boundaries (18 U.S.C. 2332b);
3.18.31 bombing of public places and facilities (18 U.S.C. 2332f);
3.18.32 producing, transferring, or threatening to use missile systems designed to destroy
aircraft (18 U.S.C. 2332g);
3.18.33 producing, transferring, or threatening to use radiological dispersal devices (18
U.S.C. 2332h);
3.18.34 harboring TERRORISTS (18 U.S.C. 2339);
3.18.35 providing material support to TERRORISTS (18 U.S.C.
3.18.36 providing material support to terrorist organizations (18 U.S.C.
3.18.37 ?nancing TERRORISM (18 U.S.C.
3.18.38 receiving military-type training from a PTO (18 U.S.C.
3.18.39 torture (18 U.S.C.
3.18.40 developing, transferring, possessing, or threatening to use atomic weapons (42
U.S.C. 2122);
OR OFFICIAL USE SECURITY INFORMATION
Page 48

OFFICIAL USE SECURITY INFORMATION
3.18.41 sabotage of nuclear facilities or fuel (42 U.S.C. 2284);
3.18.42 aircraft piracy (49 U.S.C. 46502);
3.18.43 assault on a ?ight crew with a dangerous weapon (49 U.S.C. 46504);
3.18.44 carrying a weapon or explosive aboard an aircraft (49 U.S.C. 46505(b) or 49
U.S.C. 46506 if homicide or attempted homicide is involved);
3.18.45 damaging or destroying an interstate gas pipeline facility, an interstate hazardous
liquid pipeline facility, or either an intrastate gas pipeline facility or intrastate hazardous
liquid pipeline facility (49 U.S.C. 60123(b)); or
3.18.46 manufacturing, distributing, or possessing controlled substances intending to provide
anything of pecuniary value to a PTO, member, or group (Section 1010A (iv) of the
Controlled Substances Import and Export Act).
UN OFFICIAL USE SECURITY INFORMATION
Page I 49
OFFICIAL USE SECURITY INFORMATION
3.18.41 sabotage of nuclear facilities or fuel (42 U.S.C. 2284);
3.18.42 aircraft piracy (49 U.S.C. 46502);
3.18.43 assault on a ?ight crew with a dangerous weapon (49 U.S.C. 46504);
3.18.44 carrying a weapon or explosive aboard an aircraft (49 U.S.C. 46505(b) or 49
U.S.C. 46506 if homicide or attempted homicide is involved);
3.18.45 damaging or destroying an interstate gas pipeline facility, an interstate hazardous
liquid pipeline facility, or either an intrastate gas pipeline facility or intrastate hazardous
liquid pipeline facility (49 U.S.C. 60123(b)); or
3.18.46 manufacturing, distributing, or possessing controlled substances intending to provide
anything of pecuniary value to a PTO, member, or group (Section 1010A (iv) of the
Controlled Substances Import and Export Act).
UN OFFICIAL USE SECURITY INFORMATION
Page I 49

OR OFFICIAL USE SECURITY INFORMATION
CHAPTER 4: NO FLY, SELECTEE AND EXPANDED SELECTEE LISTS
IMPLEMENTATION GUIDANCE
I. BACKGROUND
4.1 On October 2 2004, the Deputies Committee established the criteria for the No Fly and
Selectee Lists. On January 10, 2005, the DHS released the No Fly and Selectee Lists
Implementation Guidance (Implementation Guidance) to provide direction on how to
implement the No Fly and Selectee List criteria. The Implementation Guidance was updated
and supplemented on July 25, 2006.
4.2 On February 8, 2008, the Deputies Committee approved the addition of a third and fourth
criterion to the No Fly List. The Terrorist Screening Center Policy Board Working Group69
revised the Implementation Guidance on March 5, 2008, to provide direction on how to
implement these new criteria.
4.3 Following the attempted TERRORIST attack on December 25, 2009, the President directed that
a review of the current No Fly and Selectee List criteria be conducted and recommendations
be made regarding whether any adjustments were needed. The Terrorist Screening Center
Policy Board Working Group, in conjunction with the Information Sharing Access
recommended certain changes in the lists? criteria and implementation guidance. Those
recommendations were approved by the Deputies Committee on July 16, 2010.
Il. PRE-CONDITIONS FOR PLACEMENT ON THE FLY OR SELECTEE
LIST
4.4 Generally, in order to be included on either the No Fly or Selectee List, two pre-conditions
must both be met:
44.] Minimum Identifying Criteria. Absent a Special Situation as described below?,
minimum identifying biographic criteria consisting of First Name, Last Name, Full Date
of Birth are required; and,
4.4.2 Minimum Substantive Derogatory Criteria. The minimum substantive derogatory
criteria for inclusion must be met.?
This Working Group included representatives from Department of State, Department of Justice, Department of
Homeland Security, Federal Bureau of Investigation, Central Intelligence Agency, Transportation Security
Administration, National Counterternorism Center, Terrorist Screening Center, Department of Treasury, and US.
Customs and Border Protection.
7? See Chapter 4, Section IX, for additional information regarding the full date of birth requirement and applicable
exceptions.
See Paragraph I.58 for expedited nominations procedures.
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
Page 50
OR OFFICIAL USE SECURITY INFORMATION
CHAPTER 4: NO FLY, SELECTEE AND EXPANDED SELECTEE LISTS
IMPLEMENTATION GUIDANCE
I. BACKGROUND
4.1 On October 2 2004, the Deputies Committee established the criteria for the No Fly and
Selectee Lists. On January 10, 2005, the DHS released the No Fly and Selectee Lists
Implementation Guidance (Implementation Guidance) to provide direction on how to
implement the No Fly and Selectee List criteria. The Implementation Guidance was updated
and supplemented on July 25, 2006.
4.2 On February 8, 2008, the Deputies Committee approved the addition of a third and fourth
criterion to the No Fly List. The Terrorist Screening Center Policy Board Working Group69
revised the Implementation Guidance on March 5, 2008, to provide direction on how to
implement these new criteria.
4.3 Following the attempted TERRORIST attack on December 25, 2009, the President directed that
a review of the current No Fly and Selectee List criteria be conducted and recommendations
be made regarding whether any adjustments were needed. The Terrorist Screening Center
Policy Board Working Group, in conjunction with the Information Sharing Access
recommended certain changes in the lists? criteria and implementation guidance. Those
recommendations were approved by the Deputies Committee on July 16, 2010.
Il. PRE-CONDITIONS FOR PLACEMENT ON THE FLY OR SELECTEE
LIST
4.4 Generally, in order to be included on either the No Fly or Selectee List, two pre-conditions
must both be met:
44.] Minimum Identifying Criteria. Absent a Special Situation as described below?,
minimum identifying biographic criteria consisting of First Name, Last Name, Full Date
of Birth are required; and,
4.4.2 Minimum Substantive Derogatory Criteria. The minimum substantive derogatory
criteria for inclusion must be met.?
This Working Group included representatives from Department of State, Department of Justice, Department of
Homeland Security, Federal Bureau of Investigation, Central Intelligence Agency, Transportation Security
Administration, National Counterternorism Center, Terrorist Screening Center, Department of Treasury, and US.
Customs and Border Protection.
7? See Chapter 4, Section IX, for additional information regarding the full date of birth requirement and applicable
exceptions.
See Paragraph I.58 for expedited nominations procedures.
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
Page 50

UN CLASSIF OFFICIAL USE SECURITY INFORMATION
4.5
4.6
IV.
4.7
NO FLY LIST CRITERIA
Any person, regardless of citizenship, who represents:
4.5.1 a threat of committing an act of ?international (as de?ned in 18 U.S.C.
2331(1)) or ?domestic (as de?ned in 18 U.S.C. 2331(5)) with respect to an
aircraft (including a threat of air piracy, or a threat to airline, passenger, or civil aviation
security); or,
4.5.2 a threat of committing an act of ?domestic (as de?ned in 18 U.S.C.
233 1 with respect to the homeland?; or,
4.5.3 a threat of committing an act of?international (as de?ned in 18 U.S.C.
2331(1)) against any US. Government facility abroad and associated or supporting
personnel, including US. embassies, consulates and missions, military installations (as
defined by 10 U.S.C. 2801(c)(4)), U.S. ships, U.S. aircraft, or other auxiliary cra?
owned or leased by the US. Government; or,
4.5.4 a threat of engaging in or conducting a violent act of TERRORISM and who is
OPERATIONALLY of doing so.
Detainees at the Naval Station, Guantanamo Bay, Cuba. Any individual who was a
?detainee? held at the Naval Station, Guantanamo Bay, Cuba, unless the President certi?es in
writing to Congress that the detainee poses no threat to the United States, its citizens, or its
allies. For purposes of this subparagraph, the term ?detainee? means an individual in the
custody or under the physical control of the United States as a result of armed conflict?4
FURTHER CLARIFICATION OF THE NO FLY CRITERIA
Third No Fly List Criterion. Prior to the addition of the third No Fly List criterion (see
Paragraph 4.5.3), a concern over the breadth of the No Fly List arose when KNOWN or
SUSPECTED TERRORISTS who posed a threat to a US. military base overseas did not meet the
criteria for inclusion on the No Fly List. Despite national interests, the threat to the overseas
military base did not involve either civil aviation (as set forth in the ?rst No Fly List criterion)
or an act of domestic TERRORISM to the homeland (as set forth in the second No Fly List
criterion). ?Domestic Terrorism? requires that a subject?s TERRORIST ACTIVITIES occur
primarily within the territorial jurisdiction of the United States. ?Homeland? does not include
bases and embassies located abroad. Even in those instances when the 1C had identi?ed a
KNOWN or SUSPECTED speci?c target, KNOWN or SUSPECTED
maintained the advantage of operational ?exibility. The third No Fly List criterion addresses
72 Domestic acts are those that primarily occur ?within the territorial jurisdiction of the United States.?
See 13 U.S.C.
7? See Paragraph 4.8.2, infra, that de?nes
7? See 49 U.S.C. 44903(i)(2)(C)(v).
OR OFFICIAL USE SECURITY INFORMATION
Page I 51
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
4.5
4.6
IV.
4.7
NO FLY LIST CRITERIA
Any person, regardless of citizenship, who represents:
4.5.1 a threat of committing an act of ?international (as de?ned in 18 U.S.C.
2331(1)) or ?domestic (as de?ned in 18 U.S.C. 2331(5)) with respect to an
aircraft (including a threat of air piracy, or a threat to airline, passenger, or civil aviation
security); or,
4.5.2 a threat of committing an act of ?domestic (as de?ned in 18 U.S.C.
233 1 with respect to the homeland?; or,
4.5.3 a threat of committing an act of?international (as de?ned in 18 U.S.C.
2331(1)) against any US. Government facility abroad and associated or supporting
personnel, including US. embassies, consulates and missions, military installations (as
defined by 10 U.S.C. 2801(c)(4)), U.S. ships, U.S. aircraft, or other auxiliary cra?
owned or leased by the US. Government; or,
4.5.4 a threat of engaging in or conducting a violent act of TERRORISM and who is
OPERATIONALLY of doing so.
Detainees at the Naval Station, Guantanamo Bay, Cuba. Any individual who was a
?detainee? held at the Naval Station, Guantanamo Bay, Cuba, unless the President certi?es in
writing to Congress that the detainee poses no threat to the United States, its citizens, or its
allies. For purposes of this subparagraph, the term ?detainee? means an individual in the
custody or under the physical control of the United States as a result of armed conflict?4
FURTHER CLARIFICATION OF THE NO FLY CRITERIA
Third No Fly List Criterion. Prior to the addition of the third No Fly List criterion (see
Paragraph 4.5.3), a concern over the breadth of the No Fly List arose when KNOWN or
SUSPECTED TERRORISTS who posed a threat to a US. military base overseas did not meet the
criteria for inclusion on the No Fly List. Despite national interests, the threat to the overseas
military base did not involve either civil aviation (as set forth in the ?rst No Fly List criterion)
or an act of domestic TERRORISM to the homeland (as set forth in the second No Fly List
criterion). ?Domestic Terrorism? requires that a subject?s TERRORIST ACTIVITIES occur
primarily within the territorial jurisdiction of the United States. ?Homeland? does not include
bases and embassies located abroad. Even in those instances when the 1C had identi?ed a
KNOWN or SUSPECTED speci?c target, KNOWN or SUSPECTED
maintained the advantage of operational ?exibility. The third No Fly List criterion addresses
72 Domestic acts are those that primarily occur ?within the territorial jurisdiction of the United States.?
See 13 U.S.C.
7? See Paragraph 4.8.2, infra, that de?nes
7? See 49 U.S.C. 44903(i)(2)(C)(v).
OR OFFICIAL USE SECURITY INFORMATION
Page I 51

UN CLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
4.8
this speci?c vulnerability and counters the ability of KNOWN or to
target US. Government facilities outside of the ?homeland? the October 12, 2000 attack
upon the US. Navy guided missile destroyer USS Cole while it was harbored in the Yemeni
port of Aden).
Fourth No Fly List Criterion.
4.8.1 Enable Flexibility. The fourth No Fly List criterion (see Paragraph 4.5.4) is intended to
enable flexibility for nominations to the No Fly List of OPERATIONALLY CAPABLE
KNOWN or TERRORISTS who pose a threat of committing an act of
international TERRORISM abroad, but who do not meet the ?rst, second or third No Fly
List criterion because they do not pose a threat to civil aviation, a threat to the homeland,
or a threat to US. facilities and their associated or supporting personnel. Previously, the
No Fly List criteria did not prevent KNOWN or SUSPECTED from traveling
aboard aircraft, even though they may have had the intent and OPERATIONAL CAPABILITY
to commit a act against US. nationals abroad (outside of the ?homeland?) or
against a target with no nexus to the United States or its nationals. The fourth NO Fly
List criterion now addresses these two vulnerabilities.
4.8.2 OPERATIONALLY CAPABLE De?ned. An individual is if,
based on credible intelligence, he or she, acting individually or in concert with others,
reasonably appears to have the ability, knowledge, opportunity, and intent or is actively
seeking the Opportunity to engage in a violent act of TERRORISM consistent with 18
U.S.C. 233] or l8 U.S.C. 2332b. For example, attempting to obtain an IED would
indicate an individual is CAPABLE of committing an act of TERRORISM.
However, simply conducting internet research concerning lEDs would not be sufficient
without additional activity. Depending on the circumstances, and in combination with
other facts, scouting potential targets or traveling for no legitimate purpose to places that
have TERRORIST training grounds, regardless Of whether the person is presently capable
of using an 1 ED, might also indicate an individual is OPERATIONALLY CAPABLE of
committing an act of TERRORISM.
4.8.3 Possible Indicators of Being OPERATIONALLY CAPABLE. In determining whether an
individual is OPERATIONALLY CAPABLE, consideration should be given to the following
indicators regarding ability, knowledge, opportunity, and/or intent:
Subject has undergone TERRORIST training or been provided some instruction,
to include receiving military training by a designated terrorist group;
4.8.3.2 Subject has indicated intent to participate in planning/conducting an attack;
4.8.3.3 Subject has expressed desire to martyr him/herself;
4.8.3.4 Subject is in repeated contact with a KNOWN facilitator who
recruits or facilitates travel of operatives;
4.8.3.5 Subject is planning an attack either alone or as part ofa group; or,
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 52
UN CLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
4.8
this speci?c vulnerability and counters the ability of KNOWN or to
target US. Government facilities outside of the ?homeland? the October 12, 2000 attack
upon the US. Navy guided missile destroyer USS Cole while it was harbored in the Yemeni
port of Aden).
Fourth No Fly List Criterion.
4.8.1 Enable Flexibility. The fourth No Fly List criterion (see Paragraph 4.5.4) is intended to
enable flexibility for nominations to the No Fly List of OPERATIONALLY CAPABLE
KNOWN or TERRORISTS who pose a threat of committing an act of
international TERRORISM abroad, but who do not meet the ?rst, second or third No Fly
List criterion because they do not pose a threat to civil aviation, a threat to the homeland,
or a threat to US. facilities and their associated or supporting personnel. Previously, the
No Fly List criteria did not prevent KNOWN or SUSPECTED from traveling
aboard aircraft, even though they may have had the intent and OPERATIONAL CAPABILITY
to commit a act against US. nationals abroad (outside of the ?homeland?) or
against a target with no nexus to the United States or its nationals. The fourth NO Fly
List criterion now addresses these two vulnerabilities.
4.8.2 OPERATIONALLY CAPABLE De?ned. An individual is if,
based on credible intelligence, he or she, acting individually or in concert with others,
reasonably appears to have the ability, knowledge, opportunity, and intent or is actively
seeking the Opportunity to engage in a violent act of TERRORISM consistent with 18
U.S.C. 233] or l8 U.S.C. 2332b. For example, attempting to obtain an IED would
indicate an individual is CAPABLE of committing an act of TERRORISM.
However, simply conducting internet research concerning lEDs would not be sufficient
without additional activity. Depending on the circumstances, and in combination with
other facts, scouting potential targets or traveling for no legitimate purpose to places that
have TERRORIST training grounds, regardless Of whether the person is presently capable
of using an 1 ED, might also indicate an individual is OPERATIONALLY CAPABLE of
committing an act of TERRORISM.
4.8.3 Possible Indicators of Being OPERATIONALLY CAPABLE. In determining whether an
individual is OPERATIONALLY CAPABLE, consideration should be given to the following
indicators regarding ability, knowledge, opportunity, and/or intent:
Subject has undergone TERRORIST training or been provided some instruction,
to include receiving military training by a designated terrorist group;
4.8.3.2 Subject has indicated intent to participate in planning/conducting an attack;
4.8.3.3 Subject has expressed desire to martyr him/herself;
4.8.3.4 Subject is in repeated contact with a KNOWN facilitator who
recruits or facilitates travel of operatives;
4.8.3.5 Subject is planning an attack either alone or as part ofa group; or,
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 52

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
4.9
4.10
4.8.3.6 Subject is associated with a TERRORIST group/cell and the subject is
accumulating weapons/explosives.
OPERATIONALLY CAPABLE Scenarios. The three scenarios set forth below serve as some
examples of No Fly List nominations that would fall under the fourth No Fly List criterion:
There is credible information that the planning or preparation for a TERRORIST attack
against the interests of the United States or a foreign government is ongoing and there is
an indication that an individual is OPERATIONALLY
4.9.2 There is credible information that an individual is linked with an organization known to
target US interests. The actual target may be unknown but indicated to be a
commercial facility frequented by US. citizens abroad. Intelligence identi?es an
operational or pre-operational capability of this individual whose cell is planning a near-
term attack on a target a plot to kill U.S. nationals residing in a foreign hotel or
frequenting a foreign or,
4.9.3 There is credible information that an individual is linked with an organization known to
target foreign governments. The actual target may be unknown but indicated to be a
foreign government facility such as an embassy, consulate, mission or military
installation. Intelligence identi?es an operational or pre?operational capability of this
individual whose cell is planning a near-term attack on a target a plot to bomb the
British Parliament or the March 1 l, 2004, Madrid bombing).
One-Time Waiver Policy.
4. I 0.1 TSA regulations prohibit U.S. flagged air carriers and foreign flagged air carriers
from transporting individuals, who pose the level of threat required for No Fly status, on
regulated commercial flights, including all ?ights operated by US air carriers
regardless of the location, and ?ights operated by foreign air carriers to, from, or over
the United States. This prohibition applies regardless of the individual?s status as a US.
PERSON.
4.10.2 When necessary, the US. Government may authorize and grant a One Time Waiver
(OTW) to an air carrier permitting the carrier to transport an individual on a specified
itinerary under controlled conditions. OTWs are coordinated with DHS (including CBP
and TSA), FBI, DOS and DOJ as appropriate, prior to being authorized by TSC. Once
authorized by TSC, TSA will review the conditions of transport and may grant the
waiver, permitting the air carrier to transport the individual. If the itinerary changes, or
the conditions of transport of the individual change, TSA will deny boarding to the
individual until such time as satisfactory conditions are present.
4.10.3 U.S. PERSONS Encountered Overseas.
4.10.3.1 While placement on the No Fly List does not legally bar 3 us. PERSON from
UNCLASSIF OR OFFICIAL USE IVE SECURITY INFORMATION
Page i 53
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
4.9
4.10
4.8.3.6 Subject is associated with a TERRORIST group/cell and the subject is
accumulating weapons/explosives.
OPERATIONALLY CAPABLE Scenarios. The three scenarios set forth below serve as some
examples of No Fly List nominations that would fall under the fourth No Fly List criterion:
There is credible information that the planning or preparation for a TERRORIST attack
against the interests of the United States or a foreign government is ongoing and there is
an indication that an individual is OPERATIONALLY
4.9.2 There is credible information that an individual is linked with an organization known to
target US interests. The actual target may be unknown but indicated to be a
commercial facility frequented by US. citizens abroad. Intelligence identi?es an
operational or pre-operational capability of this individual whose cell is planning a near-
term attack on a target a plot to kill U.S. nationals residing in a foreign hotel or
frequenting a foreign or,
4.9.3 There is credible information that an individual is linked with an organization known to
target foreign governments. The actual target may be unknown but indicated to be a
foreign government facility such as an embassy, consulate, mission or military
installation. Intelligence identi?es an operational or pre?operational capability of this
individual whose cell is planning a near-term attack on a target a plot to bomb the
British Parliament or the March 1 l, 2004, Madrid bombing).
One-Time Waiver Policy.
4. I 0.1 TSA regulations prohibit U.S. flagged air carriers and foreign flagged air carriers
from transporting individuals, who pose the level of threat required for No Fly status, on
regulated commercial flights, including all ?ights operated by US air carriers
regardless of the location, and ?ights operated by foreign air carriers to, from, or over
the United States. This prohibition applies regardless of the individual?s status as a US.
PERSON.
4.10.2 When necessary, the US. Government may authorize and grant a One Time Waiver
(OTW) to an air carrier permitting the carrier to transport an individual on a specified
itinerary under controlled conditions. OTWs are coordinated with DHS (including CBP
and TSA), FBI, DOS and DOJ as appropriate, prior to being authorized by TSC. Once
authorized by TSC, TSA will review the conditions of transport and may grant the
waiver, permitting the air carrier to transport the individual. If the itinerary changes, or
the conditions of transport of the individual change, TSA will deny boarding to the
individual until such time as satisfactory conditions are present.
4.10.3 U.S. PERSONS Encountered Overseas.
4.10.3.1 While placement on the No Fly List does not legally bar 3 us. PERSON from
UNCLASSIF OR OFFICIAL USE IVE SECURITY INFORMATION
Page i 53

OR OFFICIAL USE SECURITY INFORMATION
returning to the United States, the US. Government has adepted a policy to review
all cases in which a U.S. PERSON on the No Fly List is denied boarding on a
commercial ?ight bound for the United States to determine whether an OTW may
be appropriate. TSC will initiate this assessment immediately, and may approve an
OTW in advance. TSA will not review or authorize an OTW until such time as an
acceptable itinerary is available.
4.10.3.2 In order to facilitate communication with such an individual, the US. Government
has determined, as a matter of policy, that US. Citizens denied boarding on a
commercial ?ight returning to the United States should be referred to the consular
section of the nearest US. Embassy or Consulate, which will facilitate communication
with the individual, including providing the individual with instructions in the event an
OTW is authorized. in keeping with the US. Government?s traditional policy of neither
continuing nor denying whether an individual is on the Terrorist Watchlist, the
individual is not informed of his or her watchlist status or that he or she would be
traveling under a waiver.
V. SELECTEE LIST CRITERIA
4.1 Selectee List Criteria. Any person regardless of citizenship, who does not meet the criteria
for inclusion on the No Fly List and who:
is a member of a foreign or domestic TERRORIST organization? (including a ?foreign
organization? designated pursuant to Statute or Executive Order, as described
in Paragraph 3.11.2); and,
4.1 1.2 is associated with (as such term is defined in section
212(a)(3)(B) of the [8 U.S.C. unless information exists that
demonstrates that the application of secondary screening to such person is not necessary,
in which case such persons may be excluded from the Selectee List.
VI. EXPANDED SELECTEE LIST CRITERIA
4.12 The Expanded Selectee List (ESEL) includes records in the TSDB that contain a full name
and full date of birth, regardless of the citizenship of the subject, who do not meet the criteria
to be placed on either the No Fly or Selectee Lists, excluding exceptions to the REASONABLE
SUSPICION standard.
VII. ACTIONS BASED UPON POSITIVE MATCHES TO THE NO FLY,
SELECTEE, OR EXPANDED SELECTEE LISTS
75 Members of a defunct terrorist group are included in this criterion if the person was a member of the group when it
participated in ACTIVITY.
UN OFFICIAL USE SECURITY INFORMATION
Page I 54
OR OFFICIAL USE SECURITY INFORMATION
returning to the United States, the US. Government has adepted a policy to review
all cases in which a U.S. PERSON on the No Fly List is denied boarding on a
commercial ?ight bound for the United States to determine whether an OTW may
be appropriate. TSC will initiate this assessment immediately, and may approve an
OTW in advance. TSA will not review or authorize an OTW until such time as an
acceptable itinerary is available.
4.10.3.2 In order to facilitate communication with such an individual, the US. Government
has determined, as a matter of policy, that US. Citizens denied boarding on a
commercial ?ight returning to the United States should be referred to the consular
section of the nearest US. Embassy or Consulate, which will facilitate communication
with the individual, including providing the individual with instructions in the event an
OTW is authorized. in keeping with the US. Government?s traditional policy of neither
continuing nor denying whether an individual is on the Terrorist Watchlist, the
individual is not informed of his or her watchlist status or that he or she would be
traveling under a waiver.
V. SELECTEE LIST CRITERIA
4.1 Selectee List Criteria. Any person regardless of citizenship, who does not meet the criteria
for inclusion on the No Fly List and who:
is a member of a foreign or domestic TERRORIST organization? (including a ?foreign
organization? designated pursuant to Statute or Executive Order, as described
in Paragraph 3.11.2); and,
4.1 1.2 is associated with (as such term is defined in section
212(a)(3)(B) of the [8 U.S.C. unless information exists that
demonstrates that the application of secondary screening to such person is not necessary,
in which case such persons may be excluded from the Selectee List.
VI. EXPANDED SELECTEE LIST CRITERIA
4.12 The Expanded Selectee List (ESEL) includes records in the TSDB that contain a full name
and full date of birth, regardless of the citizenship of the subject, who do not meet the criteria
to be placed on either the No Fly or Selectee Lists, excluding exceptions to the REASONABLE
SUSPICION standard.
VII. ACTIONS BASED UPON POSITIVE MATCHES TO THE NO FLY,
SELECTEE, OR EXPANDED SELECTEE LISTS
75 Members of a defunct terrorist group are included in this criterion if the person was a member of the group when it
participated in ACTIVITY.
UN OFFICIAL USE SECURITY INFORMATION
Page I 54

UN OR OFFICIAL USE ON SECURITY INFORMATION
4.13 The actions resulting from inclusion on the No Fly, Selectee, or Expanded Selectee List are
generally as follows:
4.13.1 Individuals that are POSITIVE to the No Fly List are prohibited from
boarding an aircra?;
4.13.2 Individuals that are POSITIVE MATCHES to the Selectee List undergo enhanced
screening prior to boarding an aircra?;
4.13.3 Individuals that are POSITIVE MATCHES to the Expanded Selectee List undergo
enhanced screening prior to boarding an aircraft.
4.14 Selectee, Expanded Selectee, and random screening all result in the same operational response
of receiving enhanced screening by Transportation Security Of?cers prior to boarding an
aircraft. TSA will notify the TSC of all No Fly, Selectee, and Expanded Selectee
ENCOUNTERS.
IMPLEMENTATION GUIDELINES
4.15 General Guidelines. The watchlisting community has developed six general guidelines
regarding the No Fly and Selectee Lists that should be reemphasized in order to effectively
implement the No Fly List and Selectee List criteria. The six general guidelines are:
4.15.1 When evaluating the signi?cance, relevance and validity of a threat, careful
consideration should be given to the extent to which the threat is current, speci?c and
credible.
4.15.2 The Selectee List is not a default position for those who do not qualify for inclusion
on the No Fly List and has distinct elements that must be met before an individual may
be included.
4.15.3 The purpose of the No Fly List is to protect against acts of inclusion on
the No Fly List has consequences that are operational, legal, economic, and diplomatic.
4.15.4 Except for expedited nominations made pursuant to Paragraph 1.58 of the
Watchlisting Guidance, the decision to include a person on the No Fly List or Selectee
List must include substantive DEROGATORY INFORMATION that satis?es the
aforementioned criteria and thus justi?es inclusion on either list. In cases where
nominations contain no substantive DEROGATORY INFORMATION, or contain insuf?cient
substantive DEROGATORY INFORMATION, the individual will not be included on either the
No Fly List or Selectee List.
4.15.5 In accordance with determinations made pursuant to Paragraph 1.59 of the
Watchlisting Guidance, the White House may direct the TSC to place categories of
individuals on the No Fly List or the Selectee List on a temporary basis based on current
OFFICIAL USE SECURITY INFORMATION
Page 55
UN OR OFFICIAL USE ON SECURITY INFORMATION
4.13 The actions resulting from inclusion on the No Fly, Selectee, or Expanded Selectee List are
generally as follows:
4.13.1 Individuals that are POSITIVE to the No Fly List are prohibited from
boarding an aircra?;
4.13.2 Individuals that are POSITIVE MATCHES to the Selectee List undergo enhanced
screening prior to boarding an aircra?;
4.13.3 Individuals that are POSITIVE MATCHES to the Expanded Selectee List undergo
enhanced screening prior to boarding an aircraft.
4.14 Selectee, Expanded Selectee, and random screening all result in the same operational response
of receiving enhanced screening by Transportation Security Of?cers prior to boarding an
aircraft. TSA will notify the TSC of all No Fly, Selectee, and Expanded Selectee
ENCOUNTERS.
IMPLEMENTATION GUIDELINES
4.15 General Guidelines. The watchlisting community has developed six general guidelines
regarding the No Fly and Selectee Lists that should be reemphasized in order to effectively
implement the No Fly List and Selectee List criteria. The six general guidelines are:
4.15.1 When evaluating the signi?cance, relevance and validity of a threat, careful
consideration should be given to the extent to which the threat is current, speci?c and
credible.
4.15.2 The Selectee List is not a default position for those who do not qualify for inclusion
on the No Fly List and has distinct elements that must be met before an individual may
be included.
4.15.3 The purpose of the No Fly List is to protect against acts of inclusion on
the No Fly List has consequences that are operational, legal, economic, and diplomatic.
4.15.4 Except for expedited nominations made pursuant to Paragraph 1.58 of the
Watchlisting Guidance, the decision to include a person on the No Fly List or Selectee
List must include substantive DEROGATORY INFORMATION that satis?es the
aforementioned criteria and thus justi?es inclusion on either list. In cases where
nominations contain no substantive DEROGATORY INFORMATION, or contain insuf?cient
substantive DEROGATORY INFORMATION, the individual will not be included on either the
No Fly List or Selectee List.
4.15.5 In accordance with determinations made pursuant to Paragraph 1.59 of the
Watchlisting Guidance, the White House may direct the TSC to place categories of
individuals on the No Fly List or the Selectee List on a temporary basis based on current
OFFICIAL USE SECURITY INFORMATION
Page 55

UNCLASSIF OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
and credible intelligence information or a particular threat stream that indicates a certain
. category of individuals may conduct an act of domestic or international TERRORISM.
4.15.6 Under exigent operational circumstances, when INFORMATION may not
be widely disseminated or stored in TIDE, individual watchlist status determinations can
be made by the Director of the TSC, in accordance with the relevant criteria76 contained
in the Watchlisting Guidance. Coordination should occur with relevant
AGENCIES and SCREENERS.
4.16 Totality of the Information. The foregoing guidance is neither intended to be determinative
nor intended to serve as a checklist. Rather, it is intended to guide the watchlisting
community in assessing whether the established criteria are satis?ed for a speci?c record,
based on the totality of available information, a current threat stream, and/or the current threat
environment.
1x. SPECIAL SITUATIONS77
4.17 Requirement for Full Names and Complete Dates of Birth. Generally, TERRORIST
4.18
identities nominated to either the No Fly or the Selectee List must have both a full name and a
complete date of birth. Identities without both will usually not be included on either list.
Dates of birth shall not be fabricated}?8
4.17.1 There is, however, a narrow exception to the requirement for full names and
complete dates of birth for individuals from non-Visa Waiver Program countries for
international TERRORIST nominations. if a non-Visa Waiver Program country79 has
issued a travel document with only a year of birth, or a veri?ed government?issued
identification document with only a year of birth, then it is permissible to use only that
year of birth. The AGENCY, however, should, whenever possible, specify
the type of document containing the year of birth, and the passport number (if the
document is a passport). Otherwise, a year of birth alone will not be accepted for
nominations to the No Fly or Selectee Lists. The NOMINATING AGENCY has a continuing
obligation to attempt to determine the complete date of birth.
Expedited Waiver of ?Full Date of Birth? Requirement for No Fly or Selectee
Nominations. When necessitated by exigent circumstances, a may nominate an
individual or individuals to the No Fly or Selectee List with only a partial date of birth, but for
whom there is additional identifying information. This provision is intended to enable
nominations based on current and credible intelligence information or a particular threat
77
7" Determinations made under this section apply to the No Fly, Selectee and Expanded Selectee List criteria.
See Paragraph 1.59 for a complete discussion of expedited nomination procedures for temporary, threat-based
categories.
7? The dates of birth ofJanuary 1 July 1 November 1 1 (1 1/1 and December 31
are examples of dates that may be fabricated and as such, should receive additional scrutiny at all stages of
the reporting, nomination, and watchlisting process.
79 Visa Waiver Program countries include a complete date of birth in their passports.
UN OR OFFICIAL USE SECURITY INFORMATION
Page 56
UNCLASSIF OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
and credible intelligence information or a particular threat stream that indicates a certain
. category of individuals may conduct an act of domestic or international TERRORISM.
4.15.6 Under exigent operational circumstances, when INFORMATION may not
be widely disseminated or stored in TIDE, individual watchlist status determinations can
be made by the Director of the TSC, in accordance with the relevant criteria76 contained
in the Watchlisting Guidance. Coordination should occur with relevant
AGENCIES and SCREENERS.
4.16 Totality of the Information. The foregoing guidance is neither intended to be determinative
nor intended to serve as a checklist. Rather, it is intended to guide the watchlisting
community in assessing whether the established criteria are satis?ed for a speci?c record,
based on the totality of available information, a current threat stream, and/or the current threat
environment.
1x. SPECIAL SITUATIONS77
4.17 Requirement for Full Names and Complete Dates of Birth. Generally, TERRORIST
4.18
identities nominated to either the No Fly or the Selectee List must have both a full name and a
complete date of birth. Identities without both will usually not be included on either list.
Dates of birth shall not be fabricated}?8
4.17.1 There is, however, a narrow exception to the requirement for full names and
complete dates of birth for individuals from non-Visa Waiver Program countries for
international TERRORIST nominations. if a non-Visa Waiver Program country79 has
issued a travel document with only a year of birth, or a veri?ed government?issued
identification document with only a year of birth, then it is permissible to use only that
year of birth. The AGENCY, however, should, whenever possible, specify
the type of document containing the year of birth, and the passport number (if the
document is a passport). Otherwise, a year of birth alone will not be accepted for
nominations to the No Fly or Selectee Lists. The NOMINATING AGENCY has a continuing
obligation to attempt to determine the complete date of birth.
Expedited Waiver of ?Full Date of Birth? Requirement for No Fly or Selectee
Nominations. When necessitated by exigent circumstances, a may nominate an
individual or individuals to the No Fly or Selectee List with only a partial date of birth, but for
whom there is additional identifying information. This provision is intended to enable
nominations based on current and credible intelligence information or a particular threat
77
7" Determinations made under this section apply to the No Fly, Selectee and Expanded Selectee List criteria.
See Paragraph 1.59 for a complete discussion of expedited nomination procedures for temporary, threat-based
categories.
7? The dates of birth ofJanuary 1 July 1 November 1 1 (1 1/1 and December 31
are examples of dates that may be fabricated and as such, should receive additional scrutiny at all stages of
the reporting, nomination, and watchlisting process.
79 Visa Waiver Program countries include a complete date of birth in their passports.
UN OR OFFICIAL USE SECURITY INFORMATION
Page 56

OR OFFICIAL USE SECURITY INFORMATION
stream that indicates the subject(s) may be used to conduct an act of domestic or international
terrorism as de?ned in 18 U.S.C. 2331(1), or as a Federal crime of terrorism as de?ned in 18
U.S.C. 2332b(g)(5). The goal of this provision is to fashion a watchlisting response that is
apprOpriate to the nature, speci?city, and severity of the threat. To achieve this goal, in
addition to the credibility of the threat intelligence, due consideration should be given to:
4.18.1 The harm to public safety posed by the threat;
4.18.2 The clarity and speci?city of the information giving rise to the threat as to time,
place, method, and identity of the suspected perpetrator(s);
4.18.3 The anticipated impact on international and domestic travel, civil liberties,
and foreign relations; and,
4.18.4 The best available screening tools, other than the No Fly or Selectee Lists, given the
type and speci?city of identi?ers and travel data.
4.19 This waiver should be utilized in limited circumstances when extreme DBROGATORY
INFORMATION has been identi?ed demonstrating the threat. The waiver should be valid as
long as the threat remains.
x. NOMINATIONS THAT ARE SUITABLE FOR EITHER
THE NO FLY OR THE SELECTEE LIST80
4.20 Nominations based on exceptions to the minimum substantive derogatory criteria contained in
Paragraph 3.14, including immediate family members of TERRORISTS spouses or children
of a KNOWN or SUSPECTED are ineligible/not suitable for inclusion on either the
No Fly or Selectee List, absent independent DEROGATORY
4.2] Subjects of lost or stolen passports or travel documents are ineligible/not suitable for inclusion
on either the No Fly or Selectee List, absent independent DEROGATORY
4.22 Deceased individuals are ineligible for inclusion on either the NO Fly or Selectee List unless
they meet the exceptions set forth in Paragraph 3.17, Identities of Deceased Individuals.
so This section can be overridden in the event of an expedited, threat-based categorical nomination procedures, pursuant
to Paragraph 1.59.
8? See INA U.S.C.
OR OFFICIAL USE SECURITY INFORMATION
Page 57
OR OFFICIAL USE SECURITY INFORMATION
stream that indicates the subject(s) may be used to conduct an act of domestic or international
terrorism as de?ned in 18 U.S.C. 2331(1), or as a Federal crime of terrorism as de?ned in 18
U.S.C. 2332b(g)(5). The goal of this provision is to fashion a watchlisting response that is
apprOpriate to the nature, speci?city, and severity of the threat. To achieve this goal, in
addition to the credibility of the threat intelligence, due consideration should be given to:
4.18.1 The harm to public safety posed by the threat;
4.18.2 The clarity and speci?city of the information giving rise to the threat as to time,
place, method, and identity of the suspected perpetrator(s);
4.18.3 The anticipated impact on international and domestic travel, civil liberties,
and foreign relations; and,
4.18.4 The best available screening tools, other than the No Fly or Selectee Lists, given the
type and speci?city of identi?ers and travel data.
4.19 This waiver should be utilized in limited circumstances when extreme DBROGATORY
INFORMATION has been identi?ed demonstrating the threat. The waiver should be valid as
long as the threat remains.
x. NOMINATIONS THAT ARE SUITABLE FOR EITHER
THE NO FLY OR THE SELECTEE LIST80
4.20 Nominations based on exceptions to the minimum substantive derogatory criteria contained in
Paragraph 3.14, including immediate family members of TERRORISTS spouses or children
of a KNOWN or SUSPECTED are ineligible/not suitable for inclusion on either the
No Fly or Selectee List, absent independent DEROGATORY
4.2] Subjects of lost or stolen passports or travel documents are ineligible/not suitable for inclusion
on either the No Fly or Selectee List, absent independent DEROGATORY
4.22 Deceased individuals are ineligible for inclusion on either the NO Fly or Selectee List unless
they meet the exceptions set forth in Paragraph 3.17, Identities of Deceased Individuals.
so This section can be overridden in the event of an expedited, threat-based categorical nomination procedures, pursuant
to Paragraph 1.59.
8? See INA U.S.C.
OR OFFICIAL USE SECURITY INFORMATION
Page 57

OR OFFICIAL USE SECURITY INFORMATION
I.
5.1
5.2
CHAPTER 5: ENCOUNTER MANAGEMENT AND ANALYSIS
INTRODUCTION AND PURPOSE
This guidance addresses the collection, processing, and analysis of TERRORISM INFORMATION
collected by the SCREENERS during an ENCOUNTER with a watchlisted subject. As described
below, all information gathered during an ENCOUNTER with a KNOWN or SUSPECTED
is referred to as an ENCOUNTER PACKAGE. This guidance does not create any
new authorities for the collection of any information during ENCOUNTERS with KNOWN or
SUSPECTED TERRORISTS. Rather, it identi?es the types of information that a Department or
Agency should consider collecting during an ENCOUNTER with a KNOWN or SUSPECTED
TERRORIST if it possesses the authority to collect such information, and should share with the
interagency community consistent with their legal authorities and executive policy.83
De?nitions.
5.2.1 ENCOUNTER. An ENCOUNTER is de?ned as an event in which an individual is identi?ed
during a screening process to be a or
to an individual who has been designated in the TSDB as a
KNOWN or SUSPECTED TERRORIST. An ENCOUNTER can be a face-to-face meeting with a
KNOWN or SUSPECTED TERRORIST, electronic or a paper-based ENCOUNTER the
KNOWN or SUSPECTED TERRORIST has submitted an application for a bene?t liked a visa,
Electronic System for Travel Authorization (ESTA) application, or information is
provided to the United States by a foreign government, aircraft operator, or other private
entity). Chapter 5 is only concerned with POSITIVE MATCHES, which occur when the
TSC determines that information about a subject encountered by a SCREENER matches a
TSDB record.
5.2.2 TERRORISM INFORMATION. TERRORISM INFORMATION in this chapter includes purely
domestic terrorism as de?ned in the TSC MOU and incorporates the de?nition found in
in section lOl6 ofthe (6 U.S.C 485), as amended. The term
means
5.2.2.1 all information, whether collected, produced, or distributed by intelligence,
law enforcement, military, homeland security, or other activities relating tow?
the existence, organization, capabilities, plans, intentions,
vulnerabilities, means of ?nance or material support, or activities of foreign
or international terrorist groups or individuals, or of domestic groups or
82 Sharing infonnation for reasons not related to KNOWN or SUSPECTED TERRORIST categories should be limited to
updating biographic identi?ers, and the sharing of relevant information that may assist in making decisions related to a
change in a person?s status in the TSDB and/or TERRORISM INFORMATION.
83 Obligations include those imposed by section 102] or by interagency agreement the Information
Sharing MOU (Appendix 5), the TSC MOU (Appendix 3) and Addendum to the TSC MOU (Appendix
UN OFFICIAL USE SECURITY INFORMATION
Page 58
OR OFFICIAL USE SECURITY INFORMATION
I.
5.1
5.2
CHAPTER 5: ENCOUNTER MANAGEMENT AND ANALYSIS
INTRODUCTION AND PURPOSE
This guidance addresses the collection, processing, and analysis of TERRORISM INFORMATION
collected by the SCREENERS during an ENCOUNTER with a watchlisted subject. As described
below, all information gathered during an ENCOUNTER with a KNOWN or SUSPECTED
is referred to as an ENCOUNTER PACKAGE. This guidance does not create any
new authorities for the collection of any information during ENCOUNTERS with KNOWN or
SUSPECTED TERRORISTS. Rather, it identi?es the types of information that a Department or
Agency should consider collecting during an ENCOUNTER with a KNOWN or SUSPECTED
TERRORIST if it possesses the authority to collect such information, and should share with the
interagency community consistent with their legal authorities and executive policy.83
De?nitions.
5.2.1 ENCOUNTER. An ENCOUNTER is de?ned as an event in which an individual is identi?ed
during a screening process to be a or
to an individual who has been designated in the TSDB as a
KNOWN or SUSPECTED TERRORIST. An ENCOUNTER can be a face-to-face meeting with a
KNOWN or SUSPECTED TERRORIST, electronic or a paper-based ENCOUNTER the
KNOWN or SUSPECTED TERRORIST has submitted an application for a bene?t liked a visa,
Electronic System for Travel Authorization (ESTA) application, or information is
provided to the United States by a foreign government, aircraft operator, or other private
entity). Chapter 5 is only concerned with POSITIVE MATCHES, which occur when the
TSC determines that information about a subject encountered by a SCREENER matches a
TSDB record.
5.2.2 TERRORISM INFORMATION. TERRORISM INFORMATION in this chapter includes purely
domestic terrorism as de?ned in the TSC MOU and incorporates the de?nition found in
in section lOl6 ofthe (6 U.S.C 485), as amended. The term
means
5.2.2.1 all information, whether collected, produced, or distributed by intelligence,
law enforcement, military, homeland security, or other activities relating tow?
the existence, organization, capabilities, plans, intentions,
vulnerabilities, means of ?nance or material support, or activities of foreign
or international terrorist groups or individuals, or of domestic groups or
82 Sharing infonnation for reasons not related to KNOWN or SUSPECTED TERRORIST categories should be limited to
updating biographic identi?ers, and the sharing of relevant information that may assist in making decisions related to a
change in a person?s status in the TSDB and/or TERRORISM INFORMATION.
83 Obligations include those imposed by section 102] or by interagency agreement the Information
Sharing MOU (Appendix 5), the TSC MOU (Appendix 3) and Addendum to the TSC MOU (Appendix
UN OFFICIAL USE SECURITY INFORMATION
Page 58

OR OFFICIAL USE SECURITY INFORMATION
II.
individuals involved in transnational
.2 threats posed by such groups or individuals to the United States, US.
PERSONS, or US. interests, or to those of other nations;
5.2.2. I .3
5.2.2.1.4 groups or individuals reasonably believed to be assisting or associated
with such groups or individuals; and
communications of or by such groups or individuals; or,
5.2.2.2 includes weapons of mass destruction information.
5.2.2.2.1 Weapons of Mass Destruction Information. Information that could
reasonably be expected to assist in the develOpment, proliferation, or use of a
weapon of mass destruction (including a chemical, biological, radiological, or
nuclear weapon) that could be used by a TERRORIST or a terrorist organization
against the United States, including information about the location of any stockpile
of nuclear materials that could be exploited for use in such a weapon that could be
used by a TERRORIST or a terrorist organization against the United States.
PROCESSING TERRORISM INFORMATION FROM ENCOUNTERS
WITH POSITIVELY IDENTIFIED KNOWN OR SUSPECTED
TERRORISTS
5.3 This section describes the major types of ENCOUNTERS by various Departments and Agencies.
5.4
ENCOUNTER PACKAGES obtained from a KNOWN or SUSPECTED TERRORIST ENCOUNTER will be
processed as follows:
Department of Homeland Security ENCOUNTERS. DHS has more ENCOUNTERS with
KNOWN or SUSPECTED TERRORISTS than any other US. Government component. The
descriptions below provide information for the majority of DHS ENCOUNTERS, although it is
not an exhaustive list of ENCOUNTER opportunities or the types of TERRORISM INFORMATION
available for collection. When lawful and available, both biographic and biometric
information will be collected as part of the ENCOUNTER PACKAGE.
US. Customs and Border Protection. CBP ENCOUNTERS occur at ports of entry
(POE), between POEs, or at the last point of departure to the United States at foreign
airports through CBP programs like Pre-Clearance and the Immigration Advisory
Program (IAP). Information available for collection from these ENCOUNTERS may
include, but is not limited to, pocket litter, travel information, identi?cation documents,
travel companions, legal documents, and other information gathered during interviews
and the examination process. CBP receives international travel reservation information
of KNOWN or SUSPECTED TERRORISTS for commercial air travel to and from the United
States (which may include travel companion information) and international private and
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
Page I 59
OR OFFICIAL USE SECURITY INFORMATION
II.
individuals involved in transnational
.2 threats posed by such groups or individuals to the United States, US.
PERSONS, or US. interests, or to those of other nations;
5.2.2. I .3
5.2.2.1.4 groups or individuals reasonably believed to be assisting or associated
with such groups or individuals; and
communications of or by such groups or individuals; or,
5.2.2.2 includes weapons of mass destruction information.
5.2.2.2.1 Weapons of Mass Destruction Information. Information that could
reasonably be expected to assist in the develOpment, proliferation, or use of a
weapon of mass destruction (including a chemical, biological, radiological, or
nuclear weapon) that could be used by a TERRORIST or a terrorist organization
against the United States, including information about the location of any stockpile
of nuclear materials that could be exploited for use in such a weapon that could be
used by a TERRORIST or a terrorist organization against the United States.
PROCESSING TERRORISM INFORMATION FROM ENCOUNTERS
WITH POSITIVELY IDENTIFIED KNOWN OR SUSPECTED
TERRORISTS
5.3 This section describes the major types of ENCOUNTERS by various Departments and Agencies.
5.4
ENCOUNTER PACKAGES obtained from a KNOWN or SUSPECTED TERRORIST ENCOUNTER will be
processed as follows:
Department of Homeland Security ENCOUNTERS. DHS has more ENCOUNTERS with
KNOWN or SUSPECTED TERRORISTS than any other US. Government component. The
descriptions below provide information for the majority of DHS ENCOUNTERS, although it is
not an exhaustive list of ENCOUNTER opportunities or the types of TERRORISM INFORMATION
available for collection. When lawful and available, both biographic and biometric
information will be collected as part of the ENCOUNTER PACKAGE.
US. Customs and Border Protection. CBP ENCOUNTERS occur at ports of entry
(POE), between POEs, or at the last point of departure to the United States at foreign
airports through CBP programs like Pre-Clearance and the Immigration Advisory
Program (IAP). Information available for collection from these ENCOUNTERS may
include, but is not limited to, pocket litter, travel information, identi?cation documents,
travel companions, legal documents, and other information gathered during interviews
and the examination process. CBP receives international travel reservation information
of KNOWN or SUSPECTED TERRORISTS for commercial air travel to and from the United
States (which may include travel companion information) and international private and
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
Page I 59

OR OFFICIAL USE SECURITY INFORMATION
commercial ?ight manifests, as well as, commercial vessel manifest for travel to and
from the United States. With the exception of passenger information required by law to
be transmitted to DHS prior to a passenger?s arrival, most information is generally
collected by CBP when the person is interviewed or apprehended. The National
Targeting Center Passenger and NTC-Cargo (NTC-C) are CBP entities
responsible for communicating with the TSC regarding ENCOUNTERS with KNOWN or
SUSPECTED to include providing relevant ENCOUNTER information.?
and NTC-C also provide a copy of the examination results to the TSOU for
dissemination to the appropriate investigating Agencies.
5.4.2 Transportation Security Administration. TSA generally encounters KNOWN or
TERRORISTS through screening commercial aircraft passengers against
subsets of the and during the application process for a credential or bene?t in the
transportation or critical infrastructure environment Transportation Worker
Identi?cation Credential When an airline encounters subjects who are
possible matches to the NO 1y or Selectee List, the air carriers are required to supply the
passenger?s name and one piece of identifying data (in the form of a govemment-issued
photo identi?cation that contains a date of birth) to the Of?ce of Intelligence and
Analysis TSA submits that information, along with information regarding
the carrier, ?ight number, time of departure, and destination to the TSC.
5.4.2.1 Absent an arrest warrant, or unless probable cause arises during the
ENCOUNTER, SCREENERS are reminded that placement on the No Fly or Selectee
List is not a legal basis to detain a KNOWN or SUSPECTED TERRORIST. To the
extent legal authority exists to question a KNOWN or SUSPECTED TERRORIST,
encounters with No Fly subjects at the airport may provide an additional
opportunity to lawfully obtain ENCOUNTER PACKAGE information. For No Fly
subjects who have made a domestic reservation, DHS will notify TSC in advance
as well as when the No Fly subject presents at the airport ticket counter. TSC will
then notify the TSOU who will notify both the l?Bl case agent and the airport
liaison agent to coordinate the appropriate operational response.
5.4.2.2 For KNOWN or SUSPECTED TERRORIST ENCOUNTERS as a result of an
individual applying for a TSA bene?t or credential, ENCOUNTER PACKAGE
information can include any supporting documents or information collected as a
part of the application process. The ENCOUNTER, and any corresponding
information, is communicated to the TSC and other Government Agencies, as
appropriate through TSA
5.4.3 United States Citizenship and Immigration Services. US. Citizenship and
Immigration Services interact with millions of individuals every year and
34 CBP may also encounter such individuals in the course of processing an application and/or conducting an interview
of an applicant for a trusted traveler program NEXUS, Free and Secure Trade (FAST), Global Entry, SENTRI,
etc.).
OR OFFICIAL USE SECURITY INFORMATION
Page 60
OR OFFICIAL USE SECURITY INFORMATION
commercial ?ight manifests, as well as, commercial vessel manifest for travel to and
from the United States. With the exception of passenger information required by law to
be transmitted to DHS prior to a passenger?s arrival, most information is generally
collected by CBP when the person is interviewed or apprehended. The National
Targeting Center Passenger and NTC-Cargo (NTC-C) are CBP entities
responsible for communicating with the TSC regarding ENCOUNTERS with KNOWN or
SUSPECTED to include providing relevant ENCOUNTER information.?
and NTC-C also provide a copy of the examination results to the TSOU for
dissemination to the appropriate investigating Agencies.
5.4.2 Transportation Security Administration. TSA generally encounters KNOWN or
TERRORISTS through screening commercial aircraft passengers against
subsets of the and during the application process for a credential or bene?t in the
transportation or critical infrastructure environment Transportation Worker
Identi?cation Credential When an airline encounters subjects who are
possible matches to the NO 1y or Selectee List, the air carriers are required to supply the
passenger?s name and one piece of identifying data (in the form of a govemment-issued
photo identi?cation that contains a date of birth) to the Of?ce of Intelligence and
Analysis TSA submits that information, along with information regarding
the carrier, ?ight number, time of departure, and destination to the TSC.
5.4.2.1 Absent an arrest warrant, or unless probable cause arises during the
ENCOUNTER, SCREENERS are reminded that placement on the No Fly or Selectee
List is not a legal basis to detain a KNOWN or SUSPECTED TERRORIST. To the
extent legal authority exists to question a KNOWN or SUSPECTED TERRORIST,
encounters with No Fly subjects at the airport may provide an additional
opportunity to lawfully obtain ENCOUNTER PACKAGE information. For No Fly
subjects who have made a domestic reservation, DHS will notify TSC in advance
as well as when the No Fly subject presents at the airport ticket counter. TSC will
then notify the TSOU who will notify both the l?Bl case agent and the airport
liaison agent to coordinate the appropriate operational response.
5.4.2.2 For KNOWN or SUSPECTED TERRORIST ENCOUNTERS as a result of an
individual applying for a TSA bene?t or credential, ENCOUNTER PACKAGE
information can include any supporting documents or information collected as a
part of the application process. The ENCOUNTER, and any corresponding
information, is communicated to the TSC and other Government Agencies, as
appropriate through TSA
5.4.3 United States Citizenship and Immigration Services. US. Citizenship and
Immigration Services interact with millions of individuals every year and
34 CBP may also encounter such individuals in the course of processing an application and/or conducting an interview
of an applicant for a trusted traveler program NEXUS, Free and Secure Trade (FAST), Global Entry, SENTRI,
etc.).
OR OFFICIAL USE SECURITY INFORMATION
Page 60

OR OFFICIAL USE SECURITY INFORMATION
ENCOUNTERS KNOWN or SUSPECTED TERRORISTS who ?le petitions or applications for
immigration bene?ts internationally and domestically.35 The USCIS of?cial contacts
the TSC to report an ENCOUNTER with a KNOWN or SUSPECTED TERRORIST. Before
making a decision on the immigration application or bene?t, USCIS contacts the
to obtain additional information that may help determine
whether the individual is eligible or ineligible to receive the immigration bene?t. In
such cases, USCIS seeks further information from the record owner or case agent and
may seek de-classi?cation of information relating to the application. In addition,
contacts the to discuss whether the USCIS decision to grant or
deny the application or bene?t would interrupt or negatively affect any ongoing
investigation.
5.4.3.1 USCIS maintains a presence at law enforcement and intelligence Agency
entities to further information sharing regarding KNOWN or SUSPECTED
TERRORISTS. USCIS maintains information, including the subject?s Alien File (A-
ilc) and other records. The type of information that may be contained in USCIS
?les, including the A-File, could be biometric data (?ngerprints and photographs);
identity documents; information relating to the application; addresses, as well as
family and work history information; immigration bene?t application information;
and records of previous ENCOUNTERS that DHS has had with the subject. Other
SCREENERS as well as other appropriate organizations who are considering
nominating a potential KNOWN or SUSPECTED TERRORIST or who have ENCOUNTERS
with a person who is a POSITIVE MATCH to a KNOWN or SUSPECTED are
advised that they can request, on a case?by-case basis, a copy of the KNOWN or
SUSPECTED A-File from USCIS if the KNOWN or SUSPECTED
TERRORIST has applied for immigration or citizenship bene?ts.86
5.4.4 U.S. Immigration and Customs Enforcement. lmmigrations and Customs
Enforcement (ICE) is the principal investigative arm of DHS. ICE is also the federal
law enforcement organization responsible for immigration and customs-related
investigations and detention within the interior and at the borders of the United States.
ICE frequently ENCOUNTERS potential KNOWN or SUSPECTED TERRORISTS during
enforcement activities under its purview. Such ENCOUNTERS are documented within
Enforcement and Removal Operations (ERO) via the Known Suspected Terrorist
Encounter Protocol and reported to the TSC and lCE?s Homeland Security
Investigations ICE Special Agents frequently encounter KNOWN or
SUSPECTED TERRORISTS internationally, domestically, at U.S. POEs, and when KNOWN or
SUSPECTED TERRORISTS are the subjects of an ICE investigation. These ENCOUNTERS are
as For example, a U.S. PERSON who is a KNOWN or SUSPECTED TERRORIST may ?le a petition for a foreign national or a
U.S. PERSON who is not a KNOWN or SUSPECTED TERRORJST may ?le a petition for a foreign national who is a KNOWN or
SUSPECTED TERRORIST.
8" Because USCIS is the custodian of information acquired through the immigration process relating to an individual
and because the A?File is not routinely attached to the TSDB or TIDE, a speci?c request to USCIS is necessary in order
to obtain information from the A-File.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 6]
OR OFFICIAL USE SECURITY INFORMATION
ENCOUNTERS KNOWN or SUSPECTED TERRORISTS who ?le petitions or applications for
immigration bene?ts internationally and domestically.35 The USCIS of?cial contacts
the TSC to report an ENCOUNTER with a KNOWN or SUSPECTED TERRORIST. Before
making a decision on the immigration application or bene?t, USCIS contacts the
to obtain additional information that may help determine
whether the individual is eligible or ineligible to receive the immigration bene?t. In
such cases, USCIS seeks further information from the record owner or case agent and
may seek de-classi?cation of information relating to the application. In addition,
contacts the to discuss whether the USCIS decision to grant or
deny the application or bene?t would interrupt or negatively affect any ongoing
investigation.
5.4.3.1 USCIS maintains a presence at law enforcement and intelligence Agency
entities to further information sharing regarding KNOWN or SUSPECTED
TERRORISTS. USCIS maintains information, including the subject?s Alien File (A-
ilc) and other records. The type of information that may be contained in USCIS
?les, including the A-File, could be biometric data (?ngerprints and photographs);
identity documents; information relating to the application; addresses, as well as
family and work history information; immigration bene?t application information;
and records of previous ENCOUNTERS that DHS has had with the subject. Other
SCREENERS as well as other appropriate organizations who are considering
nominating a potential KNOWN or SUSPECTED TERRORIST or who have ENCOUNTERS
with a person who is a POSITIVE MATCH to a KNOWN or SUSPECTED are
advised that they can request, on a case?by-case basis, a copy of the KNOWN or
SUSPECTED A-File from USCIS if the KNOWN or SUSPECTED
TERRORIST has applied for immigration or citizenship bene?ts.86
5.4.4 U.S. Immigration and Customs Enforcement. lmmigrations and Customs
Enforcement (ICE) is the principal investigative arm of DHS. ICE is also the federal
law enforcement organization responsible for immigration and customs-related
investigations and detention within the interior and at the borders of the United States.
ICE frequently ENCOUNTERS potential KNOWN or SUSPECTED TERRORISTS during
enforcement activities under its purview. Such ENCOUNTERS are documented within
Enforcement and Removal Operations (ERO) via the Known Suspected Terrorist
Encounter Protocol and reported to the TSC and lCE?s Homeland Security
Investigations ICE Special Agents frequently encounter KNOWN or
SUSPECTED TERRORISTS internationally, domestically, at U.S. POEs, and when KNOWN or
SUSPECTED TERRORISTS are the subjects of an ICE investigation. These ENCOUNTERS are
as For example, a U.S. PERSON who is a KNOWN or SUSPECTED TERRORIST may ?le a petition for a foreign national or a
U.S. PERSON who is not a KNOWN or SUSPECTED TERRORJST may ?le a petition for a foreign national who is a KNOWN or
SUSPECTED TERRORIST.
8" Because USCIS is the custodian of information acquired through the immigration process relating to an individual
and because the A?File is not routinely attached to the TSDB or TIDE, a speci?c request to USCIS is necessary in order
to obtain information from the A-File.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 6]

OFFICIAL USE SECURITY INFORMATION
documented by HSI Special Agents in Reports of Investigation (ROI). All ROls
documenting ENCOUNTERS/interviews with a KNOWN or SUSPECTED are
shared with the IC.
5.4.4.1 In addition, under section 428 of the Homeland Security Act, the Secretary of
Homeland Security has the authority to refuse visas in accordance with the law and
to assign employees of DHS to diplomatic and consular posts to review visa
applications and conduct investigations.87 ICE, through the Visa Security
Program, exercises this authority. Reviews of visa applications and interviews
with applicants can result in the encounter of KNOWN or SUSPECTED
facilitators, and associates as well as reveal previously unknown information
relating to KNOWN or SUSPECTED HSI personnel assigned to the Visa
Security Program, and to US. Embassies and Consulates abroad, work closely
with their DOS counterparts to identify KNOWN or SUSPECTED TERRORISTS and
report findings through established processes. Finally, ICE may encounter KNOWN
or SUSPECTED TERRORISTS awaiting immigration hearings who are housed in
service processing/detention centers. These detention facilities can document
interactions with the aliens while they are detained in the facility, as well as
document materials found on the individual at the time of processing. For all
immigration and enforcement activities, will communicate with the TSC
regarding encounters with watchlisted individuals, and will submit relevant
ENCOUNTER information to the TSC.
5.4.5 United States Coast Guard. The .8. Coast Guard?s Coastwatch branch screens crew
and passenger information on vessel manifests, which are required by regulation to be
transmitted to the National Vessel Movement Center (NVMC) prior to a vessel?s arrival
in a US. port. Coastwatch communicates with the NTC-P and TSC regarding any
KNOWN or SUSPECTED TERRORIST ENCOUNTERS during this process. The Coast Guard
physically encounters few KNOWN or and such
could occur from random and regular inspections of vessels and port facilities, ship
boardings, investigations, or Coast Guard licensing activities. The type of information
available for collection is dependent on the type of ENCOUNTER. The ENCOUNTER, and
any corresponding information, is communicated to the TSC through Coast Guard
Office of Intelligence and Criminal Investigations. Based on the encountering situation,
intelligence reporting will be written to provide situational awareness to the IC.
5.4.6 United States Secret Service. Although United States Secret Service does not
encounter many KNOWN or SUSPECTED TERRORISTS, such usually involve
KNOWN or SUSPECTFD with a domestic nexus to TERRORISM. Such
encounters can be the result of investigations or for event screening National
Security Special Events, political events, large scale sporting events). These
?7 Consistent with section 428 of the Homeland Security Act and the Memorandum of Understanding between the
Secretaries of State and Homeland Security Concerning Implementation of Section 428 of the Homeland Security Act of
2002, the Secretary of Homeland Security may direct a consular Of?cer to refuse or revoke a visa.
UN OR OFFICIAL USE ON SECURITY INFORMATION
Page 62
OFFICIAL USE SECURITY INFORMATION
documented by HSI Special Agents in Reports of Investigation (ROI). All ROls
documenting ENCOUNTERS/interviews with a KNOWN or SUSPECTED are
shared with the IC.
5.4.4.1 In addition, under section 428 of the Homeland Security Act, the Secretary of
Homeland Security has the authority to refuse visas in accordance with the law and
to assign employees of DHS to diplomatic and consular posts to review visa
applications and conduct investigations.87 ICE, through the Visa Security
Program, exercises this authority. Reviews of visa applications and interviews
with applicants can result in the encounter of KNOWN or SUSPECTED
facilitators, and associates as well as reveal previously unknown information
relating to KNOWN or SUSPECTED HSI personnel assigned to the Visa
Security Program, and to US. Embassies and Consulates abroad, work closely
with their DOS counterparts to identify KNOWN or SUSPECTED TERRORISTS and
report findings through established processes. Finally, ICE may encounter KNOWN
or SUSPECTED TERRORISTS awaiting immigration hearings who are housed in
service processing/detention centers. These detention facilities can document
interactions with the aliens while they are detained in the facility, as well as
document materials found on the individual at the time of processing. For all
immigration and enforcement activities, will communicate with the TSC
regarding encounters with watchlisted individuals, and will submit relevant
ENCOUNTER information to the TSC.
5.4.5 United States Coast Guard. The .8. Coast Guard?s Coastwatch branch screens crew
and passenger information on vessel manifests, which are required by regulation to be
transmitted to the National Vessel Movement Center (NVMC) prior to a vessel?s arrival
in a US. port. Coastwatch communicates with the NTC-P and TSC regarding any
KNOWN or SUSPECTED TERRORIST ENCOUNTERS during this process. The Coast Guard
physically encounters few KNOWN or and such
could occur from random and regular inspections of vessels and port facilities, ship
boardings, investigations, or Coast Guard licensing activities. The type of information
available for collection is dependent on the type of ENCOUNTER. The ENCOUNTER, and
any corresponding information, is communicated to the TSC through Coast Guard
Office of Intelligence and Criminal Investigations. Based on the encountering situation,
intelligence reporting will be written to provide situational awareness to the IC.
5.4.6 United States Secret Service. Although United States Secret Service does not
encounter many KNOWN or SUSPECTED TERRORISTS, such usually involve
KNOWN or SUSPECTFD with a domestic nexus to TERRORISM. Such
encounters can be the result of investigations or for event screening National
Security Special Events, political events, large scale sporting events). These
?7 Consistent with section 428 of the Homeland Security Act and the Memorandum of Understanding between the
Secretaries of State and Homeland Security Concerning Implementation of Section 428 of the Homeland Security Act of
2002, the Secretary of Homeland Security may direct a consular Of?cer to refuse or revoke a visa.
UN OR OFFICIAL USE ON SECURITY INFORMATION
Page 62

UN OR OFFICIAL USE SECURITY INFORMATION
5.5
5.6
5.7
ENCOUNTERS will be coordinated with the FBI, who will handle them as they do all other
FBI KNOWN or SUSPECTED
5.4.7 Department of Homeland Security Intelligence Analysis. DHS l&A provides end
products and analytical reports, which are generally available to the NCTC and the
broader counterterrorism analytic community, including fusion centers. DHS l&A
works closely with DHS components to ensure non-traditional streams of information
are fused with traditional sources of information from other members of the to give a
complete picture of potential threats to the nation. DHS l&A ?connects the dots? for
intelligence reporting and ENCOUNTERS of the DHS components, and as such, has
limited opportunity for with KNOWN or SUSPECTED TERRORISTS.
Department of State ENCOUNTERS. For DOS ENCOUNTERS with a person who is a POSITIVE
MATCH to a KNOWN or SUSPECTED TERRORIST, the DOS unit at the TSC will do the following:
Visa Applications. will upload the electronic visa application from the CCD
to the individual?s EMA record. will coordinate with the overseas posts to
scan in CCD all other available DOS documents associated with the individual. DOS
information about whether a visa is issued is currently available in individual case
records in the DOS is currently investigating upgrades to the report
function that will make the visa decision data more easily accessible to TSC and other
users.
5.5.2 Visa Revocations. SC will upload the electronic visa application from the CCD
to the individual?s EMA record.
5.5.3 Passports. After encounters with KNOWN or SUSPECTED TERRORISTS possessing
passports issued by the United States, the TSOC will upload the Passport Information
Electronic Records System application forms from the CCD to the individual?s
EMA record. SC will coordinate with the overseas posts to scan in CCD all other
available DOS documents associated with the individual.
United States Agency for International DeveIOpment ENCOUNTERS. United States Agency
for lnternational Development works in agriculture, democracy and governance,
economic growth, the environment, education, health, global partnerships, and humanitarian
assistance in more than 100 countries. When USAID receives an application seeking financial
assistance, prior to granting, these applications are subject to vetting by USAID intelligence
at the TSC. If SC ?nds that an application relates to a person who is a
POSITIVE MATCH to a KNOWN or TERRORIST in the TSDB, will provide
any TERRORISM INFORMATION concerning the application and follow standard TSC procedures
for processing TERRORISM INFORMATION, to include logging the ENCOUNTER in EMA.
Foreign Partner ENCOUNTERS. A?er each ENCOUNTER by a foreign partner, will
ask the respective country for the subject?s photo, additional biographie data and any
OR OFFICIAL USE SECURITY INFORMATION
Page I 63
UN OR OFFICIAL USE SECURITY INFORMATION
5.5
5.6
5.7
ENCOUNTERS will be coordinated with the FBI, who will handle them as they do all other
FBI KNOWN or SUSPECTED
5.4.7 Department of Homeland Security Intelligence Analysis. DHS l&A provides end
products and analytical reports, which are generally available to the NCTC and the
broader counterterrorism analytic community, including fusion centers. DHS l&A
works closely with DHS components to ensure non-traditional streams of information
are fused with traditional sources of information from other members of the to give a
complete picture of potential threats to the nation. DHS l&A ?connects the dots? for
intelligence reporting and ENCOUNTERS of the DHS components, and as such, has
limited opportunity for with KNOWN or SUSPECTED TERRORISTS.
Department of State ENCOUNTERS. For DOS ENCOUNTERS with a person who is a POSITIVE
MATCH to a KNOWN or SUSPECTED TERRORIST, the DOS unit at the TSC will do the following:
Visa Applications. will upload the electronic visa application from the CCD
to the individual?s EMA record. will coordinate with the overseas posts to
scan in CCD all other available DOS documents associated with the individual. DOS
information about whether a visa is issued is currently available in individual case
records in the DOS is currently investigating upgrades to the report
function that will make the visa decision data more easily accessible to TSC and other
users.
5.5.2 Visa Revocations. SC will upload the electronic visa application from the CCD
to the individual?s EMA record.
5.5.3 Passports. After encounters with KNOWN or SUSPECTED TERRORISTS possessing
passports issued by the United States, the TSOC will upload the Passport Information
Electronic Records System application forms from the CCD to the individual?s
EMA record. SC will coordinate with the overseas posts to scan in CCD all other
available DOS documents associated with the individual.
United States Agency for International DeveIOpment ENCOUNTERS. United States Agency
for lnternational Development works in agriculture, democracy and governance,
economic growth, the environment, education, health, global partnerships, and humanitarian
assistance in more than 100 countries. When USAID receives an application seeking financial
assistance, prior to granting, these applications are subject to vetting by USAID intelligence
at the TSC. If SC ?nds that an application relates to a person who is a
POSITIVE MATCH to a KNOWN or TERRORIST in the TSDB, will provide
any TERRORISM INFORMATION concerning the application and follow standard TSC procedures
for processing TERRORISM INFORMATION, to include logging the ENCOUNTER in EMA.
Foreign Partner ENCOUNTERS. A?er each ENCOUNTER by a foreign partner, will
ask the respective country for the subject?s photo, additional biographie data and any
OR OFFICIAL USE SECURITY INFORMATION
Page I 63

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
5.8
5.9
TERRORISM INFORMATION on the ENCOUNTER Information List gathered during the
ENCOUNTER. Provision of any material collected by the foreign partner depends on the
arrangement with, and legal authorities of, the particular foreign partner involved. Therefore,
gathering and sharing this TERRORISM INFORMATION will be done on a case-by-case, country-
by-country basis.
Federal Bureau of Investigation/Law Enforcement ENCOUNTERS. These ENCOUNTERS can
be subdivided into three categories:
5.8.1 Name-Based Queries. Name-based transaction queries by law enforcement personnel
traf?c stops) made to the National Crime Information Center at the Criminal
Justice Information Services (CJIS) Division that match a name in the KSTF (a sub-?le
of NCIC) are deemed to be POTENTIAL MATCHES. They are routed electronically to TSC
for con?rmation and subsequent processing as an ENCOUNTER.
5.8.2 Fingerprint-Based Queries. ingerprint-based queries submitted for criminal
identi?cation purposes an arrest/booking) or for civil identi?cation purposes
an employment background check) are made to the Integrated Automatic Fingerprint
Identi?cation System For POSITIVE MATCHES to records ?agged as KNOWN or
SUSPECTED records, the CJIS Division?s Special Identities Unit noti?es the
TSC and the FBI case agent (or the Agency that identi?ed the subject as a possible
TERRORIST). In similar fashion, CJIS Division?s Global Initiatives Unit coordinates
positive ?ngerprint hits from its foreign submissions with the Legal Attache. It should
be noted that IAFIS and NCIC are separate systems that are not fully at the
present time.
5.8.3 National Instant Criminal Background Check System. All background checks
resulting from attempts to buy ?rearms or to obtain explosive permits submitted to the
National Instant Criminal Background Check System (NICS) at CJIS are run against the
KSTF. The TSC is immediately noti?ed of all KSTF ?hits.? NICS consults with TSC
to con?rm the POSITIVE MATCHES and the FBI case agent to determine whether there is
available information about the prospective purchaser to disqualify him or her from
possessing a ?rearm or explosive as a matter of law. Regardless of whether the
purchase is denied or permitted to proceed, all available information is obtained and
provided to the TSC and, in turn, CTD, as TERRORISM INFORMATION and processed as an
ENCOUNTER.
Department of Defense ENCOUNTERS. The Department of Defense (DOD) has force
protection, Operational capture/apprehend, and intelligence responsibilities and on occasion
encounters KNOWN or SUSPECTED TERRORISTS. To the extent DOD knowingly encounters a
KNOWN or SUSPECTED TERRORIST, will report the ENCOUNTER in intelligence channels or
to the FBI in cases described in the MOU between the FBI and DOD Governing Information
Sharing, Operational Coordination and Investigative Responsibilities signed August 2, 201
where the FBI is the lead. In cases where the FBI is not the lead for the ENCOUNTER, the
OR OFFICIAL USE ON SECURITY INFORMATION
Page 64
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
5.8
5.9
TERRORISM INFORMATION on the ENCOUNTER Information List gathered during the
ENCOUNTER. Provision of any material collected by the foreign partner depends on the
arrangement with, and legal authorities of, the particular foreign partner involved. Therefore,
gathering and sharing this TERRORISM INFORMATION will be done on a case-by-case, country-
by-country basis.
Federal Bureau of Investigation/Law Enforcement ENCOUNTERS. These ENCOUNTERS can
be subdivided into three categories:
5.8.1 Name-Based Queries. Name-based transaction queries by law enforcement personnel
traf?c stops) made to the National Crime Information Center at the Criminal
Justice Information Services (CJIS) Division that match a name in the KSTF (a sub-?le
of NCIC) are deemed to be POTENTIAL MATCHES. They are routed electronically to TSC
for con?rmation and subsequent processing as an ENCOUNTER.
5.8.2 Fingerprint-Based Queries. ingerprint-based queries submitted for criminal
identi?cation purposes an arrest/booking) or for civil identi?cation purposes
an employment background check) are made to the Integrated Automatic Fingerprint
Identi?cation System For POSITIVE MATCHES to records ?agged as KNOWN or
SUSPECTED records, the CJIS Division?s Special Identities Unit noti?es the
TSC and the FBI case agent (or the Agency that identi?ed the subject as a possible
TERRORIST). In similar fashion, CJIS Division?s Global Initiatives Unit coordinates
positive ?ngerprint hits from its foreign submissions with the Legal Attache. It should
be noted that IAFIS and NCIC are separate systems that are not fully at the
present time.
5.8.3 National Instant Criminal Background Check System. All background checks
resulting from attempts to buy ?rearms or to obtain explosive permits submitted to the
National Instant Criminal Background Check System (NICS) at CJIS are run against the
KSTF. The TSC is immediately noti?ed of all KSTF ?hits.? NICS consults with TSC
to con?rm the POSITIVE MATCHES and the FBI case agent to determine whether there is
available information about the prospective purchaser to disqualify him or her from
possessing a ?rearm or explosive as a matter of law. Regardless of whether the
purchase is denied or permitted to proceed, all available information is obtained and
provided to the TSC and, in turn, CTD, as TERRORISM INFORMATION and processed as an
ENCOUNTER.
Department of Defense ENCOUNTERS. The Department of Defense (DOD) has force
protection, Operational capture/apprehend, and intelligence responsibilities and on occasion
encounters KNOWN or SUSPECTED TERRORISTS. To the extent DOD knowingly encounters a
KNOWN or SUSPECTED TERRORIST, will report the ENCOUNTER in intelligence channels or
to the FBI in cases described in the MOU between the FBI and DOD Governing Information
Sharing, Operational Coordination and Investigative Responsibilities signed August 2, 201
where the FBI is the lead. In cases where the FBI is not the lead for the ENCOUNTER, the
OR OFFICIAL USE ON SECURITY INFORMATION
Page 64

OR OFFICIAL USE SECURITY INFORMATION
Defense Intelligence Agency will be responsible for providing extracted information
from the ENCOUNTER to NCTC via standard national watchlisting procedures,
which utilize community accepted standards. DOD law enforcement ENCOUNTERS will be
handled in accordance with established law enforcement standards that provide noti?cation to
the Bl.
5.10 All other Departments or Agencies. Any other Department or Agency that has TERRORISM
INFORMATION from an ENCOUNTER will contact the SOC at 866- to arrange a
mutually acceptable transmission method.
Ill. CATEGORIES OF TERRORISM INFORMATION FROM ENCOUNTERS
WITH POSITIVELY IDENTIFIED KNOWN OR SUSPECTED
TERRORISTS OF POTENTIAL INTEREST
5.l ENCOUNTER Information List. The following ENCOUNTER Information List identi?es
categories of TERRORISM from ENCOUNTERS with positively identi?ed KNOWN
or TERRORISTS that are of potential interest to other counterterrorism
or the watchlisting community. The items identi?ed are not intended to be an
exclusive or exhaustive list of what constitutes INFORMATION.
5.1 1.1 ENCOUNTER information identi?ed for collection in Addendum to the TSC MOU88
when there is a POSITIVE to a KNOWN or SUSPECTEI)
Photographs
Fingerprints
Pocket litter
Written data
Reports of TERRORISM INFORMATION
meww?
1.2 Additional items of potential interest when lawfully collected during an
with a KNOWN or SUSPECTED TERRORIST:
l. Contemporaneous reports including the impressions or observations recorded by an
of?cial involved in the ENCOUNTER:
a) Reason/circumstances of ENCOUNTER
b) ICE Intel Reports
c) FBI Reports of Investigations
d) CBP Incident Reports
e) CBP Secondary Iixam Report
l) USCIS applications or petitions
g) Non-Immigrant Visa (NIV) Applications (including CCD notes)
See Appendix 3, TSC MOU.
OFFICIAL USE SECURITY INFORMATION
Page 65
OR OFFICIAL USE SECURITY INFORMATION
Defense Intelligence Agency will be responsible for providing extracted information
from the ENCOUNTER to NCTC via standard national watchlisting procedures,
which utilize community accepted standards. DOD law enforcement ENCOUNTERS will be
handled in accordance with established law enforcement standards that provide noti?cation to
the Bl.
5.10 All other Departments or Agencies. Any other Department or Agency that has TERRORISM
INFORMATION from an ENCOUNTER will contact the SOC at 866- to arrange a
mutually acceptable transmission method.
Ill. CATEGORIES OF TERRORISM INFORMATION FROM ENCOUNTERS
WITH POSITIVELY IDENTIFIED KNOWN OR SUSPECTED
TERRORISTS OF POTENTIAL INTEREST
5.l ENCOUNTER Information List. The following ENCOUNTER Information List identi?es
categories of TERRORISM from ENCOUNTERS with positively identi?ed KNOWN
or TERRORISTS that are of potential interest to other counterterrorism
or the watchlisting community. The items identi?ed are not intended to be an
exclusive or exhaustive list of what constitutes INFORMATION.
5.1 1.1 ENCOUNTER information identi?ed for collection in Addendum to the TSC MOU88
when there is a POSITIVE to a KNOWN or SUSPECTEI)
Photographs
Fingerprints
Pocket litter
Written data
Reports of TERRORISM INFORMATION
meww?
1.2 Additional items of potential interest when lawfully collected during an
with a KNOWN or SUSPECTED TERRORIST:
l. Contemporaneous reports including the impressions or observations recorded by an
of?cial involved in the ENCOUNTER:
a) Reason/circumstances of ENCOUNTER
b) ICE Intel Reports
c) FBI Reports of Investigations
d) CBP Incident Reports
e) CBP Secondary Iixam Report
l) USCIS applications or petitions
g) Non-Immigrant Visa (NIV) Applications (including CCD notes)
See Appendix 3, TSC MOU.
OFFICIAL USE SECURITY INFORMATION
Page 65

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
h) State, Local, 'I?ribal, Territorial Police Report
i) TSA OIA No Fly and Selectee Reports
j) TSA 01A ENCOUNTER Reports (Vetting Match Reports) on transportation workers
and other populations vetted by TSA against the TSDB
k) Spot Reports
l) Suspicious Activity Reports
m) Impounded vehicle inventory
n) Any inventory record
0) Any pictures, video or recording of or from the actual ENCOUNTER
p) Biometric or biographic identi?ers of traveling associates
2. Surveillance?related documents:
a) Maps
b) Pictures
c) Visitor or site information
d) Plans or diagrams g, architectural drawings, blueprints, schemas)
3. Context regarding areas of potential interest or possible targets of KNOWN or
interest:
a) Information regarding any high pro?le events taking place in geographic area of
ENCOUNTER
b) Any critical infrastructure sites near the geographic area of ENCOUNTER
0) Unique characteristics or facts about your domain/area of responsibility/geographic
area of ENCOUNTER
d) Event tickets sporting events, concerts, designated National Security Special
events)
e) Building access passes, electronic cards, fobs, keys
4. Mode of transportation used by the person who is a POSITIVE MATCH to a KNOWN or
SUSPECTEI) along with identifying information:
a) Vehicle information Vehicle registration, Vehicle identification number
(VIN), 'I?itle, Driver?s license, Car insurance cards or information)
b) Pilot medical license
c) Pilot certificates
d) Aircraft registration
e) Marine registration
0 El Pass or electronic vehicle payment system
5. Travel-related information:
a) Passport exit/entry stamps indicating places of travel
b) Any visa application or denial information from other countries
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 66
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
h) State, Local, 'I?ribal, Territorial Police Report
i) TSA OIA No Fly and Selectee Reports
j) TSA 01A ENCOUNTER Reports (Vetting Match Reports) on transportation workers
and other populations vetted by TSA against the TSDB
k) Spot Reports
l) Suspicious Activity Reports
m) Impounded vehicle inventory
n) Any inventory record
0) Any pictures, video or recording of or from the actual ENCOUNTER
p) Biometric or biographic identi?ers of traveling associates
2. Surveillance?related documents:
a) Maps
b) Pictures
c) Visitor or site information
d) Plans or diagrams g, architectural drawings, blueprints, schemas)
3. Context regarding areas of potential interest or possible targets of KNOWN or
interest:
a) Information regarding any high pro?le events taking place in geographic area of
ENCOUNTER
b) Any critical infrastructure sites near the geographic area of ENCOUNTER
0) Unique characteristics or facts about your domain/area of responsibility/geographic
area of ENCOUNTER
d) Event tickets sporting events, concerts, designated National Security Special
events)
e) Building access passes, electronic cards, fobs, keys
4. Mode of transportation used by the person who is a POSITIVE MATCH to a KNOWN or
SUSPECTEI) along with identifying information:
a) Vehicle information Vehicle registration, Vehicle identification number
(VIN), 'I?itle, Driver?s license, Car insurance cards or information)
b) Pilot medical license
c) Pilot certificates
d) Aircraft registration
e) Marine registration
0 El Pass or electronic vehicle payment system
5. Travel-related information:
a) Passport exit/entry stamps indicating places of travel
b) Any visa application or denial information from other countries
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 66

OR OFFICIAL USE SECURITY INFORMATION
'0
Travel itineraries
Tickets plane, train, boat)
Hotels reservation con?rmation, receipts)
Rental cars reservation confirmation, agreement, receipts)
Reservation method via travel agency or travel website)
PNR data
Travel manifests
Luggage or baggage tags airport check-in tags, identi?cation tags,
lost bag bar code tags)
Claim checks
Storage locker keys
m) Shipping documents and receipts
n)
o)
p)
Automated Identi?cation System (AIS) information for maritime shipping
Foreign airport security check stickers or labels
Conference/seminar materials invitation, brochure, schedule)
6. Information about gold and jewelry worn by person at time of ENCOUNTER
receipts)
7. General items informationBusiness cards
Phone numbers
Address books
Email addresses
Any cards with an electronic strip on it (hotel cards, grocery cards, gift cards,
frequent ?yer cards)
Pre-paid phone cards
Insurance cards
Medical/Health insurance information
Prescription information doctor, pharmacy information)
Sales receipts
Any additional biographic or biometric identi?ers to enhance
identity matching of associates or family members with a person who is a POSITIVE
MATCH to a KNOWN or SUSPECTED TERRORIST (as well as associates or family
members referenced in interviews or documents carried by a person who is a
POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST)
Copies of identi?cation documents obtained during the ENCOUNTER with a person
who IS a POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST passports,
Seaman?s Papers, Airman Certi?cates, driver?s licenses, state identi?cation cards,
and similar government identi?cation documents)
Any computer, uniform resource Iocator (URL), or Internet protocol (IP) address
information
Calendars/schedulers
OFFICIAL USE SECURITY INFORMATION
Page 67
OR OFFICIAL USE SECURITY INFORMATION
'0
Travel itineraries
Tickets plane, train, boat)
Hotels reservation con?rmation, receipts)
Rental cars reservation confirmation, agreement, receipts)
Reservation method via travel agency or travel website)
PNR data
Travel manifests
Luggage or baggage tags airport check-in tags, identi?cation tags,
lost bag bar code tags)
Claim checks
Storage locker keys
m) Shipping documents and receipts
n)
o)
p)
Automated Identi?cation System (AIS) information for maritime shipping
Foreign airport security check stickers or labels
Conference/seminar materials invitation, brochure, schedule)
6. Information about gold and jewelry worn by person at time of ENCOUNTER
receipts)
7. General items informationBusiness cards
Phone numbers
Address books
Email addresses
Any cards with an electronic strip on it (hotel cards, grocery cards, gift cards,
frequent ?yer cards)
Pre-paid phone cards
Insurance cards
Medical/Health insurance information
Prescription information doctor, pharmacy information)
Sales receipts
Any additional biographic or biometric identi?ers to enhance
identity matching of associates or family members with a person who is a POSITIVE
MATCH to a KNOWN or SUSPECTED TERRORIST (as well as associates or family
members referenced in interviews or documents carried by a person who is a
POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST)
Copies of identi?cation documents obtained during the ENCOUNTER with a person
who IS a POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST passports,
Seaman?s Papers, Airman Certi?cates, driver?s licenses, state identi?cation cards,
and similar government identi?cation documents)
Any computer, uniform resource Iocator (URL), or Internet protocol (IP) address
information
Calendars/schedulers
OFFICIAL USE SECURITY INFORMATION
Page 67

UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
8. Licenses, permits, membership cards, and application information:
a) Membership cards (including library cards)
b) Gun show applications, ?rearms license, concealed weapons permit, shooting club
memberships
c) HAZMAT license
d) Explosives permit
9. Tools or equipment information:
a) Scuba gear
b) Multiple cell phones
0) Binoculars
d) Peroxide
e) Ammunition
0 Camping fuel tabs
g) Any dual use material that could be used for
10. Financial information:
a) Check book/individual or loose checks, including cashier?s checks
b) Bank account numbers
c) Credit cards, especially those issued by U.S. banks and carried by non- U.S.
PERSONS
d) Tax records
c) Business ?nancial records
f) Bank statements
g) Credit card or billing statements
h) Utility bills
i) Anything with an account number
j) Wire transfer information, including receipts from Money Service Businesses
k) Denominations of money being carried what country(ics) curreney(ies) are
they carrying), including, if possible, the serial numbers of currency carried
1) Automated teller machine (ATM) receipts
m) Ledgers
1. Electronic media/devices observed or copied:
a) Cell phone list and speed dial numbers
b) Laptop images
c) GPS
d) Thumb drives
e) Disks
f) iPod or MP3
g) PDAs Palm Pilots, 'l?rios)
h) Kindle or iPad (electronic books)
i) Cameras
j) Video and/or voice recorders
OFFICIAL USE SECURITY INFORMATION
Page 68
UN CLASSIF OR OFFICIAL USE SECURITY INFORMATION
8. Licenses, permits, membership cards, and application information:
a) Membership cards (including library cards)
b) Gun show applications, ?rearms license, concealed weapons permit, shooting club
memberships
c) HAZMAT license
d) Explosives permit
9. Tools or equipment information:
a) Scuba gear
b) Multiple cell phones
0) Binoculars
d) Peroxide
e) Ammunition
0 Camping fuel tabs
g) Any dual use material that could be used for
10. Financial information:
a) Check book/individual or loose checks, including cashier?s checks
b) Bank account numbers
c) Credit cards, especially those issued by U.S. banks and carried by non- U.S.
PERSONS
d) Tax records
c) Business ?nancial records
f) Bank statements
g) Credit card or billing statements
h) Utility bills
i) Anything with an account number
j) Wire transfer information, including receipts from Money Service Businesses
k) Denominations of money being carried what country(ics) curreney(ies) are
they carrying), including, if possible, the serial numbers of currency carried
1) Automated teller machine (ATM) receipts
m) Ledgers
1. Electronic media/devices observed or copied:
a) Cell phone list and speed dial numbers
b) Laptop images
c) GPS
d) Thumb drives
e) Disks
f) iPod or MP3
g) PDAs Palm Pilots, 'l?rios)
h) Kindle or iPad (electronic books)
i) Cameras
j) Video and/or voice recorders
OFFICIAL USE SECURITY INFORMATION
Page 68

OFFICIAL USE SECURITY INFORMATION
'Pagers
Any electronic storage media
Employment information:
Pay stubs
Employment applications
Want ads
Employer correspondence
6) Access cards, badges
l315.
Professional papers/Academic information:
Resumes
Academic transcripts
Legal document information:
Birth certi?cates
Immigration and naturalization documents
Marriage licenses
Divorce decrees
Adoption papers
Living Wills
Last Will and Testament
Parking tickets
Speeding tickets
Property records (deeds)
Summons
Criminal documents or civil lawsuit information
Miscellaneous item information:
Long term storage facilities access keys, codes)
Social networking accounts Facebook, Twitter, MySpace, Linkedln, ICQ)
Titles of books, brochures being carried and their condition new,
dog-cared, annotated, unopened, professional journals)
Letters, envelopes
Letters of Introduction
Animal information vet or chip information)
IV. ENCOUNTER MANAGEMENT ACTIONS
5.l2 Handling of ENCOUNTER PACKAGES. This section outlines the processes for handling and
sharing ENCOUNTER PACKAGES by SCREENERS, the TSC and NCTC.
5. l3 Enforcement ENCOUNTERS. TSOU coordinates the US. Govemment?s reSponse to
an ENCOUNTER with a KNOWN or SUSPECTED TERRORIST. All collection of TERRORISM
OR OFFICIAL USE SECURITY INFORMATION
Page 69
OFFICIAL USE SECURITY INFORMATION
'Pagers
Any electronic storage media
Employment information:
Pay stubs
Employment applications
Want ads
Employer correspondence
6) Access cards, badges
l315.
Professional papers/Academic information:
Resumes
Academic transcripts
Legal document information:
Birth certi?cates
Immigration and naturalization documents
Marriage licenses
Divorce decrees
Adoption papers
Living Wills
Last Will and Testament
Parking tickets
Speeding tickets
Property records (deeds)
Summons
Criminal documents or civil lawsuit information
Miscellaneous item information:
Long term storage facilities access keys, codes)
Social networking accounts Facebook, Twitter, MySpace, Linkedln, ICQ)
Titles of books, brochures being carried and their condition new,
dog-cared, annotated, unopened, professional journals)
Letters, envelopes
Letters of Introduction
Animal information vet or chip information)
IV. ENCOUNTER MANAGEMENT ACTIONS
5.l2 Handling of ENCOUNTER PACKAGES. This section outlines the processes for handling and
sharing ENCOUNTER PACKAGES by SCREENERS, the TSC and NCTC.
5. l3 Enforcement ENCOUNTERS. TSOU coordinates the US. Govemment?s reSponse to
an ENCOUNTER with a KNOWN or SUSPECTED TERRORIST. All collection of TERRORISM
OR OFFICIAL USE SECURITY INFORMATION
Page 69

OR OFFICIAL USE SECURITY INFORMATION
5.14
INFORMATION during law enforcement traf?c violations, investigations,
arrests) are coordinated between the AGENCY and the ENCOUNTERINO AGENCY via
TSOU.
5.13.1 For domestic and international ENCOUNTERS with a person who is a POSITIVE
to a KNOWN or SUSPECTED TERRORIST, TSOU will do the following: After receiving
noti?cation of an ENCOUNTER from the TSC, TSOU will disseminate and coordinate
information to FBI operational entities and federal, state, and local law enforcement
Agencies. TSOU simultaneously coordinates with the appropriate FBI Field Division(s)
and Case Agent(s); Joint Terrorist Task Forces Airport Liaison Agents and
Attaches ;Lega1 Attaches U.S. Embassies and/or other appropriate
law enforcement officials, including ICE and CBP (speci?cally, and NTC-C as
appropriate); and apprOpriate members of the IC. For outbound ENCOUNTERS, or
involving subjects who have certain DEROGATORY INFORMATION, TSOU
contacts (via phone and electronic notification) the appropriate counterterrorism
element(s). Especially sensitive ENCOUNTERS often require coordination and situational
updates with the White House, Northern Command (NORTHCOM), and
Counterterrorism?Watch.
TSC Actions. TSC will update existing KNOWN or records with new
TERRORIST IDENTIFIERS and TERRORISM INFORMATION and will provide the broader
counterterrorism analytic community with as much new information as possible stemming
from an ENCOUNTER with a KNOWN or SUSPECTED TERRORIST. primary methods for
sharing TERRORISM INFORMATION with the broader counterterrorism analytic community will
be through its EMA application and the use of Intelligence Information Reports (IIRs), as
described further in Section V, infra. TSC will also coordinate with Fusion Centers on law
enforcement and other ENCOUNTERS impacting their Area of Responsibility. This
coordination will include a request for record enhancing information from the Fusion Center,
which if received, will be added to the subject?s KNOWN or TERRORIST record.
5.14.1 Any new TERRORISM INFORMATION recorded in, or attached to an EMA record by
will be provided to NCTC via an automated ingest process.89 Such daily ingests of
EMA records update TIDE to re?ect the fact of the ENCOUNTER, any new
identi?ers used to con?rm the KNOWN or SUSPECTED TERRORIST POSITIVE MATCHES, or
those identified in an IIR. Once TIDE has been updated, an automated ingest from
TIDE to TSDB is used to update the various TSDB subsets No Fly or Selectee
Lists). At this point, the process is complete and the watchlisting, screening and law
89 An ?automated ingest? is one where the contents of EMA records are incorporated into TIDE
database via a system-to?system transfer of information that identi?es new or changed information. This process allows
NCTC to spot KNOWN or SUSPECTED records that have been amended or updated. This process also
accommodates the transfer of attached ENCOUNTER PACKAGES received from SCREENERS. In those instances, the
ENCOUNTER PACKAGES appear as attachments to the KNOWN or record. ENCOUNTER PACKAGE
attachments must be moved to another system in order to give the broader counterterrorism community access to the
TERRORISM INFORMATION. That process is described in Section V, infra.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 70
OR OFFICIAL USE SECURITY INFORMATION
5.14
INFORMATION during law enforcement traf?c violations, investigations,
arrests) are coordinated between the AGENCY and the ENCOUNTERINO AGENCY via
TSOU.
5.13.1 For domestic and international ENCOUNTERS with a person who is a POSITIVE
to a KNOWN or SUSPECTED TERRORIST, TSOU will do the following: After receiving
noti?cation of an ENCOUNTER from the TSC, TSOU will disseminate and coordinate
information to FBI operational entities and federal, state, and local law enforcement
Agencies. TSOU simultaneously coordinates with the appropriate FBI Field Division(s)
and Case Agent(s); Joint Terrorist Task Forces Airport Liaison Agents and
Attaches ;Lega1 Attaches U.S. Embassies and/or other appropriate
law enforcement officials, including ICE and CBP (speci?cally, and NTC-C as
appropriate); and apprOpriate members of the IC. For outbound ENCOUNTERS, or
involving subjects who have certain DEROGATORY INFORMATION, TSOU
contacts (via phone and electronic notification) the appropriate counterterrorism
element(s). Especially sensitive ENCOUNTERS often require coordination and situational
updates with the White House, Northern Command (NORTHCOM), and
Counterterrorism?Watch.
TSC Actions. TSC will update existing KNOWN or records with new
TERRORIST IDENTIFIERS and TERRORISM INFORMATION and will provide the broader
counterterrorism analytic community with as much new information as possible stemming
from an ENCOUNTER with a KNOWN or SUSPECTED TERRORIST. primary methods for
sharing TERRORISM INFORMATION with the broader counterterrorism analytic community will
be through its EMA application and the use of Intelligence Information Reports (IIRs), as
described further in Section V, infra. TSC will also coordinate with Fusion Centers on law
enforcement and other ENCOUNTERS impacting their Area of Responsibility. This
coordination will include a request for record enhancing information from the Fusion Center,
which if received, will be added to the subject?s KNOWN or TERRORIST record.
5.14.1 Any new TERRORISM INFORMATION recorded in, or attached to an EMA record by
will be provided to NCTC via an automated ingest process.89 Such daily ingests of
EMA records update TIDE to re?ect the fact of the ENCOUNTER, any new
identi?ers used to con?rm the KNOWN or SUSPECTED TERRORIST POSITIVE MATCHES, or
those identified in an IIR. Once TIDE has been updated, an automated ingest from
TIDE to TSDB is used to update the various TSDB subsets No Fly or Selectee
Lists). At this point, the process is complete and the watchlisting, screening and law
89 An ?automated ingest? is one where the contents of EMA records are incorporated into TIDE
database via a system-to?system transfer of information that identi?es new or changed information. This process allows
NCTC to spot KNOWN or SUSPECTED records that have been amended or updated. This process also
accommodates the transfer of attached ENCOUNTER PACKAGES received from SCREENERS. In those instances, the
ENCOUNTER PACKAGES appear as attachments to the KNOWN or record. ENCOUNTER PACKAGE
attachments must be moved to another system in order to give the broader counterterrorism community access to the
TERRORISM INFORMATION. That process is described in Section V, infra.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page I 70

UN OFFICIAL USE SECURITY INFORMATION
enforcement communities have the most current and thorough TERRORISM INFORMATION
available about a KNOWN 0r SUSPECTED TERRORIST. Most?but not all?of that
TERRORISM INFORMATION is available in a structured format as part of the KNOWN or
SUSPECTED TERRORIST record discrete elements such as a date of birth, country of
origin). The unstructured TERRORISM INFORMATION, while also in digitized format g,
a computer disk, a scanned image of a business card, an encountering of?cer?s report), is
handled by NCTC.
5. IS NCTC Actions. NCTC will post to TIDE Online any digitized ENCOUNTER PACKAGE it
receives from TSC or directly from a SCREENER. ENCOUNTER PACKAGES can be found under
the subject?s main page.
V. ROLES AND RESPONSIBILITIES FOR UPDATING EXISTING KNOWN
OR SUSPECTED TERRORIST RECORDS AND NOMINATIN NEW
KNOWN OR SUSPECT ED TERRORISTS BASED ON INFORMATION
FROM POSITIVE ENCOUNTERS
5. 6 This section describes the roles and responsibilities of the watchlisting, screening, and
counterterrorism communities for exploitation and analysis of the TERRORISM INFORMATION
lawfully collected and shared when there is a POSITIVE MATCH to a KNOWN or SUSPECTED
TERRORIST. In this context the following de?nitions apply:
5.16.I means a quick review of the ENCOUNTER PACKAGE to identify
obvious, new TERRORIST IDENTIFIERS about the KNOWN or SUSPECTED
5.16.2 means a thorough review of the TERRORISM
contained in an ENCOUNTER PACKAGE obtained as a result of the ENCOUNTER with the
KNOWN or SUSPECTED TERRORIST. ADVANCED ANALYSIS includes the adding of
TERRORIST IDENTIFIERS to existing KNOWN or SUSPECTED TERRORIST records and
identifying new KNOWN or TERRORISTS who should be nominated through
the existing nomination process. In this context, ADVANCED ANALYSIS is being done on
a tactical matter related to the speci?c KNOWN or SUSPECTED TERRORIST to identify
information useful in ?connecting the dots? between and among that KNOWN or
SUSPECTED TERRORIST and other KNOWN or SUSPECTED TERRORISTS or potential KNOWN
or SUSPECTED It is also when the need for foreign language translation
services will be identified.
5.16.3 means further exploitation of a targeted set of ENCOUNTER
PACKAGES and ADVANCED ANALYSIS products to assist in identifying TERRORIST trends
and changes to methods, tactics, and practices. ENCOUNTERS for TARGETED ANALYSIS
are selected using contemporaneous threat criteria and research in additional
repositories. Contemporaneous threat criteria includes association with a priority
terrorist group NIPF Tier I or ENCOUNTERS with KNOWN or SUSPECTED
UN OR OFFICIAL USE SECURITY INFORMATION
Page I 71
UN OFFICIAL USE SECURITY INFORMATION
enforcement communities have the most current and thorough TERRORISM INFORMATION
available about a KNOWN 0r SUSPECTED TERRORIST. Most?but not all?of that
TERRORISM INFORMATION is available in a structured format as part of the KNOWN or
SUSPECTED TERRORIST record discrete elements such as a date of birth, country of
origin). The unstructured TERRORISM INFORMATION, while also in digitized format g,
a computer disk, a scanned image of a business card, an encountering of?cer?s report), is
handled by NCTC.
5. IS NCTC Actions. NCTC will post to TIDE Online any digitized ENCOUNTER PACKAGE it
receives from TSC or directly from a SCREENER. ENCOUNTER PACKAGES can be found under
the subject?s main page.
V. ROLES AND RESPONSIBILITIES FOR UPDATING EXISTING KNOWN
OR SUSPECTED TERRORIST RECORDS AND NOMINATIN NEW
KNOWN OR SUSPECT ED TERRORISTS BASED ON INFORMATION
FROM POSITIVE ENCOUNTERS
5. 6 This section describes the roles and responsibilities of the watchlisting, screening, and
counterterrorism communities for exploitation and analysis of the TERRORISM INFORMATION
lawfully collected and shared when there is a POSITIVE MATCH to a KNOWN or SUSPECTED
TERRORIST. In this context the following de?nitions apply:
5.16.I means a quick review of the ENCOUNTER PACKAGE to identify
obvious, new TERRORIST IDENTIFIERS about the KNOWN or SUSPECTED
5.16.2 means a thorough review of the TERRORISM
contained in an ENCOUNTER PACKAGE obtained as a result of the ENCOUNTER with the
KNOWN or SUSPECTED TERRORIST. ADVANCED ANALYSIS includes the adding of
TERRORIST IDENTIFIERS to existing KNOWN or SUSPECTED TERRORIST records and
identifying new KNOWN or TERRORISTS who should be nominated through
the existing nomination process. In this context, ADVANCED ANALYSIS is being done on
a tactical matter related to the speci?c KNOWN or SUSPECTED TERRORIST to identify
information useful in ?connecting the dots? between and among that KNOWN or
SUSPECTED TERRORIST and other KNOWN or SUSPECTED TERRORISTS or potential KNOWN
or SUSPECTED It is also when the need for foreign language translation
services will be identified.
5.16.3 means further exploitation of a targeted set of ENCOUNTER
PACKAGES and ADVANCED ANALYSIS products to assist in identifying TERRORIST trends
and changes to methods, tactics, and practices. ENCOUNTERS for TARGETED ANALYSIS
are selected using contemporaneous threat criteria and research in additional
repositories. Contemporaneous threat criteria includes association with a priority
terrorist group NIPF Tier I or ENCOUNTERS with KNOWN or SUSPECTED
UN OR OFFICIAL USE SECURITY INFORMATION
Page I 71

UN OR OFFICIAL USE SECURITY INFORMATION
designated as No Fly or associated with violent activity; or at the request of
any Department or Agency that identi?es a need.
5. I 7 Results of INITIAL REVIEW, ADVANCED ANALYSIS, and TARGETED ANALYSIS efforts
(collectively, ?Exploitation?) by Departments or Agencies will be reported to the watchlisting,
screening and counterterrorism communities using standard templates when available.
5.l 7.l TSC Actions.
5.17.1.1 First Stage Review. TSC actions with KNOWN or SUSPECTED TERRORIST
ENCOUNTERS occur in two stages. The ?rst stage occurs when the ENCOUNTERING
AGENCY and TSC exchange TERRORIST IDENTIFIERS to determine whether the
individual is watchlisted a POSITIVE MATCH to a TSDB record). TSC records
any new TERRORIST provided during this stage in EMA
application.
5. 7.1 .2 Second Stage Review. The second stage occurs after TSC has confirmed
there is a POSITIVE MATCH to a KNOWN or SUSPECTED For each
POSITIVE MATCII to a KNOWN or SUSPECTEI) TERRORIST, the Of?ce of
Intelligence will generate an HR for dissemination to the
counterterrorism community that provides a summary about the KNOWN or
SUSPECTED TERRORIST ENCOUNTER basic facts about the ENCOUNTER such as
date, time, and place). If available at the time the initial is prepared,
will conduct an INITIAL REVIEW Ofthe ENCOUNTER PACKAGE and provide a
thumbnail summary of the TERRORISM INFORMATION. For example, a summary
might highlight the existence of a new KNOWN or SUSPECTEI) TERRORIST
or SUSPECTED TERRORIST was traveling with three other associates not previously
identi?ed in the car where the explosives were found in a hidden compartment?) or
the possibility that new TERRORIST IDENTIFIERS are available (?approximately 80
pages carried by the KNOWN or SUSPECTED TERRORIST were converted to electronic
documents ranging from the KNOWN or calendar/address
book to bank account and credit card numbers?).
5.17.2 National Media Exploitation Center Actions. Much of the TERRORISM
INFORMATION generated by ENCOUNTERS from a person who is a POSITIVE MATCH to a
KNOWN or SUSPECTED TERRORIST is expected to be in a foreign language that may hinder
prompt exploitation. The National Media Exploitation Center (NMEC) has the
capability to translate foreign language information and the experience necessary to
understand the efforts used to hide their activities. When TSC receives ENCOUNTER
PACKAGES with information in a foreign language, or when NCTC receives them
directly from an ENCOUNTERING AGENCY, TSC or NCTC will forward/notify NMEC that
it has the action to translate the ENCOUNTER PACKAGE. Once the ENCOUNTER PACKAGE
has been translated and returned to TSC and NCTC, the assigned roles and responsibility
for exploitation will apply.
UN OR OFFICIAL USE SECURITY INFORMATION
Page 72
UN OR OFFICIAL USE SECURITY INFORMATION
designated as No Fly or associated with violent activity; or at the request of
any Department or Agency that identi?es a need.
5. I 7 Results of INITIAL REVIEW, ADVANCED ANALYSIS, and TARGETED ANALYSIS efforts
(collectively, ?Exploitation?) by Departments or Agencies will be reported to the watchlisting,
screening and counterterrorism communities using standard templates when available.
5.l 7.l TSC Actions.
5.17.1.1 First Stage Review. TSC actions with KNOWN or SUSPECTED TERRORIST
ENCOUNTERS occur in two stages. The ?rst stage occurs when the ENCOUNTERING
AGENCY and TSC exchange TERRORIST IDENTIFIERS to determine whether the
individual is watchlisted a POSITIVE MATCH to a TSDB record). TSC records
any new TERRORIST provided during this stage in EMA
application.
5. 7.1 .2 Second Stage Review. The second stage occurs after TSC has confirmed
there is a POSITIVE MATCH to a KNOWN or SUSPECTED For each
POSITIVE MATCII to a KNOWN or SUSPECTEI) TERRORIST, the Of?ce of
Intelligence will generate an HR for dissemination to the
counterterrorism community that provides a summary about the KNOWN or
SUSPECTED TERRORIST ENCOUNTER basic facts about the ENCOUNTER such as
date, time, and place). If available at the time the initial is prepared,
will conduct an INITIAL REVIEW Ofthe ENCOUNTER PACKAGE and provide a
thumbnail summary of the TERRORISM INFORMATION. For example, a summary
might highlight the existence of a new KNOWN or SUSPECTEI) TERRORIST
or SUSPECTED TERRORIST was traveling with three other associates not previously
identi?ed in the car where the explosives were found in a hidden compartment?) or
the possibility that new TERRORIST IDENTIFIERS are available (?approximately 80
pages carried by the KNOWN or SUSPECTED TERRORIST were converted to electronic
documents ranging from the KNOWN or calendar/address
book to bank account and credit card numbers?).
5.17.2 National Media Exploitation Center Actions. Much of the TERRORISM
INFORMATION generated by ENCOUNTERS from a person who is a POSITIVE MATCH to a
KNOWN or SUSPECTED TERRORIST is expected to be in a foreign language that may hinder
prompt exploitation. The National Media Exploitation Center (NMEC) has the
capability to translate foreign language information and the experience necessary to
understand the efforts used to hide their activities. When TSC receives ENCOUNTER
PACKAGES with information in a foreign language, or when NCTC receives them
directly from an ENCOUNTERING AGENCY, TSC or NCTC will forward/notify NMEC that
it has the action to translate the ENCOUNTER PACKAGE. Once the ENCOUNTER PACKAGE
has been translated and returned to TSC and NCTC, the assigned roles and responsibility
for exploitation will apply.
UN OR OFFICIAL USE SECURITY INFORMATION
Page 72

UNCLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
5.l7.3 FBI Actions. The majority of the ENCOUNTERS with KNOWN or
TERRORISTS occur in the United States. The FBI has ADVANCED ANALYSIS responsibility
for ENCOUNTER PACKAGES on KNOWN or SUSPECTED TERRORISTS for whom the FBI has
an open investigation, no matter where the individual is encountered. 1f the FBI does
not have an open investigation on a KNOWN or TERRORIST encountered in the
United States, or if the KNOWN or SUSPECTED TERRORIST is a PERSON, then TSOU
will send a lead directing the appropriate FBI ?eld of?ce to conduct an assessment of
the individual and the ENCOUNTER circumstances to determine whether to open a
preliminary or full investigation.90 This assessment includes ADVANCED ANALYSIS
packages when provided by ENCOUNTERING AGENCIES. If no investigation is opened, an
11R will be sent to the NOMINATING AGENCY and NCTC which will be used to enhance
the record with additional Bl?derived information.
5.17.4 DI-IS Actions. DHS has ADVANCED ANALYSIS responsibility for
ENCOUNTER PACKAGES where the KNOWN or SUSPECTED TERRORIST is denied entry,
denied ESTA, denied boarding, or is subject to a no board recommendation at a foreign
location, or identi?ed through lCE?s visa security processes.
5.17.5 NCTC Actions. On occasion, DOS, and foreign governments have
ENCOUNTERS with KNOWN or SUSPECTED TERRORISTS, usually in the form of a record
ENCOUNTER the KNOWN or SUSPECTED TERRORIST has submitted an application for
a bene?t like a visa or grant or information is provided to the United States by a foreign
government). has ADVANCED ANALYSIS responsibility for ENCOUNTER PACKAGES
in these instances.
5.17.5.1 For TARGETED ANALYSIS, NCTC Offers this capability for a select set of
ENCOUNTER PACKAGES based on internal or interageney tasking. Since all
ADVANCED ANALYSIS products created by FBI, DHS, or NCTC will be
disseminated to the US. Government via an HR, these materials are available to
any organization seeking to further exploit speci?c NCTC will
leverage these ADVANCED ANALYSIS products as part of its typical intelligence
analytic process to highlight emerging threats, issues or concerns.
5.17.6 A chart depicting the roles and responsibilities by Department or Agency may be
found at the end of this Chapter.
VI. RESPONSIBILITY TO COORDINATE ANY ACTIONS
CONTEMPLATED BASED ON INFORMATION FROM ENCOUNTERS
WITH A KNOWN OR SUSPECTED TERRORIST
9" Under governing authorities, the FBI can conduct ?assessments? for an authorized purpose, such as obtaining
information about a threat to national security, without a particular factual predication. To open an investigation
whether a ?preliminary? or ?full? investigation there must be a speci?c factual predication.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 73
UNCLASSIF OR OFFICIAL USE ON SECURITY INFORMATION
5.l7.3 FBI Actions. The majority of the ENCOUNTERS with KNOWN or
TERRORISTS occur in the United States. The FBI has ADVANCED ANALYSIS responsibility
for ENCOUNTER PACKAGES on KNOWN or SUSPECTED TERRORISTS for whom the FBI has
an open investigation, no matter where the individual is encountered. 1f the FBI does
not have an open investigation on a KNOWN or TERRORIST encountered in the
United States, or if the KNOWN or SUSPECTED TERRORIST is a PERSON, then TSOU
will send a lead directing the appropriate FBI ?eld of?ce to conduct an assessment of
the individual and the ENCOUNTER circumstances to determine whether to open a
preliminary or full investigation.90 This assessment includes ADVANCED ANALYSIS
packages when provided by ENCOUNTERING AGENCIES. If no investigation is opened, an
11R will be sent to the NOMINATING AGENCY and NCTC which will be used to enhance
the record with additional Bl?derived information.
5.17.4 DI-IS Actions. DHS has ADVANCED ANALYSIS responsibility for
ENCOUNTER PACKAGES where the KNOWN or SUSPECTED TERRORIST is denied entry,
denied ESTA, denied boarding, or is subject to a no board recommendation at a foreign
location, or identi?ed through lCE?s visa security processes.
5.17.5 NCTC Actions. On occasion, DOS, and foreign governments have
ENCOUNTERS with KNOWN or SUSPECTED TERRORISTS, usually in the form of a record
ENCOUNTER the KNOWN or SUSPECTED TERRORIST has submitted an application for
a bene?t like a visa or grant or information is provided to the United States by a foreign
government). has ADVANCED ANALYSIS responsibility for ENCOUNTER PACKAGES
in these instances.
5.17.5.1 For TARGETED ANALYSIS, NCTC Offers this capability for a select set of
ENCOUNTER PACKAGES based on internal or interageney tasking. Since all
ADVANCED ANALYSIS products created by FBI, DHS, or NCTC will be
disseminated to the US. Government via an HR, these materials are available to
any organization seeking to further exploit speci?c NCTC will
leverage these ADVANCED ANALYSIS products as part of its typical intelligence
analytic process to highlight emerging threats, issues or concerns.
5.17.6 A chart depicting the roles and responsibilities by Department or Agency may be
found at the end of this Chapter.
VI. RESPONSIBILITY TO COORDINATE ANY ACTIONS
CONTEMPLATED BASED ON INFORMATION FROM ENCOUNTERS
WITH A KNOWN OR SUSPECTED TERRORIST
9" Under governing authorities, the FBI can conduct ?assessments? for an authorized purpose, such as obtaining
information about a threat to national security, without a particular factual predication. To open an investigation
whether a ?preliminary? or ?full? investigation there must be a speci?c factual predication.
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Page 73

OR OFFICIAL USE SECURITY INFORMATION
5.18 Information Sharing MOU Requirements. Departments and Agencies are reminded of
their agreement to provide transparency between and among them with regard to their
?activities to preempt, prevent, and disrupt TERRORIST attacks against U.S. PERSONS and
interests.9l As a practical matter, that type of transparency demands, to the greatest extent
possible, prior coordination with affected Departments or Agencies before action within a
Department or Agency?s authorities is taken based on TERRORISM INFORMATION from a person
who is a POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST. For example, FBI, Central
intelligence Agency (CIA) or DOD, as lead counterterrorism Agencies in their respective
domains, must be consulted prior to taking any action based on ENCOUNTERS with a person
who is a POSITIVE MATCH with KNOWN or SUSPECTED This guidance is subject to
existing policies and coordination procedures when action against or pertaining to the KNOWN
or SUSPECTED TERRORIST is contemplated.
5.19 Requests for Withholding of Action. In certain circumstances, law enforcement or the 1C
may request that a SCREBNER not take action not to refuse the visa, to allow individual to
enter the United States, to not deny an individual to obtain an immigration bene?t or access to
the secure area of an airport) although action may be taken under the law. This request, to the
extent practicable, shall be in writing, by a senior of?cial, and include a statement of
justi?cation and risk mitigation. Departments and Agencies will establish mutually
acceptable processes and procedures to implement a detailed plan.
VII. EXAMPLES OF TERRORISM INFORMATION TYPICALLY
AVAILABLE FROM ENCOUNTERS
5.20 The following examples of various types of ENCOUNTERS and the type of information typically
generated from those ENCOUNTERS is offered to assist Departments and Agencies in
understanding what additional or new information may become available as a result of
following the guidance provided in this document.
5.20.1 Ports of Entry. Types of documents that could be included in the ENCOUNTER
PACKAGE typically include:
1. Business cards
2. Copies of passport and visa entries
9' See Paragraph 3(b) of the Information Sharing MOU (Appendix 5): ?Reciprocity and Transparency. All information
collected by any entity relevant to the missions and responsibilities of any other covered entities should be shared, to the
greatest extent possible, between and among all covered entities. Likewise, the parties agree that, to the greatest extent
possible, there should be transparency between and among the covered entities with regard to their activities to preempt,
prevent, and disrupt TERRORIST attacks against U.S. PERSONS and interests. Except as otherwise speci?ed in this
Agreement, or mandated by relevant Federal statutes or Presidential Directives, procedures and mechanisms for
information sharing, use, and handling shall be interpreted and implemented consistently and reciprocally regardless of
the role a particular covered entity plays as a provider or recipient of covered information. In other words, for example,
international TERRORISM collected by the Border Patrol should be shared by DHS with the to the same
extent foreign intelligence information on TERRORISM is shared by the with
OR OFFICIAL USE SECURITY INFORMATION
Page 74
OR OFFICIAL USE SECURITY INFORMATION
5.18 Information Sharing MOU Requirements. Departments and Agencies are reminded of
their agreement to provide transparency between and among them with regard to their
?activities to preempt, prevent, and disrupt TERRORIST attacks against U.S. PERSONS and
interests.9l As a practical matter, that type of transparency demands, to the greatest extent
possible, prior coordination with affected Departments or Agencies before action within a
Department or Agency?s authorities is taken based on TERRORISM INFORMATION from a person
who is a POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST. For example, FBI, Central
intelligence Agency (CIA) or DOD, as lead counterterrorism Agencies in their respective
domains, must be consulted prior to taking any action based on ENCOUNTERS with a person
who is a POSITIVE MATCH with KNOWN or SUSPECTED This guidance is subject to
existing policies and coordination procedures when action against or pertaining to the KNOWN
or SUSPECTED TERRORIST is contemplated.
5.19 Requests for Withholding of Action. In certain circumstances, law enforcement or the 1C
may request that a SCREBNER not take action not to refuse the visa, to allow individual to
enter the United States, to not deny an individual to obtain an immigration bene?t or access to
the secure area of an airport) although action may be taken under the law. This request, to the
extent practicable, shall be in writing, by a senior of?cial, and include a statement of
justi?cation and risk mitigation. Departments and Agencies will establish mutually
acceptable processes and procedures to implement a detailed plan.
VII. EXAMPLES OF TERRORISM INFORMATION TYPICALLY
AVAILABLE FROM ENCOUNTERS
5.20 The following examples of various types of ENCOUNTERS and the type of information typically
generated from those ENCOUNTERS is offered to assist Departments and Agencies in
understanding what additional or new information may become available as a result of
following the guidance provided in this document.
5.20.1 Ports of Entry. Types of documents that could be included in the ENCOUNTER
PACKAGE typically include:
1. Business cards
2. Copies of passport and visa entries
9' See Paragraph 3(b) of the Information Sharing MOU (Appendix 5): ?Reciprocity and Transparency. All information
collected by any entity relevant to the missions and responsibilities of any other covered entities should be shared, to the
greatest extent possible, between and among all covered entities. Likewise, the parties agree that, to the greatest extent
possible, there should be transparency between and among the covered entities with regard to their activities to preempt,
prevent, and disrupt TERRORIST attacks against U.S. PERSONS and interests. Except as otherwise speci?ed in this
Agreement, or mandated by relevant Federal statutes or Presidential Directives, procedures and mechanisms for
information sharing, use, and handling shall be interpreted and implemented consistently and reciprocally regardless of
the role a particular covered entity plays as a provider or recipient of covered information. In other words, for example,
international TERRORISM collected by the Border Patrol should be shared by DHS with the to the same
extent foreign intelligence information on TERRORISM is shared by the with
OR OFFICIAL USE SECURITY INFORMATION
Page 74

OR OFFICIAL USE SECURITY INFORMATION
10.
12.
13.
14.
Driver?s license
Resumes
Conference literature
Correspondence not in possession of the US. Postal Service.
Letters of introduction
Checks, bank deposit slips
Calendar/schedule
Address book
Notepad entries
Mariner?s certi?cates
Telephone data
Location and duration of previous travel stops on current or past travel
itinerary
5.20.2 Law Enforcement ENCOUNTERS. Information collected from law enforcement
with a person who is a POSITIVE MATCH to a KNOWN or SUSPECTED
can include any information that would be collected when a law enforcement
of?cer speaks with a KNOWN or TERRORIST. Typically information that
could be included in the ENCOUNTER PACKAGE can include, but is not limited to:
5.20.3
Associates
Telephone numbers (home, business, cell, pager, or fax)
Other forms of identi?cation
Physical descriptors
Family members
Occupation and work history
Travel plans or history
Vehicle information
Visa Applications. A typical DOS ENCOUNTER PACKAGE with a person who is a
POSITIVE MATCH to a KNOWN or SUSPECTED will be a visa application for
entry to the United States, which identi?es basic information about the encountered
KNOWN or SUSPECTED TERRORIST and the ENCOUNTER. Types of documents that could
be included in the ENCOUNTER PACKAGE typically include:
Ppwsa
Home and work address
Copies of passport and visa entries
National identi?cation Number (if applicable to the country)
Phone numbers (home, business, cell, pager, or fax)
Sponsorship information (when available, to include individual?s
name/Company/Govemment, address and contact information)
Family member names spouse, parents, children)
Police Certi?cates (if applicable)
Biometrics (Photos and Fingerprint Identi?cation Number
Resumes (when applying for business visas)
Letters of introduction
OR OFFICIAL USE SECURITY INFORMATION
Page 75
OR OFFICIAL USE SECURITY INFORMATION
10.
12.
13.
14.
Driver?s license
Resumes
Conference literature
Correspondence not in possession of the US. Postal Service.
Letters of introduction
Checks, bank deposit slips
Calendar/schedule
Address book
Notepad entries
Mariner?s certi?cates
Telephone data
Location and duration of previous travel stops on current or past travel
itinerary
5.20.2 Law Enforcement ENCOUNTERS. Information collected from law enforcement
with a person who is a POSITIVE MATCH to a KNOWN or SUSPECTED
can include any information that would be collected when a law enforcement
of?cer speaks with a KNOWN or TERRORIST. Typically information that
could be included in the ENCOUNTER PACKAGE can include, but is not limited to:
5.20.3
Associates
Telephone numbers (home, business, cell, pager, or fax)
Other forms of identi?cation
Physical descriptors
Family members
Occupation and work history
Travel plans or history
Vehicle information
Visa Applications. A typical DOS ENCOUNTER PACKAGE with a person who is a
POSITIVE MATCH to a KNOWN or SUSPECTED will be a visa application for
entry to the United States, which identi?es basic information about the encountered
KNOWN or SUSPECTED TERRORIST and the ENCOUNTER. Types of documents that could
be included in the ENCOUNTER PACKAGE typically include:
Ppwsa
Home and work address
Copies of passport and visa entries
National identi?cation Number (if applicable to the country)
Phone numbers (home, business, cell, pager, or fax)
Sponsorship information (when available, to include individual?s
name/Company/Govemment, address and contact information)
Family member names spouse, parents, children)
Police Certi?cates (if applicable)
Biometrics (Photos and Fingerprint Identi?cation Number
Resumes (when applying for business visas)
Letters of introduction
OR OFFICIAL USE SECURITY INFORMATION
Page 75

OR OFFICIAL USE SECURITY INFORMATION
ll.
12.
l3.
l4.
l6.
17.
Military related documents
Education
Prior travel
Occupation and work history
Financial information used to support visa application including bank
statements, salary slips/letters, property records
Photos
Email addresses
5.20.4 Applications or Petitions for Immigration Bene?ts. may receive an
application from an alien for immigration benefits or petitions. Depending on the
completed form, may have information from the following non-exhaustive
categories:
5.20.5
Residences domestic and foreign
amin Members (often extended family)
Occupation
Bank account information
Biometrics
Gender
Identity documents
Travel document information (and 1-94)
Civil documents?FOB, COC data
. Employer/Prospective Employer
. Religious Af?liations
. Resumes
. Educational Background
. Past marriages or divorces
. Biographical Information
ENCOUNTERS by HSPD-6 Foreign Partners. On some occasions, and based on the
arrangement with and legal authorities of the particular foreign partner involved, an
ENCOUNTER PACKAGE may include the KNOWN or SUSPECTED visa
application to a foreign partner. One such student visa/permit application to a foreign
partner could include information provided from the KNOWN or SUSPECTED in
the following categories:
Name as shown in passport
Other names known by or ever known by
Name in ethnic script
Gender
Date of birth
Town/city of birth
Country of birth
OR OFFICIAL USE SECURITY INFORMATION
Page 76
OR OFFICIAL USE SECURITY INFORMATION
ll.
12.
l3.
l4.
l6.
17.
Military related documents
Education
Prior travel
Occupation and work history
Financial information used to support visa application including bank
statements, salary slips/letters, property records
Photos
Email addresses
5.20.4 Applications or Petitions for Immigration Bene?ts. may receive an
application from an alien for immigration benefits or petitions. Depending on the
completed form, may have information from the following non-exhaustive
categories:
5.20.5
Residences domestic and foreign
amin Members (often extended family)
Occupation
Bank account information
Biometrics
Gender
Identity documents
Travel document information (and 1-94)
Civil documents?FOB, COC data
. Employer/Prospective Employer
. Religious Af?liations
. Resumes
. Educational Background
. Past marriages or divorces
. Biographical Information
ENCOUNTERS by HSPD-6 Foreign Partners. On some occasions, and based on the
arrangement with and legal authorities of the particular foreign partner involved, an
ENCOUNTER PACKAGE may include the KNOWN or SUSPECTED visa
application to a foreign partner. One such student visa/permit application to a foreign
partner could include information provided from the KNOWN or SUSPECTED in
the following categories:
Name as shown in passport
Other names known by or ever known by
Name in ethnic script
Gender
Date of birth
Town/city of birth
Country of birth
OR OFFICIAL USE SECURITY INFORMATION
Page 76

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
10.
l2.
13.
14.
15.
l6.
l7.
l8.
I9.
20.
21.
22.
23.
24.
25.
26.
27.
28.
29.
30.
Passport number, country, expiration date
Country of citizenship
Other citizenships held
Residential address and telephone number in home country
Local residential address and telephone number (if already in country)
Name and address for communication about this application
Name and address of friends, relatives, or contacts you have in the country (if
applicable)
All periods of employment, including self-employment (to/from dates, name of
employer, location, type of work/occupation/job title)
Financial information used to support visa application including bank
statements, salary slips/letters, and property records
Length of planned stay in country
Questions concerning the person?s character whether the person has ever
been convicted, charged, or under investigation for any offensc(s) against the
law in any country; ever deported, excluded or refused a visa by/removed from
any country; and police certi?cates (as evidence of character) from home
country or countries of citizenship and from all countries where the person has
lived for five or more years since age 17)
Whether the application is for a student visa, a student permit, or a limited
purpose visa
Whether the application is for a variation of conditions to work
Course of study and details of the course(s) enrolled
Arrangements for outward travel from host country
Name of legal guardian, other names legal guardian is known by, and
relationship mother, father, legal guardian)
Any national identity number or other unique identifier issued by a government
Any completed military service from/to dates, rank, unit name or number,
role)
Whether presently subject to military service obligation in any country
Any association with any intelligence agency or group, or law enforcement
agency
Any association with any group or organization that has used or promoted
violence to further their aims
Any involvement in war crimes, crimes against humanity, and/or human rights
abuses
Payment method for application fee bank check/draft, credit card, or
personal check)
OBTAINING ENCOUNTER INFORMATION THROUGH DAILY
ENCOUNTER REPORTS
5.2] in addition to the aforementioned lle following an ENCOUNTER with a person who is
a POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST, Agencies can obtain the Daily
OR OFFICIAL USE SECURITY INFORMATION
Page 77
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
10.
l2.
13.
14.
15.
l6.
l7.
l8.
I9.
20.
21.
22.
23.
24.
25.
26.
27.
28.
29.
30.
Passport number, country, expiration date
Country of citizenship
Other citizenships held
Residential address and telephone number in home country
Local residential address and telephone number (if already in country)
Name and address for communication about this application
Name and address of friends, relatives, or contacts you have in the country (if
applicable)
All periods of employment, including self-employment (to/from dates, name of
employer, location, type of work/occupation/job title)
Financial information used to support visa application including bank
statements, salary slips/letters, and property records
Length of planned stay in country
Questions concerning the person?s character whether the person has ever
been convicted, charged, or under investigation for any offensc(s) against the
law in any country; ever deported, excluded or refused a visa by/removed from
any country; and police certi?cates (as evidence of character) from home
country or countries of citizenship and from all countries where the person has
lived for five or more years since age 17)
Whether the application is for a student visa, a student permit, or a limited
purpose visa
Whether the application is for a variation of conditions to work
Course of study and details of the course(s) enrolled
Arrangements for outward travel from host country
Name of legal guardian, other names legal guardian is known by, and
relationship mother, father, legal guardian)
Any national identity number or other unique identifier issued by a government
Any completed military service from/to dates, rank, unit name or number,
role)
Whether presently subject to military service obligation in any country
Any association with any intelligence agency or group, or law enforcement
agency
Any association with any group or organization that has used or promoted
violence to further their aims
Any involvement in war crimes, crimes against humanity, and/or human rights
abuses
Payment method for application fee bank check/draft, credit card, or
personal check)
OBTAINING ENCOUNTER INFORMATION THROUGH DAILY
ENCOUNTER REPORTS
5.2] in addition to the aforementioned lle following an ENCOUNTER with a person who is
a POSITIVE MATCH to a KNOWN or SUSPECTED TERRORIST, Agencies can obtain the Daily
OR OFFICIAL USE SECURITY INFORMATION
Page 77

UN OR OFFICIAL USE SECURITY INFORMATION
Summary Report (DSR) to assist them in identifying ENCOUNTERS of interest to their
organizational missions. DSRs will contain as much information as legally permissible.
DSRs are available from the following locations:
5.2 .I On the Secret Internet Protocol Router Network (SIPRNET),
click on the Intel Daily Summary Reports? link on the right side.
5.2 .2 On Law Enforcement Online (LEO) via
5.21.3 0n Regional Information Sharing Systems via
5.21.4 On HS (for access contact state or local fusion center) or email:
a .dhs. ov
5.21.5 Two sources on FBlNet:
5.21.5.1 homepage at
5.21.5.2 Current lntelligence Report at
OR OFFICIAL USE SECURITY INFORMATION
Page I 78
UN OR OFFICIAL USE SECURITY INFORMATION
Summary Report (DSR) to assist them in identifying ENCOUNTERS of interest to their
organizational missions. DSRs will contain as much information as legally permissible.
DSRs are available from the following locations:
5.2 .I On the Secret Internet Protocol Router Network (SIPRNET),
click on the Intel Daily Summary Reports? link on the right side.
5.2 .2 On Law Enforcement Online (LEO) via
5.21.3 0n Regional Information Sharing Systems via
5.21.4 On HS (for access contact state or local fusion center) or email:
a .dhs. ov
5.21.5 Two sources on FBlNet:
5.21.5.1 homepage at
5.21.5.2 Current lntelligence Report at
OR OFFICIAL USE SECURITY INFORMATION
Page I 78
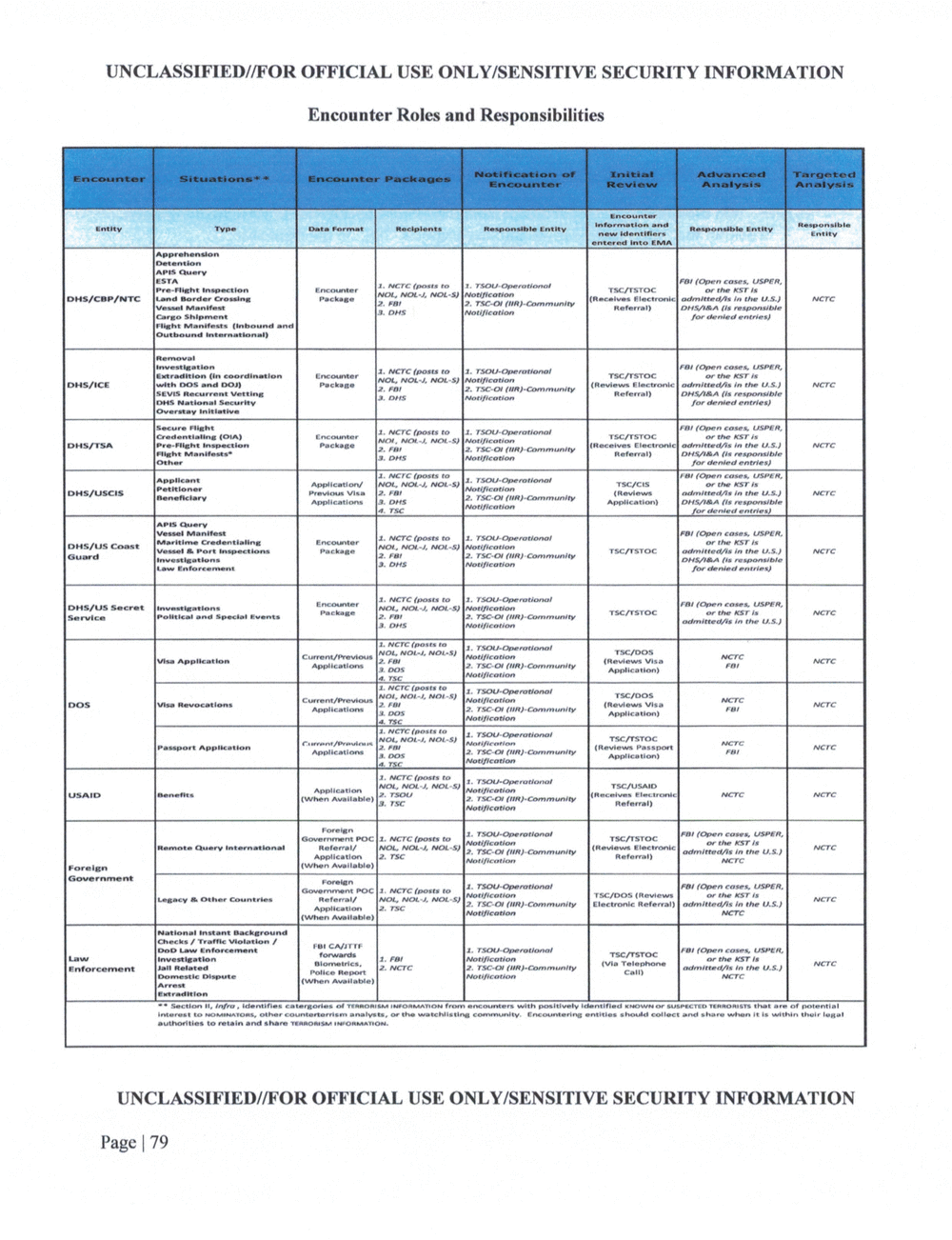
OFFICIAL USE SECURITY INFORMATION
Encounter Roles and Responsibilities
lane-untu-
and man-nu.
M. on. mm
now mm In" ln'nv
m? Into
Wuhan
?caution
APIS (In-w
FBI (Chen cans, USPER,
m-m-M moo-men Enema! Lozm??abap'm TSCITSTOC or me
Lll'ld lord- Dodo. 2 "2 No In?) mun, (Il?im lloclronlc Dd!"li In the 1.1.5.) NCTC
Var-.1 Mon? 3' t) I: "on - Halon-ll) DHWA (I:
Mo Shim!? I a for outdo!)
Huh: Manolo.? llnbouud and
Outbound Int-rumba?)
I'm-l
hug-tunnel! A. I 1. me, ?30? 1 Fl! (?on calls, USPIR,
w? "0:4 "o?rs? ?numl or I?ll. KST ll
00? MC Pick-.- a 2 rx_a Elacwonlc odnll?cd?s In the 0.5.) NCTC
Suns manna: mun. J. on; Natl. Relen-l) responsible
OHS Nation-l Why [or denied (atrial)
Our-rm
locum ?ight (Opln can; USPER,
Guam-nu. (01A) Encounur It?! ?c 9 ?hrzc,mu ?can? or the KST
Pro-?ight lawlon Puclugn (ll-cow" Eloctronic admitted/I: In the U5.)
2. FBI 2. nice: (MU-Conlmunlly
Hut? Mann-m. OHS ?No??cau?an union-I) (ll
Oth-i for denied
1. IVCIC (poor: to I'll 1.17"; LISPEH,
Appumw N01. NOL-J, Mac-5) 1' 'rsc/cos or xer:
vrovnou- 2. For 2 ?Ga mun, (um-w- In m. 41.5.) NCYC
I I I Applicant)!? 3. '7 Apouca?onl DHWA (fl "Wu-
4. TSC [or donkd crud-'3)
Qua-v
wand. Manual . 1. to m_ m" I Fl! (man?s-nus. USPER.
nus/us Coast ~04 Iva?1 wt-s) o"
Von-l In Pen milea- Puclroln 2 2 rgc_a In tho 1.1.5.)
mung-cum "on ans/m4 "mum.
Law [Momma-n [or car-lad cum")
1. {posts to 1. TSOU-anm?onal
Sacra: . m-nlonl ~01, Iva-J, Mot?s) Noti?cation to" 'us"n'
?Mg. I'omlcal and Inca-I lv-ntl 2. PM 2. not? (Ilk)-Cornmunny [gm M:
3. ans Nofl?callon
I. (pan- to r?m I
Cmrn/W No? "at-1' Nob? :l-ou?ca?on TmeS NC'rc
vh- "pug-Non 2. Fl: 2- 7560? (Reviews n" NCTC
3 Do; Apo?callon)
.Nou?couoo
I. (pout to
m, um, Mo: .1, Mal-S) 'sa?nudop?m "um" rsc/oos MC
DOS VOI- Moe-?out 2. 2. 7500? (mu. Manny (Review. NCTC
up I. 1 DOS Nau?m Application)
4. 736
NCTC (pour:
x. TSOU?Opom?onal
NOL. Not-l. NOL-SJ
fumM/Pululnnq Nonlk'auon WC .
.
Panpon Alanna-Non it.? i z. i (?aw mum? (Revlow?sc-Jgirin rat NCIC
TEE Noti?cation I I
1. WC (pa-ll to
1.
game; I. manna? (n on! ~Crc
(whoa Anllablo) 2. rsc-o: (nu-ammunny
3. 756 ?taunt!?
Fad-n
. I
1 a" on? T?c?SToc I:
ulnmotom morn-slam lul?cmll/ 20L. NOL-S) 7360? alum? 23M: m?mM? M. us.) NCTC
NDH?ca'lon ~ch
For-I."
Fm"
I TSCIDOS (mm-w- 9,3321: R.
. . - NCTC
hm . 433:" gage? I s) 2. (560! (mu-Community Electronic Referral) mined/h In the 0.5.)
I Nauru-cum
union-l Inn-n: ?round
mocha/Truf?e ?outlon I
DOD 1. mmfoc (Open can]. USPER.
Law menu-thou mm 1. Fl! Nouns-cum w" or the 151? II
[Mal-emf? nu Isl-Rod mfg-"M . MT: 2. rsc-ov (mu-Community admf?ld/n In the us.)
comic H.01- ?Natl/Itoth WC
Am
Hlmradnlon
Suction II, Infra . ld-Ml?ol cit-modal oi
"on!
poultle ldonulI-d Inownor nun-unto that Dr. oI pol-null
Int-rust lo mammal, olhov counlommnm IMIVICI, or the CWIV incessant-rin- should colloc? 3nd sham whor- II It Ihvh Ian-I
anthem-IN? to Ind than "noon-m "powwow.
OR OFFICIAL USE SECURITY INFORMATION
Page 79
OFFICIAL USE SECURITY INFORMATION
Encounter Roles and Responsibilities
lane-untu-
and man-nu.
M. on. mm
now mm In" ln'nv
m? Into
Wuhan
?caution
APIS (In-w
FBI (Chen cans, USPER,
m-m-M moo-men Enema! Lozm??abap'm TSCITSTOC or me
Lll'ld lord- Dodo. 2 "2 No In?) mun, (Il?im lloclronlc Dd!"li In the 1.1.5.) NCTC
Var-.1 Mon? 3' t) I: "on - Halon-ll) DHWA (I:
Mo Shim!? I a for outdo!)
Huh: Manolo.? llnbouud and
Outbound Int-rumba?)
I'm-l
hug-tunnel! A. I 1. me, ?30? 1 Fl! (?on calls, USPIR,
w? "0:4 "o?rs? ?numl or I?ll. KST ll
00? MC Pick-.- a 2 rx_a Elacwonlc odnll?cd?s In the 0.5.) NCTC
Suns manna: mun. J. on; Natl. Relen-l) responsible
OHS Nation-l Why [or denied (atrial)
Our-rm
locum ?ight (Opln can; USPER,
Guam-nu. (01A) Encounur It?! ?c 9 ?hrzc,mu ?can? or the KST
Pro-?ight lawlon Puclugn (ll-cow" Eloctronic admitted/I: In the U5.)
2. FBI 2. nice: (MU-Conlmunlly
Hut? Mann-m. OHS ?No??cau?an union-I) (ll
Oth-i for denied
1. IVCIC (poor: to I'll 1.17"; LISPEH,
Appumw N01. NOL-J, Mac-5) 1' 'rsc/cos or xer:
vrovnou- 2. For 2 ?Ga mun, (um-w- In m. 41.5.) NCYC
I I I Applicant)!? 3. '7 Apouca?onl DHWA (fl "Wu-
4. TSC [or donkd crud-'3)
Qua-v
wand. Manual . 1. to m_ m" I Fl! (man?s-nus. USPER.
nus/us Coast ~04 Iva?1 wt-s) o"
Von-l In Pen milea- Puclroln 2 2 rgc_a In tho 1.1.5.)
mung-cum "on ans/m4 "mum.
Law [Momma-n [or car-lad cum")
1. {posts to 1. TSOU-anm?onal
Sacra: . m-nlonl ~01, Iva-J, Mot?s) Noti?cation to" 'us"n'
?Mg. I'omlcal and Inca-I lv-ntl 2. PM 2. not? (Ilk)-Cornmunny [gm M:
3. ans Nofl?callon
I. (pan- to r?m I
Cmrn/W No? "at-1' Nob? :l-ou?ca?on TmeS NC'rc
vh- "pug-Non 2. Fl: 2- 7560? (Reviews n" NCTC
3 Do; Apo?callon)
.Nou?couoo
I. (pout to
m, um, Mo: .1, Mal-S) 'sa?nudop?m "um" rsc/oos MC
DOS VOI- Moe-?out 2. 2. 7500? (mu. Manny (Review. NCTC
up I. 1 DOS Nau?m Application)
4. 736
NCTC (pour:
x. TSOU?Opom?onal
NOL. Not-l. NOL-SJ
fumM/Pululnnq Nonlk'auon WC .
.
Panpon Alanna-Non it.? i z. i (?aw mum? (Revlow?sc-Jgirin rat NCIC
TEE Noti?cation I I
1. WC (pa-ll to
1.
game; I. manna? (n on! ~Crc
(whoa Anllablo) 2. rsc-o: (nu-ammunny
3. 756 ?taunt!?
Fad-n
. I
1 a" on? T?c?SToc I:
ulnmotom morn-slam lul?cmll/ 20L. NOL-S) 7360? alum? 23M: m?mM? M. us.) NCTC
NDH?ca'lon ~ch
For-I."
Fm"
I TSCIDOS (mm-w- 9,3321: R.
. . - NCTC
hm . 433:" gage? I s) 2. (560! (mu-Community Electronic Referral) mined/h In the 0.5.)
I Nauru-cum
union-l Inn-n: ?round
mocha/Truf?e ?outlon I
DOD 1. mmfoc (Open can]. USPER.
Law menu-thou mm 1. Fl! Nouns-cum w" or the 151? II
[Mal-emf? nu Isl-Rod mfg-"M . MT: 2. rsc-ov (mu-Community admf?ld/n In the us.)
comic H.01- ?Natl/Itoth WC
Am
Hlmradnlon
Suction II, Infra . ld-Ml?ol cit-modal oi
"on!
poultle ldonulI-d Inownor nun-unto that Dr. oI pol-null
Int-rust lo mammal, olhov counlommnm IMIVICI, or the CWIV incessant-rin- should colloc? 3nd sham whor- II It Ihvh Ian-I
anthem-IN? to Ind than "noon-m "powwow.
OR OFFICIAL USE SECURITY INFORMATION
Page 79

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
A.
F.
G.
ADVANCED ANALYSIS: is a thorough review of the TERRORISM INFORMATION contained in an
ENCOUNTER PACKAGE obtained as a result of the ENCOUNTER with the KNOWN or SUSPECTED
TERRORIST. ADVANCED ANALYSIS includes the adding of TERRORIST IDENTIFIERS to existing
KNOWN or SUSPECTED TERRORIST records and identifying new KNOWN or SUSPECTED
TERRORISTS who should be nominated through the existing nomination process. In this context,
ADVANCED ANALYSIS is being done on a tactical matter related to the speci?c KNOWN or
SUSPECTED TERRORIST to identify information useful in ?connecting the dots? between and
among that KNOWN or SUSPECTED TERRORIST and other KNOWN or SUSPECTED or
potential KNOWN or SUSPECTED TERRORISTS. It is also when the need for foreign language
translation services will be identi?ed.
1 xIpuoddV
AGGREGATORS: are those who receive and hold TERRORISM INFORMATION and certain other
INFORMATION they are authorized to receive and retain.
DEROGATORY INFORMATION: is intelligence or information that demonstrates the nature of an
individual?s or group?s association with TERRORISM and/0r TERRORIST ACTIVITIES.
ENCOUNTER: is an event in which an individual is identified during a screening process to be a
or to an individual who has
been designated in the T803 as a KNOWN or SUSPECTED TERRORIST. An ENCOUNTER can be a
face-to-face meeting with a KNOWN or SUSPECTED TERRORIST, electronic or a paper-based
ENCOUNTER the KNOWN or SUSPECTED TERRORIST has submitted an application for a
bene?t liked a visa, ETSA grant, or information is provided to the United States by a foreign
government, aircraft operator, or other private entity).
ENCOUNTERING AGENCY: is a Department or Agency of the .8. Government with TERRORIST
screening or law enforcement responsibilities that comes into contact with a KNOWN or
SUSPECTED TERRORIST (whether in a face-to~face situation or via an electronic or written
submission such as an application for a bene?t) that the TSC determines is a POSITIVE MATCH tO
a KNOWN or SUSPECTED
ENCOUNTER PACKAGE: is all information gathered during an ENCOUNTER with a KNOWN or
SUSPECTED TERRORIST.
ENHANCEMENT: is the addition of new TERRORIST IDENTIFIERS or INFORMATION
on a KNOWN or TERRORIST.
FOREIGN FIGHTERS: are nationals of one country who travel or attempt to travel to another
country to participate in TERRORISM and/ or TERRORIST ACTIVITIES.
FRAGMENTARY INFORMATION: is information that suggests an individual may have a nexus to
TERRORISM and or TERRORIST ACTIVITIES but the information available to the NOMINATOR does
not meet either or both the minimum identifying criteria that will facilitate identi?cation of
these individuals or the substantive DEROGATORY INFORMATION to meet the REASONABLE
SUSPICION standard but does qualify as information that should be provided to NCTC pursuant
to
OR OFFICIAL USE SECURITY INFORMATION
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
A.
F.
G.
ADVANCED ANALYSIS: is a thorough review of the TERRORISM INFORMATION contained in an
ENCOUNTER PACKAGE obtained as a result of the ENCOUNTER with the KNOWN or SUSPECTED
TERRORIST. ADVANCED ANALYSIS includes the adding of TERRORIST IDENTIFIERS to existing
KNOWN or SUSPECTED TERRORIST records and identifying new KNOWN or SUSPECTED
TERRORISTS who should be nominated through the existing nomination process. In this context,
ADVANCED ANALYSIS is being done on a tactical matter related to the speci?c KNOWN or
SUSPECTED TERRORIST to identify information useful in ?connecting the dots? between and
among that KNOWN or SUSPECTED TERRORIST and other KNOWN or SUSPECTED or
potential KNOWN or SUSPECTED TERRORISTS. It is also when the need for foreign language
translation services will be identi?ed.
1 xIpuoddV
AGGREGATORS: are those who receive and hold TERRORISM INFORMATION and certain other
INFORMATION they are authorized to receive and retain.
DEROGATORY INFORMATION: is intelligence or information that demonstrates the nature of an
individual?s or group?s association with TERRORISM and/0r TERRORIST ACTIVITIES.
ENCOUNTER: is an event in which an individual is identified during a screening process to be a
or to an individual who has
been designated in the T803 as a KNOWN or SUSPECTED TERRORIST. An ENCOUNTER can be a
face-to-face meeting with a KNOWN or SUSPECTED TERRORIST, electronic or a paper-based
ENCOUNTER the KNOWN or SUSPECTED TERRORIST has submitted an application for a
bene?t liked a visa, ETSA grant, or information is provided to the United States by a foreign
government, aircraft operator, or other private entity).
ENCOUNTERING AGENCY: is a Department or Agency of the .8. Government with TERRORIST
screening or law enforcement responsibilities that comes into contact with a KNOWN or
SUSPECTED TERRORIST (whether in a face-to~face situation or via an electronic or written
submission such as an application for a bene?t) that the TSC determines is a POSITIVE MATCH tO
a KNOWN or SUSPECTED
ENCOUNTER PACKAGE: is all information gathered during an ENCOUNTER with a KNOWN or
SUSPECTED TERRORIST.
ENHANCEMENT: is the addition of new TERRORIST IDENTIFIERS or INFORMATION
on a KNOWN or TERRORIST.
FOREIGN FIGHTERS: are nationals of one country who travel or attempt to travel to another
country to participate in TERRORISM and/ or TERRORIST ACTIVITIES.
FRAGMENTARY INFORMATION: is information that suggests an individual may have a nexus to
TERRORISM and or TERRORIST ACTIVITIES but the information available to the NOMINATOR does
not meet either or both the minimum identifying criteria that will facilitate identi?cation of
these individuals or the substantive DEROGATORY INFORMATION to meet the REASONABLE
SUSPICION standard but does qualify as information that should be provided to NCTC pursuant
to
OR OFFICIAL USE SECURITY INFORMATION

UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
INCONCLUSIVE MATCH: is the ?nal determination by TSC that limited information in the subject
data set matches TSDB data in a TSDB record and no additional identi?ers are available to
verify the match.
1 xIpuaddV
. INITIAL REVIEW: is a quick primary review of the ENCOUNTER PACKAGE to identify obvious,
new TERRORIST IDENTIFIERS about the KNOWN or SUSPECTED
KNOWN TERRORIST: is an individual whom the US. Government knows is engaged, has been
engaged, or who intends to engage in TERRORISM and/or ACTIVITY, including an
individual who has been, charged, arrested, indicted, or convicted for a crime related to
TERRORISM by US. Government or foreign government authorities; or identi?ed as a
terrorist or member of a designated foreign terrorist organization pursuant to statute, Executive
Order or international legal obligation pursuant to a United Nations Security Council
Resolution.
. LONE WOLF: an individual motivated by one or more extremists ideologies, who operates alone
and supports, or engages in acts of violence in furtherance of that ideology or ideologies that
may involve direction, assistance, or influence from a larger terrorist organization of a foreign
actor.
NOMINATOR or NOMINATING DEPARTMENT OR AGENCY: is a Federal Department or Agency
that has information to indicate that an individual meets the criteria for a KNOWN or SUSPECTED
TERRORIST and nominates that individual to TIDE and the TSDB based on information that
originated with that Department or Agency and/or a third Department or Agency.
OPERATIONALLY CAPABLE: as described in Chapter 4, an individual is
if, based on credible intelligence, he or she, acting individually or in concert with
others, reasonably appears to have the ability, knowledge, opportunity, and intent or is actively
seeking the opportunity to engage in a violent act of TERRORISM consistent with 18 U.S.C. 2331
or 18 U.S.C. 2332b. For example, attempting to obtain an IED would indicate an individual is
CAPABLE of committing an act of TERRORISM. However, simply conducting
intemet research concerning lEDs would not be suf?cient without additional activity.
Depending on circumstances, and in combination with other facts, scouting potential targets or
traveling for no legitimate purpose to places that have TERRORIST training grounds, regardless of
whether the person is presently capable of using an IED, might also indicate an individual is
OPERATIONALLY CAPABLE of committing an act of TERRORISM.
ORIGINATOR: is the Department or Agency that has appropriate subject matter interest and
classification authority and collects TERRORISM INFORMATION raw information) and
disseminates it or TERRORIST IDENTIFIERS to other US. Government entities in an intelligence
report ?nished intelligence) or other mechanism.
PARTICULARIZED INFORMATION: is the type of information relied on to
determine whether REASONABLE SUSPICION is met. This is information that demonstrates the
nature of an individual?s or group?s association with TERRORISM and/or ACTIVITIES
UNCLASSIF OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
INCONCLUSIVE MATCH: is the ?nal determination by TSC that limited information in the subject
data set matches TSDB data in a TSDB record and no additional identi?ers are available to
verify the match.
1 xIpuaddV
. INITIAL REVIEW: is a quick primary review of the ENCOUNTER PACKAGE to identify obvious,
new TERRORIST IDENTIFIERS about the KNOWN or SUSPECTED
KNOWN TERRORIST: is an individual whom the US. Government knows is engaged, has been
engaged, or who intends to engage in TERRORISM and/or ACTIVITY, including an
individual who has been, charged, arrested, indicted, or convicted for a crime related to
TERRORISM by US. Government or foreign government authorities; or identi?ed as a
terrorist or member of a designated foreign terrorist organization pursuant to statute, Executive
Order or international legal obligation pursuant to a United Nations Security Council
Resolution.
. LONE WOLF: an individual motivated by one or more extremists ideologies, who operates alone
and supports, or engages in acts of violence in furtherance of that ideology or ideologies that
may involve direction, assistance, or influence from a larger terrorist organization of a foreign
actor.
NOMINATOR or NOMINATING DEPARTMENT OR AGENCY: is a Federal Department or Agency
that has information to indicate that an individual meets the criteria for a KNOWN or SUSPECTED
TERRORIST and nominates that individual to TIDE and the TSDB based on information that
originated with that Department or Agency and/or a third Department or Agency.
OPERATIONALLY CAPABLE: as described in Chapter 4, an individual is
if, based on credible intelligence, he or she, acting individually or in concert with
others, reasonably appears to have the ability, knowledge, opportunity, and intent or is actively
seeking the opportunity to engage in a violent act of TERRORISM consistent with 18 U.S.C. 2331
or 18 U.S.C. 2332b. For example, attempting to obtain an IED would indicate an individual is
CAPABLE of committing an act of TERRORISM. However, simply conducting
intemet research concerning lEDs would not be suf?cient without additional activity.
Depending on circumstances, and in combination with other facts, scouting potential targets or
traveling for no legitimate purpose to places that have TERRORIST training grounds, regardless of
whether the person is presently capable of using an IED, might also indicate an individual is
OPERATIONALLY CAPABLE of committing an act of TERRORISM.
ORIGINATOR: is the Department or Agency that has appropriate subject matter interest and
classification authority and collects TERRORISM INFORMATION raw information) and
disseminates it or TERRORIST IDENTIFIERS to other US. Government entities in an intelligence
report ?nished intelligence) or other mechanism.
PARTICULARIZED INFORMATION: is the type of information relied on to
determine whether REASONABLE SUSPICION is met. This is information that demonstrates the
nature of an individual?s or group?s association with TERRORISM and/or ACTIVITIES
UNCLASSIF OR OFFICIAL USE ON SITIVE SECURITY INFORMATION

OR OFFICIAL USE SECURITY INFORMATION
that is descriptive and speci?c to an event or activity, and is more than a label. For example,
?Subject provides false travel documentation for Al-Qaida Operatives? is PARTICULARIZED
whereas ?Subject is a supporter,? standing alone, is not
considered PARTICULARIZED DEROGATORY
xlpueddv
POSITIVE MATCH: occurs when the TSC determines that information about a subject
encountered by a SCREENER exactly or reasonably matches a record in the TSDB.
POTENTIAL MATCH: occurs when an ENCOUNTERING AGENCY believes it has a match with a
KNOWN or record in the TSDB. An ENCOUNTERING AGENCY may attempt
to resolve POTENTIAL MATCHES first through its review process. If an ENCOUNTERING
review process cannot resolve the individual?s status as not a match to a TSDB record, the
ENCOUNTERING AGENCY will refer the POTENTIAL MATCH to TSC for ?nal adjudication.
PURELY DOMESTIC TERRORISM INFORMATION: is de?ned in the TSC MOU as information
about U.S. PERSONS that has been determined to be PURELY DOMESTIC TERRORISM INFORMATION
with ?no link to foreign intelligence, or international
REASONABLE SUSPICION: is the standard that must be met in order to include an individual in
the TSDB, absent an exception provided for in the Watchlisting Guidance. To meet the
REASONABLE SUSPICION standard, the NOMINATOR, based on the totality of the circumstances,
must rely upon articulable intelligence or information which, taken together with rational
inferences from those facts, reasonably warrants a determination that an individual is known or
suspected to be or has been knowingly engaged in conduct constituting, in preparation for, in aid
of, or related to TERRORISM and/or TERRORIST ACTIVITIES. There must be an objective factual
basis for the NOMINATOR to believe that the individual is a KNOWN or SUSPECTED TERRORIST.
Mere guesses or hunches are not enough to constitute a REASONABLE SUSPICION that an
individual is a KNOWN or SUSPECTED Reporting of suspicious activity alone that
does not meet the REASONABLE SUSPICION standard set forth herein is not a suf?cient basis to
watchlist an individual. The facts, however, given fair consideration, should sensibly lead to the
conclusion that an individual is, or has, engaged in TERRORISM and/or ACTIVITIES.
SCREENER: a Department or Agency that is authorized to conduct TERRORISM screening to
determine if an individual is a possible match to a KNOWN or SUSPECTED TERRORIST in the
TSDB. SCREENERS can include Federal Departments or Agencies, state, local, tribal, territorial,
or foreign governments and certain private entities. The term is used throughout
this document as a general reference to a government official who compares an individual?s
information with information in the TSDB to determine if an individual is in the TSDB. Law
enforcement of?cials who engage in such activities may normally describe their targeting or
other actions in this context as other than "screening." For ease of reference, government
officials who compare an individual?s information with information in the TSDB will be
referred to in the Watchlisting Guidance as a
. SUSPECTED is an individual who is REASONABLY SUSPECTED to be, or has been
engaged in conduct constituting, in preparation for, in aid of, or related to TERRORISM and/or
TERRORIST ACTIVITIES based on an articulable and REASONABLE SUSPICION.
UN LASSIF OR OFFICIAL USE SECURITY INFORMATION
OR OFFICIAL USE SECURITY INFORMATION
that is descriptive and speci?c to an event or activity, and is more than a label. For example,
?Subject provides false travel documentation for Al-Qaida Operatives? is PARTICULARIZED
whereas ?Subject is a supporter,? standing alone, is not
considered PARTICULARIZED DEROGATORY
xlpueddv
POSITIVE MATCH: occurs when the TSC determines that information about a subject
encountered by a SCREENER exactly or reasonably matches a record in the TSDB.
POTENTIAL MATCH: occurs when an ENCOUNTERING AGENCY believes it has a match with a
KNOWN or record in the TSDB. An ENCOUNTERING AGENCY may attempt
to resolve POTENTIAL MATCHES first through its review process. If an ENCOUNTERING
review process cannot resolve the individual?s status as not a match to a TSDB record, the
ENCOUNTERING AGENCY will refer the POTENTIAL MATCH to TSC for ?nal adjudication.
PURELY DOMESTIC TERRORISM INFORMATION: is de?ned in the TSC MOU as information
about U.S. PERSONS that has been determined to be PURELY DOMESTIC TERRORISM INFORMATION
with ?no link to foreign intelligence, or international
REASONABLE SUSPICION: is the standard that must be met in order to include an individual in
the TSDB, absent an exception provided for in the Watchlisting Guidance. To meet the
REASONABLE SUSPICION standard, the NOMINATOR, based on the totality of the circumstances,
must rely upon articulable intelligence or information which, taken together with rational
inferences from those facts, reasonably warrants a determination that an individual is known or
suspected to be or has been knowingly engaged in conduct constituting, in preparation for, in aid
of, or related to TERRORISM and/or TERRORIST ACTIVITIES. There must be an objective factual
basis for the NOMINATOR to believe that the individual is a KNOWN or SUSPECTED TERRORIST.
Mere guesses or hunches are not enough to constitute a REASONABLE SUSPICION that an
individual is a KNOWN or SUSPECTED Reporting of suspicious activity alone that
does not meet the REASONABLE SUSPICION standard set forth herein is not a suf?cient basis to
watchlist an individual. The facts, however, given fair consideration, should sensibly lead to the
conclusion that an individual is, or has, engaged in TERRORISM and/or ACTIVITIES.
SCREENER: a Department or Agency that is authorized to conduct TERRORISM screening to
determine if an individual is a possible match to a KNOWN or SUSPECTED TERRORIST in the
TSDB. SCREENERS can include Federal Departments or Agencies, state, local, tribal, territorial,
or foreign governments and certain private entities. The term is used throughout
this document as a general reference to a government official who compares an individual?s
information with information in the TSDB to determine if an individual is in the TSDB. Law
enforcement of?cials who engage in such activities may normally describe their targeting or
other actions in this context as other than "screening." For ease of reference, government
officials who compare an individual?s information with information in the TSDB will be
referred to in the Watchlisting Guidance as a
. SUSPECTED is an individual who is REASONABLY SUSPECTED to be, or has been
engaged in conduct constituting, in preparation for, in aid of, or related to TERRORISM and/or
TERRORIST ACTIVITIES based on an articulable and REASONABLE SUSPICION.
UN LASSIF OR OFFICIAL USE SECURITY INFORMATION

OR OFFICIAL USE SECURITY INFORMATION
X. TARGETED ANALYSIS: is further exploitation of a targeted set of ENCOUNTER PACKAGES and
ADVANCED ANALYSIS products to assist in identifying TERRORIST trends and changes to methods,
tactics, and practices. ENCOUNTERS for TARGETED ANALYSIS are selected using
contemporaneous threat criteria, and research in additional repositories. Contemporaneous
threat criteria include association with a priority terrorist group NIPF Tier I or
ENCOUNTERS with KNOWN or SUSPECTED TERRORISTS designated as No Fly or associated with
violent activity; or at the request of any Department or Agency that identi?es a need.
1 xIpuaddV
Y. TERRORISM TERRORIST ACTIVITIES: is a combination of de?nitions because none of
the federal law definitions of ?terrorism? or ?terrorist activities? were directly applicable to the
consolidated approach to watchlisting. For terrorist watchlisting purposes under this
Watchlisting Guidance, ?terrorism and/or terrorist activities? combine elements from various
federal definitions and are considered to: involve violent acts or acts dangerous to human
life, property, or infrastructure that may be a violation of U.S. law, or may have been, if those
acts were committed in the United States; and, appear intended to intimidate or coerce a
civilian population, in?uence the policy of a government by intimidation or coercion, or affect
the conduct of government by mass destruction, assassination, kidnapping, or hostage-taking.
This includes activities that facilitate or support TERRORISM and/or TERRORIST ACTIVITIES, such
as providing a safe house, transportation, communications, funds, transfer of funds or other
material bene?t, false documentation or identi?cation, weapons (including chemical, biological,
or radiological weapons), explosives, or training for the commission of act of terrorism and/or
TERRORIST ACTIVITY.
Z. TERRORISM INFORMATION: applies, where appropriate, to purely domestic terrorism as de?ned
in the TSC MOU and incorporates the de?nition found in in section l0 6 of the IRTPA (6
U.S.C. 485), as amended. The term means
1. all information, whether collected, produced, or distributed by intelligence, law
enforcement, military, homeland security, or other activities relating to~~
a) the existence, organization, capabilities, plans, intentions, vulnerabilities,
means of ?nance or material support, or activities of foreign or
international terrorist groups or individuals, or of domestic groups or
individuals involved in transnational
b) threats posed by such groups or individuals to the United States, .S.
PERSONS, or United States interests, or to those of other nations;
c) communications of or by such groups or individuals; or
d) groups or individuals reasonably believed to be assisting or associated with
such groups or individuals; and
2. includes weapons of mass destruction information.
a) Weapons of Mass Destruction Information: information that could
reasonably be expected to assist in the development, proliferation, or use of
a weapon of mass destruction (including a chemical, biological,
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
OR OFFICIAL USE SECURITY INFORMATION
X. TARGETED ANALYSIS: is further exploitation of a targeted set of ENCOUNTER PACKAGES and
ADVANCED ANALYSIS products to assist in identifying TERRORIST trends and changes to methods,
tactics, and practices. ENCOUNTERS for TARGETED ANALYSIS are selected using
contemporaneous threat criteria, and research in additional repositories. Contemporaneous
threat criteria include association with a priority terrorist group NIPF Tier I or
ENCOUNTERS with KNOWN or SUSPECTED TERRORISTS designated as No Fly or associated with
violent activity; or at the request of any Department or Agency that identi?es a need.
1 xIpuaddV
Y. TERRORISM TERRORIST ACTIVITIES: is a combination of de?nitions because none of
the federal law definitions of ?terrorism? or ?terrorist activities? were directly applicable to the
consolidated approach to watchlisting. For terrorist watchlisting purposes under this
Watchlisting Guidance, ?terrorism and/or terrorist activities? combine elements from various
federal definitions and are considered to: involve violent acts or acts dangerous to human
life, property, or infrastructure that may be a violation of U.S. law, or may have been, if those
acts were committed in the United States; and, appear intended to intimidate or coerce a
civilian population, in?uence the policy of a government by intimidation or coercion, or affect
the conduct of government by mass destruction, assassination, kidnapping, or hostage-taking.
This includes activities that facilitate or support TERRORISM and/or TERRORIST ACTIVITIES, such
as providing a safe house, transportation, communications, funds, transfer of funds or other
material bene?t, false documentation or identi?cation, weapons (including chemical, biological,
or radiological weapons), explosives, or training for the commission of act of terrorism and/or
TERRORIST ACTIVITY.
Z. TERRORISM INFORMATION: applies, where appropriate, to purely domestic terrorism as de?ned
in the TSC MOU and incorporates the de?nition found in in section l0 6 of the IRTPA (6
U.S.C. 485), as amended. The term means
1. all information, whether collected, produced, or distributed by intelligence, law
enforcement, military, homeland security, or other activities relating to~~
a) the existence, organization, capabilities, plans, intentions, vulnerabilities,
means of ?nance or material support, or activities of foreign or
international terrorist groups or individuals, or of domestic groups or
individuals involved in transnational
b) threats posed by such groups or individuals to the United States, .S.
PERSONS, or United States interests, or to those of other nations;
c) communications of or by such groups or individuals; or
d) groups or individuals reasonably believed to be assisting or associated with
such groups or individuals; and
2. includes weapons of mass destruction information.
a) Weapons of Mass Destruction Information: information that could
reasonably be expected to assist in the development, proliferation, or use of
a weapon of mass destruction (including a chemical, biological,
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION

OFFICIAL USE SECURITY INFORMATION
AA.
BB.
CC
DD.
EE.
radiological, or nuclear weapon) that could be used by a TERRORIST or a
terrorist organization against the United States, including information about
the location of any stockpile Of nuclear materials that could be exploited for
use in such a weapon that could be used by a or a terrorist
organization against the United States.
I xIpuaddv
TERRORISM SCREENING INFORMATION: is de?ned in the standard HSPD-6 agreement to
mean unclassi?ed identifying information about KNOWN or
please see KNOWN TERRORIST or TERRORIST.
IDENTIFIERS: are referred to in the TSC MOU as data for inclusion
into the TSDB. TERRORIST IDENTIFIERS are data points about a particular identity that include
names and aliases, dates Of birth, places of birth, unique identifying numbers, passport
information, country of origin and nationality, physical identi?ers, addresses, photographs or
renderings of the individual, ?ngerprints or other biometric data, employment data, license plate
numbers, and any other TERRORISM INFORMATION that ORIGINATORS speci?cally provide for
passage to the SC.
TERRORIST INFORMATION: as de?ned in HSPD-6 is ?information about individuals known
or appropriately suspected to be or have been engaged in conduct constituting, in preparation
for, in aid of, or related to
U.S. PERSON: is de?ned in Executive Order 12333 (as amended) as ?a United States citizen,
an alien known by the intelligence element concerned to be a permanent resident alien, an
unincorporated association substantially composed of United States citizens or permanent
resident aliens, or a corporation incorporated in the United States, except for a corporation
directed and controlled by a foreign government or governments.? The Watchlisting Guidance
contains certain exceptions to the minimum substantive derogatory standards for TERRORIST
watchlisting that support immigration and visa screening activities by the DHS and DOS to
determine whether ineligibilities exist for admission to the United States or visa adjudication
pursuant to the INA. Because the INA de?nes ?aliens? as any person not a citizen or national of
the United States, the INA admissibility provisions also apply to LPRS, in certain circumstances,
who are considered as U.S. PERSONS under Executive Order 12333. Consequently,
developed a mechanism in TIDE to identify and distinguish U.S. citizens from non-U.S. citizens
in order to further distinguish between ?aliens? under the INA and U.S. PERSONS under
Executive Order 12333. See INA [8 U.S.C.
OR OFFICIAL USE SECURITY INFORMATION
OFFICIAL USE SECURITY INFORMATION
AA.
BB.
CC
DD.
EE.
radiological, or nuclear weapon) that could be used by a TERRORIST or a
terrorist organization against the United States, including information about
the location of any stockpile Of nuclear materials that could be exploited for
use in such a weapon that could be used by a or a terrorist
organization against the United States.
I xIpuaddv
TERRORISM SCREENING INFORMATION: is de?ned in the standard HSPD-6 agreement to
mean unclassi?ed identifying information about KNOWN or
please see KNOWN TERRORIST or TERRORIST.
IDENTIFIERS: are referred to in the TSC MOU as data for inclusion
into the TSDB. TERRORIST IDENTIFIERS are data points about a particular identity that include
names and aliases, dates Of birth, places of birth, unique identifying numbers, passport
information, country of origin and nationality, physical identi?ers, addresses, photographs or
renderings of the individual, ?ngerprints or other biometric data, employment data, license plate
numbers, and any other TERRORISM INFORMATION that ORIGINATORS speci?cally provide for
passage to the SC.
TERRORIST INFORMATION: as de?ned in HSPD-6 is ?information about individuals known
or appropriately suspected to be or have been engaged in conduct constituting, in preparation
for, in aid of, or related to
U.S. PERSON: is de?ned in Executive Order 12333 (as amended) as ?a United States citizen,
an alien known by the intelligence element concerned to be a permanent resident alien, an
unincorporated association substantially composed of United States citizens or permanent
resident aliens, or a corporation incorporated in the United States, except for a corporation
directed and controlled by a foreign government or governments.? The Watchlisting Guidance
contains certain exceptions to the minimum substantive derogatory standards for TERRORIST
watchlisting that support immigration and visa screening activities by the DHS and DOS to
determine whether ineligibilities exist for admission to the United States or visa adjudication
pursuant to the INA. Because the INA de?nes ?aliens? as any person not a citizen or national of
the United States, the INA admissibility provisions also apply to LPRS, in certain circumstances,
who are considered as U.S. PERSONS under Executive Order 12333. Consequently,
developed a mechanism in TIDE to identify and distinguish U.S. citizens from non-U.S. citizens
in order to further distinguish between ?aliens? under the INA and U.S. PERSONS under
Executive Order 12333. See INA [8 U.S.C.
OR OFFICIAL USE SECURITY INFORMATION

xipuaddv
For Immediate Release
Office of the Press Secretary
September 18. 2003
Homeland Security Presidential Directivelepd-B
Subject: Integration and Use of Screening Information
To protect against terrorism it is the policy of the United States to (1) develop. integrate. and maintain
thorough. accurate. and current information abOut individuals known or appropriately suspected to be Or
have been engaged in conduct constituting. in preparation for. in aid of. or related to terrorism (Terrorist
information); and (2) use that information as appropriate and to the full extent permitted by law to support
Federal. State. local. territorial. tribal. foreign-government. and private-sector screening processes.
and diplomatic. military. intelligence. law enforcement. immigration. visa. and protective processes.
This directive shall be implemented in a manner consistent with the provisions of the Constitution and
applicable laws. including those protecting the rights of all Americans.
To further strengthen the ability of the United States Government to protect the people. property. and
territory of the United States against acts of terrorism. and to the full extent permitted by law and
consistent with the policy set forth above:
(1) The Attorney General shall establish an organization to consolidate the Government's approach to
terronsm screening and provide for the appropriate and lawful use of Terrorist information in screening
processes.
The heads of executive departments and agencies shall, to the extent permitted by law. prowde to the
Terrorist Threat Integration Center (TTIC) on an ongorng basis all appropriate Terrorist information in their
possession. custody. or control. The Attorney General, in coordination with the Secretary of State. the
Secretary of Homeland Security. and the Director of Central Intelligence shall implement apprOpriate
procedures and safeguards with respect to all such information about United States persons. The T'l'lC
will provide the organization referenced in paragraph (1) with access to all appropriate information or
intelligence in the TTIC's custody. possession, or control that the organization requires to perform its
functions.
(3) The heads of executive departments and agencies shall conduct screening using such information at
all appropriate opportunities. and shall report to the Attorney General not later than 90 days from the date
of this directive. as to the opportunities at which such screening shall and shall not be conducted.
(4) The Secretary of Homeland Security shall develop guidelines to govern the use of such information to
support State. local. territorial. and tribal screening processes. and private sector screening processes
that have a substantial bearing on homeland security.
(5) The Secretary of State shall develop a proposal for my approval for enhancing cooperation with
certain foreign governments. beginning with those countries for which the United States has waived visa
requirements. to establish appropriate access to terrorism screening information of the participating
governments.
This directive does not alter existing authorities 0r responsibilities of department and agency heads to
carry out operational activrties or provrde or receive information This directive is intended only to improve
the internal management of the executive branch and IS not intended to. and does not. create any right or
Page I of 2
xipuaddv
For Immediate Release
Office of the Press Secretary
September 18. 2003
Homeland Security Presidential Directivelepd-B
Subject: Integration and Use of Screening Information
To protect against terrorism it is the policy of the United States to (1) develop. integrate. and maintain
thorough. accurate. and current information abOut individuals known or appropriately suspected to be Or
have been engaged in conduct constituting. in preparation for. in aid of. or related to terrorism (Terrorist
information); and (2) use that information as appropriate and to the full extent permitted by law to support
Federal. State. local. territorial. tribal. foreign-government. and private-sector screening processes.
and diplomatic. military. intelligence. law enforcement. immigration. visa. and protective processes.
This directive shall be implemented in a manner consistent with the provisions of the Constitution and
applicable laws. including those protecting the rights of all Americans.
To further strengthen the ability of the United States Government to protect the people. property. and
territory of the United States against acts of terrorism. and to the full extent permitted by law and
consistent with the policy set forth above:
(1) The Attorney General shall establish an organization to consolidate the Government's approach to
terronsm screening and provide for the appropriate and lawful use of Terrorist information in screening
processes.
The heads of executive departments and agencies shall, to the extent permitted by law. prowde to the
Terrorist Threat Integration Center (TTIC) on an ongorng basis all appropriate Terrorist information in their
possession. custody. or control. The Attorney General, in coordination with the Secretary of State. the
Secretary of Homeland Security. and the Director of Central Intelligence shall implement apprOpriate
procedures and safeguards with respect to all such information about United States persons. The T'l'lC
will provide the organization referenced in paragraph (1) with access to all appropriate information or
intelligence in the TTIC's custody. possession, or control that the organization requires to perform its
functions.
(3) The heads of executive departments and agencies shall conduct screening using such information at
all appropriate opportunities. and shall report to the Attorney General not later than 90 days from the date
of this directive. as to the opportunities at which such screening shall and shall not be conducted.
(4) The Secretary of Homeland Security shall develop guidelines to govern the use of such information to
support State. local. territorial. and tribal screening processes. and private sector screening processes
that have a substantial bearing on homeland security.
(5) The Secretary of State shall develop a proposal for my approval for enhancing cooperation with
certain foreign governments. beginning with those countries for which the United States has waived visa
requirements. to establish appropriate access to terrorism screening information of the participating
governments.
This directive does not alter existing authorities 0r responsibilities of department and agency heads to
carry out operational activrties or provrde or receive information This directive is intended only to improve
the internal management of the executive branch and IS not intended to. and does not. create any right or
Page I of 2

bene?t enforceable at law or in equity by any party against the United States. its departments. agencies.
entities. of?cers. emoloyees 0r agents. or any other person.
The Attorney General, in consultation with the Secretary of State. the Secretary of Homeland Security,
and the Director of Central Intelligence. shall report to me through the Assistant to the President for
Homeland Security not later than October 31. 2003. on progress made to implement this directive and
shall thereafter report to me on such progress or any recommended changes from time to time as
appropriate.
3 xtpuaddv
GEORGE BUSH
Page 2 of 2
bene?t enforceable at law or in equity by any party against the United States. its departments. agencies.
entities. of?cers. emoloyees 0r agents. or any other person.
The Attorney General, in consultation with the Secretary of State. the Secretary of Homeland Security,
and the Director of Central Intelligence. shall report to me through the Assistant to the President for
Homeland Security not later than October 31. 2003. on progress made to implement this directive and
shall thereafter report to me on such progress or any recommended changes from time to time as
appropriate.
3 xtpuaddv
GEORGE BUSH
Page 2 of 2

THE SECRETARY OF STATE
THE ATTORNEY GENERAL
THE SECRETARY OF HOMELAND SECURITY
THE DIRECTOR OF CENTRAL INTELLIGENCE
xtpuaddv
MEMORANDUM OF UNDERSTANDING
ON THE INTEGRATION AND USE OF SCREENING INFORMATION
TO PROTECT AGAINST TERRORISM
(I) This memorandum represents the consensus view of the Secretary of State, the Attorney
General, the Secretary of Homeland Security. and the Director of Central lntelligenceregarding
the implementation of" Homeland Security Presidential Directive-6 (HSPD-G), dated
September l6. 2003, entitled ?Integration and Use of Screening Information to Protect Against
Terrorism." (U)
(2) Consistent with the President?s direction. the Parties to this MemOrandum will develop and
maintain. to the extent permitted by law, the most thorough, accurate, and current information
possible about individuals known or appropriately suSpected to be or have been involved in
activities constituting, in preparation f0r, in aid of, or related to terrorism ("Terrorist
Information"), and will, as described in this Memorandum:
use that information to support screening processes at all appropriate opportunities;
make accessible appropriate information to State. local. territorial, and tribal authorities to
support their Screening processes and otherwise enable them to identify, or assist in identifying,
such individuals;
host mechanisms. to the extent permitted by law. to support appropriate private sector
screening processes that have a substantial bearing on homeland security;
host mechanisms, to the extent permitted by law, to suppon appropriate foreign government
screening processes that have a substantial bearing on hemeland security;
provide 01' make accessible appropriate information to foreign governments cOOperating with
the United States in the war on terrorists of global reach; and
(0 ensure that these activities are carried out in a manner consistent with the Constitution and
applicable laws. (U)
Page i of 8
THE SECRETARY OF STATE
THE ATTORNEY GENERAL
THE SECRETARY OF HOMELAND SECURITY
THE DIRECTOR OF CENTRAL INTELLIGENCE
xtpuaddv
MEMORANDUM OF UNDERSTANDING
ON THE INTEGRATION AND USE OF SCREENING INFORMATION
TO PROTECT AGAINST TERRORISM
(I) This memorandum represents the consensus view of the Secretary of State, the Attorney
General, the Secretary of Homeland Security. and the Director of Central lntelligenceregarding
the implementation of" Homeland Security Presidential Directive-6 (HSPD-G), dated
September l6. 2003, entitled ?Integration and Use of Screening Information to Protect Against
Terrorism." (U)
(2) Consistent with the President?s direction. the Parties to this MemOrandum will develop and
maintain. to the extent permitted by law, the most thorough, accurate, and current information
possible about individuals known or appropriately suSpected to be or have been involved in
activities constituting, in preparation f0r, in aid of, or related to terrorism ("Terrorist
Information"), and will, as described in this Memorandum:
use that information to support screening processes at all appropriate opportunities;
make accessible appropriate information to State. local. territorial, and tribal authorities to
support their Screening processes and otherwise enable them to identify, or assist in identifying,
such individuals;
host mechanisms. to the extent permitted by law. to support appropriate private sector
screening processes that have a substantial bearing on homeland security;
host mechanisms, to the extent permitted by law, to suppon appropriate foreign government
screening processes that have a substantial bearing on hemeland security;
provide 01' make accessible appropriate information to foreign governments cOOperating with
the United States in the war on terrorists of global reach; and
(0 ensure that these activities are carried out in a manner consistent with the Constitution and
applicable laws. (U)
Page i of 8

Terrorist Screening Center
-, (3) To implement the President's directive, the Attorney General, acting through the Director of
the FBI, and in coordination with the Secretary of State, the Secretary of Homeland Security, and
the Director of Central Intelligence, will establish the Terrorist Screening Center to consolidate
the Government?s approach to terrorism screening and provide for the appropriate and lawful use
of Terrorist information, in screening processes. (U)
xtpuaddv
(4) The Terrorist Screening Center will:
maintain a consolidated terrorist screening database that is a continuously updated, sensitive
but unclassi?ed subset of the TerrOnst lnfonnation possessed by the and the Pure]
Domestic Terrorism lnformation information about US. persons that has been determined
to be purely domestic terrorism information with no link to foreign intelligence.
counterintelligence, or international terrorism) possessed by the
determine, for each entry in the consolidated terrorist screening database, which supported
screening processes shall query that entry, as described in paragraphs (15) through
ensure, consistent with applicable law, that appropriate information possessed by State, local,
territorial, and tribal governments, which is available to the Federal government, is considered in
determinations made by the Terrorist Screening Center;
host mechanisms to support appropriate screening processes; and
provide continual operational support to assist in the identi?cation of persons screened and.
when an individual known or suspected to be involved in activities constituting, in
preparation for, in aid of, or related to terrorism, has been identi?ed through a screening process.
facilitate, to the extent pemiirted by law, appropriate and lanul actions to be taken by
appropriate departments and agencies. (U)
(S) The Terrorist Screening Center will be headed by a senior US. Government of?cial (the
Director of the Terrorist Screening Center), who will report to the Attorney General through the
Director of the FBI. The Director of the Terrori5t Screening Center will be appointed by the
Attorney General, in consultation with the Secretary of Homeland Security, the Secretary of
State, the Director of the FBI, and the Director of Central intelligence. The Principal Deputy
Director of the Terrorist Screening Center will be a senior official from the Department of
Homeland Security. (U)
(6) The Terronst Screening Center will be staffed with assignees and other of?cials from the
Department of State, the Department of Justice, the Depanment of Homeland Security, and other
Federal departments and agencies that the Terrorist Screening Center supports. The Director of
Central Intelligence, acting in his capacity as statutory head of the intelligence Community. may
Page 2 of8
Terrorist Screening Center
-, (3) To implement the President's directive, the Attorney General, acting through the Director of
the FBI, and in coordination with the Secretary of State, the Secretary of Homeland Security, and
the Director of Central Intelligence, will establish the Terrorist Screening Center to consolidate
the Government?s approach to terrorism screening and provide for the appropriate and lawful use
of Terrorist information, in screening processes. (U)
xtpuaddv
(4) The Terrorist Screening Center will:
maintain a consolidated terrorist screening database that is a continuously updated, sensitive
but unclassi?ed subset of the TerrOnst lnfonnation possessed by the and the Pure]
Domestic Terrorism lnformation information about US. persons that has been determined
to be purely domestic terrorism information with no link to foreign intelligence.
counterintelligence, or international terrorism) possessed by the
determine, for each entry in the consolidated terrorist screening database, which supported
screening processes shall query that entry, as described in paragraphs (15) through
ensure, consistent with applicable law, that appropriate information possessed by State, local,
territorial, and tribal governments, which is available to the Federal government, is considered in
determinations made by the Terrorist Screening Center;
host mechanisms to support appropriate screening processes; and
provide continual operational support to assist in the identi?cation of persons screened and.
when an individual known or suspected to be involved in activities constituting, in
preparation for, in aid of, or related to terrorism, has been identi?ed through a screening process.
facilitate, to the extent pemiirted by law, appropriate and lanul actions to be taken by
appropriate departments and agencies. (U)
(S) The Terrorist Screening Center will be headed by a senior US. Government of?cial (the
Director of the Terrorist Screening Center), who will report to the Attorney General through the
Director of the FBI. The Director of the Terrori5t Screening Center will be appointed by the
Attorney General, in consultation with the Secretary of Homeland Security, the Secretary of
State, the Director of the FBI, and the Director of Central intelligence. The Principal Deputy
Director of the Terrorist Screening Center will be a senior official from the Department of
Homeland Security. (U)
(6) The Terronst Screening Center will be staffed with assignees and other of?cials from the
Department of State, the Department of Justice, the Depanment of Homeland Security, and other
Federal departments and agencies that the Terrorist Screening Center supports. The Director of
Central Intelligence, acting in his capacity as statutory head of the intelligence Community. may
Page 2 of8

also determine that assignees of other appropriate agencies. within the Intelligence Community,
will he made available to perform appropriate duties at the Terrorist Screening Center. (U)
(7) Personnel assigned to the TerroriSt Screening Center will have appropriate access to the TTIC
database and any relevant intelligence information necessary to perform the Terrorist Screening
Center?s functions. To the extent required by law, the Parties to this Memorandum may jointly
determine the circumstances under which personnel from the intelligence Community, assigned
to the Terrorist Screening Center in accordance with paragraph (6), may participate in the
Functions of the Terrorist Screening Center relating to US. persons. (U)
5 xtpuaddv
(8) The Director of the Terrorist Screening Center will establish necessary precedures and
safeguards to ensure the Terrorist Screening Center's functions are carried out in a manner
consistent with the Constitution and applicable laws, including, but not limited to, procedures to:
address the repeated misidenti?cation of persons in any Government screening process;
regularly review information, and to adjust or delete erroneous or outdated
information; and
protect personal privacy. (U)
(9) Consistent with the President?s directive. the Secretary of State, in consultation with the
Secretary of Homeland Security. the Attorney General, and the DirectOr of Central Intelligence,
and working with the Director of the Terrorist Screening Center, not later than 180 days from
today, will recommend to the President through the Assistant to the President for Homeland
Security and the Assistant to the President for National Security Affairs, a proposal for
cooperating with certain foreign governments (beginning with those countries f0r which the
United States has waived visa requirements) to establish appropriate access to terrorist screening
information of the participating govemments, in a manner consistent with each government's
laws, and to provide Operational support to the participating governments. (U)
Terrorist Threat Integration Center (11? 1C) Identities Database
(10) The database will include, to the extent permitted by law. all information the U.S.
government possesses related to the identities of individuals known or appropriately suspected to
be or have been involved in activities constituting, in preparation for, in aid of. or related to
terrorism, with the exception of Purely Domestic Terrorism Information. (U)
(l 1) As directed by the President, and to the extent permitted by law, Federal departments and
agencies will provide to the on an ongoing basis all relevant Terrorist information in their
possession, custody. or control, with the exception of Purely Domestic Terrorism Information.
which will instead be provided directly to the FBI. Departments and agencies will continue to
Page 3 of 8
also determine that assignees of other appropriate agencies. within the Intelligence Community,
will he made available to perform appropriate duties at the Terrorist Screening Center. (U)
(7) Personnel assigned to the TerroriSt Screening Center will have appropriate access to the TTIC
database and any relevant intelligence information necessary to perform the Terrorist Screening
Center?s functions. To the extent required by law, the Parties to this Memorandum may jointly
determine the circumstances under which personnel from the intelligence Community, assigned
to the Terrorist Screening Center in accordance with paragraph (6), may participate in the
Functions of the Terrorist Screening Center relating to US. persons. (U)
5 xtpuaddv
(8) The Director of the Terrorist Screening Center will establish necessary precedures and
safeguards to ensure the Terrorist Screening Center's functions are carried out in a manner
consistent with the Constitution and applicable laws, including, but not limited to, procedures to:
address the repeated misidenti?cation of persons in any Government screening process;
regularly review information, and to adjust or delete erroneous or outdated
information; and
protect personal privacy. (U)
(9) Consistent with the President?s directive. the Secretary of State, in consultation with the
Secretary of Homeland Security. the Attorney General, and the DirectOr of Central Intelligence,
and working with the Director of the Terrorist Screening Center, not later than 180 days from
today, will recommend to the President through the Assistant to the President for Homeland
Security and the Assistant to the President for National Security Affairs, a proposal for
cooperating with certain foreign governments (beginning with those countries f0r which the
United States has waived visa requirements) to establish appropriate access to terrorist screening
information of the participating govemments, in a manner consistent with each government's
laws, and to provide Operational support to the participating governments. (U)
Terrorist Threat Integration Center (11? 1C) Identities Database
(10) The database will include, to the extent permitted by law. all information the U.S.
government possesses related to the identities of individuals known or appropriately suspected to
be or have been involved in activities constituting, in preparation for, in aid of. or related to
terrorism, with the exception of Purely Domestic Terrorism Information. (U)
(l 1) As directed by the President, and to the extent permitted by law, Federal departments and
agencies will provide to the on an ongoing basis all relevant Terrorist information in their
possession, custody. or control, with the exception of Purely Domestic Terrorism Information.
which will instead be provided directly to the FBI. Departments and agencies will continue to
Page 3 of 8

provide new or updated information, and adjust or retract information as needed, in as near to
real-time as possible. To this end, the Parties to this Memorandum will automate, to the
maximum extent possible while providing for necessary review, their processes and mechanisms
for securely sharing this information. including, but not limited to, the following:
xtpuaddv
The Secretary of State, the Attorney General, the Secretary of Homeland Security, and the
Director of Central intelligence, in coordination with other relevant department and agency
heads, not later than 180 days from today, willjointly recommend to the President through the
Assistant to the President for Homeland Security, in consultation with the Assistant to the
President for National Security Affairs, improvements, if any, to the existing cable-based system
of sharing terrorism-related information with other departments and agencies.
The Attorney General will ensure that the FBI's information technology modernization
programs incorporate automated means of sharing appropriate information with the 'lTlC and
other departments and agencies, while providing for necessary review, in near realztime. (U)
(l2) The TTIC identities database, and the Bi?s database containing Purely Domestic Terrorism
Information, will incorporate, to the extent permitted by law, available biometric data, including
data on persons who even if otherwise unidenti?ed are known or appropriately suSpected to be or
have been involved in activities constituting, in preparation for, in aid of, or related to terrorism.
The databases will have the capability of periodically incomorating advancements in biometric
technology. (U)
Relationship of the TTIC and FBI Databases to the Terrorist Screening Center Terrorist
Screening Database
(13) The identities database will serve, with the exception described in paragraph (10), as
the single source for the Terrorist Screening Center terrorist screening database. The Director of
the FBI will serve as the source for the Terrorist Screening Center terrorist screening database
with regard to Purely Domestic TerroriSm Information. The Terrorist Screening Center terrorist
sereening database will be a continuously updated, sensitive but unclassi?ed subset of the
Terrorist Information possessed by the TTIC, and the Purely Domestic Terrorism lnfonnatiOn
possessed by the FBI. (U)
Terrorist Screening Center Terrorist Screening Database
(M) The Director of the Tl'lC, the Director of the Terrorist Screening Center, and the heads of
Federal departments and agencies, or their designees, may nominate persons for inclusion in the
tenon'St screening database, with noti?cation, as appropriate, to the Director of the and/or
the Director of the FBI. (U)
Page 4 of 8
provide new or updated information, and adjust or retract information as needed, in as near to
real-time as possible. To this end, the Parties to this Memorandum will automate, to the
maximum extent possible while providing for necessary review, their processes and mechanisms
for securely sharing this information. including, but not limited to, the following:
xtpuaddv
The Secretary of State, the Attorney General, the Secretary of Homeland Security, and the
Director of Central intelligence, in coordination with other relevant department and agency
heads, not later than 180 days from today, willjointly recommend to the President through the
Assistant to the President for Homeland Security, in consultation with the Assistant to the
President for National Security Affairs, improvements, if any, to the existing cable-based system
of sharing terrorism-related information with other departments and agencies.
The Attorney General will ensure that the FBI's information technology modernization
programs incorporate automated means of sharing appropriate information with the 'lTlC and
other departments and agencies, while providing for necessary review, in near realztime. (U)
(l2) The TTIC identities database, and the Bi?s database containing Purely Domestic Terrorism
Information, will incorporate, to the extent permitted by law, available biometric data, including
data on persons who even if otherwise unidenti?ed are known or appropriately suSpected to be or
have been involved in activities constituting, in preparation for, in aid of, or related to terrorism.
The databases will have the capability of periodically incomorating advancements in biometric
technology. (U)
Relationship of the TTIC and FBI Databases to the Terrorist Screening Center Terrorist
Screening Database
(13) The identities database will serve, with the exception described in paragraph (10), as
the single source for the Terrorist Screening Center terrorist screening database. The Director of
the FBI will serve as the source for the Terrorist Screening Center terrorist screening database
with regard to Purely Domestic TerroriSm Information. The Terrorist Screening Center terrorist
sereening database will be a continuously updated, sensitive but unclassi?ed subset of the
Terrorist Information possessed by the TTIC, and the Purely Domestic Terrorism lnfonnatiOn
possessed by the FBI. (U)
Terrorist Screening Center Terrorist Screening Database
(M) The Director of the Tl'lC, the Director of the Terrorist Screening Center, and the heads of
Federal departments and agencies, or their designees, may nominate persons for inclusion in the
tenon'St screening database, with noti?cation, as appropriate, to the Director of the and/or
the Director of the FBI. (U)
Page 4 of 8

(IS) The Terrorist Screening Center will determine, according to criteria established jointly with
the entity responsible for each supported screening process, which supported screening processes
will query that entry in the consolidated terrorist screening database. The Terrorist Screening
Center will make these determinations based on criteria and procedures developed in
coordination with the Parties to this Memorandum and in consultation with the heads of
appropriate Federal departments and agencies, based on factors including, but not limited to, the
following:
5 xipuoddv
the nature of the person's association with terrorism;
the quality of the data, including credibility, reliability, and extent of corroboration;
the extent of uniquely identifying data;
the authority or authorities under which the data was obtained, and any restrictions on how it
may be shared or used;
the authority or authorities of the screening entity;
(1) the circumstances, including changes in the Homeland Security Alert Level, under which
screening will occur; and
the action the screening entity will take if a person is identi?ed as a person in the terrorist
screening database. (U)
6) The Director of the Terrorist Screening Center, in coordination with the Parties to this
Memorandum and in consultation with the heads of appropriate Federal departments and
agencies, will establish procedures to review the continued inclusion of a person in the terrorist
screening database, and to review the inclusion of that person in particular screening processes as
described in paragraph (1 5) above. whenever new information about that person is developed.
(U)
(l 7) Except upon written direction ?'om the President, determinations to include US. persons in
the terrorist screening database based solely on information concerning the domestic activities of
such persons will be made as by the Secretary of State. the Attorney General, and the
Secretary of Homeland Security, or their designees. (U)
(18) The Attorney General. aeting through the Director of the Terrorist Screening Center, will
review each nomination and determine whether to include that person in those records that can
be queried by law enforcement authorities through the NCIC database; for aliens, the Attorney
General will do so in consultation with the Secretary of Homeland Security, acting though the
Secretary of Homeland Seourity?s representative assigned to the Terrorist Screening Center. (U)
Page 5 of8
(IS) The Terrorist Screening Center will determine, according to criteria established jointly with
the entity responsible for each supported screening process, which supported screening processes
will query that entry in the consolidated terrorist screening database. The Terrorist Screening
Center will make these determinations based on criteria and procedures developed in
coordination with the Parties to this Memorandum and in consultation with the heads of
appropriate Federal departments and agencies, based on factors including, but not limited to, the
following:
5 xipuoddv
the nature of the person's association with terrorism;
the quality of the data, including credibility, reliability, and extent of corroboration;
the extent of uniquely identifying data;
the authority or authorities under which the data was obtained, and any restrictions on how it
may be shared or used;
the authority or authorities of the screening entity;
(1) the circumstances, including changes in the Homeland Security Alert Level, under which
screening will occur; and
the action the screening entity will take if a person is identi?ed as a person in the terrorist
screening database. (U)
6) The Director of the Terrorist Screening Center, in coordination with the Parties to this
Memorandum and in consultation with the heads of appropriate Federal departments and
agencies, will establish procedures to review the continued inclusion of a person in the terrorist
screening database, and to review the inclusion of that person in particular screening processes as
described in paragraph (1 5) above. whenever new information about that person is developed.
(U)
(l 7) Except upon written direction ?'om the President, determinations to include US. persons in
the terrorist screening database based solely on information concerning the domestic activities of
such persons will be made as by the Secretary of State. the Attorney General, and the
Secretary of Homeland Security, or their designees. (U)
(18) The Attorney General. aeting through the Director of the Terrorist Screening Center, will
review each nomination and determine whether to include that person in those records that can
be queried by law enforcement authorities through the NCIC database; for aliens, the Attorney
General will do so in consultation with the Secretary of Homeland Security, acting though the
Secretary of Homeland Seourity?s representative assigned to the Terrorist Screening Center. (U)
Page 5 of8

(19) The Secretary of Homeland Security, acting through his representative assigned to the
Terrorist Screening Center, will review each nomination and determine whether to include that
person in those records that can be queried by, or made accessible by appropriate means. to other
State, local, territorial, and tribal officials for homeland security purposes. including, bm not
limited to, screening persons when they apply for driver's licenses or other forms of
identi?cation. (U)
5 xtpuoddv
(20) The Secretary of Homeland Security, acting through his representative assigned to the
Terrorist Screening Center, will review each nomination and determine whether to include that
person in those records that will be subject to queries submitted by private sector
critical infrastructure operators or organizers of large events. The Secretary of Homeland
Security. in consultation with the other Parties to this Memorandum, and working with the
Director of the Terronst Screening Center, will establish necessary guidelines and criteria to:
govern the mechanisms by which private sector entities can submit such querie's; and
initiate appropriate law enforcement or other governmental action, if any, when a person
submitted for query by a private sector entity is identi?ed as a person in the terrorist screening
database. (U)
(21) The Secretary of State in consultation with the Attorney General, the Secretary of Homeland
Security, and the Director of Central Intelligence, acting through their representatives assigned to
the Terrorist Screening Center, will review each nomination and determine whether to include
that person in those records that can be queried by, or made accessible by apprOpriate means to,
foreign governments c00perating with the United States in the war on terrorists of global reach.
(U)
[Paragraphs (22) - (24) are classi?ed and therefore redacted]
(25) The terrorist screening database will be accessible to screening processes on a real-time
basis. Screening processes will only be able to access those rec0rds that have been identi?ed and
approved for such screening. as described in paragraphs (15) through (24) above. The Director
of the Terrorist Screening Center will strictly limit, to the maximum extent possible, the need to
provide US. Government terrorist screening data in list form to supported entities. (U)
Additional Implementation Provisions
(26) Per the President's direction. and consistent with guidelines developed by the Attorney
General in coordination with the other Parties to this Memorandum, the heads of Federal
departments and agencies will conduct screening using the Terrorisr Screening Center database
at all appropriate opportunities. and shall report to the Attorney General not later than 90 days
Page 6 of 8
(19) The Secretary of Homeland Security, acting through his representative assigned to the
Terrorist Screening Center, will review each nomination and determine whether to include that
person in those records that can be queried by, or made accessible by appropriate means. to other
State, local, territorial, and tribal officials for homeland security purposes. including, bm not
limited to, screening persons when they apply for driver's licenses or other forms of
identi?cation. (U)
5 xtpuoddv
(20) The Secretary of Homeland Security, acting through his representative assigned to the
Terrorist Screening Center, will review each nomination and determine whether to include that
person in those records that will be subject to queries submitted by private sector
critical infrastructure operators or organizers of large events. The Secretary of Homeland
Security. in consultation with the other Parties to this Memorandum, and working with the
Director of the Terronst Screening Center, will establish necessary guidelines and criteria to:
govern the mechanisms by which private sector entities can submit such querie's; and
initiate appropriate law enforcement or other governmental action, if any, when a person
submitted for query by a private sector entity is identi?ed as a person in the terrorist screening
database. (U)
(21) The Secretary of State in consultation with the Attorney General, the Secretary of Homeland
Security, and the Director of Central Intelligence, acting through their representatives assigned to
the Terrorist Screening Center, will review each nomination and determine whether to include
that person in those records that can be queried by, or made accessible by apprOpriate means to,
foreign governments c00perating with the United States in the war on terrorists of global reach.
(U)
[Paragraphs (22) - (24) are classi?ed and therefore redacted]
(25) The terrorist screening database will be accessible to screening processes on a real-time
basis. Screening processes will only be able to access those rec0rds that have been identi?ed and
approved for such screening. as described in paragraphs (15) through (24) above. The Director
of the Terrorist Screening Center will strictly limit, to the maximum extent possible, the need to
provide US. Government terrorist screening data in list form to supported entities. (U)
Additional Implementation Provisions
(26) Per the President's direction. and consistent with guidelines developed by the Attorney
General in coordination with the other Parties to this Memorandum, the heads of Federal
departments and agencies will conduct screening using the Terrorisr Screening Center database
at all appropriate opportunities. and shall report to the Attorney General not later than 90 days
Page 6 of 8

from today the screening opportunities at which such screening shall and shall not be conducted.
(U)
(27) The Attorney General and the Secretary of Homeland Secority will conduct a review of the
organization, structure and progress of the Terrorist Screening Center at an appropriate time, and
report to the President through the Assistant to the President for Homeland Security. The report
will include a recommendation on whether any modi?cations to the Terrorist Screening Center
should be made. (U)
5 xtpuaddv
(28) To the extent permitted by law, the Director of the will assume
responsibility for the functions and personnel of the Department of State's
counterterforist program, less those components devoted to providing operational support to
TIPOF users and will ensure that all terrorist identity information contained within the
database is fully integrated into the 'lTlC database. The functionality of the TI POF program,
whereby consular of?cials receive near real-time feedback to hits to TIPOFF entries, will be
maintained or improved upon, A senararp Annex In this Memorandum will be anreer?
to regarding the modalities of TIPOFF relocation to the arm the responsibilities of
each rarty. tU) I
(29) Beginning with the standup of the Terrorist Screening Center, Federal departments and
agencies will discontinue or transfer to the Terrorist Sereening Center, to the extent permitted by
law and with appropriate consultation with the Congress. those operations that are duplicativc of
the Terrorist Screening Center's mission to provide continuous operational support to users of
the terrorist screening database, including but not limited to:
those components of the Department of State?s counterterrorist program devoted to
providing operational support to TIPOFF users (with the exception of a small element that will
remain at the Department of State to facilitate intelligence support to the Bureau of Consular
Affairs);
the FBl?s Watchlist Unit; and
the Transportation Security Agency's No-Fly and Selectee list program. (U)
(30) Consistent with and other presidential directives, this Memorandum does not alter
existing authorities or responsibilities of the heads of Federal departments and agencies to carry
out operational activities or pr0vide or receive information. (U)
(3 To the extent that existing notices are not suf?cient, the Parties to this Memorandum, which
will provide information to the the and/or the Terrorist Screening Center under
HSPD-6 and this Memorandum. will publish in the Federal Register, prior to the standup of the
Terrorist Screening Center, "routine use" notices under the Privacy Act suf?cient to indicate that
such information will be provided. (U)
Page 7 ol'8
from today the screening opportunities at which such screening shall and shall not be conducted.
(U)
(27) The Attorney General and the Secretary of Homeland Secority will conduct a review of the
organization, structure and progress of the Terrorist Screening Center at an appropriate time, and
report to the President through the Assistant to the President for Homeland Security. The report
will include a recommendation on whether any modi?cations to the Terrorist Screening Center
should be made. (U)
5 xtpuaddv
(28) To the extent permitted by law, the Director of the will assume
responsibility for the functions and personnel of the Department of State's
counterterforist program, less those components devoted to providing operational support to
TIPOF users and will ensure that all terrorist identity information contained within the
database is fully integrated into the 'lTlC database. The functionality of the TI POF program,
whereby consular of?cials receive near real-time feedback to hits to TIPOFF entries, will be
maintained or improved upon, A senararp Annex In this Memorandum will be anreer?
to regarding the modalities of TIPOFF relocation to the arm the responsibilities of
each rarty. tU) I
(29) Beginning with the standup of the Terrorist Screening Center, Federal departments and
agencies will discontinue or transfer to the Terrorist Sereening Center, to the extent permitted by
law and with appropriate consultation with the Congress. those operations that are duplicativc of
the Terrorist Screening Center's mission to provide continuous operational support to users of
the terrorist screening database, including but not limited to:
those components of the Department of State?s counterterrorist program devoted to
providing operational support to TIPOFF users (with the exception of a small element that will
remain at the Department of State to facilitate intelligence support to the Bureau of Consular
Affairs);
the FBl?s Watchlist Unit; and
the Transportation Security Agency's No-Fly and Selectee list program. (U)
(30) Consistent with and other presidential directives, this Memorandum does not alter
existing authorities or responsibilities of the heads of Federal departments and agencies to carry
out operational activities or pr0vide or receive information. (U)
(3 To the extent that existing notices are not suf?cient, the Parties to this Memorandum, which
will provide information to the the and/or the Terrorist Screening Center under
HSPD-6 and this Memorandum. will publish in the Federal Register, prior to the standup of the
Terrorist Screening Center, "routine use" notices under the Privacy Act suf?cient to indicate that
such information will be provided. (U)
Page 7 ol'8

(32) Memorandum of Understanding is effective from the date of signatux by all Panic
Any Party may nebmit, through the Assistant to the President for Homeland Securitv writtens'
renuests for reViStons. amendments, modi?cations, annexes and supplementarv undeistand'
Memorandum at any time. Such changes shall become effecnve upon the-date ofa 111%]
by all Panies. The Parties shall review this Memorandum not me? than .. fr ?pprow
effective date. (U) . on- dear 0mm
xipuoddv
mneo?wcu - . . . h. "September-16,1093
emu-w of Stile:
. I .
than? J. Rid
Swim-yer Bantam! See'mity .
Szgnatures are consolidated from classi?ed version of the original TSC MOU.
Page 8 of8
(32) Memorandum of Understanding is effective from the date of signatux by all Panic
Any Party may nebmit, through the Assistant to the President for Homeland Securitv writtens'
renuests for reViStons. amendments, modi?cations, annexes and supplementarv undeistand'
Memorandum at any time. Such changes shall become effecnve upon the-date ofa 111%]
by all Panies. The Parties shall review this Memorandum not me? than .. fr ?pprow
effective date. (U) . on- dear 0mm
xipuoddv
mneo?wcu - . . . h. "September-16,1093
emu-w of Stile:
. I .
than? J. Rid
Swim-yer Bantam! See'mity .
Szgnatures are consolidated from classi?ed version of the original TSC MOU.
Page 8 of8

THE SECRETARY OF STATE
THE OF THE TREASURY
THE SECRETARY OF DEFENSE
THE ATTORNEY
SECRETARY OF HOMELAND SECURITY
THE DIRECTOR OF NATIONAL memos
TEE DIRECTOR OF THE 021mm. Wanna; AGEQCY
THE DIRECTOR 01" NATIONAL COMMON (ENTER
DIRECTOR OF THE mom SW6 CENTER
17 xgpusddv
ADDENDUM
WWOFWANDWGONMMAWANDUSEOF
We
Bad:ng
(1) mmcm?nm
16.
m.muscnw3mdmmuamA.mm2.m. Totheextwt
MAME mpemndusdleTSCMOU.
In ?damn them-deM.
the,
Nation!
Agencym
Infomuion.
(2)
Pmies?nc?am.
Infam?ma Sharing MOUslnn canto] lha unions oflhe Parties Addendum.
Purpose
mmdudendm?am:
Directive-6 CREPE-6), dated SW 16. 2003. entitled ?Tnzegmion nd Use of Sawing
Mound? to Protect Against Terrain" and
THE SECRETARY OF STATE
THE OF THE TREASURY
THE SECRETARY OF DEFENSE
THE ATTORNEY
SECRETARY OF HOMELAND SECURITY
THE DIRECTOR OF NATIONAL memos
TEE DIRECTOR OF THE 021mm. Wanna; AGEQCY
THE DIRECTOR 01" NATIONAL COMMON (ENTER
DIRECTOR OF THE mom SW6 CENTER
17 xgpusddv
ADDENDUM
WWOFWANDWGONMMAWANDUSEOF
We
Bad:ng
(1) mmcm?nm
16.
m.muscnw3mdmmuamA.mm2.m. Totheextwt
MAME mpemndusdleTSCMOU.
In ?damn them-deM.
the,
Nation!
Agencym
Infomuion.
(2)
Pmies?nc?am.
Infam?ma Sharing MOUslnn canto] lha unions oflhe Parties Addendum.
Purpose
mmdudendm?am:
Directive-6 CREPE-6), dated SW 16. 2003. entitled ?Tnzegmion nd Use of Sawing
Mound? to Protect Against Terrain" and

tomm??izethehm?w
Integration Center,now1heNndoml
the Practicum (EVA) ?2004. Section 1016(a)(4)) in
dial-possession
Procedures
17 xgpuaddv
(4) bthandcouismwiduhe
madmanonmt.
(Giginuou').
mechanimtomvidemchinfmna?on.
(S)
mmwi?mhav?abloto
An
(6)
(7)
mo?mmamcningdme (TSDB):
(I) Nmand?iases;
Duck ofbinh;
(0) Places of birth;
Unique Identifying numb?: and: dim visa numbers. :0an security
account unmbets:
Paspon infomn?m. including passport numbers. countriss of issuance. dues and locations
of expimion dues. tampon phoms. and our: mum ch?;
(1) Wefo?ginmdm?m?i?es;
tomm??izethehm?w
Integration Center,now1heNndoml
the Practicum (EVA) ?2004. Section 1016(a)(4)) in
dial-possession
Procedures
17 xgpuaddv
(4) bthandcouismwiduhe
madmanonmt.
(Giginuou').
mechanimtomvidemchinfmna?on.
(S)
mmwi?mhav?abloto
An
(6)
(7)
mo?mmamcningdme (TSDB):
(I) Nmand?iases;
Duck ofbinh;
(0) Places of birth;
Unique Identifying numb?: and: dim visa numbers. :0an security
account unmbets:
Paspon infomn?m. including passport numbers. countriss of issuance. dues and locations
of expimion dues. tampon phoms. and our: mum ch?;
(1) Wefo?ginmdm?m?i?es;

(3) Physical identifiers awhassu, race. (2010:, haircolor. scars. antics, or
tattoos;
I 17 xgpueddv
Known locations. Le.
Photomph: or madame: oftbc individe
a) Fingerprints or can: biomwic am:
Employment data:
(I) license plate numbers;
(mgzoma'rmmuomm :pad?cany pmvideforpamctothe
(8) Tumu'sm
Parties dean
meTmodstIdani?usWhpu-nmh mForO?ci?UseOnlyGOUO) of
memcdtothc
TSC willbedeanchOUO.
(9)
authorizes. from
reduoetheire?'ec?mu.
(10) Itcng anOtip'mmr?s abilith Mitsped?c Tamas!
We: to
nurse. regadless
(11)
NCTC.
(12)
admhisu-ative proceedingouums. {minding process,
nouldresuhinpubuc disclosm wmmwa?mudaivadthm?mmy
LheAuomeyGeamL AnyrecipleMo?nfoxm?on?anSDB handmme
(3) Physical identifiers awhassu, race. (2010:, haircolor. scars. antics, or
tattoos;
I 17 xgpueddv
Known locations. Le.
Photomph: or madame: oftbc individe
a) Fingerprints or can: biomwic am:
Employment data:
(I) license plate numbers;
(mgzoma'rmmuomm :pad?cany pmvideforpamctothe
(8) Tumu'sm
Parties dean
meTmodstIdani?usWhpu-nmh mForO?ci?UseOnlyGOUO) of
memcdtothc
TSC willbedeanchOUO.
(9)
authorizes. from
reduoetheire?'ec?mu.
(10) Itcng anOtip'mmr?s abilith Mitsped?c Tamas!
We: to
nurse. regadless
(11)
NCTC.
(12)
admhisu-ative proceedingouums. {minding process,
nouldresuhinpubuc disclosm wmmwa?mudaivadthm?mmy
LheAuomeyGeamL AnyrecipleMo?nfoxm?on?anSDB handmme

17 xgpuaddv
Attorneme Marimba. Anyreproductinn, diuanim?nu, cremation (handing,
butnoch'mitedto. onlb?e?ngs) by:
mementofthesemstrictions. unlimited set
(:me Idemi?m: me; dneofbinh;
WWI). with mm, localudu?nl Mufu?pgovm for terrorism
Wham upcmicted bylaw, regulation. or agreement
(13)
imam. for
inclusioninTIDF.
above.
(14) manhunt-of?ng bmw?mitedm,
with?
vulnuubilitynf'I?SDB tommhmimdm oraploimion. 'l'heestahlishm amuse
MWM innomy the NCTC arch: TSC.
(l5)
Madam-related
udc?nedinthem?m.
Implementation
(16) Addende is
is
contained.
(17) 311111
(18)
and agencies to pafonn made: kw. consism with applicable legal
Munymothmginm? than}:
shringrequimm otthe
17 xgpuaddv
Attorneme Marimba. Anyreproductinn, diuanim?nu, cremation (handing,
butnoch'mitedto. onlb?e?ngs) by:
mementofthesemstrictions. unlimited set
(:me Idemi?m: me; dneofbinh;
WWI). with mm, localudu?nl Mufu?pgovm for terrorism
Wham upcmicted bylaw, regulation. or agreement
(13)
imam. for
inclusioninTIDF.
above.
(14) manhunt-of?ng bmw?mitedm,
with?
vulnuubilitynf'I?SDB tommhmimdm oraploimion. 'l'heestahlishm amuse
MWM innomy the NCTC arch: TSC.
(l5)
Madam-related
udc?nedinthem?m.
Implementation
(16) Addende is
is
contained.
(17) 311111
(18)
and agencies to pafonn made: kw. consism with applicable legal
Munymothmginm? than}:
shringrequimm otthe
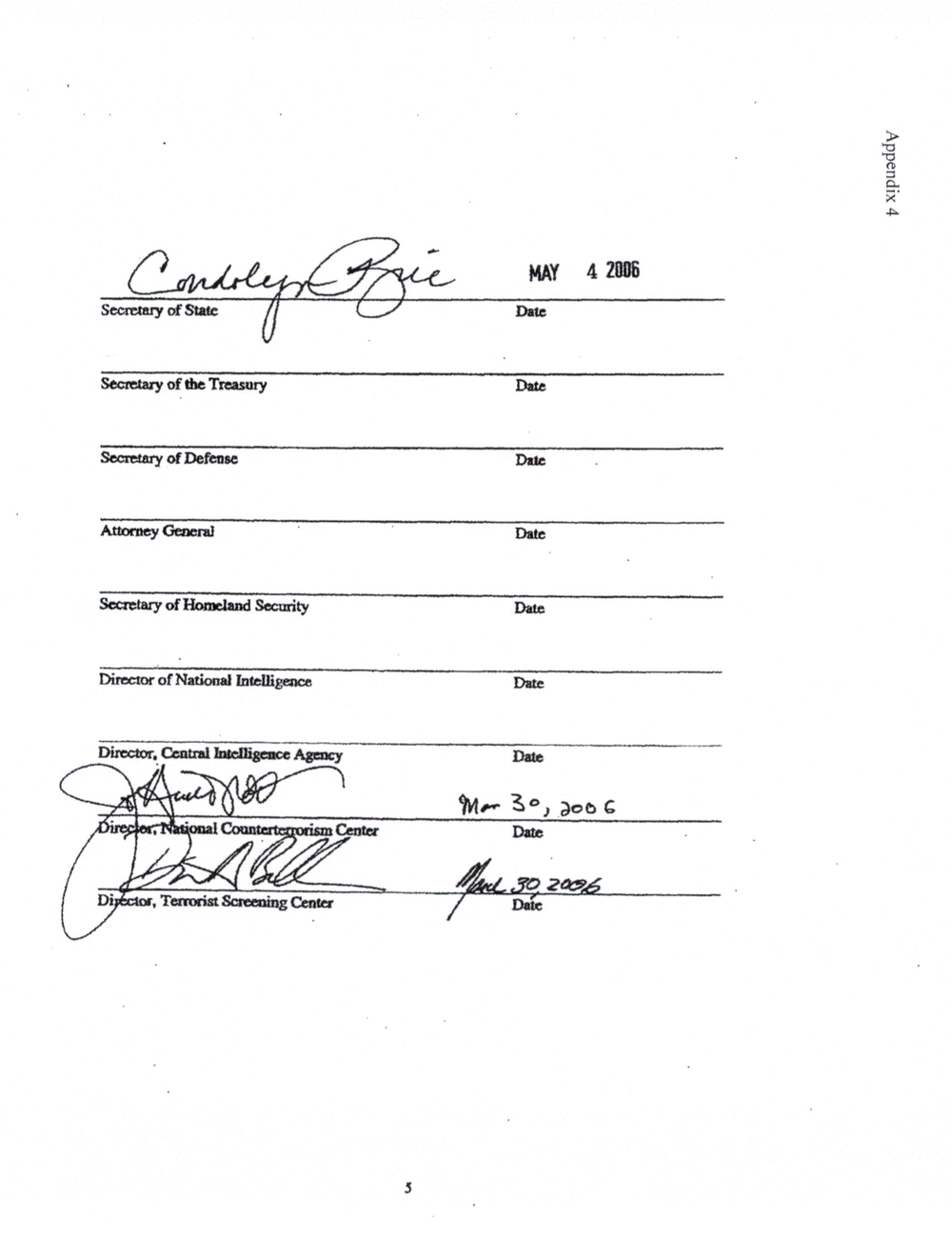
MAY 4 21105
swarm Dal:
Daze
SacramyofDefenu Due
Amrnemecm Date-
Dan:
Dimat?aama Intelligauoe Due
17 xgpuaddv
MAY 4 21105
swarm Dal:
Daze
SacramyofDefenu Due
Amrnemecm Date-
Dan:
Dimat?aama Intelligauoe Due
17 xgpuaddv
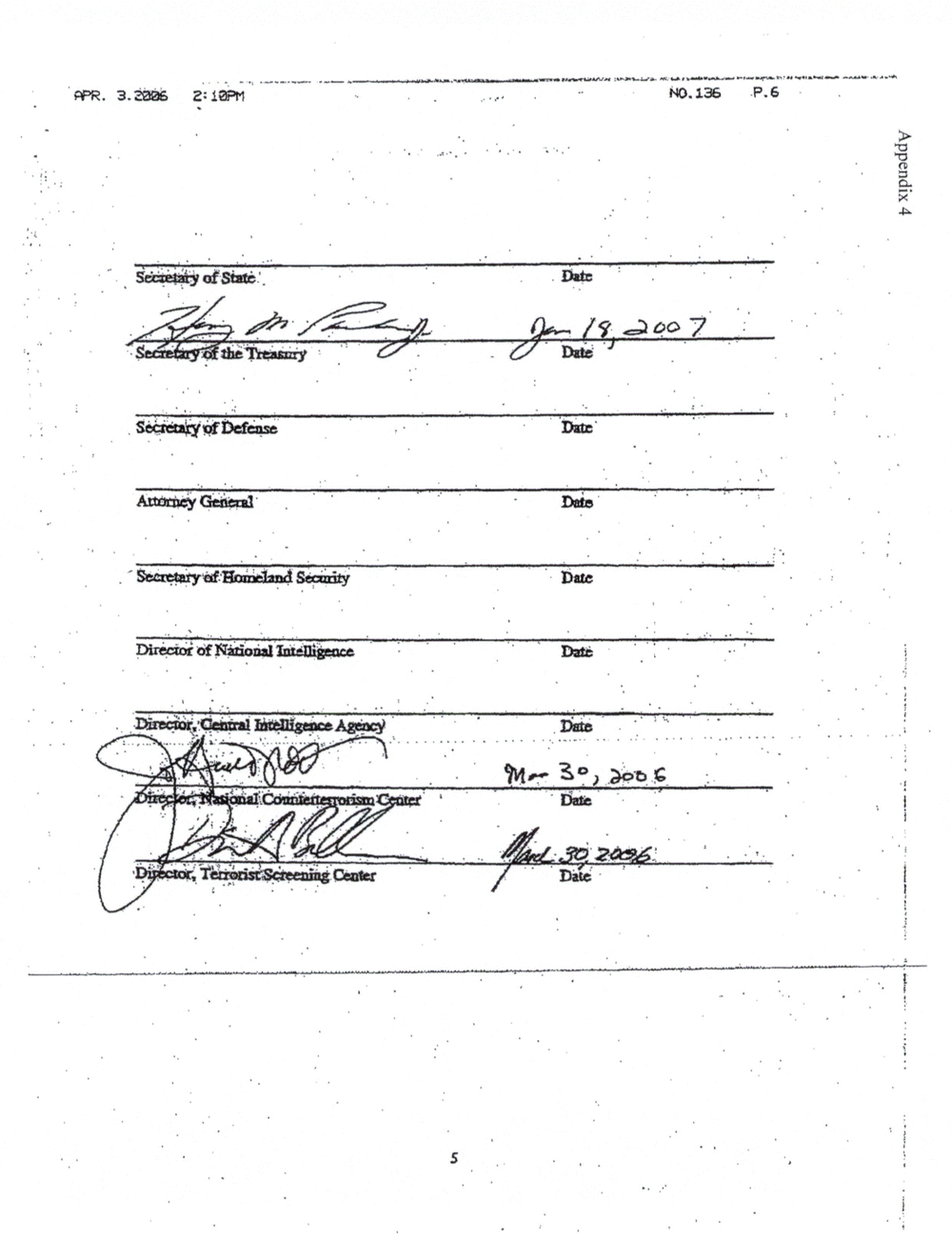
APR.
[mum/u In" a yy?I?La?u ll amb- .n a.
N0. 136
'7 xgpuaddv
APR.
[mum/u In" a yy?I?La?u ll amb- .n a.
N0. 136
'7 xgpuaddv
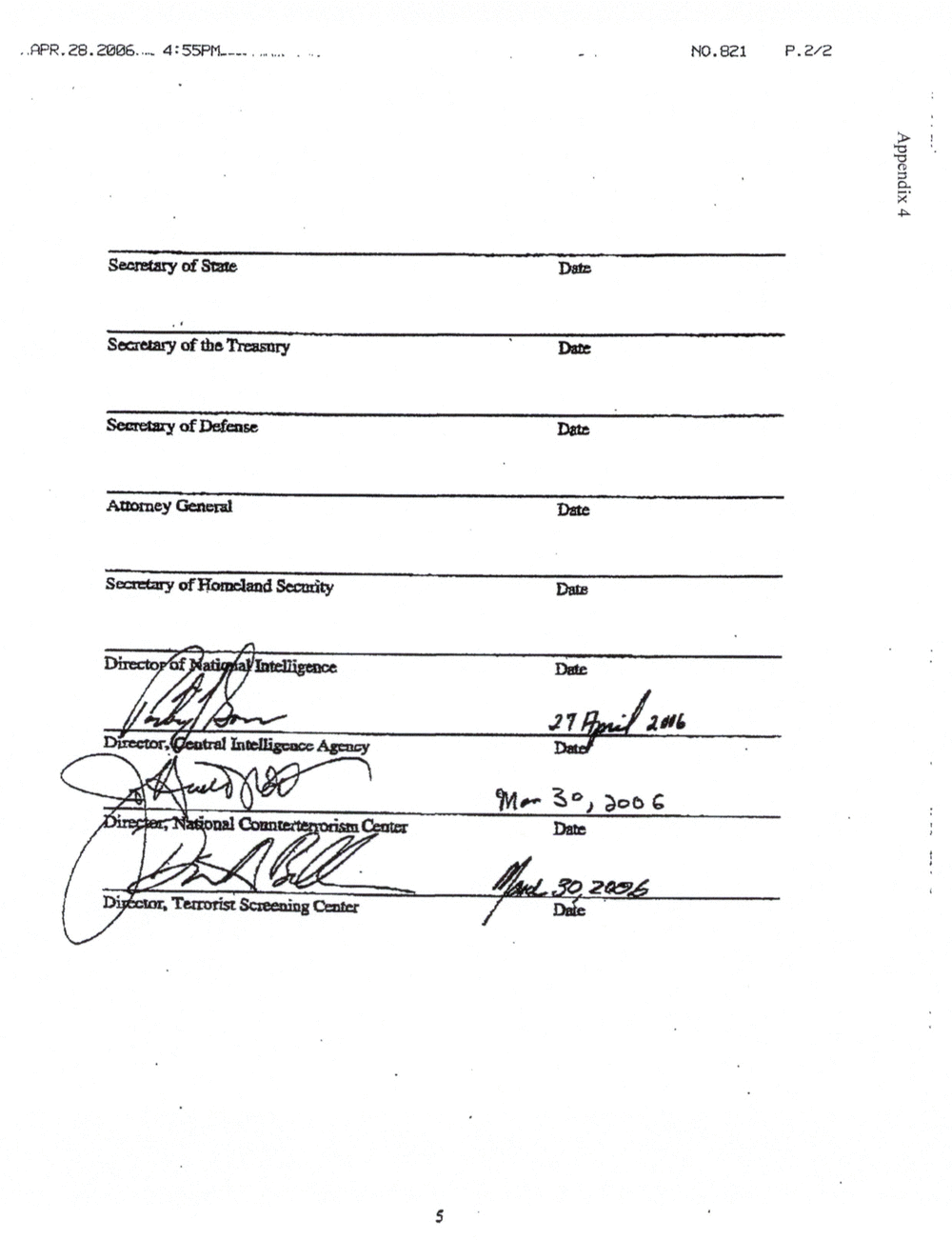
. .. - NO.821
swarm Du:
Smgf?xa'husmy Dan:
SmofDafense Dam
Anomey?encnl Dane
Data
DE
.27 2115
300
Du:
17 xgpuaddv
. .. - NO.821
swarm Du:
Smgf?xa'husmy Dan:
SmofDafense Dam
Anomey?encnl Dane
Data
DE
.27 2115
300
Du:
17 xgpuaddv
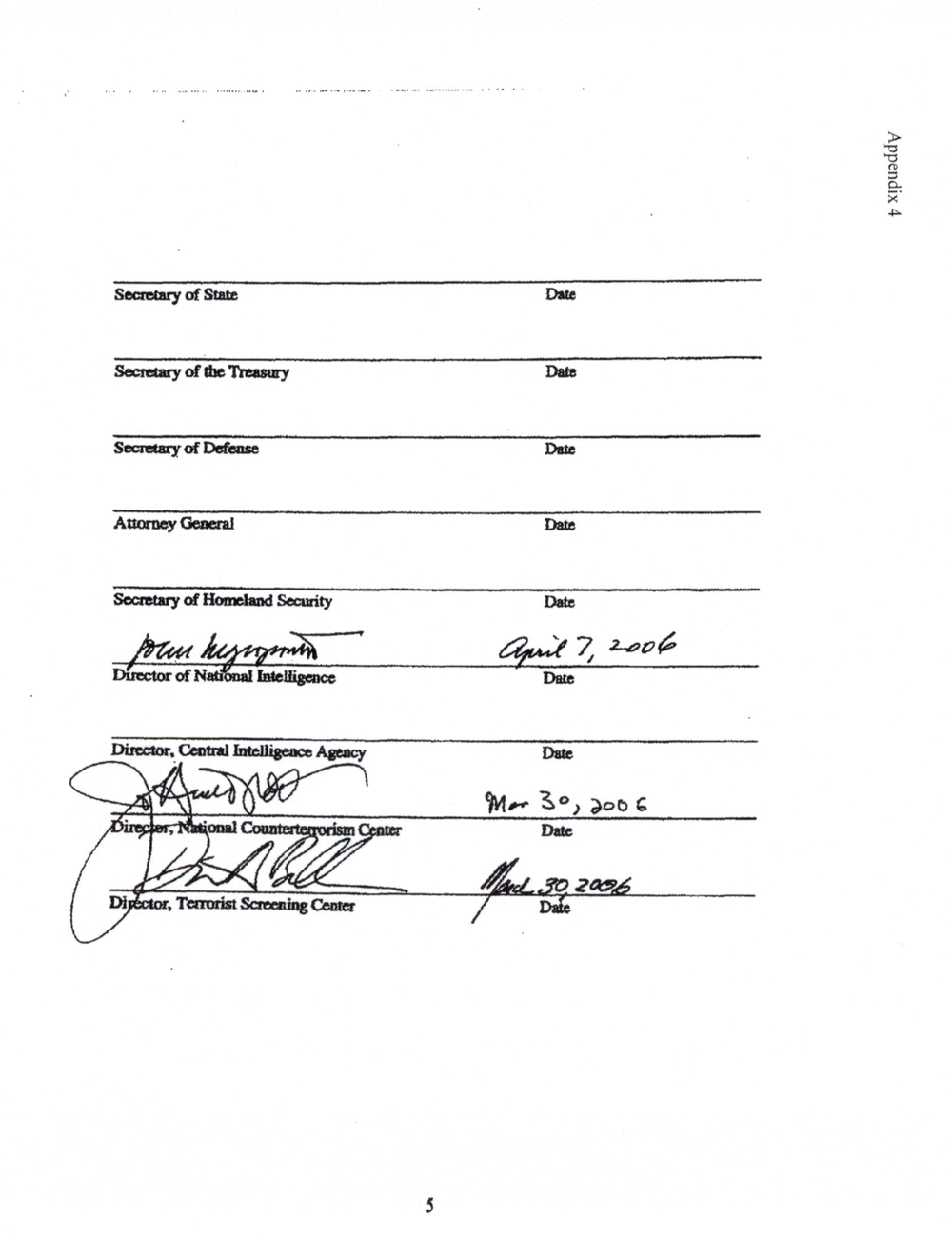
Societal-yome Due
Sacral-yth
swarm Due
Anomey?enenl Dam
Du:
Duet:de Dale
Dim..me Dan:
30?
Date
?i Em
xgpuaddv
Societal-yome Due
Sacral-yth
swarm Due
Anomey?enenl Dam
Du:
Duet:de Dale
Dim..me Dan:
30?
Date
?i Em
xgpuaddv
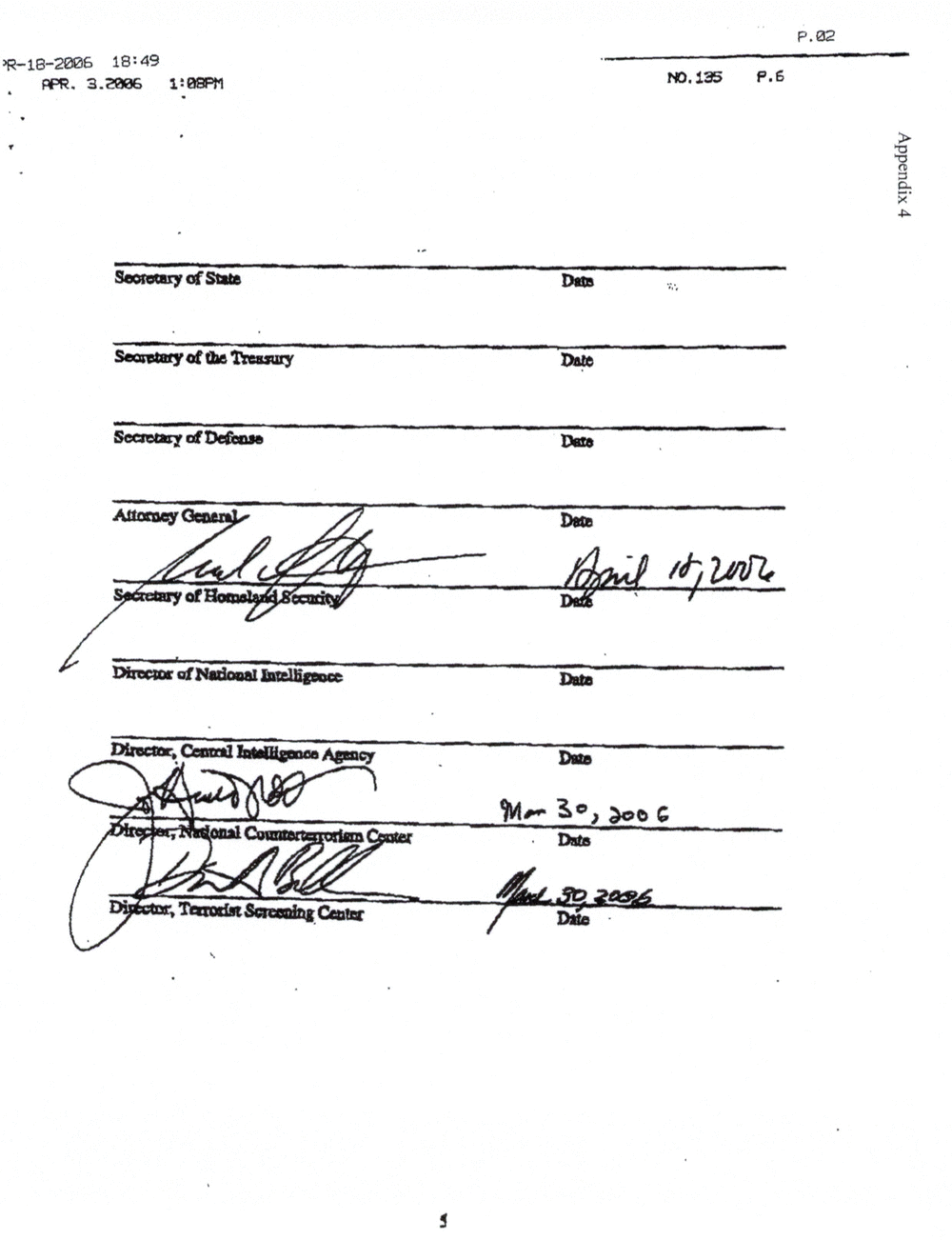
18:49
PPR. 3.2% 1:333?
Worm
Smde
de
m- 135
P.6
19.82
17 xgpuaddv
18:49
PPR. 3.2% 1:333?
Worm
Smde
de
m- 135
P.6
19.82
17 xgpuaddv

17 xgpuaddv
17 xgpuaddv
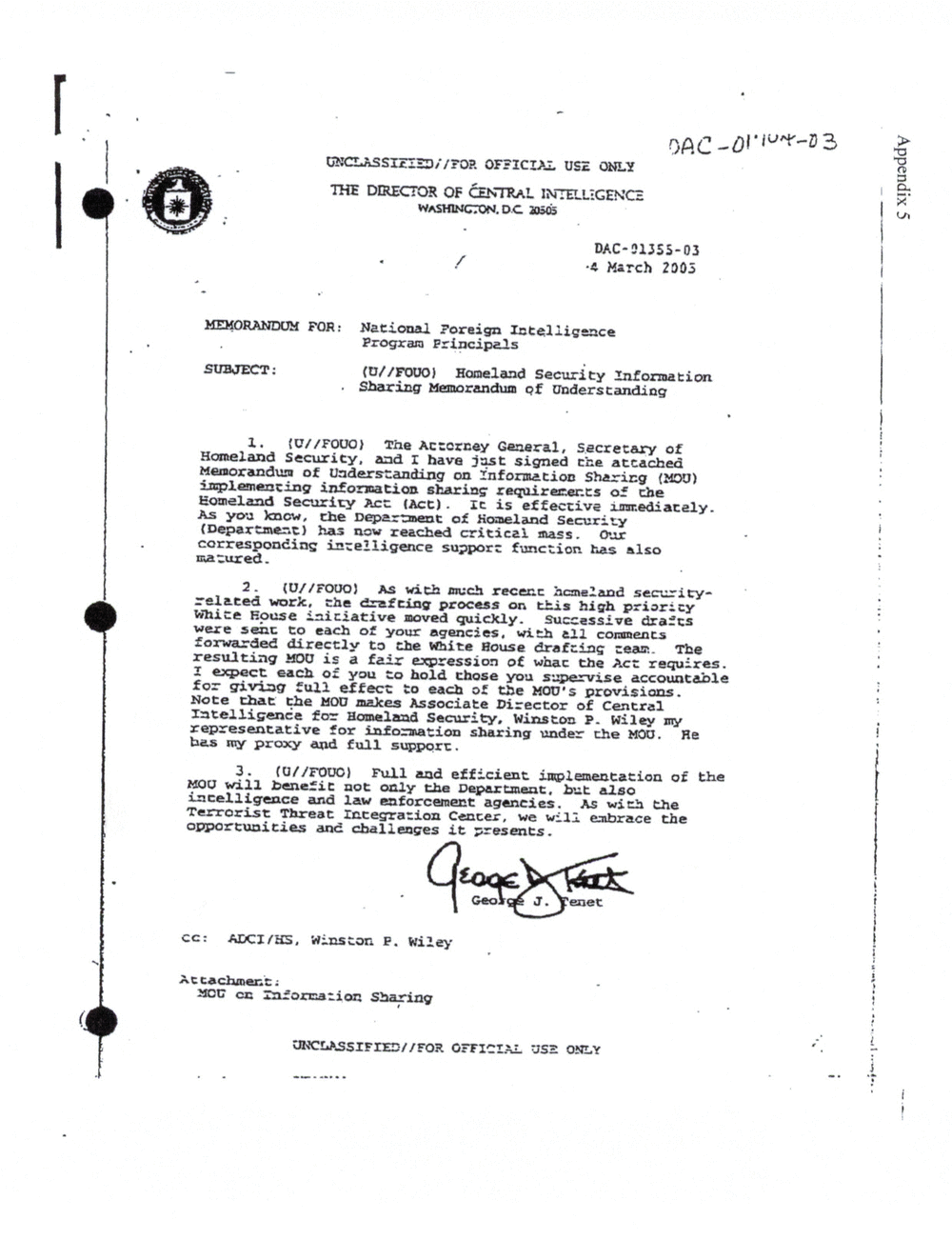
.-
SAC ?33
USE ONLY
no: DIRECTOR OF ?Emmy. mmucmcs
wan-numtc 2050's
4 March 2003
National Foreign Intelligence
Program Principals
Homeland SeCurity Information
Sharing Memorandum of Understanding
1. The Attorney General. Secretary of
Homeland Security. and I have just signed the attached
Memorandum of Understanding on Information Sharing (MOD)
implanting information sharing rewireitetts of the
Hamelend Security Act (Act) . It is effeCtive immoraly.
As you know. the Wt of Homeland Secutit
(Department) has now reached critical mass. Our
corresponding Ltelligmce support function has also
matured.
2- As with much recent homeland security-
related work. the drafting process on this high priority
White House initiative moved quickly. Successive drafts
were sent to each of. your agencies. with ell coments
forwarded directly to the imite House drafting team. The
resulting ?100 is a fair expression of what the Act requires.
I eaqaect each of you to hold those you supervise accountable
for giving full effect to each of the 1400's provisions.
Note that the MOD makes Associate Director of Central
Intelligence for Homeland Security. Winston P. Wiley my
representatiVe for intonation sharing under the MOD. He
has my proxy and. full support.
3. Full and efficient implementation of the
M00 will bene?t not only the Department. but also
intelligence and law enforcement agencies. 35 with the
Terrorist Threat Integration Center. we will embrace the
opportunities and challenges it presmts.
CC: Winston F. Wiley
enet
At techmen?t
not: on 31301131108 Sharing
OFFICIAL USE ONLY
. .-
xgpuoddv
- -.. . --.
.-
SAC ?33
USE ONLY
no: DIRECTOR OF ?Emmy. mmucmcs
wan-numtc 2050's
4 March 2003
National Foreign Intelligence
Program Principals
Homeland SeCurity Information
Sharing Memorandum of Understanding
1. The Attorney General. Secretary of
Homeland Security. and I have just signed the attached
Memorandum of Understanding on Information Sharing (MOD)
implanting information sharing rewireitetts of the
Hamelend Security Act (Act) . It is effeCtive immoraly.
As you know. the Wt of Homeland Secutit
(Department) has now reached critical mass. Our
corresponding Ltelligmce support function has also
matured.
2- As with much recent homeland security-
related work. the drafting process on this high priority
White House initiative moved quickly. Successive drafts
were sent to each of. your agencies. with ell coments
forwarded directly to the imite House drafting team. The
resulting ?100 is a fair expression of what the Act requires.
I eaqaect each of you to hold those you supervise accountable
for giving full effect to each of the 1400's provisions.
Note that the MOD makes Associate Director of Central
Intelligence for Homeland Security. Winston P. Wiley my
representatiVe for intonation sharing under the MOD. He
has my proxy and. full support.
3. Full and efficient implementation of the
M00 will bene?t not only the Department. but also
intelligence and law enforcement agencies. 35 with the
Terrorist Threat Integration Center. we will embrace the
opportunities and challenges it presmts.
CC: Winston F. Wiley
enet
At techmen?t
not: on 31301131108 Sharing
OFFICIAL USE ONLY
. .-
xgpuoddv
- -.. . --.

(D
:3
E:
u.
EMORANDUM OFUND RSTAN mo CE
VI NT
OF HOMELAND SECURI SHAREG
This Agreement provides a framework and guidance to govern information sharing, use.
and handling between: the Secretary of Homeland Security, on behalf of the Department of
Homeland Security (DHS). including all entities that are or become, wholly or in part, elements
of the Director of Central intelligence (DCl)l on behalf of all entities that are, Or become.
wholly or in part. elements of the United States Intelligence Community (1C), other than those
that are to become part of and the Attorney Genu?al. on behalf of the Department of Justice
(DOJ). including the Federal Bureau of Investigation and all entities that are, or become. wholly
Or in part, elements of and any other department, agency. or entity having federal law
enforcement responsibilities. other than those that are to become part of DHS.
l. 8939; 91 Applicatim. This Agreement shall be binding on all such departments.
agencies. and entities on whose behalf the Secretary of Homeland Security. the DU. and the
Attorney General agree herein. This Agreement is intended to mandate minimum requirements
and procedurm for information sharing. use, and handling, and for coordination and decon?iction
of analytic judynents. Departments and agencies are encouraged to develop additional
procedures and mechanisms to provide for greater information sharing and coordination than
required herein, consistent with the DHS Legislation and other relevant statutory authorities,
Presidential Directives. the President's announced policies for protecting against terrorist threats .
to the homeland. and this Agreement, including. but not limited to: .
the Homeland Security Act of 2002;
the National Security Act of I947, as amended;
the Uniting and Strengthening America by Providing ApprOpriate Tools Required
to intercept and Obstruet Terrorism Act of 200];
the Foreign intelligence Surveillance Act. as amended; .
Executive Order 12333. as amended. and any subsequent Executive Orders on
Intelligence Activities;
Executive Order 1323!. as amended. and any subsequent Executive Orders on
Homeland Security,
(3) Guidelines Regarding Disclosure to the Director of Central intelligence and
Homeland Security Officials of Foreign Intelligence Acquired in the Course of a
Criminal investigation, dated September 23. 2002; and
Guidelines for Disclosure of Grand Jury and Electronic. Wire. and Oral
Interception Information identifying United States Persons. dated September 23.
2002.
To the extent that this Agreement provides for more expansive information shanng than
other authorities or agreements, with the exception of statutes. or Presidential Directives
including, but not limited to. Executive Orders. (?Presidential Directives"), the more expansive
provisions of this Agreement shall be followed
(D
:3
E:
u.
EMORANDUM OFUND RSTAN mo CE
VI NT
OF HOMELAND SECURI SHAREG
This Agreement provides a framework and guidance to govern information sharing, use.
and handling between: the Secretary of Homeland Security, on behalf of the Department of
Homeland Security (DHS). including all entities that are or become, wholly or in part, elements
of the Director of Central intelligence (DCl)l on behalf of all entities that are, Or become.
wholly or in part. elements of the United States Intelligence Community (1C), other than those
that are to become part of and the Attorney Genu?al. on behalf of the Department of Justice
(DOJ). including the Federal Bureau of Investigation and all entities that are, or become. wholly
Or in part, elements of and any other department, agency. or entity having federal law
enforcement responsibilities. other than those that are to become part of DHS.
l. 8939; 91 Applicatim. This Agreement shall be binding on all such departments.
agencies. and entities on whose behalf the Secretary of Homeland Security. the DU. and the
Attorney General agree herein. This Agreement is intended to mandate minimum requirements
and procedurm for information sharing. use, and handling, and for coordination and decon?iction
of analytic judynents. Departments and agencies are encouraged to develop additional
procedures and mechanisms to provide for greater information sharing and coordination than
required herein, consistent with the DHS Legislation and other relevant statutory authorities,
Presidential Directives. the President's announced policies for protecting against terrorist threats .
to the homeland. and this Agreement, including. but not limited to: .
the Homeland Security Act of 2002;
the National Security Act of I947, as amended;
the Uniting and Strengthening America by Providing ApprOpriate Tools Required
to intercept and Obstruet Terrorism Act of 200];
the Foreign intelligence Surveillance Act. as amended; .
Executive Order 12333. as amended. and any subsequent Executive Orders on
Intelligence Activities;
Executive Order 1323!. as amended. and any subsequent Executive Orders on
Homeland Security,
(3) Guidelines Regarding Disclosure to the Director of Central intelligence and
Homeland Security Officials of Foreign Intelligence Acquired in the Course of a
Criminal investigation, dated September 23. 2002; and
Guidelines for Disclosure of Grand Jury and Electronic. Wire. and Oral
Interception Information identifying United States Persons. dated September 23.
2002.
To the extent that this Agreement provides for more expansive information shanng than
other authorities or agreements, with the exception of statutes. or Presidential Directives
including, but not limited to. Executive Orders. (?Presidential Directives"), the more expansive
provisions of this Agreement shall be followed

2. 'For purposes of this Agreement:
"c
(D
:s
Ur
?Analytic conclusion" means the product of analysis of one or more pieces
of information in which inferences are drawn from the information being analyzed to
arrive at a determination about a fact - such as, for example, a potential threat that is
not explicit or apparent from the face of the original information itself. It does not
include, for example, a summary of the factual content of a piece of intelligence
information, a report of an interview, or a report or other document that merely collects
and summarizes information from multiple sources about the same or related topics, or
other types of communication which do not include analytic conclusions as described
above.
'Attomey General" means the Attorney General of the United States Or the
Attorney General's designcc, except as otherwise provided herein.
(0) "Classi?ed information" means inforrnation that has been determined pursuant
to Executive Order No. [2958..or any successor order, Executive Order No.
1295 I, or any successor order, or the Atomic Energy Act of [954 (42 U.S.C.
201 to require protection against unauthorized disclosure.
"Covered entity? means; any department, agency, bureau, of?ce or other
entity that is, or becomes, wholly or in part. an element of the Department of Homeland
Security (including the Department itself); any department, agency, bureau, of?ce or
other entity that is. or becomes. wholly or in part, an element of the United States
Intelligence Community or the Department of Justice; and any other department, agency,
or entity having federal lawenforcement responsibilities:
"Covered information" means terrorism information, weapons of mass
destruction (WMD) information, vulnerabilities infatuation. and other information
relevant to the duties of the Department of Homeland Security, as well as analyses based
wholly or in part on such covered information.
"Department" or ?Di-l5? shall mean the Department of Homeland Security
and any entity that is, or becomes, an element of that Department.
(3) Legislation" means the Homeland Security Act of 2002 (HR. 5005,
[07th Congress. 2d Session) (November 26, 2002), as it may be amended from' time to
time. -
means the Director of Central lntelligencc, or, except as therwise
provided herein, the DCl's designce, in his or her capacity as head of the intelligence
Community, and as head of the Central Intelligence Agency.
"Foreign intelligence" has the meaning given to that term in Section 3 of
the National Security Act of I947, as amended (50 U.S.C. 40hr), m: that statutory term
may be amended from time to time. I
2. 'For purposes of this Agreement:
"c
(D
:s
Ur
?Analytic conclusion" means the product of analysis of one or more pieces
of information in which inferences are drawn from the information being analyzed to
arrive at a determination about a fact - such as, for example, a potential threat that is
not explicit or apparent from the face of the original information itself. It does not
include, for example, a summary of the factual content of a piece of intelligence
information, a report of an interview, or a report or other document that merely collects
and summarizes information from multiple sources about the same or related topics, or
other types of communication which do not include analytic conclusions as described
above.
'Attomey General" means the Attorney General of the United States Or the
Attorney General's designcc, except as otherwise provided herein.
(0) "Classi?ed information" means inforrnation that has been determined pursuant
to Executive Order No. [2958..or any successor order, Executive Order No.
1295 I, or any successor order, or the Atomic Energy Act of [954 (42 U.S.C.
201 to require protection against unauthorized disclosure.
"Covered entity? means; any department, agency, bureau, of?ce or other
entity that is, or becomes, wholly or in part. an element of the Department of Homeland
Security (including the Department itself); any department, agency, bureau, of?ce or
other entity that is. or becomes. wholly or in part, an element of the United States
Intelligence Community or the Department of Justice; and any other department, agency,
or entity having federal lawenforcement responsibilities:
"Covered information" means terrorism information, weapons of mass
destruction (WMD) information, vulnerabilities infatuation. and other information
relevant to the duties of the Department of Homeland Security, as well as analyses based
wholly or in part on such covered information.
"Department" or ?Di-l5? shall mean the Department of Homeland Security
and any entity that is, or becomes, an element of that Department.
(3) Legislation" means the Homeland Security Act of 2002 (HR. 5005,
[07th Congress. 2d Session) (November 26, 2002), as it may be amended from' time to
time. -
means the Director of Central lntelligencc, or, except as therwise
provided herein, the DCl's designce, in his or her capacity as head of the intelligence
Community, and as head of the Central Intelligence Agency.
"Foreign intelligence" has the meaning given to that term in Section 3 of
the National Security Act of I947, as amended (50 U.S.C. 40hr), m: that statutory term
may be amended from time to time. I

"Homeland" means the United States as de?ned in the DHS Legislation.
Q.-
?lnfrastructtne? means the basic systems, assets, facilities, Services, and
installations needed for the functioning of our society. The term includes, but is not
limited to, critical in?astructure, meaning systems and assets, whether physical or virtual,
so vital to the United States that the incapacity or destruction of such systems and assets
would have a debilitating impact on United States national security, economic security,
national public health or safety, or any combination of these. Critical infrastructure
includes, but is not limited to. agriculture, food, water, public health, emergency services,
government, defenSe industrial base, information and telecommunications, energy,
transportation, banking and ?nance, chemical industry and hazardous materials. postal
and shipping, and national monuments and icons. -- -
(1) ?Infrastructure information" means all information related to the
identi?catiOn, status, security. criticality, risk assessment, Vulnerability to all means of
attack, interdependency. and attack consequences (including potential impact on public
health or safety, the economy. national security, governance and public con?dence) of the
infrastructure of the United States.
"intelligence Community" has the meaning given it in section 3(4) of the
National Security Act of 1947 (SO U.S.C. 40la(4)), as it may be amended from time to
time.
"Need-to-know" means a determination made by an authorized holder of .
classi?ed information, or sensitive law enforcement information, that a prOSpective
recipient requires access to a Speci?c piece, or category of information in order to
perform or assist in a lawful and authorized gOVernmental function.
(0) "Parties" means the signatories to this Agreernent and their successors, on
behalf of all covered entities they head, supervise or represent.
Act" means the Uniting and Strengthening America by
Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA
PATRIOT) Act Pub. L. 107-56, 15 Stat. 272, 278-81.
"Secretary" means the Secretary of Homeland Security or the Secretary's
dcsigncc. except as otherwise provided herein.
"Terrorism information" means all information relating to the existence,
organization, capabilities. plans. intentions, vulnerabilities, means of ?nance or material
support, or activities of foreign or international terrorist groups or individuals, domestic
groups or individuals involved in terrorism. to threats posed by such groups or individuals
to the United States, United States persons, or United States interests. or to those of other
nations. or to communications between such groups or individuals, and to
"Homeland" means the United States as de?ned in the DHS Legislation.
Q.-
?lnfrastructtne? means the basic systems, assets, facilities, Services, and
installations needed for the functioning of our society. The term includes, but is not
limited to, critical in?astructure, meaning systems and assets, whether physical or virtual,
so vital to the United States that the incapacity or destruction of such systems and assets
would have a debilitating impact on United States national security, economic security,
national public health or safety, or any combination of these. Critical infrastructure
includes, but is not limited to. agriculture, food, water, public health, emergency services,
government, defenSe industrial base, information and telecommunications, energy,
transportation, banking and ?nance, chemical industry and hazardous materials. postal
and shipping, and national monuments and icons. -- -
(1) ?Infrastructure information" means all information related to the
identi?catiOn, status, security. criticality, risk assessment, Vulnerability to all means of
attack, interdependency. and attack consequences (including potential impact on public
health or safety, the economy. national security, governance and public con?dence) of the
infrastructure of the United States.
"intelligence Community" has the meaning given it in section 3(4) of the
National Security Act of 1947 (SO U.S.C. 40la(4)), as it may be amended from time to
time.
"Need-to-know" means a determination made by an authorized holder of .
classi?ed information, or sensitive law enforcement information, that a prOSpective
recipient requires access to a Speci?c piece, or category of information in order to
perform or assist in a lawful and authorized gOVernmental function.
(0) "Parties" means the signatories to this Agreernent and their successors, on
behalf of all covered entities they head, supervise or represent.
Act" means the Uniting and Strengthening America by
Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA
PATRIOT) Act Pub. L. 107-56, 15 Stat. 272, 278-81.
"Secretary" means the Secretary of Homeland Security or the Secretary's
dcsigncc. except as otherwise provided herein.
"Terrorism information" means all information relating to the existence,
organization, capabilities. plans. intentions, vulnerabilities, means of ?nance or material
support, or activities of foreign or international terrorist groups or individuals, domestic
groups or individuals involved in terrorism. to threats posed by such groups or individuals
to the United States, United States persons, or United States interests. or to those of other
nations. or to communications between such groups or individuals, and to

information relating to groups or individuals reasonably believed to be assisting 0r
associated with them.
xtpueddv
?Vulnerabilities information" means all information relating to the
susceptibility - actual. perceived, or conceptual of the United States, including any
portion, sector, population. geographic area, or industry, to terrorist attack.
?Weapons of Mass Destruction information" or inf?nna?tion"
means terrorism information or Vulnerabilities information relating to conventional
explosive weapons and non-conventional weapons capable of causing mass casualties and
damage, including chemical orbiological agents, radioactive or nuclear materials, and the
means to deliver them. -
3. Policies and for lgt?ogation Sharing, Handling Ed use. Consistent
with the DHS Legislation, and except as otherwise speci?cally provided in this Agreement, the
following agreed-upon policies and procedures shall apply to the provision of covered
information by any covered entity to any other covered entity, to the interpretation of all
provisions of this Agreement, and to the resolution of all issues related to in?ormation sharing,
handling and use, and the coordination and deconfliction of operations and analytic conclusions:
Priority on Preemption. Prevention. and Disruption. All procedures,
guidelines, and mechanisms under this Agreement shall be designed and implemented,
and all determinations with regard to sharing information covered by this Agreement shall
be made, with the understood, overriding priority ofprevenring, preempting,
disrupting terrorist threats to our homeland. The parties recognize and agree that, in some
cases. this priority shall dictate information sharing even where doing so may affect.
criminal prosecutions or ongoing law enforcement or intelligence operations.
. Nonetheless, the covered entities shall act under this Agreement in a manner to protect, to
the greatest extent possible. these other signi?cant interests, including the prorection of
intelligence and sensitive law enforcement sources and methods, Other classi?ed
information, and sensitive operational and prosecutorial information.
Reciprocin and Transparency. All information collected by any covered
entity relevant to the missions and responsibilities of any other covered entities. should be
shared. to the greatest extent possible, between and among all covered entities. Likewise,
the parties agree that, to the greatest extent possible, there should be transparency
between and among the covered entities with regard to their activities to preempt,
prevent, and disrupt terrorist attacks against US. persons and interests. Except as
otherwise speci?ed in this Agreement, or mandated by relevant Federal statutes or
Presidential Directives, procedures and mechanisms for information sharing, use. and
handling shall be interpreted and implemented consistently and reciprocally regardless of
the role a particular covered entity plays as a provider or recipient of covered information.
In other words, for example, international terrorism information collected by the Border
Patrol should be shared by DHS with the to the same extent foreign intelligence
information on terrorism is shared by the IC with DHS.
information relating to groups or individuals reasonably believed to be assisting 0r
associated with them.
xtpueddv
?Vulnerabilities information" means all information relating to the
susceptibility - actual. perceived, or conceptual of the United States, including any
portion, sector, population. geographic area, or industry, to terrorist attack.
?Weapons of Mass Destruction information" or inf?nna?tion"
means terrorism information or Vulnerabilities information relating to conventional
explosive weapons and non-conventional weapons capable of causing mass casualties and
damage, including chemical orbiological agents, radioactive or nuclear materials, and the
means to deliver them. -
3. Policies and for lgt?ogation Sharing, Handling Ed use. Consistent
with the DHS Legislation, and except as otherwise speci?cally provided in this Agreement, the
following agreed-upon policies and procedures shall apply to the provision of covered
information by any covered entity to any other covered entity, to the interpretation of all
provisions of this Agreement, and to the resolution of all issues related to in?ormation sharing,
handling and use, and the coordination and deconfliction of operations and analytic conclusions:
Priority on Preemption. Prevention. and Disruption. All procedures,
guidelines, and mechanisms under this Agreement shall be designed and implemented,
and all determinations with regard to sharing information covered by this Agreement shall
be made, with the understood, overriding priority ofprevenring, preempting,
disrupting terrorist threats to our homeland. The parties recognize and agree that, in some
cases. this priority shall dictate information sharing even where doing so may affect.
criminal prosecutions or ongoing law enforcement or intelligence operations.
. Nonetheless, the covered entities shall act under this Agreement in a manner to protect, to
the greatest extent possible. these other signi?cant interests, including the prorection of
intelligence and sensitive law enforcement sources and methods, Other classi?ed
information, and sensitive operational and prosecutorial information.
Reciprocin and Transparency. All information collected by any covered
entity relevant to the missions and responsibilities of any other covered entities. should be
shared. to the greatest extent possible, between and among all covered entities. Likewise,
the parties agree that, to the greatest extent possible, there should be transparency
between and among the covered entities with regard to their activities to preempt,
prevent, and disrupt terrorist attacks against US. persons and interests. Except as
otherwise speci?ed in this Agreement, or mandated by relevant Federal statutes or
Presidential Directives, procedures and mechanisms for information sharing, use. and
handling shall be interpreted and implemented consistently and reciprocally regardless of
the role a particular covered entity plays as a provider or recipient of covered information.
In other words, for example, international terrorism information collected by the Border
Patrol should be shared by DHS with the to the same extent foreign intelligence
information on terrorism is shared by the IC with DHS.

'13
to
:3
(Jr
Scope of ?Covered Information. Consistent with the priority established
in Section information relating to terrorism, Weapons of Mass Destruction,
vulnerabilities, or other tirnctions of the Department of Homeland Security shall be
presumed to be ?covered information? under this AgreemenL If. after applying this
presumption, disagreement remains between covered entities about whether particular
information is ?covered information," such disagreement shall be resolved pursuant to
Section
E?ectr?ve date afinfonnotion sharing obligations. Notwithstanding
provisions of this Agreement mandating further agreement on mechanisms, procedures,
Or other issues, the parties recognize that the obligation to begin the hill range
of information sharing mandated by the DHS Legislation came into force on January 24,
2003, and that obligations under this Agreement will be in force updn the signature of all
parties.
Sharing Requirements Based on Substance Only. Consistent with the
DHS Legislation and other relevant statutory authorities. Presidential Directives, the
President?s announced policies for protecting against terrorist threats to the homeland.
and this Agreement, the parties agree that this Agreement requires that covered
information. including, but not limited to. terrorism information, WMD information,
infrastructure, and vulnerabilities information. be provided by any covered entity that
collects or analyzes that information to any other covered entity that has a need-to-know
that information (or information relating to that subject matter), based on a broad .
interpretation of the mission of the other covered entity. regardless of:
The ofcommun'cation in in i co rated.
Covered information must be provided as required in this Agreement regardless of
the type of communication in which it is originally reported by the providing
agency. The fact that particular covered information may be contained originally
in a particular type of communication shall not. under any circumstances. be
grounds either to withhold or delay the sharing of any covered information. As
illustrative examples only, covered information must be provided by CIA, within
the time frames agreed to, whether such information is contained originally in
communications referred to as ?intel cables." "cps cables," or any other
type of communication- Likewise, covered information must be provided by the
within the time frames agreed to, whether soch infomration is comained
originally in communications referred to as ?3025.? or any other
type of communication;
(ii) a oer in which the info ation ividual rcci icnts. Covered entities shall continually
endeavor to improve technological means of access to afford maximum
?exibility, speed, and volume of information shared. consistent with the strictly
necessary protection of intelligence or sensitive law enforcement sources and
methods, and with section 3(a) and other relevant previsions of this Agreement. .
'13
to
:3
(Jr
Scope of ?Covered Information. Consistent with the priority established
in Section information relating to terrorism, Weapons of Mass Destruction,
vulnerabilities, or other tirnctions of the Department of Homeland Security shall be
presumed to be ?covered information? under this AgreemenL If. after applying this
presumption, disagreement remains between covered entities about whether particular
information is ?covered information," such disagreement shall be resolved pursuant to
Section
E?ectr?ve date afinfonnotion sharing obligations. Notwithstanding
provisions of this Agreement mandating further agreement on mechanisms, procedures,
Or other issues, the parties recognize that the obligation to begin the hill range
of information sharing mandated by the DHS Legislation came into force on January 24,
2003, and that obligations under this Agreement will be in force updn the signature of all
parties.
Sharing Requirements Based on Substance Only. Consistent with the
DHS Legislation and other relevant statutory authorities. Presidential Directives, the
President?s announced policies for protecting against terrorist threats to the homeland.
and this Agreement, the parties agree that this Agreement requires that covered
information. including, but not limited to. terrorism information, WMD information,
infrastructure, and vulnerabilities information. be provided by any covered entity that
collects or analyzes that information to any other covered entity that has a need-to-know
that information (or information relating to that subject matter), based on a broad .
interpretation of the mission of the other covered entity. regardless of:
The ofcommun'cation in in i co rated.
Covered information must be provided as required in this Agreement regardless of
the type of communication in which it is originally reported by the providing
agency. The fact that particular covered information may be contained originally
in a particular type of communication shall not. under any circumstances. be
grounds either to withhold or delay the sharing of any covered information. As
illustrative examples only, covered information must be provided by CIA, within
the time frames agreed to, whether such information is contained originally in
communications referred to as ?intel cables." "cps cables," or any other
type of communication- Likewise, covered information must be provided by the
within the time frames agreed to, whether soch infomration is comained
originally in communications referred to as ?3025.? or any other
type of communication;
(ii) a oer in which the info ation ividual rcci icnts. Covered entities shall continually
endeavor to improve technological means of access to afford maximum
?exibility, speed, and volume of information shared. consistent with the strictly
necessary protection of intelligence or sensitive law enforcement sources and
methods, and with section 3(a) and other relevant previsions of this Agreement. .

(1) Terrorist Threat Integration Center. The parties agree that. when fully
operational. the Terrorist Threat Integration Center (TTIC) shall be the preferred, though
not the exclusive, method for sharing covered, information at the national level:
information-sharing mechanisms and procedures shall be consistent with the DHS
Legislation and other relevant statutory authorities, Presidential Directives, the
President?s announced policies for protecting against terrorist threats to the homeland.
and this Agreement. As soon as practicable, the parties shall determine the extent to
which provision of information to one or more covered entities via the 'l'l'lC may
constitute the only required mahod for providing such information to such entities.
provided however. that any_decision to share covered information among the parties
solely by mean of the shall be memorialized in a separate written agreement
executed by the parties, including by dcsignees of the o??rcials signing this Agreement.
Analytic conclusions contained in products shall 'not be altered by agencies prior to
dissemination. -
Policies for Sharing Particular Types oflnfonnan'on With DHS.
Consistent with the DHS Legislation and other relevant statutory authorities, Presidential
Directives, the President's announced policies for protecting against terrorist threats to
the homeland, and this Agreement, the Secretary shall be provided access toall
information necessary for him to carry out the mission of the Department. Except as
otherwise directed by the President, the parties agree that the amount of information and
depth of detail of information provided to the Secretary, which will vary by the type of
information at issue, will be governed by the following policies:
elat of ainst the 'ted
grates. As required by the DHS Legislation, DHS shall be provided. without
request, all ?reports (including information repons containing intelligence which
has not been fully evaluated), assessments, and analytical information." The
parties understand that, in this category, except upon further request by DHS, and
ageemcnt by the originating entity, provided information will not routinely
include information, collected through intelligence sources or methods, or
sensitive law enfOrecment sources or methods, which has not been processed in
any way to reduce the amount of substantive content or the material.
Thus, for example, a recording of a conversation intercepted under the Foreign
Intelligence Surveillance Act or an intelligence of?cer's or FBI agent?s
hand-written notes of a discussion with a source would not be routinely provided
in this'category. By contrast, a report forwarding the substgice of a
recorded conversation, or an FBI "Electronic Communication" (BC), including the
substance of a discussion with a source, even ifthese include verbatim quotes
from the underlying notes, would be provided. ECs containing substantive
information, along with "3025," ?lle," and all other similar
including substantive information, fall into the category of information to be
provided. The parties agree, as soon as practicable. to identify andlor put into
place necessary and reasonable mechanisms, including, when operational, the
THC, along with the Joint Terrorism Task Forces and procedures, to
ensure that DHS receives all such information automatically, under the policies
(o
:3
9-.
u.
(1) Terrorist Threat Integration Center. The parties agree that. when fully
operational. the Terrorist Threat Integration Center (TTIC) shall be the preferred, though
not the exclusive, method for sharing covered, information at the national level:
information-sharing mechanisms and procedures shall be consistent with the DHS
Legislation and other relevant statutory authorities, Presidential Directives, the
President?s announced policies for protecting against terrorist threats to the homeland.
and this Agreement. As soon as practicable, the parties shall determine the extent to
which provision of information to one or more covered entities via the 'l'l'lC may
constitute the only required mahod for providing such information to such entities.
provided however. that any_decision to share covered information among the parties
solely by mean of the shall be memorialized in a separate written agreement
executed by the parties, including by dcsignees of the o??rcials signing this Agreement.
Analytic conclusions contained in products shall 'not be altered by agencies prior to
dissemination. -
Policies for Sharing Particular Types oflnfonnan'on With DHS.
Consistent with the DHS Legislation and other relevant statutory authorities, Presidential
Directives, the President's announced policies for protecting against terrorist threats to
the homeland, and this Agreement, the Secretary shall be provided access toall
information necessary for him to carry out the mission of the Department. Except as
otherwise directed by the President, the parties agree that the amount of information and
depth of detail of information provided to the Secretary, which will vary by the type of
information at issue, will be governed by the following policies:
elat of ainst the 'ted
grates. As required by the DHS Legislation, DHS shall be provided. without
request, all ?reports (including information repons containing intelligence which
has not been fully evaluated), assessments, and analytical information." The
parties understand that, in this category, except upon further request by DHS, and
ageemcnt by the originating entity, provided information will not routinely
include information, collected through intelligence sources or methods, or
sensitive law enfOrecment sources or methods, which has not been processed in
any way to reduce the amount of substantive content or the material.
Thus, for example, a recording of a conversation intercepted under the Foreign
Intelligence Surveillance Act or an intelligence of?cer's or FBI agent?s
hand-written notes of a discussion with a source would not be routinely provided
in this'category. By contrast, a report forwarding the substgice of a
recorded conversation, or an FBI "Electronic Communication" (BC), including the
substance of a discussion with a source, even ifthese include verbatim quotes
from the underlying notes, would be provided. ECs containing substantive
information, along with "3025," ?lle," and all other similar
including substantive information, fall into the category of information to be
provided. The parties agree, as soon as practicable. to identify andlor put into
place necessary and reasonable mechanisms, including, when operational, the
THC, along with the Joint Terrorism Task Forces and procedures, to
ensure that DHS receives all such information automatically, under the policies
(o
:3
9-.
u.

and procedures agreed to in this Agreement, without further request.
(ii) As required by the DHS Legislation,
DHS shall be provided. without request. all information of any kind concerning
?the vulnerability of the infrastructure of the United States; or other vulnerabilities
of the United States. to terrorism, whether or not such information has been
analyzed." The parties understand that, in this category. without further requeSt
by DHS, provided information will routinely include information. collected
through intelligence sources or methods, or sensitive law enforcement sources or
methods. which has not been processed in any way to reduce the amount of
substantive content or the material. Provided information will include
all types of information. without regard to the distinctions drawn by way of . .
example in Section except as further agreed to by the parties or their
dcsignees. The parties agree. as soon as practicable, to identify and/or put into
place necessary and reasonable mechanisms, including. when Operational. the
along with the and procedures. to ensure that DHS receives all such
information. under the principles agreed to in this Agreement. without ?rrther
request.
Information Relatng to Signi?cant and Credible Threats of
jljenorism. As required by the DHS Legislation. DHS shall be provided. without
request. all information of any kind concerning ?signi?cant and credible threats of
terrorism against the United States. whether or not such information has been
analyzed." The parties understand that. in this category. without ?rrther request
by DHS. provided information will routinely include information. collected
throttin intelligence sources or methods, or sensitive law enforcement sources or
methods. which has not been processed in any way to reduce the amount of
substantive content or the material. Provided information will include
all types of information. without regard to the distinctions drawn by way of
example in Section except as further agreed to by the parties or their
designees. The parties agree. as soon as practicable, to identify and/or put into
place necessary and reasonable mechanisms. including. when operational. the
TTIC. along with the and procedures. to ensure that DHS receives all such
information, under the principles agreed to in this Agreement. without further
request.
(iv) er Inf rmati the Secrets . The Secretary shall
be provided. upon request. with such other informatiOn relating to threats of
terrorism againsr the United States or to other areas of responsibility.
whether or not such information has been analyzed. The parties understand that
DHS will be provided information in this category upon request including. if so
requested. infomration which has not been processed in any way to reduce the
amount of substantiVe content or the material. If so requested.
provided information will include all types of information. without regard to the
distinctions drawn by way of example in Section except as otherwise
directed by the President. The parties agree. as soon as practicable
and procedures agreed to in this Agreement, without further request.
(ii) As required by the DHS Legislation,
DHS shall be provided. without request. all information of any kind concerning
?the vulnerability of the infrastructure of the United States; or other vulnerabilities
of the United States. to terrorism, whether or not such information has been
analyzed." The parties understand that, in this category. without further requeSt
by DHS, provided information will routinely include information. collected
through intelligence sources or methods, or sensitive law enforcement sources or
methods. which has not been processed in any way to reduce the amount of
substantive content or the material. Provided information will include
all types of information. without regard to the distinctions drawn by way of . .
example in Section except as further agreed to by the parties or their
dcsignees. The parties agree. as soon as practicable, to identify and/or put into
place necessary and reasonable mechanisms, including. when Operational. the
along with the and procedures. to ensure that DHS receives all such
information. under the principles agreed to in this Agreement. without ?rrther
request.
Information Relatng to Signi?cant and Credible Threats of
jljenorism. As required by the DHS Legislation. DHS shall be provided. without
request. all information of any kind concerning ?signi?cant and credible threats of
terrorism against the United States. whether or not such information has been
analyzed." The parties understand that. in this category. without ?rrther request
by DHS. provided information will routinely include information. collected
throttin intelligence sources or methods, or sensitive law enforcement sources or
methods. which has not been processed in any way to reduce the amount of
substantive content or the material. Provided information will include
all types of information. without regard to the distinctions drawn by way of
example in Section except as further agreed to by the parties or their
designees. The parties agree. as soon as practicable, to identify and/or put into
place necessary and reasonable mechanisms. including. when operational. the
TTIC. along with the and procedures. to ensure that DHS receives all such
information, under the principles agreed to in this Agreement. without further
request.
(iv) er Inf rmati the Secrets . The Secretary shall
be provided. upon request. with such other informatiOn relating to threats of
terrorism againsr the United States or to other areas of responsibility.
whether or not such information has been analyzed. The parties understand that
DHS will be provided information in this category upon request including. if so
requested. infomration which has not been processed in any way to reduce the
amount of substantiVe content or the material. If so requested.
provided information will include all types of information. without regard to the
distinctions drawn by way of example in Section except as otherwise
directed by the President. The parties agree. as soon as practicable

i
necessary and reasonable mechanisms, including, when operational, the
along with the and procedures, to ensure that DHS, when requeIsted,
receives all such information, under the principles agreed to in this Agreement. .
Timely Sharing of Information. Covered information must be provided to
those with a needsto-ltnow that information (or information relating to that subject
matter), based on a broad interpretation of the mission of the other covered entity. as
quickly as possible. Providing all timely and relevant covered information to those who
have a need-to-know it in order to assist them in meeting their homeland security-related
mponsibilities is fundamental to the success of the Department and all other efforts to
ensure the security of the homeland from terrorist attack. Delay in providing such
information risks frustrating efforts to meet these critical reSponsibilities and could result
in preventable attacks against 0.5. persons or interests failing to be preempted, prevented,
or disrupted. Accordingly, except as otherwise directed by the President or agreed to by
all parties. the parties agree that:
Information that a covered entity reasonably believes relates to a
potential terrorism 0r WMD threat. to the United States homeland, its
infrastructure, or to United States persons or interests, shall be provided
immediately to other covered entities;
(ii) Other covered information, including, but not limited to,
vulnerabilities information, but which a covered entity does not reasonably
believe relates to a potential terrorism or WMD threat to the United States
homeland. its infrastrucrure, or to United States persons or interests, shall be
provided as expeditiome as possible;
Under no circumstances may covered information be withheld
from a covered entity with a need-to-know that information (or information
relating to that subject matter), based on a broad interpretation of the mission of
the other covered entity, or may the sharing of such information be delayed
beyond the time frames agreed to in this Agreement. except as consistent with the
Section or other relevant provisions of this Agreement; -
(iv) When a question arises as to whether covered information must be
provided to the Department or any other covered entity pursuant to this
Agreement, the parties will resolve the question pursuant to Section
Covered entities agree to use, to the greatwt extent possible, the
most rapid methods of information sharing, consistent with the strictly necessary
protection of intelligence or sensitive law enforcement sources and methods, and
with Section 3(a) and other relevant provisions of this Agreement; and
(vi) Consistent with Section 3, and other relevant provisions of this
Agreement, the parties agree that they shall work diligently to ensure that all
covered entities receive the sumo information within the same time frame.
xtpuoddv
i
necessary and reasonable mechanisms, including, when operational, the
along with the and procedures, to ensure that DHS, when requeIsted,
receives all such information, under the principles agreed to in this Agreement. .
Timely Sharing of Information. Covered information must be provided to
those with a needsto-ltnow that information (or information relating to that subject
matter), based on a broad interpretation of the mission of the other covered entity. as
quickly as possible. Providing all timely and relevant covered information to those who
have a need-to-know it in order to assist them in meeting their homeland security-related
mponsibilities is fundamental to the success of the Department and all other efforts to
ensure the security of the homeland from terrorist attack. Delay in providing such
information risks frustrating efforts to meet these critical reSponsibilities and could result
in preventable attacks against 0.5. persons or interests failing to be preempted, prevented,
or disrupted. Accordingly, except as otherwise directed by the President or agreed to by
all parties. the parties agree that:
Information that a covered entity reasonably believes relates to a
potential terrorism 0r WMD threat. to the United States homeland, its
infrastructure, or to United States persons or interests, shall be provided
immediately to other covered entities;
(ii) Other covered information, including, but not limited to,
vulnerabilities information, but which a covered entity does not reasonably
believe relates to a potential terrorism or WMD threat to the United States
homeland. its infrastrucrure, or to United States persons or interests, shall be
provided as expeditiome as possible;
Under no circumstances may covered information be withheld
from a covered entity with a need-to-know that information (or information
relating to that subject matter), based on a broad interpretation of the mission of
the other covered entity, or may the sharing of such information be delayed
beyond the time frames agreed to in this Agreement. except as consistent with the
Section or other relevant provisions of this Agreement; -
(iv) When a question arises as to whether covered information must be
provided to the Department or any other covered entity pursuant to this
Agreement, the parties will resolve the question pursuant to Section
Covered entities agree to use, to the greatwt extent possible, the
most rapid methods of information sharing, consistent with the strictly necessary
protection of intelligence or sensitive law enforcement sources and methods, and
with Section 3(a) and other relevant provisions of this Agreement; and
(vi) Consistent with Section 3, and other relevant provisions of this
Agreement, the parties agree that they shall work diligently to ensure that all
covered entities receive the sumo information within the same time frame.
xtpuoddv

Agreement. to withhold in its entirety 'a communication containing covered
information, such indication shall occur immediately.
xgpueddv
The parties agree that the pr0visi'ons of this section shalli not apply
to established source protection procedures utilized by ClA?s Directorate of
Operations. or equivalent procedures develoPed and used by other covered
entities, provided that such procedures do not result in the failure to provide DHS
with substantive information as required under the DHS Legislation and this
Agreement, and that the Secretary may personally request revisions in such
prooedures if he determines that they restrict access to information in a way
that jeopardizes mission. For information described in Section such
procedures shall be revised, as soon as is practicable. and without request from the
Secretary, to ensure that those procedures?onl remove such intelligence that
clearly identi?es, or would reasonany permit ready identi?cation of, intelligence
or sensitive law enforcement sources or methods that are particularly susceptible
to countermeasures that would nullify or measurably reduce their effectiveness.
0) Requests for Additional Information. In additiOn to the participation of
DHS in the processes. as discussed further herein, the DHS Legislation
provides for DHS to request additional or follow-up information upon receipt of
individual items of infurmation. As soon as practicable, the parties shall agree.to
mechanisms and procedures, including the 'lTlC, and. if appropriate, focal points,
for DHS to make. and covered entities to respond to, such requests. These mechanisms
and procedures shall be designed to facilitate the greatest amount of additional
information sharing consistent with strictly necessary protection of intelligencqor
sensitive law enforcement sources and methods, with Section 3(a) and other relevant
provisions of this Agreement. and with the timeliest possible responses to requesrs for
additional information.
(it) [nformtion Use Restrictions. In general. parties shall disclose covered
information free of any originator controls or information use restrictions. Several
categories of covered information that must be disclosed to covered entities pursuant to
the DHS Legislation. this Agreement. and other authorities. remain subject to special
labeling. handling, storage, use and access auditing requirements imposed by statute or. to
the extent consistent with the DHS Legislation. Presidential Directives, the President's
announced policies for protecting against terrorist threats to the homeland, and this
Agreement. pursuant to applicable regulations. The scope and duration of such
restrictions. including caveats restricting use of the disclosed information to a particular
level or element of a covered entity, will be tailored to address the particular situation 01'
subject matter involved. When imposed, use restrictions shall be no more restrictive than
strictly necessary to accomplish the desired effect.
(I Secondary Information Sharing. To the extent consistent with this
Agreement. covered entities may share information provided by other covered entities
with additional covered entities. Such secondary sharing shall be carried out. to the
greatest extent possible. in a manner that permits the originating agency to know to
ID
Agreement. to withhold in its entirety 'a communication containing covered
information, such indication shall occur immediately.
xgpueddv
The parties agree that the pr0visi'ons of this section shalli not apply
to established source protection procedures utilized by ClA?s Directorate of
Operations. or equivalent procedures develoPed and used by other covered
entities, provided that such procedures do not result in the failure to provide DHS
with substantive information as required under the DHS Legislation and this
Agreement, and that the Secretary may personally request revisions in such
prooedures if he determines that they restrict access to information in a way
that jeopardizes mission. For information described in Section such
procedures shall be revised, as soon as is practicable. and without request from the
Secretary, to ensure that those procedures?onl remove such intelligence that
clearly identi?es, or would reasonany permit ready identi?cation of, intelligence
or sensitive law enforcement sources or methods that are particularly susceptible
to countermeasures that would nullify or measurably reduce their effectiveness.
0) Requests for Additional Information. In additiOn to the participation of
DHS in the processes. as discussed further herein, the DHS Legislation
provides for DHS to request additional or follow-up information upon receipt of
individual items of infurmation. As soon as practicable, the parties shall agree.to
mechanisms and procedures, including the 'lTlC, and. if appropriate, focal points,
for DHS to make. and covered entities to respond to, such requests. These mechanisms
and procedures shall be designed to facilitate the greatest amount of additional
information sharing consistent with strictly necessary protection of intelligencqor
sensitive law enforcement sources and methods, with Section 3(a) and other relevant
provisions of this Agreement. and with the timeliest possible responses to requesrs for
additional information.
(it) [nformtion Use Restrictions. In general. parties shall disclose covered
information free of any originator controls or information use restrictions. Several
categories of covered information that must be disclosed to covered entities pursuant to
the DHS Legislation. this Agreement. and other authorities. remain subject to special
labeling. handling, storage, use and access auditing requirements imposed by statute or. to
the extent consistent with the DHS Legislation. Presidential Directives, the President's
announced policies for protecting against terrorist threats to the homeland, and this
Agreement. pursuant to applicable regulations. The scope and duration of such
restrictions. including caveats restricting use of the disclosed information to a particular
level or element of a covered entity, will be tailored to address the particular situation 01'
subject matter involved. When imposed, use restrictions shall be no more restrictive than
strictly necessary to accomplish the desired effect.
(I Secondary Information Sharing. To the extent consistent with this
Agreement. covered entities may share information provided by other covered entities
with additional covered entities. Such secondary sharing shall be carried out. to the
greatest extent possible. in a manner that permits the originating agency to know to
ID

whom the infarrnation has been provided. The parties shall agree, as soon as is
practicable, upon recommendations, if any, for changes to Executive Order 12958,
Director of Central Intelligence Directive 6/6 (and complementary or successor directives
dealing with Originator Controls, the so-called ?third agency rule," and other policies or
procedures governing the sharing of received information with additional recipients) in
order to comply with the DHS Legislation, and to any out the President's announced
policies for protecting against terrorist threats to the homeland, and the provisions of this
A greement.
Other Obligation: to Share Information. A covered entity's voluntary or
obligatory pr0vision of covered information to another covered entity does not in itself
discharge or diminish any other obligation the-providing entity may have to provide that
information, or any part of it, to any other department, agency or other public or private
organization or individual under any statute, Presidential Directive, or other agreement.
Although all covered entities will attempt to identify and call attention to information
relevant to the mission of other covered entities. the responsibility to share information
relevant to the mission or responsibilities of any covered entity in addition to DHS
remains the responsibility of the originator or initial federal recipient of the information
and does not shift to DHS by virtue of receipt of the information. The parties
agree, however, that, to the greatest cxrent possible, other sharing obligations shall be
harmonized and coordinated with those covered by this Agreement, including the agreed
preference for using the 111C and as information-sharing mechanisms, in order to
reduce duplication, facilitate decon?iction, and increase ef?ciency.
PA Information. Law enforcernent~related informatiOn related
to DHS mission, permitted or required to be provided to intelligence agencies under the
PATRIOT Act and its implementing guidelines shall also be considered covered
information under this Agreement and shall, therefore. be provided to the Department and
other covered entities, in accordance with the DHS Legislation and other relevant
statutory provisions. and this Agreement.
(0) Other Intelligence Information. Nothing in this Agreement shall be read
to restrict the access of the Secretary or his designee to information the Secretary
ordinarily would receive as a member of the Intelligence Community, including national
security and foreign intelligence information.
Information Sharing Mechanisms. As soon as practicable, the parties shall
agree upon specific mechanisms, consistent with Section 3 and other relevant provisions
of this Agreement, for how different types of covered infomtation will be shared,
including technical and administrative arrangements. and, as appropriate, designation of
focal points, to maximize the effectiveness and coordination for providing covered
information. Subsequent arrangements for information sharing may he reached upon the
approval of the parties or their designees. The parties shall work to develop. as part of
this process, effective mechanisms for covered entities to identify covered information
held by them and to ensure, to the greatest degree feasible, the provision of such
information. without speci?c request, to other covered entities. The parties further agree .
whom the infarrnation has been provided. The parties shall agree, as soon as is
practicable, upon recommendations, if any, for changes to Executive Order 12958,
Director of Central Intelligence Directive 6/6 (and complementary or successor directives
dealing with Originator Controls, the so-called ?third agency rule," and other policies or
procedures governing the sharing of received information with additional recipients) in
order to comply with the DHS Legislation, and to any out the President's announced
policies for protecting against terrorist threats to the homeland, and the provisions of this
A greement.
Other Obligation: to Share Information. A covered entity's voluntary or
obligatory pr0vision of covered information to another covered entity does not in itself
discharge or diminish any other obligation the-providing entity may have to provide that
information, or any part of it, to any other department, agency or other public or private
organization or individual under any statute, Presidential Directive, or other agreement.
Although all covered entities will attempt to identify and call attention to information
relevant to the mission of other covered entities. the responsibility to share information
relevant to the mission or responsibilities of any covered entity in addition to DHS
remains the responsibility of the originator or initial federal recipient of the information
and does not shift to DHS by virtue of receipt of the information. The parties
agree, however, that, to the greatest cxrent possible, other sharing obligations shall be
harmonized and coordinated with those covered by this Agreement, including the agreed
preference for using the 111C and as information-sharing mechanisms, in order to
reduce duplication, facilitate decon?iction, and increase ef?ciency.
PA Information. Law enforcernent~related informatiOn related
to DHS mission, permitted or required to be provided to intelligence agencies under the
PATRIOT Act and its implementing guidelines shall also be considered covered
information under this Agreement and shall, therefore. be provided to the Department and
other covered entities, in accordance with the DHS Legislation and other relevant
statutory provisions. and this Agreement.
(0) Other Intelligence Information. Nothing in this Agreement shall be read
to restrict the access of the Secretary or his designee to information the Secretary
ordinarily would receive as a member of the Intelligence Community, including national
security and foreign intelligence information.
Information Sharing Mechanisms. As soon as practicable, the parties shall
agree upon specific mechanisms, consistent with Section 3 and other relevant provisions
of this Agreement, for how different types of covered infomtation will be shared,
including technical and administrative arrangements. and, as appropriate, designation of
focal points, to maximize the effectiveness and coordination for providing covered
information. Subsequent arrangements for information sharing may he reached upon the
approval of the parties or their designees. The parties shall work to develop. as part of
this process, effective mechanisms for covered entities to identify covered information
held by them and to ensure, to the greatest degree feasible, the provision of such
information. without speci?c request, to other covered entities. The parties further agree .

that. notwithstanding their agreement to develop further mechanisms and procedures for
information sharing, covered entities shall build on mechanisms and procedures
already in place to identify and provide to OHS covered information that is generated or
received by them in the course of carrying out their missions.
Methods of Providing Information. The parties recognize and agree that
there are many possible methods for "providing" information, including, but not limited
to. hand-delivery. oral brie?ngs. transmission by secure data-link. and affording routine
and unrestricted access to computerized databases, including the ability to transfer such
information to a recipient entity as nectssuy. and by full and complete oo-location of
or other personnel and full integration of. and access to. information, as well as.
for example, ensuring that the Secretary receives all dain threat brie?ng materials
(including thrat matrices and overnight reports). The parties further agree that
requirements to ?provide? information under this Agreemmt may be satisfied. depending
on the type of information at issue. by the use of a single mechanism. such as via the
TTIC, consistent with section 3(0 of this Ayeement. or a combination of mechanisms
already in place andlor created under this Agreement. The parties shall agree. as part of
the development of these mechanisms and procedures. as to which method, or
combination of methods. of providing information will be suf?cient for particular types
or categories of information.
Raponst?ble Q?t?cial: for Information Sharing. Until such time as
modi?ed by the parties, the responsible officials for information sharing under this
Agreement are as follows:
For the Secretary of Homeland Security. the Undersecretary for
information Analysis and Infrastructure Protection, or another individual
designated by the Secretary to act in this capacity;
(ii) For the Attorney General, Executive Assistant Director for
Counterterrorism and Counterintelligence; and
For the Director of Central Intelligence, the Associate Director of
Central Intelligence for Homeland Security.
(5) Provision of Cavered Information to the DHS Directorate of Information
Analysis and In?asrrucmre Protection. Until further agreement by the parties. or their
designees. all covered information provided. including information provided. under
current procedures, to existing elements transferred to OHS. the United States Coast
Guard and the U.S. Customs Service. shall also be separately provided to the Directorate
of information Analysis and Infrastructure Protecrion. including. if agreed by the
Secretary. via the ?I'l?lC. The Undersecretary for information and Infrastructure
Protection, or another individual designated by the Secretary to act in this capacity. shall
work with entities not within the Directorate to ensure effective coordination of
information.
'13
n:
:1
that. notwithstanding their agreement to develop further mechanisms and procedures for
information sharing, covered entities shall build on mechanisms and procedures
already in place to identify and provide to OHS covered information that is generated or
received by them in the course of carrying out their missions.
Methods of Providing Information. The parties recognize and agree that
there are many possible methods for "providing" information, including, but not limited
to. hand-delivery. oral brie?ngs. transmission by secure data-link. and affording routine
and unrestricted access to computerized databases, including the ability to transfer such
information to a recipient entity as nectssuy. and by full and complete oo-location of
or other personnel and full integration of. and access to. information, as well as.
for example, ensuring that the Secretary receives all dain threat brie?ng materials
(including thrat matrices and overnight reports). The parties further agree that
requirements to ?provide? information under this Agreemmt may be satisfied. depending
on the type of information at issue. by the use of a single mechanism. such as via the
TTIC, consistent with section 3(0 of this Ayeement. or a combination of mechanisms
already in place andlor created under this Agreement. The parties shall agree. as part of
the development of these mechanisms and procedures. as to which method, or
combination of methods. of providing information will be suf?cient for particular types
or categories of information.
Raponst?ble Q?t?cial: for Information Sharing. Until such time as
modi?ed by the parties, the responsible officials for information sharing under this
Agreement are as follows:
For the Secretary of Homeland Security. the Undersecretary for
information Analysis and Infrastructure Protection, or another individual
designated by the Secretary to act in this capacity;
(ii) For the Attorney General, Executive Assistant Director for
Counterterrorism and Counterintelligence; and
For the Director of Central Intelligence, the Associate Director of
Central Intelligence for Homeland Security.
(5) Provision of Cavered Information to the DHS Directorate of Information
Analysis and In?asrrucmre Protection. Until further agreement by the parties. or their
designees. all covered information provided. including information provided. under
current procedures, to existing elements transferred to OHS. the United States Coast
Guard and the U.S. Customs Service. shall also be separately provided to the Directorate
of information Analysis and Infrastructure Protecrion. including. if agreed by the
Secretary. via the ?I'l?lC. The Undersecretary for information and Infrastructure
Protection, or another individual designated by the Secretary to act in this capacity. shall
work with entities not within the Directorate to ensure effective coordination of
information.
'13
n:
:1

Classified Information The head of each covered entity shall put
procedures in place to ensure that each individual recipient of classi?ed information has.
and maintains, appropriate security clearances, training, and need-to?know to receive
classi?ed information at the level at which the recipient will receive such information.
Individuals shall be designated at each covered entity at several levels of seniority to
receive classi?ed information judged by the originating agency to be suf?ciently
sensitive to require limited distribution. in rare cases, the parties expect that extremely
sensitive information may be provided only to the Secretary or, as appropriate. the head
of another covered entity. The head of each covered entity also shall ensure that all
mechanisms and procedures for receiving, storing, and handling classi?ed information
meet established legal and regulatory standards. The policies and procedures governing
access to covered information under this Agreement. including such information that is
classi?ed, shall apply without regard to whether that information is made available in
written, oral, or electronic form, or to the means or mechanism by which it is
communicated to the recipient.
Thresholds. In order to ensure that the Department is provided with all
information necessary to carry out its responsibilities, but is not inundated with
unmanageable volumes of information below thresholds reasonable to perform its
mission, as soon as practicable. the Secretary shall advise the other parties, individually
or collectively. as to establishing additioaal thresholds for information sharing, consistent
with the DHS Legislation. For example. the Secretary may determine that low-level
information concerning purely indigenous foreign terrorist groups with no apparent
capability to mount operations against the United States is not relevant to mission.
Such ?rrther agreement shall be consistent with the DHS Legislation and other relevant
statutory authorities, Presidential Directives. the President?s announced policies for
protecting against terrorist threats to the homeland. and this Agreement. At any time
following such initial agreement. the parties may agree to additional information sharing.
or to more or less restrictive thresholds, as the volume of information involved and the
needs of DHS become clearer, so long as such agreements are consistent with the DHS
Legislation and this Agreement. Such agreements may be made by designees of the
parties.
Privacy. All information sharing pursuant to this Agreement shall be
consistent with applicable privacy laws.
4. nggdinatign, Decon?iclion, and [213mg nglution.
Coordination and Deeon?iction Policy. Consistent with the President's
direction that our highest priority is the protection of the American people from
potentially devastating terrorist attacks. covered entities shall take all necessary measures
to ensure that terrorist threats to our homeland are addressed cooperatively. ef?ciently,
and with the understood overriding purpose of preventing, precarpting, and dismpting
those threats. To that end, the parties agree that no homeland security-related prevention.
preemption. or disruption acrivity of any covered entity shall be presumed to be the best
Option in any given case. or otherwise deemed of higher precedence. importance. or
gpuaddv
Classified Information The head of each covered entity shall put
procedures in place to ensure that each individual recipient of classi?ed information has.
and maintains, appropriate security clearances, training, and need-to?know to receive
classi?ed information at the level at which the recipient will receive such information.
Individuals shall be designated at each covered entity at several levels of seniority to
receive classi?ed information judged by the originating agency to be suf?ciently
sensitive to require limited distribution. in rare cases, the parties expect that extremely
sensitive information may be provided only to the Secretary or, as appropriate. the head
of another covered entity. The head of each covered entity also shall ensure that all
mechanisms and procedures for receiving, storing, and handling classi?ed information
meet established legal and regulatory standards. The policies and procedures governing
access to covered information under this Agreement. including such information that is
classi?ed, shall apply without regard to whether that information is made available in
written, oral, or electronic form, or to the means or mechanism by which it is
communicated to the recipient.
Thresholds. In order to ensure that the Department is provided with all
information necessary to carry out its responsibilities, but is not inundated with
unmanageable volumes of information below thresholds reasonable to perform its
mission, as soon as practicable. the Secretary shall advise the other parties, individually
or collectively. as to establishing additioaal thresholds for information sharing, consistent
with the DHS Legislation. For example. the Secretary may determine that low-level
information concerning purely indigenous foreign terrorist groups with no apparent
capability to mount operations against the United States is not relevant to mission.
Such ?rrther agreement shall be consistent with the DHS Legislation and other relevant
statutory authorities, Presidential Directives. the President?s announced policies for
protecting against terrorist threats to the homeland. and this Agreement. At any time
following such initial agreement. the parties may agree to additional information sharing.
or to more or less restrictive thresholds, as the volume of information involved and the
needs of DHS become clearer, so long as such agreements are consistent with the DHS
Legislation and this Agreement. Such agreements may be made by designees of the
parties.
Privacy. All information sharing pursuant to this Agreement shall be
consistent with applicable privacy laws.
4. nggdinatign, Decon?iclion, and [213mg nglution.
Coordination and Deeon?iction Policy. Consistent with the President's
direction that our highest priority is the protection of the American people from
potentially devastating terrorist attacks. covered entities shall take all necessary measures
to ensure that terrorist threats to our homeland are addressed cooperatively. ef?ciently,
and with the understood overriding purpose of preventing, precarpting, and dismpting
those threats. To that end, the parties agree that no homeland security-related prevention.
preemption. or disruption acrivity of any covered entity shall be presumed to be the best
Option in any given case. or otherwise deemed of higher precedence. importance. or
gpuaddv

priority than any other such activity. The covered emities shall work together, lo the
greatest extent possible, to achieve, in each case, the maximum preventative, preemptive,
and disruptive e?ect on potential threats, including coordinating simultaneous and
complementary activities of multiple covered entities when appropriate. Because the
failure to coordinate operatiOnal activities to preempt. prevent, and disrupt terrorist
threats can create'confusion, inefficiency and, in extreme cases, dangerous situations
resulting from conflicting Operational activities, the parties agree to coordinate.
. operational activities to the greatest possible extent. Speci?cally. each party shall take all
reasonable steps to ensure coordination and decon?iction of homeland security-related
law enforcement, intelligence or national security-related activities of covered entities
under that party?s.authority with such activities of other covered entities.
xrpuoddv
Analytic Conclusions and Supporting lnfomrarion. Terrorism and other
homeland-security related analytic efforts of all covered entities must be inforrned by the
most comprehensive, accurate, and timely information available, regardless of its nature
and source, including, but not limited to, terrorism, WMD, vulnerabilities, and other
pertinent information available to any covered entity. Analytic conclusions relating to
terrorist or WMD threats to the homeland, or other issues within the responsibility of
including information updating and amplifying previous conclusions, must be
shared with all covered entities as soon as they are produced. Preemptive. preventative.
and disruptive actions by all covered entities must be informed to the greatest extent
possible by all available information and by all analytic conclusions, including competing
conclusions, of all entities with relevant analytic responsibilities. At the same time. the
Federal government must, to the greatest extent possible, speak with one voice to state
and local of?cials. private industry, and the public. in order to prevent con?rsion. mixed
signals, and. potentially, dangerous operational con?icts. In ?rrtherance of these goals,
the parties agree as follows:
The parties shall ensure that covered entities disseminate their
terrorism or other homeland security-related analytic products without delay to
other covered entities that have related interests and responsibilities;
(ii) Except as otherwise provided in Sections 4(inii) or no
analytic canclusions, as de?ned in Section 2(a) of this Agreement, of any covered
entity shall be disseminated to state, local, or private sector of?cials, or to the
public, without the prior approval of the Secretary of Homeland Security, his
designee, or in accordance with approval mechanisms, potentially including the
or the established by the Secretary alter the date of this Agreement.
Analytic conclusions may be provided directly to such of?cials or
to the public where the head of a covered entity or his or her designcc reasonably
determines that exigent circumstances exist such that providing an analytic
conclusion prior to required approval is necessary to prevent. preempt, or disrupt
an imminmt threat of death or serious bodily injury or signi?cant damage to US.
or other interests. In the event an analytic conclusion is -
disseminated pursuant to the exigent circumstances exception in this paragraph,
l4
priority than any other such activity. The covered emities shall work together, lo the
greatest extent possible, to achieve, in each case, the maximum preventative, preemptive,
and disruptive e?ect on potential threats, including coordinating simultaneous and
complementary activities of multiple covered entities when appropriate. Because the
failure to coordinate operatiOnal activities to preempt. prevent, and disrupt terrorist
threats can create'confusion, inefficiency and, in extreme cases, dangerous situations
resulting from conflicting Operational activities, the parties agree to coordinate.
. operational activities to the greatest possible extent. Speci?cally. each party shall take all
reasonable steps to ensure coordination and decon?iction of homeland security-related
law enforcement, intelligence or national security-related activities of covered entities
under that party?s.authority with such activities of other covered entities.
xrpuoddv
Analytic Conclusions and Supporting lnfomrarion. Terrorism and other
homeland-security related analytic efforts of all covered entities must be inforrned by the
most comprehensive, accurate, and timely information available, regardless of its nature
and source, including, but not limited to, terrorism, WMD, vulnerabilities, and other
pertinent information available to any covered entity. Analytic conclusions relating to
terrorist or WMD threats to the homeland, or other issues within the responsibility of
including information updating and amplifying previous conclusions, must be
shared with all covered entities as soon as they are produced. Preemptive. preventative.
and disruptive actions by all covered entities must be informed to the greatest extent
possible by all available information and by all analytic conclusions, including competing
conclusions, of all entities with relevant analytic responsibilities. At the same time. the
Federal government must, to the greatest extent possible, speak with one voice to state
and local of?cials. private industry, and the public. in order to prevent con?rsion. mixed
signals, and. potentially, dangerous operational con?icts. In ?rrtherance of these goals,
the parties agree as follows:
The parties shall ensure that covered entities disseminate their
terrorism or other homeland security-related analytic products without delay to
other covered entities that have related interests and responsibilities;
(ii) Except as otherwise provided in Sections 4(inii) or no
analytic canclusions, as de?ned in Section 2(a) of this Agreement, of any covered
entity shall be disseminated to state, local, or private sector of?cials, or to the
public, without the prior approval of the Secretary of Homeland Security, his
designee, or in accordance with approval mechanisms, potentially including the
or the established by the Secretary alter the date of this Agreement.
Analytic conclusions may be provided directly to such of?cials or
to the public where the head of a covered entity or his or her designcc reasonably
determines that exigent circumstances exist such that providing an analytic
conclusion prior to required approval is necessary to prevent. preempt, or disrupt
an imminmt threat of death or serious bodily injury or signi?cant damage to US.
or other interests. In the event an analytic conclusion is -
disseminated pursuant to the exigent circumstances exception in this paragraph,
l4

the Secretary and other covered entities shall be noti?ed immediately of the
dissemination.
(iv) Analytic conclusions may be shared with federal, state. and local
law enforcement of?cials without the prior approval of the Secretary of
Homeland Security, provided, however, that it is the intention of the parties that
DHS he provided with the earliest possible advance notice of the potential of such
communications and, where possible, DHS will be included in the development of
the communications through the DHS liaisons at FBI Headquarters. The
Secretary of Homeland Security, or his designee (including a DHS representative
to a JTTF if designated by the Secretary to do so), must approve further
dissemination of such analytic conclusions to other non-law enforcement state and
local oilicials or to the public.
Nothing in this Agreement shall prevent covered entities ?om
coordinating on analytic conclusions with, or seeking the views of, other Federal
Government entities in evaluating terrorism or other homeland-secm-ity-related
information.
Establishment of Mechanisms for Operational Coordination and
Decon?lction. As soon as practicable, the parties shall agree upon speci?c mechanisms,
including technical, administrative, and, as appropriate. designation of focal points, to
maximize the effectiveness of Operational coordination and deconlliction. These will
cover bath Overseas and domestic Operations related to homeland security. Subsequent
agreements for operational coordination and deeon?iction may be reached upon the
approval of the parties or their designees.
Information Sharing Dispute Resolution. Consistent with the DHS
Legislation and other relevant statutory authorities, Presidential Directives, the
President's announced policies for protecting against terrorist threats to the homeland, the
obligation to protect intelligence or sensitive law enforcement sources and methods from
unauthorized disclosure, and with Section and other relevant sections of this
A greement, issues concerning the application of the terms of this Agreement in any
speci?c context with reSpect to whether particular covered information should be
provided to the Department or to any other covered entity shall be handled under the
following procedures:
A holder of particular covered information at issue. whether within
or outside the entity originating that information, shall refer the matter by the most
expeditious means to the head of the entity originating the information (or
that of?cial's designee) for expeditious review.
ii) The reviewing of?cial shall, without exception, render a definitive
decision on the request within 24 hours ofrcceiving the referral and, in light of
the access provisions in the DHS Legislation, shall resolve any doubt in favor
the Secretary and other covered entities shall be noti?ed immediately of the
dissemination.
(iv) Analytic conclusions may be shared with federal, state. and local
law enforcement of?cials without the prior approval of the Secretary of
Homeland Security, provided, however, that it is the intention of the parties that
DHS he provided with the earliest possible advance notice of the potential of such
communications and, where possible, DHS will be included in the development of
the communications through the DHS liaisons at FBI Headquarters. The
Secretary of Homeland Security, or his designee (including a DHS representative
to a JTTF if designated by the Secretary to do so), must approve further
dissemination of such analytic conclusions to other non-law enforcement state and
local oilicials or to the public.
Nothing in this Agreement shall prevent covered entities ?om
coordinating on analytic conclusions with, or seeking the views of, other Federal
Government entities in evaluating terrorism or other homeland-secm-ity-related
information.
Establishment of Mechanisms for Operational Coordination and
Decon?lction. As soon as practicable, the parties shall agree upon speci?c mechanisms,
including technical, administrative, and, as appropriate. designation of focal points, to
maximize the effectiveness of Operational coordination and deconlliction. These will
cover bath Overseas and domestic Operations related to homeland security. Subsequent
agreements for operational coordination and deeon?iction may be reached upon the
approval of the parties or their designees.
Information Sharing Dispute Resolution. Consistent with the DHS
Legislation and other relevant statutory authorities, Presidential Directives, the
President's announced policies for protecting against terrorist threats to the homeland, the
obligation to protect intelligence or sensitive law enforcement sources and methods from
unauthorized disclosure, and with Section and other relevant sections of this
A greement, issues concerning the application of the terms of this Agreement in any
speci?c context with reSpect to whether particular covered information should be
provided to the Department or to any other covered entity shall be handled under the
following procedures:
A holder of particular covered information at issue. whether within
or outside the entity originating that information, shall refer the matter by the most
expeditious means to the head of the entity originating the information (or
that of?cial's designee) for expeditious review.
ii) The reviewing of?cial shall, without exception, render a definitive
decision on the request within 24 hours ofrcceiving the referral and, in light of
the access provisions in the DHS Legislation, shall resolve any doubt in favor

providing the requested information.
11>
'0
13
9-.
(J1
Ifthe originating agency?s reviewing official declines to provide
the covered information requested, that o?icial shall, within the 24 hours allotted
for response, provide the Department or other covered with -
(A) the fact that the specific information is being withheld;
(B) a succinct and speci?c statement of the reasons for the
withholding; and
(C) as much of the information requested as the head of the
originating agency (or that of?cial?s designee} reasonably concludes can
be provided given the President?s announced policies for protecting
against terrorist threats to the homeland. the DHS Legislation and other
relevant statutory authorities. and relevant Presidential Directives.
(iv) If, at that point, a compromise is not reached expeditiously. the
dispute will be resolved either by the Secretary. Attorney General, and DCI by
mutual decision or through referral to the Assisrant to the President for National
Security Affairs and Assistant to the President for Homeland Security Affairs, or
their designees, for resolution. Notwithstanding any other provision of this
Agreement, the Attorney General, Secretary, or DC I, or their deputies may.
whenever any of them deems it necessary or advisable (particularly when a
fundamental matter of policy is implicated or time is of the essence). intervene to
raise and resolve any issue ofaccess to covered infomiation by mutual decision or
through the National Security Council and/or Homeland Security Council system.
NSPD-8. Nothing in this Agreement in any way affects the
responsibilities and authorities for coordination of United States counter-terrorism
activities established in National Presidential Directive (NSPD) 8.
5. Protection of Intelligence and Sensitive Law Enforcement ?gurces and Methods.
The parties intend that all provisions of this Agreement be interpreted consistently with the DCl's
statutory responsibility to protect intelligence sources and methods from unauthorized disclosure
and with similar responsibilities of the Attorney General and the Secretary to protect sensitive
law enforcement sources and methods, with the DHS Legislation and other relevant statutory
authorities, Presidential Directives. the President?s announced policies for protecting against
terrorist threats to the homeland, and with Section and other relevant provisions of this
Agreement. Consistent with this agreed-upon interpretation:
(it) The DCI shall carry out his responsibilities for the protection of
intelligence sources and methods, and the Secretary and Attorney General shall carry out
analogous reSponsibilities for sensitive law enforcement sources and methods. in a
manner, and through mechanisms. that ensure that all c0vered infOnnation is made
available to the Department, and to other covered entities with a need?tc-know
and proper secwity clearances and handling procedures in place, subject only to with
handling and use restrictions as are strictly and unavoidably necessary to protect
l6
providing the requested information.
11>
'0
13
9-.
(J1
Ifthe originating agency?s reviewing official declines to provide
the covered information requested, that o?icial shall, within the 24 hours allotted
for response, provide the Department or other covered with -
(A) the fact that the specific information is being withheld;
(B) a succinct and speci?c statement of the reasons for the
withholding; and
(C) as much of the information requested as the head of the
originating agency (or that of?cial?s designee} reasonably concludes can
be provided given the President?s announced policies for protecting
against terrorist threats to the homeland. the DHS Legislation and other
relevant statutory authorities. and relevant Presidential Directives.
(iv) If, at that point, a compromise is not reached expeditiously. the
dispute will be resolved either by the Secretary. Attorney General, and DCI by
mutual decision or through referral to the Assisrant to the President for National
Security Affairs and Assistant to the President for Homeland Security Affairs, or
their designees, for resolution. Notwithstanding any other provision of this
Agreement, the Attorney General, Secretary, or DC I, or their deputies may.
whenever any of them deems it necessary or advisable (particularly when a
fundamental matter of policy is implicated or time is of the essence). intervene to
raise and resolve any issue ofaccess to covered infomiation by mutual decision or
through the National Security Council and/or Homeland Security Council system.
NSPD-8. Nothing in this Agreement in any way affects the
responsibilities and authorities for coordination of United States counter-terrorism
activities established in National Presidential Directive (NSPD) 8.
5. Protection of Intelligence and Sensitive Law Enforcement ?gurces and Methods.
The parties intend that all provisions of this Agreement be interpreted consistently with the DCl's
statutory responsibility to protect intelligence sources and methods from unauthorized disclosure
and with similar responsibilities of the Attorney General and the Secretary to protect sensitive
law enforcement sources and methods, with the DHS Legislation and other relevant statutory
authorities, Presidential Directives. the President?s announced policies for protecting against
terrorist threats to the homeland, and with Section and other relevant provisions of this
Agreement. Consistent with this agreed-upon interpretation:
(it) The DCI shall carry out his responsibilities for the protection of
intelligence sources and methods, and the Secretary and Attorney General shall carry out
analogous reSponsibilities for sensitive law enforcement sources and methods. in a
manner, and through mechanisms. that ensure that all c0vered infOnnation is made
available to the Department, and to other covered entities with a need?tc-know
and proper secwity clearances and handling procedures in place, subject only to with
handling and use restrictions as are strictly and unavoidably necessary to protect
l6

intelligence and sensitive law enforcement sources and methods from unauthonzed
disclosure.
The shall ensure that the substance of all covered information
relevant to the responsibilities of all covered entities is provided to those entities
in a form suited to their effective use of that information. consistent with the
DCl?s obligation to protect intelligence sources and methods from unauthorized
disclosure and Section 3(a) of this Agreement. The Secretary and the Attorney
General shall similarly ensure that the substance of covered information is
provided in a suitable form.
(ii) The shall ensure that dissemination of classi?ed reporting
based. wholly or in part, on covered information. is accompanied by disseminatiOn
of as much of that reporting and counted information as is possible at an
unclassi?ed (which may. when necessary. be marked "Sensitive-but-Unclassi?ed"
or or reduced classi?cation level. in order to ensure the broadest possible
availability and use of covered information by those with a need-to-know that
information (or information relating to that subject matter), based on a broad
interpretation of the mission of the other covered entity; The Secretary and the
Attorney General shall similarly ensure that dissemination is done in a manner
that ensures the broadest possible availability.
Information may be redacted or put into a tailored product to the extent
consistent with Section 3(i) of this Agreement.
Norhing in this section relieves any member of the Intelligence
Community that originates covered information from its obligation to provide that
information to DHS and other covered entities. as appropriate. in a form consistent with
this Agreement. the DHS Legislation, and other relevant statutes and authorities
regarding the protection of sources and methods.
Consistent with the President's announced policies, our national priorities.
including this section. Section and other relevant provisions of this Agreement. the
DHS Legislation and other relevant statutes and Presidential Directives, covered entities
that originate covered information that is classi?ed shall retain the authority to determine
whether that information. or any portions thereof. must remain classi?ed in the interest of
national security.
Covered entities shall ensure that covered information that is
classi?ed 0r otherwise subject to restricted dissemination, but which reasonably
appears likely to require onward passage to state. local. or private sector of?cials.
the public. or other law enforcement of?cials for use in a criminal investigation.
reaches DHS with accompanying high-content ?tear lines? suitable fur
onward passage at an unclassi?ed level. Until this can be achieved
l7
.
intelligence and sensitive law enforcement sources and methods from unauthonzed
disclosure.
The shall ensure that the substance of all covered information
relevant to the responsibilities of all covered entities is provided to those entities
in a form suited to their effective use of that information. consistent with the
DCl?s obligation to protect intelligence sources and methods from unauthorized
disclosure and Section 3(a) of this Agreement. The Secretary and the Attorney
General shall similarly ensure that the substance of covered information is
provided in a suitable form.
(ii) The shall ensure that dissemination of classi?ed reporting
based. wholly or in part, on covered information. is accompanied by disseminatiOn
of as much of that reporting and counted information as is possible at an
unclassi?ed (which may. when necessary. be marked "Sensitive-but-Unclassi?ed"
or or reduced classi?cation level. in order to ensure the broadest possible
availability and use of covered information by those with a need-to-know that
information (or information relating to that subject matter), based on a broad
interpretation of the mission of the other covered entity; The Secretary and the
Attorney General shall similarly ensure that dissemination is done in a manner
that ensures the broadest possible availability.
Information may be redacted or put into a tailored product to the extent
consistent with Section 3(i) of this Agreement.
Norhing in this section relieves any member of the Intelligence
Community that originates covered information from its obligation to provide that
information to DHS and other covered entities. as appropriate. in a form consistent with
this Agreement. the DHS Legislation, and other relevant statutes and authorities
regarding the protection of sources and methods.
Consistent with the President's announced policies, our national priorities.
including this section. Section and other relevant provisions of this Agreement. the
DHS Legislation and other relevant statutes and Presidential Directives, covered entities
that originate covered information that is classi?ed shall retain the authority to determine
whether that information. or any portions thereof. must remain classi?ed in the interest of
national security.
Covered entities shall ensure that covered information that is
classi?ed 0r otherwise subject to restricted dissemination, but which reasonably
appears likely to require onward passage to state. local. or private sector of?cials.
the public. or other law enforcement of?cials for use in a criminal investigation.
reaches DHS with accompanying high-content ?tear lines? suitable fur
onward passage at an unclassi?ed level. Until this can be achieved
l7
.

simultaneously to the transmission of covered information. the development of
such tearlines shall not delay the provision of covered information.
9 xtpuaddv
(ii) The parties shall ensure. to the greatest extent possible. that
covered entities utilize agreed-upon standardized formatting for preparation of
tear-iine material for passage to state, local, or private sector officials, including
state and local law enforcement of?cials for use in a law enforcement
investigation. or to the public. with the goal of providing necessary substantive
information. but not enabling recipients to determine the originator, within the
Federal government. of the information.
DHS may. on its own initiative or at the request of a homeland Security
official to whom covered information is disseminated. ask that the originating agency
dcclassify 0r reduce the classi?cation level attached to that information in order to permit
dissemination to additional officials who have a need-to?know the information. to
promorc case of handling by those authorized to review it. to permit its incorporation into
a document that is unclassi?ed or classi?ed at a lower level. or for other purposes
consistent with the need to provide homeland security of?cials with all relevant
covered information that they have a necd-to-know in the conduct of their of?cial duties.
Whenever it receives such a request. the originating agency shall respond to DHS. within
24 hours (or such longer period as is agreed to by all parties). unless compelling
circumstances exist to require a longer response time. Such response will either
agree to declassify or reduce the classification level of the covered
information in question as requested; or
(ii) provide an alternative formulation responsive to the requestcr's
need for additional information sharing. but without or reducing the
classi?cation of the original document or covered information where that cannm
be done consistent with assuring the national security.
Where the need by DHS for further dissemination of classi?ed
information received from Other covered entities, including throngh declassi?cation or
the preparation of unclassi?ed tear-lines. is urgent because that information contains or
may contain terrOrist threat indications critical to the ability of homeland security
of?cials to prevent. preempt. or disrupt a possible terrorist attack, that information may
be passed directly to the entity or official that has a needle-know that information.
provided that the covered entity passing the information ?rst notifies the originating
agency and takes steps reasonable under the exigent circumstances to protect whatever
classified infomiatiou is not essential In initiating the urgent homeland Security assurance
measures that may be requrred.
The parties agree to develop together. as soon as practicable. mechanisms
and procedures. including through the use of detailees and to the 'lTlC and
as appropriate. to carry out the provisions of Section 6. The parties agree to work
simultaneously to the transmission of covered information. the development of
such tearlines shall not delay the provision of covered information.
9 xtpuaddv
(ii) The parties shall ensure. to the greatest extent possible. that
covered entities utilize agreed-upon standardized formatting for preparation of
tear-iine material for passage to state, local, or private sector officials, including
state and local law enforcement of?cials for use in a law enforcement
investigation. or to the public. with the goal of providing necessary substantive
information. but not enabling recipients to determine the originator, within the
Federal government. of the information.
DHS may. on its own initiative or at the request of a homeland Security
official to whom covered information is disseminated. ask that the originating agency
dcclassify 0r reduce the classi?cation level attached to that information in order to permit
dissemination to additional officials who have a need-to?know the information. to
promorc case of handling by those authorized to review it. to permit its incorporation into
a document that is unclassi?ed or classi?ed at a lower level. or for other purposes
consistent with the need to provide homeland security of?cials with all relevant
covered information that they have a necd-to-know in the conduct of their of?cial duties.
Whenever it receives such a request. the originating agency shall respond to DHS. within
24 hours (or such longer period as is agreed to by all parties). unless compelling
circumstances exist to require a longer response time. Such response will either
agree to declassify or reduce the classification level of the covered
information in question as requested; or
(ii) provide an alternative formulation responsive to the requestcr's
need for additional information sharing. but without or reducing the
classi?cation of the original document or covered information where that cannm
be done consistent with assuring the national security.
Where the need by DHS for further dissemination of classi?ed
information received from Other covered entities, including throngh declassi?cation or
the preparation of unclassi?ed tear-lines. is urgent because that information contains or
may contain terrOrist threat indications critical to the ability of homeland security
of?cials to prevent. preempt. or disrupt a possible terrorist attack, that information may
be passed directly to the entity or official that has a needle-know that information.
provided that the covered entity passing the information ?rst notifies the originating
agency and takes steps reasonable under the exigent circumstances to protect whatever
classified infomiatiou is not essential In initiating the urgent homeland Security assurance
measures that may be requrred.
The parties agree to develop together. as soon as practicable. mechanisms
and procedures. including through the use of detailees and to the 'lTlC and
as appropriate. to carry out the provisions of Section 6. The parties agree to work

together to ensure that the administrative. ?nancial. and personnel burdens of this section
are shared to the greatest extent possible among covered entities.
7. Detail or oi Emanuel. To facilitate the information sharing.
coordination. and decon?iclion policies covered in this Agreement. covered entities shall detail,
and/or assign. to the greatest extent possible. including to the T?l?lC and/or JTl?i-?s. personnel who
have the authority either to make classification review and redaction decisions themselves, or,
consistent with the time frames established in this Agreement, to refer those decisions to the
appropriate of?cials at the originating agency for prompt action.
8. DHS Participgtion in Rguirernents Prgessgs. As soon as practicable, the parties
shall modify existing mechanisms and processes for prioritization of terrorism, WMD and other
relevant foreign intelligence collection (including within the United States) and requirements
processes to ensure that DHS has meaningful participation at each stage and level of each such
mechanism or process. including through participation in the Ti 1C. The parties also shall work
together to provide recommendations as to whether, and how, processes or mechanisms for
purely ?domestic? terrorism concerning the capabilities. plans and intentions of exclusively
domestic white suprernacrsr or militia gronps). and other relevant intelligence collection should
be created or. alternatively. how to ensure meaningful participation by DHS in the prioritization
for gathering such information. This section does not refer to operational actiwlics.
9. Databases. The parties agree to establish procedures and mechanisms to provide
DHS. and. as appropriate and practicable, other covered entities, with access to databases
containing covered information. To this end. the parties shall establish a working group. within .
30 days of the date of this Agreement. Developed procedures and mechanisms. including
through the use of the and/or should be consistent with the DHS Legislation and
other relevant statutory authorities. Presidential Directives. the President?s announced policies
for protecting against terrorist threats to the homeland. and the appropriate needs for access by
Dt-lS to appropriate databases. as well as with the protection of intelligence or sensitive law
enforcement sources and methods. and with Section 3(a) and other pmvisions of this Agreement.
Such procedures and mechanisms should facilitate. to the greatest possible ex tent: ease and
speed of information exchange; differentiated access. to allow individuals with different levels of
security clearance and need-to-know to have different levels of access to databases; and
compatibility with other databases of covered entities.
10. Statement of {malt Concerning Inlogmation ?magma. it is the intent of the
parties to build and modernize all relevant databases and other information technology systems
in order to rnaximrzr: compatibility with other systems with which they must interact. Such
procedures and mechanisms also must comply with existing statutory and Presidential
Directives. including with regard to the protection of classi?ed information and applicable
privacy protections.
1. Handling and Storage. The parties shall ensure that covered entities within their
jurisdiction observe the esra'olished handling and storage standards apprOpriate to the
classi?cation and access restrictions indicated on covered information they receive. use. and .
together to ensure that the administrative. ?nancial. and personnel burdens of this section
are shared to the greatest extent possible among covered entities.
7. Detail or oi Emanuel. To facilitate the information sharing.
coordination. and decon?iclion policies covered in this Agreement. covered entities shall detail,
and/or assign. to the greatest extent possible. including to the T?l?lC and/or JTl?i-?s. personnel who
have the authority either to make classification review and redaction decisions themselves, or,
consistent with the time frames established in this Agreement, to refer those decisions to the
appropriate of?cials at the originating agency for prompt action.
8. DHS Participgtion in Rguirernents Prgessgs. As soon as practicable, the parties
shall modify existing mechanisms and processes for prioritization of terrorism, WMD and other
relevant foreign intelligence collection (including within the United States) and requirements
processes to ensure that DHS has meaningful participation at each stage and level of each such
mechanism or process. including through participation in the Ti 1C. The parties also shall work
together to provide recommendations as to whether, and how, processes or mechanisms for
purely ?domestic? terrorism concerning the capabilities. plans and intentions of exclusively
domestic white suprernacrsr or militia gronps). and other relevant intelligence collection should
be created or. alternatively. how to ensure meaningful participation by DHS in the prioritization
for gathering such information. This section does not refer to operational actiwlics.
9. Databases. The parties agree to establish procedures and mechanisms to provide
DHS. and. as appropriate and practicable, other covered entities, with access to databases
containing covered information. To this end. the parties shall establish a working group. within .
30 days of the date of this Agreement. Developed procedures and mechanisms. including
through the use of the and/or should be consistent with the DHS Legislation and
other relevant statutory authorities. Presidential Directives. the President?s announced policies
for protecting against terrorist threats to the homeland. and the appropriate needs for access by
Dt-lS to appropriate databases. as well as with the protection of intelligence or sensitive law
enforcement sources and methods. and with Section 3(a) and other pmvisions of this Agreement.
Such procedures and mechanisms should facilitate. to the greatest possible ex tent: ease and
speed of information exchange; differentiated access. to allow individuals with different levels of
security clearance and need-to-know to have different levels of access to databases; and
compatibility with other databases of covered entities.
10. Statement of {malt Concerning Inlogmation ?magma. it is the intent of the
parties to build and modernize all relevant databases and other information technology systems
in order to rnaximrzr: compatibility with other systems with which they must interact. Such
procedures and mechanisms also must comply with existing statutory and Presidential
Directives. including with regard to the protection of classi?ed information and applicable
privacy protections.
1. Handling and Storage. The parties shall ensure that covered entities within their
jurisdiction observe the esra'olished handling and storage standards apprOpriate to the
classi?cation and access restrictions indicated on covered information they receive. use. and .

disseminate. subject only to the provisions of this Agreement pertaining to exigent
cirCumsutnces.
12. WW- Tnis Aarcement
contemplates a separate Memorandum of Understanding. consistent with this Agreement. being
agreed to by the parties, that addresses concerns related to intormation collected and shared by
foreign governments.
13. Matriculation-
ta) Each of the parties shall implement their responsibilities under this
Agreement as to the covered entities under their jurisdiction through such binding
regulations. orders. directives, and guidance as necessary or prudent From time to time.
xtpuaddv
Any authority or duty herein to the Attorney General. the
Secretary. Or the may be delegated to one or more subordinate of?cials at the
discretion of the of?cial to whom the authority or duty is assigned. except as otherwise
provided in this Agreement. Each such delegation shall be communicated to all
other parties.
i4. No Pg?vgtg Bight; Created. These procedures are not intended to and do not
create any rights. privileges. or bene?ts. substantive or procedural. enforceable by any individual
or organization against the United States. its departments. agencies. or other entities. its of?cers
or employees. or any other person.
15. Counterpart ?iggature?. This Agreement may be signed in counterparts. each of
which shall be considered to be an original.
s/s
1-3-40 .
Attorney General Date
2003
Director of Central Intelligence Date
sis
Feb. ZS, 2091
Secretary of Homeland Security Date
disseminate. subject only to the provisions of this Agreement pertaining to exigent
cirCumsutnces.
12. WW- Tnis Aarcement
contemplates a separate Memorandum of Understanding. consistent with this Agreement. being
agreed to by the parties, that addresses concerns related to intormation collected and shared by
foreign governments.
13. Matriculation-
ta) Each of the parties shall implement their responsibilities under this
Agreement as to the covered entities under their jurisdiction through such binding
regulations. orders. directives, and guidance as necessary or prudent From time to time.
xtpuaddv
Any authority or duty herein to the Attorney General. the
Secretary. Or the may be delegated to one or more subordinate of?cials at the
discretion of the of?cial to whom the authority or duty is assigned. except as otherwise
provided in this Agreement. Each such delegation shall be communicated to all
other parties.
i4. No Pg?vgtg Bight; Created. These procedures are not intended to and do not
create any rights. privileges. or bene?ts. substantive or procedural. enforceable by any individual
or organization against the United States. its departments. agencies. or other entities. its of?cers
or employees. or any other person.
15. Counterpart ?iggature?. This Agreement may be signed in counterparts. each of
which shall be considered to be an original.
s/s
1-3-40 .
Attorney General Date
2003
Director of Central Intelligence Date
sis
Feb. ZS, 2091
Secretary of Homeland Security Date

(-
A
9 xrpuaddv
Executive Order 13388 of October 25, 2005
urtber Strengthening the Sharing of Terrorism Information to Protect Americans
By the authority vested in me as President by the Constitution and the laws of the United States
of America. including of the Intelligence Refomt and Terrorism Prevention Act of
(Public Law mil-458). and in order to urtber strengthen the effective conduct ot'l lnited
States counterterrorism activities and protect the territory. people. and interests of the linited
States of America. including against terrorist attacks. it is hereby ordered as follows:
Section 1. Policy. To the maximum extent consistent with applicable law. agencies shall. in the
design and use ol'int'omtation systems and in the dissemination ot'int'ormation among agencies:
give the highest priority to the detection. prevention. disruption.
preemption. and mitigation of the effects of terrorist activities against the
territory. people. and interests of the United States of America: (ii) the
interchange of terrorism infomtation among agencies: the interchange of
terrorism infomtation between agencies and appropriate authorities of State. local.
and tribal governments. and between agencies and appropriate private sector
entities: and (iv) the protection of the ability of agencies to acquire additional
such infonnation: and
protect the freedom. information privacy. and other legal rights of Americans
in the conduct of activities implementing subsection
See. 2. Duties of Heads of Agencies Possessing or Acquiring Terrorism Infomtation. To
implement the policy set forth in section 1 of this order. the head of each agency that possesses
or acquires terrorism infonnation:
shall give access to the terrorism information to the head of each
other agency that has counterterrorism functions. and provide the terrorism
information to each such agency. unless otherwise directed by the President. and
consistent with the statutory responsibilities of the agencies providing and
receit. ing the infonnation: ti i) any guidance issued by the Attomey (ieneral to
fulfilf the policy set forth in subsection 1(b) oftltis order: and other applicable
lays. including sections and tit of the National Security Act of W47.
section 1016 of the Intelligence Reform and Terrorism Prevention Act ofIOO-l
(including any policies. procedures. guidelines. rules. and standards issued
pursuant thereto). sections 202 and 802 of the Homeland Security Act ot'2002.
Executive Order [2958 oprril I7. 1995. as amended. and liseeutive )rder
133l ofJuly 2003: and
shall cooperate in and facilitate produetion of reports based on terrorism
infonnation with contents and fomiats that permit dissemination that maximizes
the utility of the information in protecting the territory. people. and interests ofthe
United States.
See. 3. Preparing Terrorism Information for Maximum Distribution. To assist in expeditious and
effective implementation by agencies ol'the policy set forth in section I ot'this order. the
Page 1 of3
(-
A
9 xrpuaddv
Executive Order 13388 of October 25, 2005
urtber Strengthening the Sharing of Terrorism Information to Protect Americans
By the authority vested in me as President by the Constitution and the laws of the United States
of America. including of the Intelligence Refomt and Terrorism Prevention Act of
(Public Law mil-458). and in order to urtber strengthen the effective conduct ot'l lnited
States counterterrorism activities and protect the territory. people. and interests of the linited
States of America. including against terrorist attacks. it is hereby ordered as follows:
Section 1. Policy. To the maximum extent consistent with applicable law. agencies shall. in the
design and use ol'int'omtation systems and in the dissemination ot'int'ormation among agencies:
give the highest priority to the detection. prevention. disruption.
preemption. and mitigation of the effects of terrorist activities against the
territory. people. and interests of the United States of America: (ii) the
interchange of terrorism infomtation among agencies: the interchange of
terrorism infomtation between agencies and appropriate authorities of State. local.
and tribal governments. and between agencies and appropriate private sector
entities: and (iv) the protection of the ability of agencies to acquire additional
such infonnation: and
protect the freedom. information privacy. and other legal rights of Americans
in the conduct of activities implementing subsection
See. 2. Duties of Heads of Agencies Possessing or Acquiring Terrorism Infomtation. To
implement the policy set forth in section 1 of this order. the head of each agency that possesses
or acquires terrorism infonnation:
shall give access to the terrorism information to the head of each
other agency that has counterterrorism functions. and provide the terrorism
information to each such agency. unless otherwise directed by the President. and
consistent with the statutory responsibilities of the agencies providing and
receit. ing the infonnation: ti i) any guidance issued by the Attomey (ieneral to
fulfilf the policy set forth in subsection 1(b) oftltis order: and other applicable
lays. including sections and tit of the National Security Act of W47.
section 1016 of the Intelligence Reform and Terrorism Prevention Act ofIOO-l
(including any policies. procedures. guidelines. rules. and standards issued
pursuant thereto). sections 202 and 802 of the Homeland Security Act ot'2002.
Executive Order [2958 oprril I7. 1995. as amended. and liseeutive )rder
133l ofJuly 2003: and
shall cooperate in and facilitate produetion of reports based on terrorism
infonnation with contents and fomiats that permit dissemination that maximizes
the utility of the information in protecting the territory. people. and interests ofthe
United States.
See. 3. Preparing Terrorism Information for Maximum Distribution. To assist in expeditious and
effective implementation by agencies ol'the policy set forth in section I ot'this order. the
Page 1 of3

common standards :or the sharing of terrorism iniomtation established pursuant to section 3 of
. of August 27. 2004. shall be used. as appropriate. in carrying out
of the intelligence Reform and 'l'errorism Prevention Act of 2004.
See. Requirements for Collection of'l'etrorism lnfonnation inside the United States. To assist
in expeditious and effective implementation by agencies of the policy set forth in section of
this order. the recommendations regarding the establishment of executive branch?wide collection
and sharing requirements. procedures. and guidelines for terrorism infomtation collected within
the United States made pursuant to section 4 of Executive Order l3356 shall be used. as
appropriate. in carrying out -- . r- of the Intelligence Reform and Terrorism Prevention
Act of 2004.
See. 5. Establishment and Functions of Information Sharing Council.
ta) Consistent with section 10! 6tg) of the Intelligence Reform and Terrorism
Prevention Act of2004. there is hereby established an lnfomtation Sharing
Council (Council). chaired by the Program Manager to whom section 1016 of
such Act refers. and composed exclusively of designecs of: the Secretaries of
State. the Treasury. Defense. ommercc. Energy. and Homeland Security: the
Attorney General: the Director of National Intelligence: the Director ofthe
Central intelligence Agency: the Director of the Office of Management and
Budget: the Director of the Federal Bureau of investigation: the Director ofthe
National Center: and such other heads of departments or
agencies as the Director of National Intelligence may designate.
The mission of the Council is to ti) provide advice and information concerning
the establishment of an interoperable terrorism information sharing environment
to facilitate automated sharing of terrorism information among appropriate
agencies to implement the policy set forth in section I of this order: and (ii)
perform the duties set forth in section [01 6( g) of the Intelligence Reform and
Terrorism Prevention Act of 2004.
tel To assist in expeditious and effective implementation by agencies of the policy
set forth in section I of this order. the plan for establishment ofa proposed
interoperable terrorism information sharing environment reported under section
5(c) of Executive Order l3356 shall be used. as appropriate. in carrying out
ofthe Intelligence Refomt and Terrorism Prevention Act onOO-l.
Sec. 6. Definitions. used in this order: .
ta) the term "agency" has the meaning set fonh for the term "executive agency" in
section 105 oftitle 5. Limited States Code. together with the Department of
Homeland Security. but includes the Postal Rate Commission and the [failed
States Postal Service and excludes the Govemment Accountability Office: and
the term "terrorism information" has the meaning set forth for such term in
section of the intelligence Rct?omt and Terrorism Prevention Act of
2004.
See. 7. General l?rmisions.
tat I his order:
(it shall be implemented in a manner consistent with applicable law.
including Federal law protecting the information privacy and other legal
rights of Americans- and subject to the availability ofappropriations:
9 xtpuoddv
Page 2 of3
common standards :or the sharing of terrorism iniomtation established pursuant to section 3 of
. of August 27. 2004. shall be used. as appropriate. in carrying out
of the intelligence Reform and 'l'errorism Prevention Act of 2004.
See. Requirements for Collection of'l'etrorism lnfonnation inside the United States. To assist
in expeditious and effective implementation by agencies of the policy set forth in section of
this order. the recommendations regarding the establishment of executive branch?wide collection
and sharing requirements. procedures. and guidelines for terrorism infomtation collected within
the United States made pursuant to section 4 of Executive Order l3356 shall be used. as
appropriate. in carrying out -- . r- of the Intelligence Reform and Terrorism Prevention
Act of 2004.
See. 5. Establishment and Functions of Information Sharing Council.
ta) Consistent with section 10! 6tg) of the Intelligence Reform and Terrorism
Prevention Act of2004. there is hereby established an lnfomtation Sharing
Council (Council). chaired by the Program Manager to whom section 1016 of
such Act refers. and composed exclusively of designecs of: the Secretaries of
State. the Treasury. Defense. ommercc. Energy. and Homeland Security: the
Attorney General: the Director of National Intelligence: the Director ofthe
Central intelligence Agency: the Director of the Office of Management and
Budget: the Director of the Federal Bureau of investigation: the Director ofthe
National Center: and such other heads of departments or
agencies as the Director of National Intelligence may designate.
The mission of the Council is to ti) provide advice and information concerning
the establishment of an interoperable terrorism information sharing environment
to facilitate automated sharing of terrorism information among appropriate
agencies to implement the policy set forth in section I of this order: and (ii)
perform the duties set forth in section [01 6( g) of the Intelligence Reform and
Terrorism Prevention Act of 2004.
tel To assist in expeditious and effective implementation by agencies of the policy
set forth in section I of this order. the plan for establishment ofa proposed
interoperable terrorism information sharing environment reported under section
5(c) of Executive Order l3356 shall be used. as appropriate. in carrying out
ofthe Intelligence Refomt and Terrorism Prevention Act onOO-l.
Sec. 6. Definitions. used in this order: .
ta) the term "agency" has the meaning set fonh for the term "executive agency" in
section 105 oftitle 5. Limited States Code. together with the Department of
Homeland Security. but includes the Postal Rate Commission and the [failed
States Postal Service and excludes the Govemment Accountability Office: and
the term "terrorism information" has the meaning set forth for such term in
section of the intelligence Rct?omt and Terrorism Prevention Act of
2004.
See. 7. General l?rmisions.
tat I his order:
(it shall be implemented in a manner consistent with applicable law.
including Federal law protecting the information privacy and other legal
rights of Americans- and subject to the availability ofappropriations:
9 xtpuoddv
Page 2 of3

(ii) shall be implemented in a manner consistent with the authority of the
principal of?cers of agencies as heads of their respective agencies.
including under section 199 of the Revised Statutes (22 U.S.C. 2651
section 20] ol?thc Department ot?Energy Organization Amt-12
7] 3i section it)? ot'the National Security Act of WW (50 [1.8.0 403-3).
section 102(a) of the Homeland Security Act ol'2002 (6 l2tal).
and sections 301 ot?titlc 5. 113(h) and lGth) ol?title ID. 150] ol'title 15.
503 of title 28. and 301th) ot'titlc 3 . United States Code:
be implemented consistent with the - - -: . I. -. -r
on "Strengthening lnl?onnation Sharing. Access. and
Integration Organizational. Management. and Policy Development
Structures for Creating the Terrorism Int?onnation Sharing Environment"
shall not be construed to impair or otherwise affect the functions of
the Director of the Of?ce of Management and Budget relating to budget.
administrative. and legislative proposals; and
shall be implemented in a manner consistent with section 102A ol'the
National Security Act of [947.
(bl This order is intended only to improve the internal management of the Federal
Government and is not intended to. and does not. create any rights or bene?ts.
substantive or procedural. enforceable at law or in equity by a party against the
L'nitcd States. its departments. agencies. instrumentalities- or entities. its of?cers.
employees. or agents. or any other person.
Sec. 8. Amendments and Revocation.
lisceutive Order I ol'July 2003. is amended:
by striking "Director intelligence" each place it appears and
inserting in lieu tliereot'in each such place "Director of National
Intelligence": and
(ill by striking "l03tcll7?t" and inserting in lieu thereof ll 1
(bl - ol?August 27. 2004. is hereby revoked.
[signedzl George W. Bush
THE WHITE. HOUSE.
October 35. 3005.
Page 3 of}
9 xtpuaddv
(ii) shall be implemented in a manner consistent with the authority of the
principal of?cers of agencies as heads of their respective agencies.
including under section 199 of the Revised Statutes (22 U.S.C. 2651
section 20] ol?thc Department ot?Energy Organization Amt-12
7] 3i section it)? ot'the National Security Act of WW (50 [1.8.0 403-3).
section 102(a) of the Homeland Security Act ol'2002 (6 l2tal).
and sections 301 ot?titlc 5. 113(h) and lGth) ol?title ID. 150] ol'title 15.
503 of title 28. and 301th) ot'titlc 3 . United States Code:
be implemented consistent with the - - -: . I. -. -r
on "Strengthening lnl?onnation Sharing. Access. and
Integration Organizational. Management. and Policy Development
Structures for Creating the Terrorism Int?onnation Sharing Environment"
shall not be construed to impair or otherwise affect the functions of
the Director of the Of?ce of Management and Budget relating to budget.
administrative. and legislative proposals; and
shall be implemented in a manner consistent with section 102A ol'the
National Security Act of [947.
(bl This order is intended only to improve the internal management of the Federal
Government and is not intended to. and does not. create any rights or bene?ts.
substantive or procedural. enforceable at law or in equity by a party against the
L'nitcd States. its departments. agencies. instrumentalities- or entities. its of?cers.
employees. or agents. or any other person.
Sec. 8. Amendments and Revocation.
lisceutive Order I ol'July 2003. is amended:
by striking "Director intelligence" each place it appears and
inserting in lieu tliereot'in each such place "Director of National
Intelligence": and
(ill by striking "l03tcll7?t" and inserting in lieu thereof ll 1
(bl - ol?August 27. 2004. is hereby revoked.
[signedzl George W. Bush
THE WHITE. HOUSE.
October 35. 3005.
Page 3 of}
9 xtpuaddv

xtpuaddv
Department of Justice Protocol Regarding Terrorist Nominations
as white at the mepnty camera!
2' .. 3' Washington. ISLE. 20530
- . October 3. 2008
.K
MEMORANDUM FOR HEADS DEPARTMENT COMPONENTS
From: The Deputy Attorney General
Subject: Department ofJustiee Protocol Regarding 'I'errorist Watehlist Nominatmns
The attached protocol re?ects a new policy for the Department's internal process for
nominating individuals for the 'l'errorist Screening Database (TSDB).
'l'he TSUB consolidates the U.S. Government's terrorism screening and lookout databases
into single integrated identities database. The TSDB is also known as the "watehlist."
This protocol is designed to ensure consistent and appropriate handling of watchlist
information. The protocol responds to issues raised by the report ol?the Inspector
General, dated March I4, 2008. entitled ?Audit of the Department ot'Justiee
'l?crrorist Watehlist Nomination Processes." Speci?cally. that report recommended that
the Dcpartmen; adopt a general policy for submission of watch list nominations.
lmplementation ot?thc attached protocol will accomplish that task.
All components are directed to comply with this protocol effective immediately.
Ol" lCli PROTOCOL
DING NOMINATIONS
A. Background
I. On September Id, 2003, the President directed the Attorney Getteral in Homeland
Security Presidential Directive 6 to "establish an organimtion to consolidate
the Government's approach to terrorism screening and provide ['or the appropriate and
lawful use ot"E'errorist la formation in screening processcs." Terrorist information was
speci?cally de?ned to mean "individuals known or appropriately suspected to he or have
been engaged in conduct constituting. in preparation for. in aid of, or related to
terrorism."
2. Concurrent with the signing of llSl?D-O, the Memorandum of Under-MmMing on the
Integration and Use of Screening Inlet-nnuirm to Protect Against 'l'errm-ism Mt
was signed by the Secretaries of State and Homeland Security, the Attorney General and
Page I ol?S
xtpuaddv
Department of Justice Protocol Regarding Terrorist Nominations
as white at the mepnty camera!
2' .. 3' Washington. ISLE. 20530
- . October 3. 2008
.K
MEMORANDUM FOR HEADS DEPARTMENT COMPONENTS
From: The Deputy Attorney General
Subject: Department ofJustiee Protocol Regarding 'I'errorist Watehlist Nominatmns
The attached protocol re?ects a new policy for the Department's internal process for
nominating individuals for the 'l'errorist Screening Database (TSDB).
'l'he TSUB consolidates the U.S. Government's terrorism screening and lookout databases
into single integrated identities database. The TSDB is also known as the "watehlist."
This protocol is designed to ensure consistent and appropriate handling of watchlist
information. The protocol responds to issues raised by the report ol?the Inspector
General, dated March I4, 2008. entitled ?Audit of the Department ot'Justiee
'l?crrorist Watehlist Nomination Processes." Speci?cally. that report recommended that
the Dcpartmen; adopt a general policy for submission of watch list nominations.
lmplementation ot?thc attached protocol will accomplish that task.
All components are directed to comply with this protocol effective immediately.
Ol" lCli PROTOCOL
DING NOMINATIONS
A. Background
I. On September Id, 2003, the President directed the Attorney Getteral in Homeland
Security Presidential Directive 6 to "establish an organimtion to consolidate
the Government's approach to terrorism screening and provide ['or the appropriate and
lawful use ot"E'errorist la formation in screening processcs." Terrorist information was
speci?cally de?ned to mean "individuals known or appropriately suspected to he or have
been engaged in conduct constituting. in preparation for. in aid of, or related to
terrorism."
2. Concurrent with the signing of llSl?D-O, the Memorandum of Under-MmMing on the
Integration and Use of Screening Inlet-nnuirm to Protect Against 'l'errm-ism Mt
was signed by the Secretaries of State and Homeland Security, the Attorney General and
Page I ol?S

the Director ol'L?cntral Intelligence (DCI) (on behalt'ol'the entire LLS. intelligence
t"ommunity). 'l'he MOU established the 'l'errorist Screening (?enter ('l'SCi to
consolidate the Government's approach to terrorism screening and provide for the
and lawful use ol'Terrorist information. a term clari?ed by the inclusion of
'l'ertorist identifiers in a subsequent agreement ol'the parties. llnder the
was to develop and maintain a database, to the extent permitted by law. containing the
most thorough. accurate. and current inl'omtation possible about known or suspected
terrorists. llSl?lLo requires that its implementation be consistent with the Constitution
and applicable laws. including those protecting the rights ol'all Americans. The
created the 'l?crrorist Screening Database t'l'Slm) to meet these goals. l'he
consolidates the L15. Government's terrorism screening and lookout databases into a
single integrath identities database. The TSDH is aiso knotsn as the
xtpuaddv
3. The MOI 3 also incorporated all prtWisions ol'lhe of!
rht' Intelligent-c Federal [mi- [infill-t elm-m (loom-mi: and the
Information .S'Imrmg. dated March 30m
tthe "information Kharing
4. ln the Secretaries ol?State. 'l'reasury. and Defense became signatories to
Intonnation Sharing MOU by signing Addendum A to the TSC MOI lly doing so. they
agreed that all provisions ol'the MOU and the Sharing i apply to
all entities that are or become a part ofthcir respective Departments.
5. second addendum (Addendum B). which supplements and incorporates by
all provisions r-l?the MOU, superseded Addendum A and was linaliZed on January
KR. 2007. The Directors ot'National Intelligence, and the TSP joined as
signatories in Addendum B. llnder paragraph (3) ol'Addendunt I3 the Parties agreed,
to the tnasimtm: extent permitted by law, to "provide to the on an ongoing basis
all 'l'errorism Information (as delincd in
the lntelligene: Reform and Terrorism Prevention Act Section
(wt) [as amended to include homeland security information and weapons ot'mass
destruction in formation] in their possession. Custody. or control. Paragraph 7 ul
Addendum it introduces the term Terrorist ldentiliers .to more clearly describe the type of
terrorism inliirtnation that (and the Federal Bureau of Investigation (FBI) l'or
l?urely Domestic ?l?crrorism lnl'omiation, as delined in the receives t'rom
interagcney partners and subsequently shares with for inclusion in the ?l'SlJli.
lisecutive Order 13354 (August 27. 2004) created the National (.?ountetterrorism
(Tentet to serve as the primary organization in the United States Government lor
anal yzing and .ntegrating all intelligence possessed or acquired by the United States
iovernment pertaining to terrorism and eounter?tcrrorism. excepting purely domestic
counterterrorisrn information. That same provision. however. provides that may
receive. retain. and disseminate inl'ormatimt from any Federal. State. or local covenant-at.
v: other source necessary to ful?ll its responsibilities. giving NCI authority?to receive.
r:t:tin. and disseminate domestic. terrorism ittliirmatiun.
Page .3 t'l 5
the Director ol'L?cntral Intelligence (DCI) (on behalt'ol'the entire LLS. intelligence
t"ommunity). 'l'he MOU established the 'l'errorist Screening (?enter ('l'SCi to
consolidate the Government's approach to terrorism screening and provide for the
and lawful use ol'Terrorist information. a term clari?ed by the inclusion of
'l'ertorist identifiers in a subsequent agreement ol'the parties. llnder the
was to develop and maintain a database, to the extent permitted by law. containing the
most thorough. accurate. and current inl'omtation possible about known or suspected
terrorists. llSl?lLo requires that its implementation be consistent with the Constitution
and applicable laws. including those protecting the rights ol'all Americans. The
created the 'l?crrorist Screening Database t'l'Slm) to meet these goals. l'he
consolidates the L15. Government's terrorism screening and lookout databases into a
single integrath identities database. The TSDH is aiso knotsn as the
xtpuaddv
3. The MOI 3 also incorporated all prtWisions ol'lhe of!
rht' Intelligent-c Federal [mi- [infill-t elm-m (loom-mi: and the
Information .S'Imrmg. dated March 30m
tthe "information Kharing
4. ln the Secretaries ol?State. 'l'reasury. and Defense became signatories to
Intonnation Sharing MOU by signing Addendum A to the TSC MOI lly doing so. they
agreed that all provisions ol'the MOU and the Sharing i apply to
all entities that are or become a part ofthcir respective Departments.
5. second addendum (Addendum B). which supplements and incorporates by
all provisions r-l?the MOU, superseded Addendum A and was linaliZed on January
KR. 2007. The Directors ot'National Intelligence, and the TSP joined as
signatories in Addendum B. llnder paragraph (3) ol'Addendunt I3 the Parties agreed,
to the tnasimtm: extent permitted by law, to "provide to the on an ongoing basis
all 'l'errorism Information (as delincd in
the lntelligene: Reform and Terrorism Prevention Act Section
(wt) [as amended to include homeland security information and weapons ot'mass
destruction in formation] in their possession. Custody. or control. Paragraph 7 ul
Addendum it introduces the term Terrorist ldentiliers .to more clearly describe the type of
terrorism inliirtnation that (and the Federal Bureau of Investigation (FBI) l'or
l?urely Domestic ?l?crrorism lnl'omiation, as delined in the receives t'rom
interagcney partners and subsequently shares with for inclusion in the ?l'SlJli.
lisecutive Order 13354 (August 27. 2004) created the National (.?ountetterrorism
(Tentet to serve as the primary organization in the United States Government lor
anal yzing and .ntegrating all intelligence possessed or acquired by the United States
iovernment pertaining to terrorism and eounter?tcrrorism. excepting purely domestic
counterterrorisrn information. That same provision. however. provides that may
receive. retain. and disseminate inl'ormatimt from any Federal. State. or local covenant-at.
v: other source necessary to ful?ll its responsibilities. giving NCI authority?to receive.
r:t:tin. and disseminate domestic. terrorism ittliirmatiun.
Page .3 t'l 5

7. Section l02t ofthe Intelligence Reform and 'l?errorisnt Prevention Act of 2004
tllt?l'l?A) amended the National Security Act of I947 to codify the creation of
Pursuant to lR?ft?A. serves "as the central and shared knowledge bank on known
and suspected terrorists and international terror groups." centralized knowledge
bank is known as the Terrorist Identities Datarnart Environment Section 102 NC)
on Domestic Intelligence states "tnay. consistent with applicable
law. the direction ofthc President. and guidelines referred to in section ltl2A(b). receive
intelligence pertaining exclusively to domestic from any Federal. State.
or local government or other source necessary to ful?ll its responsibilities and retain and
disseminate such intelligence."
xipuoddv
8. To enhance information sharing, the President issued Executive Order l3388. I?m-thw-
b?trm-rgtheniug the .S'Irm?ing of 'l?crrm'rsm Information to Protect Americans (October 25,
2005?}, which requires the head of each agency that possesses or acquires terrorism
information to give access to that information to the head ofeaeh other agency
that has cttunterterrorism functions.
0. Pursuant to paragraph (2) of l-lSPl)-6. is mandated to "provide with
access to all appropriate information or intelligence in the custody, possessmn.
or control that requires to perform its functions."
it). serves as the single source for the except for Purely Domestic 'l'crrorisrn
information, which is provided directly to the from the via a formalized
procedure. Purely Domestic crmrism Information is defined about US. per5ons that has been determined to be purely domestic terrorism
information with no link to foreign intelligence, counterintelligcnce. or international
terrorism."
1 l. 'l?ll)li contains the identilying and derogatory information on known or appropriately
suspected international terrorists and the Ffll's Automated Case Support system contains
supporting information regarding purely domestic terrorists. The TSDB contains the
identifiers exported from 'l?llJli and the identitiers ol'domcstic terrorists exported by the
PH l. Asa result, the 'l'SDl?l contains the Ub?. comprehensive database of
both international and domestic Terrorist Identifiers.
ll. Nominating (.?ompoucnts
Department ol'Justicc contains a number of components that may acquire
information regarding domestic or international terrorists. These components include the
l?lil, the the National Security Division. the Criminal Division, the Civil Rights
Division. the Drug Enforcement Administration, the United States Marshals Service. the
Bureau ol'Alcolrol, Tobacco, Firearms, and ExplosiVes, The federal Bureau ol'l?risons,
the Executive Of?ce ofthc United States Attorneys. the United States Attorneys. and the
United States National Central Bureau.
Page 3 ol'5
7. Section l02t ofthe Intelligence Reform and 'l?errorisnt Prevention Act of 2004
tllt?l'l?A) amended the National Security Act of I947 to codify the creation of
Pursuant to lR?ft?A. serves "as the central and shared knowledge bank on known
and suspected terrorists and international terror groups." centralized knowledge
bank is known as the Terrorist Identities Datarnart Environment Section 102 NC)
on Domestic Intelligence states "tnay. consistent with applicable
law. the direction ofthc President. and guidelines referred to in section ltl2A(b). receive
intelligence pertaining exclusively to domestic from any Federal. State.
or local government or other source necessary to ful?ll its responsibilities and retain and
disseminate such intelligence."
xipuoddv
8. To enhance information sharing, the President issued Executive Order l3388. I?m-thw-
b?trm-rgtheniug the .S'Irm?ing of 'l?crrm'rsm Information to Protect Americans (October 25,
2005?}, which requires the head of each agency that possesses or acquires terrorism
information to give access to that information to the head ofeaeh other agency
that has cttunterterrorism functions.
0. Pursuant to paragraph (2) of l-lSPl)-6. is mandated to "provide with
access to all appropriate information or intelligence in the custody, possessmn.
or control that requires to perform its functions."
it). serves as the single source for the except for Purely Domestic 'l'crrorisrn
information, which is provided directly to the from the via a formalized
procedure. Purely Domestic crmrism Information is defined about US. per5ons that has been determined to be purely domestic terrorism
information with no link to foreign intelligence, counterintelligcnce. or international
terrorism."
1 l. 'l?ll)li contains the identilying and derogatory information on known or appropriately
suspected international terrorists and the Ffll's Automated Case Support system contains
supporting information regarding purely domestic terrorists. The TSDB contains the
identifiers exported from 'l?llJli and the identitiers ol'domcstic terrorists exported by the
PH l. Asa result, the 'l'SDl?l contains the Ub?. comprehensive database of
both international and domestic Terrorist Identifiers.
ll. Nominating (.?ompoucnts
Department ol'Justicc contains a number of components that may acquire
information regarding domestic or international terrorists. These components include the
l?lil, the the National Security Division. the Criminal Division, the Civil Rights
Division. the Drug Enforcement Administration, the United States Marshals Service. the
Bureau ol'Alcolrol, Tobacco, Firearms, and ExplosiVes, The federal Bureau ol'l?risons,
the Executive Of?ce ofthc United States Attorneys. the United States Attorneys. and the
United States National Central Bureau.
Page 3 ol'5

2. the policy ot? the Department ot'Justice is tor all components to provide the Fill with
all domestic or international 'l?crrorism lnlortnation or Terrorist Identi?ers so that the "71]
can make appropriate nominations to the consolidated terrorist walchlist. Willi one
exception relating to 'l?SC?s authorin in exigent circumstances. only the Pill is authorized
to nominate domestic or international terrorists for inclusion in the 'l?SDll on hehatl?ol'the
Department ol'Justice. The FBI has implemented policies governing the submission of
such nominations. including procedures to follow when adding, modifying, or deleting a
T300 record. in making any proposed recommendation for watehlisting, each
component she-old ensure that the underlying information is reasonably accurate. relevant
and timely. to addition. the has implemented its Fromm! (tr-naming: 'l'ermrm
-\'umumrirms These policies must be followed regarding all nominations trom the
')epartment of Justice
5. the THC. naich is administered by the Hit and reports to the Attorney (ieueral. is
permitted to make entries into the 'l'SDtt when exigent circumstances exist. Such
expedited nominations must he made in compliance with the FBI nomination policies and
the 'l'SC's Regarding Nmm?mm?mrr.
The Joint 'l?errorism 'l?ask l-?orecs are a imttli-agemz)l effort led by the
Department ofJustiee and the I?lil tn eomhine and leverage law enforcement and
intelligence community resources to protect the United States from terrorist attach. .t'l?l't?s
are comprised ol'highly trained. locally based. investigators. linguists. and other
specialists from Federal. state. local. tribal, territorial law and intelligence
community agencies. The National .l't't?li was established in Jul}- 2002 to serve as the
coordinating meehanism for the
S. Department ot'lustiee emnponents. other than the hill or the are not permitted to
make direct or :ninations to the 'l'SDll. A Department ol'lostiee component should
inform the appropriate J'l'l'lr through disseminated intelligence reports. electronit'
communication. or other method appropriate to the circumstances when it becomes aware
ot"l?errorist lni'ormation. 't'errorist Identi?ers. or Purely Domestic 'l?errorism lnt'ornnition
(collectively, intelligence lntirrmation). The originating DOJ component should state
whether it recommends watch listing the individual. the basis for that reeonunendation.
and the investigative steps, it'any. it has undertaken regarding the individual. ll'the
determines that the in limitation received than another component standing alone or in
conjunction with other information known in the Pill meets the standards set forth in the
Attorney (.iuidelines for opening a preliminary terrorism investigation or a tail
errorism investigation and one has not been opened. the shall initiate an
investigation and shall nominate case suhieets for inclusion in 'l?ll)l: the in
accordance ith l-?Bl policy. by forwarding all Intelligence information. as appropriate. it?-
the t"tli's Review and Examination t'nit ('l'ltliXt using the t-?L?itl l'nrm amt
process.
o. The relevant is ill notin the Department ot'lustice component that Intelligence
lntormation prevailed by that component has been used. in whole or in part. as the basis
for a nomination to the 'l'SlNl or the creation ol'a record in 'l'lflli. To the extent possible.
Page. of 5
xtpuaddv
2. the policy ot? the Department ot'Justice is tor all components to provide the Fill with
all domestic or international 'l?crrorism lnlortnation or Terrorist Identi?ers so that the "71]
can make appropriate nominations to the consolidated terrorist walchlist. Willi one
exception relating to 'l?SC?s authorin in exigent circumstances. only the Pill is authorized
to nominate domestic or international terrorists for inclusion in the 'l?SDll on hehatl?ol'the
Department ol'Justice. The FBI has implemented policies governing the submission of
such nominations. including procedures to follow when adding, modifying, or deleting a
T300 record. in making any proposed recommendation for watehlisting, each
component she-old ensure that the underlying information is reasonably accurate. relevant
and timely. to addition. the has implemented its Fromm! (tr-naming: 'l'ermrm
-\'umumrirms These policies must be followed regarding all nominations trom the
')epartment of Justice
5. the THC. naich is administered by the Hit and reports to the Attorney (ieueral. is
permitted to make entries into the 'l'SDtt when exigent circumstances exist. Such
expedited nominations must he made in compliance with the FBI nomination policies and
the 'l'SC's Regarding Nmm?mm?mrr.
The Joint 'l?errorism 'l?ask l-?orecs are a imttli-agemz)l effort led by the
Department ofJustiee and the I?lil tn eomhine and leverage law enforcement and
intelligence community resources to protect the United States from terrorist attach. .t'l?l't?s
are comprised ol'highly trained. locally based. investigators. linguists. and other
specialists from Federal. state. local. tribal, territorial law and intelligence
community agencies. The National .l't't?li was established in Jul}- 2002 to serve as the
coordinating meehanism for the
S. Department ot'lustiee emnponents. other than the hill or the are not permitted to
make direct or :ninations to the 'l'SDll. A Department ol'lostiee component should
inform the appropriate J'l'l'lr through disseminated intelligence reports. electronit'
communication. or other method appropriate to the circumstances when it becomes aware
ot"l?errorist lni'ormation. 't'errorist Identi?ers. or Purely Domestic 'l?errorism lnt'ornnition
(collectively, intelligence lntirrmation). The originating DOJ component should state
whether it recommends watch listing the individual. the basis for that reeonunendation.
and the investigative steps, it'any. it has undertaken regarding the individual. ll'the
determines that the in limitation received than another component standing alone or in
conjunction with other information known in the Pill meets the standards set forth in the
Attorney (.iuidelines for opening a preliminary terrorism investigation or a tail
errorism investigation and one has not been opened. the shall initiate an
investigation and shall nominate case suhieets for inclusion in 'l?ll)l: the in
accordance ith l-?Bl policy. by forwarding all Intelligence information. as appropriate. it?-
the t"tli's Review and Examination t'nit ('l'ltliXt using the t-?L?itl l'nrm amt
process.
o. The relevant is ill notin the Department ot'lustice component that Intelligence
lntormation prevailed by that component has been used. in whole or in part. as the basis
for a nomination to the 'l'SlNl or the creation ol'a record in 'l'lflli. To the extent possible.
Page. of 5
xtpuaddv

the relevant J'l'l'F will assign a representative from the nominating Department ot?Justiee
component to participate in the preliminary or full investigation that arises out of
nominations from Department ol'Justiee components. ()nce noti?ed. the Department
component will provide TREK with additions. or deletions
to a particular record as appropriate regarding that Intelligence Information via the
component's f'l'l? representative.
7. To prevent possible duplicate or partial reporting. the shall he informed that the
FBI and the are the sole TIDE and/or 'l'SDli nominating agencies tor the
Department ol'Justice.
8. 'l?he provisions nl? this Protocol are not intended to prejudice, restrict. or interfere with
any other agreement or arrangement of Department ot'Justiee components, including
arrangements related to law enforcement, exchange of information or
efforts as appropriate.
All l.)epartment ol'Jnstiec components should continue to share Intelligence Information
as appropriate within the US. intelligence Community.
Page 5 ot?S
xtpuaddv
the relevant J'l'l'F will assign a representative from the nominating Department ot?Justiee
component to participate in the preliminary or full investigation that arises out of
nominations from Department ol'Justiee components. ()nce noti?ed. the Department
component will provide TREK with additions. or deletions
to a particular record as appropriate regarding that Intelligence Information via the
component's f'l'l? representative.
7. To prevent possible duplicate or partial reporting. the shall he informed that the
FBI and the are the sole TIDE and/or 'l'SDli nominating agencies tor the
Department ol'Justice.
8. 'l?he provisions nl? this Protocol are not intended to prejudice, restrict. or interfere with
any other agreement or arrangement of Department ot'Justiee components, including
arrangements related to law enforcement, exchange of information or
efforts as appropriate.
All l.)epartment ol'Jnstiec components should continue to share Intelligence Information
as appropriate within the US. intelligence Community.
Page 5 ot?S
xtpuaddv

MEMORANDUM OF UNDERSTANDING
ON TERRORIST REDRESS PROCEDURES
8 xtpuaddv
l'he Department nl'Justiec ll)( )1 t. the Federal Bureau at" lnteStigatinn t. the errerisl
Screening ('enter the Department til I lntnelantl Seettrit} (DI I?ll. the Department ul'Rtate
the ("Tree ul'the Directur ul' Natiunal Intelligence (UDXI the \attnnal
(TentertNUl?Cl. the Central Intelligence Agency the Department ul?
Defense (Ht NJ). and the Department ul'the 'l't'easury [hereinafter t'elet?retl in an the Parties):
Recognizing that the United States(im'ernntent has tletelnped a cunmlidatctl tlatahase nl~
Mum'tl and suspected (L?I'l?tll'ihls that suppurts many tlil?let?c-ttl screening nperated
distinct stalulury and regulalnry authorities:
Recugnixing that agencies that enntrihute tn. compile. distribute. and use the cunsulitlatetl
database must use hcx't el?l'nrts' tn maintain current. accurate. and thumugh
Reengui/ing that the implementation nl'the screening programs nuncthele? nut}. at
times. cause ineumenience. delay. or other experiences for individuals during the
terrurisni screening
Reengni/ing that euniplaintx rceeh etl regarding llte terrorism screening prueevm
he rex lL'? ed and ilder?SSCti ith tlignil} and rexpeet:
Reengnizing that the experience ?11' and other indit itluuls interacting ith
gm et'nnient screening personnel is potentially affected by factors nutaitle the lut'l'tll'ihtll screening;
\enpe nl?this Meinm'antlutn ul' Understanding. including. l'nr example. screening.
screening:I lint? int ult'etnent ilh illicit drugs nr other illegal conduct. heltat iural screening
criteria. as ell the basic prnl'essinnalisnt antl emtrtesy ul'gnt'erntnent screening persunnel.
and that attentiun In these l?aelnrs must he thrnugh other apprtipriate means within the
respective jurisdictiuns til' the Parties:
Reeugnizing than on January I7. 2006. the Departments nl?State antl Ilnmelantl Seettrit}
annuuneetl an initiatit un ?Secure Borders and tpen Hunt's in the luliirmatiun Age.? other? ist-
as the Initiative. including the establishment ul'a redress. prncess tu address
pct'ceitetl pruhlents in internatinnal antl tluniestie trawler sereening: :tntl
Ilat ing cunsultetl ith the Prime} and kit il Liberties Board and the Pl'lHlL?}
and ei\ il liberties til'licials. nl'l)! IS. and in tle\ elnping the prncetlut'ex contained in
this agreement:
llcreh} enter intn this ul?l ntlerslantling
MEMORANDUM OF UNDERSTANDING
ON TERRORIST REDRESS PROCEDURES
8 xtpuaddv
l'he Department nl'Justiec ll)( )1 t. the Federal Bureau at" lnteStigatinn t. the errerisl
Screening ('enter the Department til I lntnelantl Seettrit} (DI I?ll. the Department ul'Rtate
the ("Tree ul'the Directur ul' Natiunal Intelligence (UDXI the \attnnal
(TentertNUl?Cl. the Central Intelligence Agency the Department ul?
Defense (Ht NJ). and the Department ul'the 'l't'easury [hereinafter t'elet?retl in an the Parties):
Recognizing that the United States(im'ernntent has tletelnped a cunmlidatctl tlatahase nl~
Mum'tl and suspected (L?I'l?tll'ihls that suppurts many tlil?let?c-ttl screening nperated
distinct stalulury and regulalnry authorities:
Recugnixing that agencies that enntrihute tn. compile. distribute. and use the cunsulitlatetl
database must use hcx't el?l'nrts' tn maintain current. accurate. and thumugh
Reengui/ing that the implementation nl'the screening programs nuncthele? nut}. at
times. cause ineumenience. delay. or other experiences for individuals during the
terrurisni screening
Reengni/ing that euniplaintx rceeh etl regarding llte terrorism screening prueevm
he rex lL'? ed and ilder?SSCti ith tlignil} and rexpeet:
Reengnizing that the experience ?11' and other indit itluuls interacting ith
gm et'nnient screening personnel is potentially affected by factors nutaitle the lut'l'tll'ihtll screening;
\enpe nl?this Meinm'antlutn ul' Understanding. including. l'nr example. screening.
screening:I lint? int ult'etnent ilh illicit drugs nr other illegal conduct. heltat iural screening
criteria. as ell the basic prnl'essinnalisnt antl emtrtesy ul'gnt'erntnent screening persunnel.
and that attentiun In these l?aelnrs must he thrnugh other apprtipriate means within the
respective jurisdictiuns til' the Parties:
Reeugnizing than on January I7. 2006. the Departments nl?State antl Ilnmelantl Seettrit}
annuuneetl an initiatit un ?Secure Borders and tpen Hunt's in the luliirmatiun Age.? other? ist-
as the Initiative. including the establishment ul'a redress. prncess tu address
pct'ceitetl pruhlents in internatinnal antl tluniestie trawler sereening: :tntl
Ilat ing cunsultetl ith the Prime} and kit il Liberties Board and the Pl'lHlL?}
and ei\ il liberties til'licials. nl'l)! IS. and in tle\ elnping the prncetlut'ex contained in
this agreement:
llcreh} enter intn this ul?l ntlerslantling

I. HACKURHI
8 xtpuaddv
Homeland Security Presidential )it?ecti\ a t? lSl'l Hi I. "Integration and ?se ot'Scrcening
Intiirmatton to Protect \gainst 'l'errorism." dated September In. 2003. required the Attorney
.eneral to establish an to consolidate the (im approach to terrorism
screening and ide tor the appropriate and Ian l'ul use nt?tcrt?orist inliirmation in screening
processes. Also on September lb. 20m. and in support of the Memorandum of
on the Integration and Use nl?Screening Information to Protect .- gains! 'l'crroristn
J-(t Mt )l 7) was signed by the Secretary ul'State. the Attorney (ietteral. the Secretary of
Homeland Security. and the Director ol't?entral Intelligence establishing August 2.
an addendutn (Addendum A), which supplemented and ineorporated by reference all
provisions ol'the was signed by the Secretary ol'the 'l'reasur.? and the Secretary
ol'l)el'ensc. in addition to the signatories ot'tlte llSl?lMi By their signatures on
the Secretary ot'the and the Secretary ol~ Del'euse also became
sitinatories to the llSl?le Mt In 2007. Addendum A was superseded h} Addendum B.
hieh added the Director ol'National Intelligence and the Director ol'tlte ?l'St? as signatories.
2. l?L?Rl?t?tSl-? s( 1 31?
l?hc purpose ol'this is to set forth the understamling ol'the Parties to establish and
implement a coordinated redress process to respond to indix idual complaints about atherse
experiences during terrorism screening that relate to tlte Use of tn the
gm emment's consolidated database ot'kno? and suspected terrorists. knnu as the Terrorist
Screening Database or rsnn. 'l'his Mt is intended to complement. and shall not be construed
to coutlict ith. the Constitution. statutes. or regulations of the United States or any Party's legal
authority to process screening-related complaints or app ads. in the extent that any ision ot
this Mt?? con?icts with any Party's legal authority for screening or to ltear appeals. the
con?icting provisions ol'this Ml shall not apply. This MUU does not apply to individual
complaints. or parts thereof. that pertain tn screening esperienecs that are unrelated to the use of
contained in the T308.
-\ny reference in this Ml to a Party or l'artics shall also be understood to rel'er to any
components ol'such Part} or Parties to the e\tent that such components l'all xx itltitt the de?nition
ot'screening agency or agency as set forth heloxy. or that such
components haxe been designated by the l?itt'l) or Parties as hat ing obligations arising from [his
\lt Nothing in this Mt precludes any Party from conducting periodic re\ ieus ot~
indix idttals in the to determine uhethet' an indix idual should remain in the hat
their status modi?ed. or be remoyed than the tn this \ll shall be
construed to mterl'ere uith. limit. or impede an} l?arty 's ability to protect inliirutation that is
classi?ed pursuant to l'\ecuti\e )rdcr 13053. as amended. or is other? ise protected by In? from
disclosure.
I. HACKURHI
8 xtpuaddv
Homeland Security Presidential )it?ecti\ a t? lSl'l Hi I. "Integration and ?se ot'Scrcening
Intiirmatton to Protect \gainst 'l'errorism." dated September In. 2003. required the Attorney
.eneral to establish an to consolidate the (im approach to terrorism
screening and ide tor the appropriate and Ian l'ul use nt?tcrt?orist inliirmation in screening
processes. Also on September lb. 20m. and in support of the Memorandum of
on the Integration and Use nl?Screening Information to Protect .- gains! 'l'crroristn
J-(t Mt )l 7) was signed by the Secretary ul'State. the Attorney (ietteral. the Secretary of
Homeland Security. and the Director ol't?entral Intelligence establishing August 2.
an addendutn (Addendum A), which supplemented and ineorporated by reference all
provisions ol'the was signed by the Secretary ol'the 'l'reasur.? and the Secretary
ol'l)el'ensc. in addition to the signatories ot'tlte llSl?lMi By their signatures on
the Secretary ot'the and the Secretary ol~ Del'euse also became
sitinatories to the llSl?le Mt In 2007. Addendum A was superseded h} Addendum B.
hieh added the Director ol'National Intelligence and the Director ol'tlte ?l'St? as signatories.
2. l?L?Rl?t?tSl-? s( 1 31?
l?hc purpose ol'this is to set forth the understamling ol'the Parties to establish and
implement a coordinated redress process to respond to indix idual complaints about atherse
experiences during terrorism screening that relate to tlte Use of tn the
gm emment's consolidated database ot'kno? and suspected terrorists. knnu as the Terrorist
Screening Database or rsnn. 'l'his Mt is intended to complement. and shall not be construed
to coutlict ith. the Constitution. statutes. or regulations of the United States or any Party's legal
authority to process screening-related complaints or app ads. in the extent that any ision ot
this Mt?? con?icts with any Party's legal authority for screening or to ltear appeals. the
con?icting provisions ol'this Ml shall not apply. This MUU does not apply to individual
complaints. or parts thereof. that pertain tn screening esperienecs that are unrelated to the use of
contained in the T308.
-\ny reference in this Ml to a Party or l'artics shall also be understood to rel'er to any
components ol'such Part} or Parties to the e\tent that such components l'all xx itltitt the de?nition
ot'screening agency or agency as set forth heloxy. or that such
components haxe been designated by the l?itt'l) or Parties as hat ing obligations arising from [his
\lt Nothing in this Mt precludes any Party from conducting periodic re\ ieus ot~
indix idttals in the to determine uhethet' an indix idual should remain in the hat
their status modi?ed. or be remoyed than the tn this \ll shall be
construed to mterl'ere uith. limit. or impede an} l?arty 's ability to protect inliirutation that is
classi?ed pursuant to l'\ecuti\e )rdcr 13053. as amended. or is other? ise protected by In? from
disclosure.

3. DEFINITIONS
As used itt this Mt these or phrases are delined as lollows:
B.
3 xtpuaddv
Comp/aim or Rec/rem ('unm/uim: An individual?s statement about an allegedly
adverse experience or outcome during a terrorism screening process. which
usually includes a request for assistance or a remedy.
Dementia-r 'I'hc inliirmation relied upon or generated by a
nominating/originating agency to support the nomination ol?an individual to the
Known m- .S'uspeelccl Yerrm'isl: As delined by an individual known or
appropriately suspected to be or to have been engaged in conduct constituting. in
preparation for. in aid of. or related to terrorism. Pursuant to the
shall ittclude identilying inliu?nuuion about all known or suspected terrorists.
Person: An individual who has had an adverse experichc or
outcome during terrorism screening because the individual is a near match to a
knonn or suspected terrorist in the TSDB. isidcntilied persons are not actually
listed in the TSUB but usually share an identical or very similar name and date at
birth with a person in the which causes them to be delayed or otherwise
inconvenienced during screening.
A Federal agency that has determined that an individual is a
known or suspected terrorist and nominates that individual to the TSDB based on
in lormation that originated with that agency and/or a third agency.
Originating A Federal agency that generates derogatory or identifying
inlorntation about a known or suspected terrorist.
Persona/Ir Information: Any representation of inl?onnation that
permits the identity ol?an individtutl to whom the inlormation applies to be
reasonably inferred by either direct or indirect means including any other
inlortnation. which is linked to such individual.
It?eu'ress: The process whereby an individual may seek the help ol?a screening
agency in addressing the cause ot'an adverse experience or outcome related to the
use data by tiling a complaint with the screening agency. The screening
agency or its designee, in cooperation with and the nominaling/originating
agency. provides assistance by determining the cause ot'that adverse experience.
verilying that all relevant information relied ttpon in the screening process is
thorough. accurate. and current. and making any warranted corrections to
pertinent records. The redress process as de?ned in this paragraph does not apply
to complaints related to the visa application process.
Screening.rlgema': Any agency that conducts terrorism screening. A screening
agency acquires intornmtion for the purpose ol? determining whether an individual
is a known or suspected terrorist in the and evaluates and/or uses that
information in order to take a particular gm-?ernmental action with respect to an
individual. such as requiring additional physical security screening at an airport
security checkpoint. determining admissibility into the United States. or similar
?41
3. DEFINITIONS
As used itt this Mt these or phrases are delined as lollows:
B.
3 xtpuaddv
Comp/aim or Rec/rem ('unm/uim: An individual?s statement about an allegedly
adverse experience or outcome during a terrorism screening process. which
usually includes a request for assistance or a remedy.
Dementia-r 'I'hc inliirmation relied upon or generated by a
nominating/originating agency to support the nomination ol?an individual to the
Known m- .S'uspeelccl Yerrm'isl: As delined by an individual known or
appropriately suspected to be or to have been engaged in conduct constituting. in
preparation for. in aid of. or related to terrorism. Pursuant to the
shall ittclude identilying inliu?nuuion about all known or suspected terrorists.
Person: An individual who has had an adverse experichc or
outcome during terrorism screening because the individual is a near match to a
knonn or suspected terrorist in the TSDB. isidcntilied persons are not actually
listed in the TSUB but usually share an identical or very similar name and date at
birth with a person in the which causes them to be delayed or otherwise
inconvenienced during screening.
A Federal agency that has determined that an individual is a
known or suspected terrorist and nominates that individual to the TSDB based on
in lormation that originated with that agency and/or a third agency.
Originating A Federal agency that generates derogatory or identifying
inlorntation about a known or suspected terrorist.
Persona/Ir Information: Any representation of inl?onnation that
permits the identity ol?an individtutl to whom the inlormation applies to be
reasonably inferred by either direct or indirect means including any other
inlortnation. which is linked to such individual.
It?eu'ress: The process whereby an individual may seek the help ol?a screening
agency in addressing the cause ot'an adverse experience or outcome related to the
use data by tiling a complaint with the screening agency. The screening
agency or its designee, in cooperation with and the nominaling/originating
agency. provides assistance by determining the cause ot'that adverse experience.
verilying that all relevant information relied ttpon in the screening process is
thorough. accurate. and current. and making any warranted corrections to
pertinent records. The redress process as de?ned in this paragraph does not apply
to complaints related to the visa application process.
Screening.rlgema': Any agency that conducts terrorism screening. A screening
agency acquires intornmtion for the purpose ol? determining whether an individual
is a known or suspected terrorist in the and evaluates and/or uses that
information in order to take a particular gm-?ernmental action with respect to an
individual. such as requiring additional physical security screening at an airport
security checkpoint. determining admissibility into the United States. or similar
?41

governmental action. The and DHS shall not be considered screening
agencies with respect to the visa application process.
Terror-?rm Screening: The evaluation ofan individual to whether he or
she is a known or suspected terrorist identified in the TSDB in order to take a
particular governmental action with respect to an individual. as requiring
additional physical security screening at an airport security checkpoint.
determining admissibility into the United States. or similar governmental action.
Terrorist Database or TSDB: The Federal government?s consolidated
database that contains identifying intiirmation about known or suspected
terrorists. lt is also commonly known as the consolidated terrorist watchlist. 'l'he
TSDB is a sensitive but unclassi?ed database and does not contain any derogatory
in formation.
'l'errorist Identities Datamart [Environment which is a
classified database containing the derogatory that supports the
nominations ofknown or suspected international terrorists to the TSDB.
3 xipuaddv
RESPONSIBILITIES OF TI IE PARTIES
.
Responsibilities of All Parties;
i. Designation of Responsible Official. I'iach Party will identify a senior
official who will he responsible for ensuring the Party's full participation
in the redress process and overall compliance with this MOU. A Party
may also designate redress officials for eomprments ofthat Party that
perform screening or nominating/originating agency functions. The
Patties agree to identify these officials and exchange the names ofthesc
of?cials no later than 30 calendar days alter this MOU becomes effective
and Update the information as needed thereafter.
ii. Resources. Subject to the a 'ailability of funds. ?ach Party will identify
and commit appropriate staff and other resources to carry out
responsibilities under this MOU. This includes identifying the olticcts)
responsible for carrying Party's responsibilities pertaining to the
processing of individual redress eontplaints as set forth in this MOU. The
Parties agree to exchange the names and contact information for the
responsible offices no later than 30 calendar days after this MOU becomes
effective. and update the information as needed thereafter.
Information Sharing. liach Party will sltare all information relevant to the
resolution ofa complaint with other Parties to the extent necessary to
carry out this MOU or to defend any judicial challenge to the resolution of
a complaint. consistent with legal requirements and classi?cation and
handling controls. A Party may provide the relevant in formation in a
or substituted format to protect sensitive sources and
methods.
iv. Protection of Personallv Identifiable liaeh Party will take
appropriate action to protect personally identi?able information (PM) in its
own record systems related to a redress matter against unauthorized access
4
governmental action. The and DHS shall not be considered screening
agencies with respect to the visa application process.
Terror-?rm Screening: The evaluation ofan individual to whether he or
she is a known or suspected terrorist identified in the TSDB in order to take a
particular governmental action with respect to an individual. as requiring
additional physical security screening at an airport security checkpoint.
determining admissibility into the United States. or similar governmental action.
Terrorist Database or TSDB: The Federal government?s consolidated
database that contains identifying intiirmation about known or suspected
terrorists. lt is also commonly known as the consolidated terrorist watchlist. 'l'he
TSDB is a sensitive but unclassi?ed database and does not contain any derogatory
in formation.
'l'errorist Identities Datamart [Environment which is a
classified database containing the derogatory that supports the
nominations ofknown or suspected international terrorists to the TSDB.
3 xipuaddv
RESPONSIBILITIES OF TI IE PARTIES
.
Responsibilities of All Parties;
i. Designation of Responsible Official. I'iach Party will identify a senior
official who will he responsible for ensuring the Party's full participation
in the redress process and overall compliance with this MOU. A Party
may also designate redress officials for eomprments ofthat Party that
perform screening or nominating/originating agency functions. The
Patties agree to identify these officials and exchange the names ofthesc
of?cials no later than 30 calendar days alter this MOU becomes effective
and Update the information as needed thereafter.
ii. Resources. Subject to the a 'ailability of funds. ?ach Party will identify
and commit appropriate staff and other resources to carry out
responsibilities under this MOU. This includes identifying the olticcts)
responsible for carrying Party's responsibilities pertaining to the
processing of individual redress eontplaints as set forth in this MOU. The
Parties agree to exchange the names and contact information for the
responsible offices no later than 30 calendar days after this MOU becomes
effective. and update the information as needed thereafter.
Information Sharing. liach Party will sltare all information relevant to the
resolution ofa complaint with other Parties to the extent necessary to
carry out this MOU or to defend any judicial challenge to the resolution of
a complaint. consistent with legal requirements and classi?cation and
handling controls. A Party may provide the relevant in formation in a
or substituted format to protect sensitive sources and
methods.
iv. Protection of Personallv Identifiable liaeh Party will take
appropriate action to protect personally identi?able information (PM) in its
own record systems related to a redress matter against unauthorized access
4

vi.
vii.
and to ensure that is handled in a way that provides security and
accountability. When Parties transmit related to a redress tnatlcr via
non-electronic or electronic means. such as etnail. laesimile. portable
media or otherwise. the Parties will properly mark the data andfor
to provide appropriate notice ol'the
existence of PH and will ettsurc the ?ans ol'tt'ansmission are secured by
or equi 'alent protections.
.-\dministrativc Record. Each Party will be responsible for maintaining the
administrative records necessary to document its participation the
redress process.
Liudatine Agency Records. Each Party that maintains data related to the
terrorist watchlist in its paper and/or electronic reeordkceping systems will
update its records correct. modify. or delete) expeditioust once
notil'ted ol'a change to an individual?s watehlist status as the result ol'the
disposition ol?a redress matter. This provision applies to data in
government systems te.g.. 'I'll)li. Treasury Enforcement
L?ommunications Border inspection System
No-Fly List. Consular Lookout And Support System] used
for 'atehlist creation or screening purposes. It is not intended to require
the ?arties to change records that rellect actions already taken based on
'atchlist status. unless and only to the extent that the record will have an
um 'arranted adverse impact on the individual seeking redress.
Litigation. Subject to paragraph above. each Party agrees to
cooperate with 00.! to assist in defending any judicial challenge to the
resolution of a redress contplaint processed under this or a
determitmtion by a screening agency that relied in whole or in part on
records or inlormation in the TSDB. This provision shall not be construed
to limit DOS's discretion under section 322i I) ol'thc and
Nationality Act (INA). 8 l2ll2tl?). concerning the disclosure ot?
visa records itt litigation.
l?rivacv Act (.?omnliancc. in carrying out this MOU. each Party is
responsible for its own compliance with the Privacy Act of N74. 5
55.71am in the collection. maintenance. use. and
dissemination of personally identi?able information. Within 30 calendar
days after the el'l'ectivc date ot?this MOU, each Party agrees to review its
applicable Privacy Act system of records notices and any relevant lorms
used to collect inlormation from the public where ma)
ultimater be used the redress process. liach Party agrees to make
appropriate changes to those documents. if necessary. including the
publication ol'new or modilied routine uses to permit the sharing of
inlormation to resolve redress matters and related litigation.
Record Retention. [Each Party agrees to retain its redress records for at
least sis years from the date ol? linal agency disposition. Agencies may
8 xipuaddv
vi.
vii.
and to ensure that is handled in a way that provides security and
accountability. When Parties transmit related to a redress tnatlcr via
non-electronic or electronic means. such as etnail. laesimile. portable
media or otherwise. the Parties will properly mark the data andfor
to provide appropriate notice ol'the
existence of PH and will ettsurc the ?ans ol'tt'ansmission are secured by
or equi 'alent protections.
.-\dministrativc Record. Each Party will be responsible for maintaining the
administrative records necessary to document its participation the
redress process.
Liudatine Agency Records. Each Party that maintains data related to the
terrorist watchlist in its paper and/or electronic reeordkceping systems will
update its records correct. modify. or delete) expeditioust once
notil'ted ol'a change to an individual?s watehlist status as the result ol'the
disposition ol?a redress matter. This provision applies to data in
government systems te.g.. 'I'll)li. Treasury Enforcement
L?ommunications Border inspection System
No-Fly List. Consular Lookout And Support System] used
for 'atehlist creation or screening purposes. It is not intended to require
the ?arties to change records that rellect actions already taken based on
'atchlist status. unless and only to the extent that the record will have an
um 'arranted adverse impact on the individual seeking redress.
Litigation. Subject to paragraph above. each Party agrees to
cooperate with 00.! to assist in defending any judicial challenge to the
resolution of a redress contplaint processed under this or a
determitmtion by a screening agency that relied in whole or in part on
records or inlormation in the TSDB. This provision shall not be construed
to limit DOS's discretion under section 322i I) ol'thc and
Nationality Act (INA). 8 l2ll2tl?). concerning the disclosure ot?
visa records itt litigation.
l?rivacv Act (.?omnliancc. in carrying out this MOU. each Party is
responsible for its own compliance with the Privacy Act of N74. 5
55.71am in the collection. maintenance. use. and
dissemination of personally identi?able information. Within 30 calendar
days after the el'l'ectivc date ot?this MOU, each Party agrees to review its
applicable Privacy Act system of records notices and any relevant lorms
used to collect inlormation from the public where ma)
ultimater be used the redress process. liach Party agrees to make
appropriate changes to those documents. if necessary. including the
publication ol'new or modilied routine uses to permit the sharing of
inlormation to resolve redress matters and related litigation.
Record Retention. [Each Party agrees to retain its redress records for at
least sis years from the date ol? linal agency disposition. Agencies may
8 xipuaddv

elect to establish a longer retention period to meet statutor}. regulator). or
operational requirements.
Requests for Disclosure of'l'SllB Data. L'nless attd until ad\ iscs the
Parties ofan alternate procedure. each Party agrees that it still contact
legal counsel if it such es a request for inlortnation or records that
it knons would eal an indi\ idttal's status tposititc or negatii et in the
or would othernisc re\ cal the contents of data. legal
counsel nill provide timely guidance on to respond to these requests.
This prorision also pertains to requests for data resident in
supported screening systems. such as the Nosl-?Iy List. ?l'liL'Si IBIS. the
National Crime Information 'enter's Violent (iang and 'l'crrorist
()rganixatit?m I?ilc i'I'l I. and the )S?s Consular Lookout attd
Support System (CLASH).
ll. Responsibilities ol?SereeningI Agencies:
Designation of Responsibilities. An} Party tltat is a screening agency ma).
designate another Party. ith the other consent ifneeded. to
perform the responsibilities outlined itt section 4.15. ofthis MI W. In
addition. here a screening agency is a ot'a Part}. the Part}
Illil} determine at its discretion that an}- responsibilil} ot'that screening
agene} out} be performed in ?hole or pan b} the Part}.
Resources. Subject to the :nailability of funds. each screening agcnc
ill designate or create an office to carry out its operational
responsibilities for redress. Where a Part} has several components that
perform terrorism screening. the responsible official for that Party ts'et'
Section above) ill determine whether a single centralized office or
separate offices in the appropriate components. or some cotnbination of
the two. will perform tltis function. Subject to the availability of funds.
each screening agency will comntit suf?cient and appropriate staffand
resources to that office or offices to ensure redress complaints are
processed in a timely attd efficient manner. The screening agencies agree
to notify the other Parties ofthe identity ol'and contact information for the
designated ofliees under this paragraph no later than 30 calendar da)
after this becomes effectixe and update that information as needed.
Receipt and Initial Processing ofL'onn'ilaints. liach screening agettc} ?ill
hax a procedure for rceeis ing complaints from members ofthe public. If
the screening agency receii es a complaint from an indi\ idual who appears
to be in the TSDII and the complaint relates to an ad\ ctse effect in the
screening process arising out ofhis her in the the
agenc} \xill fomard a cop) ofthe complaint and related information to
nithin a reasonable time. The screening agenc} ?ill be responsible
for the identil} ofthe complainant in accordance ith the
screening agency's applicable regulations and policies. When litrtxarding
a complaint to the screening agency must pt?tn idc; I i all rcIe\ ant
correspondence the individual. copies ofany relevant internal
(i
3 xtpuaddv
elect to establish a longer retention period to meet statutor}. regulator). or
operational requirements.
Requests for Disclosure of'l'SllB Data. L'nless attd until ad\ iscs the
Parties ofan alternate procedure. each Party agrees that it still contact
legal counsel if it such es a request for inlortnation or records that
it knons would eal an indi\ idttal's status tposititc or negatii et in the
or would othernisc re\ cal the contents of data. legal
counsel nill provide timely guidance on to respond to these requests.
This prorision also pertains to requests for data resident in
supported screening systems. such as the Nosl-?Iy List. ?l'liL'Si IBIS. the
National Crime Information 'enter's Violent (iang and 'l'crrorist
()rganixatit?m I?ilc i'I'l I. and the )S?s Consular Lookout attd
Support System (CLASH).
ll. Responsibilities ol?SereeningI Agencies:
Designation of Responsibilities. An} Party tltat is a screening agency ma).
designate another Party. ith the other consent ifneeded. to
perform the responsibilities outlined itt section 4.15. ofthis MI W. In
addition. here a screening agency is a ot'a Part}. the Part}
Illil} determine at its discretion that an}- responsibilil} ot'that screening
agene} out} be performed in ?hole or pan b} the Part}.
Resources. Subject to the :nailability of funds. each screening agcnc
ill designate or create an office to carry out its operational
responsibilities for redress. Where a Part} has several components that
perform terrorism screening. the responsible official for that Party ts'et'
Section above) ill determine whether a single centralized office or
separate offices in the appropriate components. or some cotnbination of
the two. will perform tltis function. Subject to the availability of funds.
each screening agency will comntit suf?cient and appropriate staffand
resources to that office or offices to ensure redress complaints are
processed in a timely attd efficient manner. The screening agencies agree
to notify the other Parties ofthe identity ol'and contact information for the
designated ofliees under this paragraph no later than 30 calendar da)
after this becomes effectixe and update that information as needed.
Receipt and Initial Processing ofL'onn'ilaints. liach screening agettc} ?ill
hax a procedure for rceeis ing complaints from members ofthe public. If
the screening agency receii es a complaint from an indi\ idual who appears
to be in the TSDII and the complaint relates to an ad\ ctse effect in the
screening process arising out ofhis her in the the
agenc} \xill fomard a cop) ofthe complaint and related information to
nithin a reasonable time. The screening agenc} ?ill be responsible
for the identil} ofthe complainant in accordance ith the
screening agency's applicable regulations and policies. When litrtxarding
a complaint to the screening agency must pt?tn idc; I i all rcIe\ ant
correspondence the individual. copies ofany relevant internal
(i
3 xtpuaddv

vi.
vii.
agency records. and (3) information identil'ying the cotnplainant including.
at a minimum. the complainant?s full name. date ol'hirtlt. and place of
citizenship. After consultation with affected Parties. may revise
these requirements in the future as needed for expeditious processing of
redress complaints. No amendtnent to the MUU would be required to
effectuate such a change.
Follow-up with the Complainant. ll?rcquested by the screening
agency will contact the complainant to request additional information to
assist or the nominatbig/originating agency in verifying the
complainant?s identity and processing the complaint. Nothing in this
subsection precludes a screening agency from contacting the et'implainanl
in accordance with the screening agency?s procedures or discretion.
Response to the Complainant. Screening agencies are responsible for
providing a written response to complaints they receive based on
infm?matimi provided by and the nominating/origimiling agency.
Because ofthe sensitivity ofthe and derogatory information. the
content ofany response to a complaint must be coordinated with l?St.? and
the nomimtting/originating agency through Screening agencies may
use standardized response letters that have been coordinated in advance by
the screening agency. and
Rcdress for Misidentilied Persons. On January I7. 2000. DHS and DOS
announced an initiative on ?Secure Borders and Open Doors in the
lnliirmation Age." otherwise known as the Riee-C'hertofl' Initiative. which
includes the establishment ol'a redress process to address perceived
problems in intermttiomtl and domestic traveler screening. The HHS
Screening Coordination Office is I aiding the inter-agency ell'ort to fulfill
the goals ofthe Ricei'hertol'l'Initiative. which is intended to improve the
redress process for persons who are misidenti?ed during traveler
screening processes. among other improvements.
Administrative Appeals. If the screening agency has established an
administrative appeals process for redress determinations or other agency
determinations in which the TSDB was used. the screening agency will
notify after receiving any such administrative appeal and work with
as needed. to process the appeal. and coordinate the linal agency
response with The screening agency will provide all relevant
paperwork to (including a copy oftlt appeal letter and any
inliirmation submitted by the individual on their own behalf). When the
screening agency has the legal authority to make the tinal decision on the
appeal. it will notify ofthat decision.
Litigat?i. When the screening agency becomes aware of litigation arising
out ofterrorism screening. the screening agency will notify and
as soon as possible after identilying the nexus to the TEDH. Notification
should occur as soon as the Patty learns ofan individual's intent to sue or
immediately after being served with legal process.
3 xtpuaddv
vi.
vii.
agency records. and (3) information identil'ying the cotnplainant including.
at a minimum. the complainant?s full name. date ol'hirtlt. and place of
citizenship. After consultation with affected Parties. may revise
these requirements in the future as needed for expeditious processing of
redress complaints. No amendtnent to the MUU would be required to
effectuate such a change.
Follow-up with the Complainant. ll?rcquested by the screening
agency will contact the complainant to request additional information to
assist or the nominatbig/originating agency in verifying the
complainant?s identity and processing the complaint. Nothing in this
subsection precludes a screening agency from contacting the et'implainanl
in accordance with the screening agency?s procedures or discretion.
Response to the Complainant. Screening agencies are responsible for
providing a written response to complaints they receive based on
infm?matimi provided by and the nominating/origimiling agency.
Because ofthe sensitivity ofthe and derogatory information. the
content ofany response to a complaint must be coordinated with l?St.? and
the nomimtting/originating agency through Screening agencies may
use standardized response letters that have been coordinated in advance by
the screening agency. and
Rcdress for Misidentilied Persons. On January I7. 2000. DHS and DOS
announced an initiative on ?Secure Borders and Open Doors in the
lnliirmation Age." otherwise known as the Riee-C'hertofl' Initiative. which
includes the establishment ol'a redress process to address perceived
problems in intermttiomtl and domestic traveler screening. The HHS
Screening Coordination Office is I aiding the inter-agency ell'ort to fulfill
the goals ofthe Ricei'hertol'l'Initiative. which is intended to improve the
redress process for persons who are misidenti?ed during traveler
screening processes. among other improvements.
Administrative Appeals. If the screening agency has established an
administrative appeals process for redress determinations or other agency
determinations in which the TSDB was used. the screening agency will
notify after receiving any such administrative appeal and work with
as needed. to process the appeal. and coordinate the linal agency
response with The screening agency will provide all relevant
paperwork to (including a copy oftlt appeal letter and any
inliirmation submitted by the individual on their own behalf). When the
screening agency has the legal authority to make the tinal decision on the
appeal. it will notify ofthat decision.
Litigat?i. When the screening agency becomes aware of litigation arising
out ofterrorism screening. the screening agency will notify and
as soon as possible after identilying the nexus to the TEDH. Notification
should occur as soon as the Patty learns ofan individual's intent to sue or
immediately after being served with legal process.
3 xtpuaddv

Responsibilities ot? the 'I"errorist Screening t'entcr:
I.
Receipt and Coordination will reccixe complaints
from screening agencies and research them to determine the nature and
cause ol'the indiridttal's experience. will track all
and will he responsible for facilitating any inter-agency
coordination necessary to properly rcscarclt the complaint and respond to
the screening agency regarding the outcome leg. any corrections made or
recommended t.
Rex icw ol? Basis for Inclusion in the ?l'ShB. Itt cases where the
complainant is or appears to he in the ill idc copies of
tlte complaint letter and other relcx ant ittlot'ntalion to Xt'l t? attd or the
nominating originating agency to assist to the resolution complaint.
will then work with MSI and or the nominating originating
as appropriate. to determine whether the complainant's current
status the is appropriate hascd on the most current. accurate. attd
thorough inlormalion tnailuhle. may atst attd.or the
uontittatiug/origiuatiug agency to prot'tde updated information or analysis
to assist in this determination as well as for a recommend-ation on
addressing the complaint.
A l'ter ret iewing the atailahle information and considering
an} recotmnettdation from the nominating'originatittg TSC will
make a determittation whether the record should remain the TSUB.
hat its status modi?ed. or he remm ed. unless the legal
to make such a determination resides. in ltole or part. ith another
agene}. In such cases. will onl) prepare a recimintentlatiott for the
decision-making agency and will implement an)? determination once
made. ill take an) necessary action to implement the determination.
suclt as removing the record from the ISUH or ntodilying the record's
status in the leg. downgrade li?om Nit-lily to Helectce). Before
taking action that is inconsistent with a recommendation ol'thc
nominalpig/originating agency. will notil'y which ill com
that determination hack to the nominating?originating agettc}. unless the
nontiuatittg-originating agency is the itt which case will contact
the l-lil directl). The itominatinglorigatatittg agency will then be
responsible for addressing the conlliet ith or the decision-making
agenc) either directl} or through Nt?l?t'. The Parties will then coordinate
on an agreed?to resolution.
I pdatc ol?tltc '1 will ensure that records are
appropriatcl} deleted or modi?ed in accordance ith a determination on :t
redress matter. will also \cril'y that such retnotals or modi?cations
carr) over to other screening systems that data te.g.,
No-l-?Iy List).
DeconlIietion. In the event ol'a multi-agettcy nomination where the
nominating and-tor originating agencies do not agree on what
recommendation should he made on a specilie redress matter. ill
3 xtpuaddv
Responsibilities ot? the 'I"errorist Screening t'entcr:
I.
Receipt and Coordination will reccixe complaints
from screening agencies and research them to determine the nature and
cause ol'the indiridttal's experience. will track all
and will he responsible for facilitating any inter-agency
coordination necessary to properly rcscarclt the complaint and respond to
the screening agency regarding the outcome leg. any corrections made or
recommended t.
Rex icw ol? Basis for Inclusion in the ?l'ShB. Itt cases where the
complainant is or appears to he in the ill idc copies of
tlte complaint letter and other relcx ant ittlot'ntalion to Xt'l t? attd or the
nominating originating agency to assist to the resolution complaint.
will then work with MSI and or the nominating originating
as appropriate. to determine whether the complainant's current
status the is appropriate hascd on the most current. accurate. attd
thorough inlormalion tnailuhle. may atst attd.or the
uontittatiug/origiuatiug agency to prot'tde updated information or analysis
to assist in this determination as well as for a recommend-ation on
addressing the complaint.
A l'ter ret iewing the atailahle information and considering
an} recotmnettdation from the nominating'originatittg TSC will
make a determittation whether the record should remain the TSUB.
hat its status modi?ed. or he remm ed. unless the legal
to make such a determination resides. in ltole or part. ith another
agene}. In such cases. will onl) prepare a recimintentlatiott for the
decision-making agency and will implement an)? determination once
made. ill take an) necessary action to implement the determination.
suclt as removing the record from the ISUH or ntodilying the record's
status in the leg. downgrade li?om Nit-lily to Helectce). Before
taking action that is inconsistent with a recommendation ol'thc
nominalpig/originating agency. will notil'y which ill com
that determination hack to the nominating?originating agettc}. unless the
nontiuatittg-originating agency is the itt which case will contact
the l-lil directl). The itominatinglorigatatittg agency will then be
responsible for addressing the conlliet ith or the decision-making
agenc) either directl} or through Nt?l?t'. The Parties will then coordinate
on an agreed?to resolution.
I pdatc ol?tltc '1 will ensure that records are
appropriatcl} deleted or modi?ed in accordance ith a determination on :t
redress matter. will also \cril'y that such retnotals or modi?cations
carr) over to other screening systems that data te.g.,
No-l-?Iy List).
DeconlIietion. In the event ol'a multi-agettcy nomination where the
nominating and-tor originating agencies do not agree on what
recommendation should he made on a specilie redress matter. ill
3 xtpuaddv

joint recommendation to ll?the miminatingl'origimtting agencies
request that the agencies consult with one another and share appropriate
information about the watchlisted individual in an attetnpt to provid a
3 xtpuaddv
cannot agree to ajoint recommendation. or other agency with the
legal authority to make the decision} will make the linal determination
considering the inl'ormatitm provided by each agency.
Review Related to Misidenlilicd Persons. Ilia complainant's adtersc
experience or outcome during terrorism screening is a result of being a
near match to a record in the TSDB. and that complaint
is rcl'erred to by the screening agency. will review the record in
the TSUB, as described in the paragraphs: above. to ensure the TSUH
record is valid and satis?es the criteria for inclusion in the and
dctertnine il't?tdditional information can be added to the or
other agency systems to reduce the likelihood ol'a l'uture misideotilication.
ll'the record does not meet the criteria. it will be removed liom the
Administrative Appeals. will work with a screening agency to assist
it in processing any administrative appeal ol?a redress determination or
other determination in which the TSDB was used. When receives
notice of an appeal. will notify I and/or the
nominating/originating agency as soon as possible. will facilitate
conununiealions between the nominatinghniginating and screening
agencies on the Following issues: i determining what material may be
rel 'asablc to the individual during appeal (if applicable). and t2) ttpdating
the analysis ol'any inli?nrntation that may have developed since the original
determination and/or any information that was provided by the individual
on his or her behall'doring the appeals process itself. Alter reviewing the
available information and considering any recommendation from the
nomimtting/originating agency. will make a determination whether
the record should remain in the have its TSDB status modi?ed. or
he removed. unless legal authority to make such a determination
resides. in whole or in part. with another agency. In such cases. will
only prepare a recommendation for the decision-making agency and will
implement any determination once made.
Litigation. When becomes aware ot?litigation arising out of terrorism
screening. will notify the nominaling/originating agency. and
l)C).l as soon as possible.
Responsibilities ol'tlte National Center:
[LevichC?oordinalion, and Research of Complaints. Upon receipt ol' a
complaint from NCTC will review its holdings. notify the
nomihating/originaling agency ol?the complaint. and provide the
nominaling/originating agency with a copy ol'thc complaint for review.
0
joint recommendation to ll?the miminatingl'origimtting agencies
request that the agencies consult with one another and share appropriate
information about the watchlisted individual in an attetnpt to provid a
3 xtpuaddv
cannot agree to ajoint recommendation. or other agency with the
legal authority to make the decision} will make the linal determination
considering the inl'ormatitm provided by each agency.
Review Related to Misidenlilicd Persons. Ilia complainant's adtersc
experience or outcome during terrorism screening is a result of being a
near match to a record in the TSDB. and that complaint
is rcl'erred to by the screening agency. will review the record in
the TSUB, as described in the paragraphs: above. to ensure the TSUH
record is valid and satis?es the criteria for inclusion in the and
dctertnine il't?tdditional information can be added to the or
other agency systems to reduce the likelihood ol'a l'uture misideotilication.
ll'the record does not meet the criteria. it will be removed liom the
Administrative Appeals. will work with a screening agency to assist
it in processing any administrative appeal ol?a redress determination or
other determination in which the TSDB was used. When receives
notice of an appeal. will notify I and/or the
nominating/originating agency as soon as possible. will facilitate
conununiealions between the nominatinghniginating and screening
agencies on the Following issues: i determining what material may be
rel 'asablc to the individual during appeal (if applicable). and t2) ttpdating
the analysis ol'any inli?nrntation that may have developed since the original
determination and/or any information that was provided by the individual
on his or her behall'doring the appeals process itself. Alter reviewing the
available information and considering any recommendation from the
nomimtting/originating agency. will make a determination whether
the record should remain in the have its TSDB status modi?ed. or
he removed. unless legal authority to make such a determination
resides. in whole or in part. with another agency. In such cases. will
only prepare a recommendation for the decision-making agency and will
implement any determination once made.
Litigation. When becomes aware ot?litigation arising out of terrorism
screening. will notify the nominaling/originating agency. and
l)C).l as soon as possible.
Responsibilities ol'tlte National Center:
[LevichC?oordinalion, and Research of Complaints. Upon receipt ol' a
complaint from NCTC will review its holdings. notify the
nomihating/originaling agency ol?the complaint. and provide the
nominaling/originating agency with a copy ol'thc complaint for review.
0

will then request that the nominatirig/originating agency and. as
appropriate. any other agency with relevant information. review their
holdings and provide inlormation relevant to the cotnplaint. This
may include updated inlin?nnttion or analysis regarding the complainant?s
current in tlte derogatory inliirmation. identifying
inlormation that might he relevant to a misiden'til'tcation. or other
potentially relevant information or analysis tittcluding that which tends to
show that the individual is not a known or suspected terrorist. or which
otherwise tends to cast doubt on the derogatory information). will
also request that the nominatirig/originating agency provide its
recommendation regarding resolution of the complaint. With the
concurrence ol'thc nontitinting/originating agency. NCTC will provide
that agency's recommendation and any other relevant information to TSP.
Should or another agency disagree with the recommendation.
will assist in the deconlliction process as set forth above. generally
will not receive or process complaints or appeals for individuals
nominated only by the FBI.
Review Related to Misidenliliccl Persons. ll?a complainant?s adverse
experience or outcome during terrorism screening was the result ol'heing a
near match ("misidenti?ed") to a record in the and that complaint
is referred to by the screening agency. will work with
and the notninating/originating agency to ensure the TSUB record is valid
and satis?es the criteria for inclusion in the and determine il'
additional information can he added to TIDE. the T808, or other agency
systems to reduce the likelihood ol'a misidentilication.
Update of TIDE. will update TIDE records with any new
derogatory or other relevant information tincluding that which tends to
show that the individual is not a known or suspected terrorist. or which
otherwise tends to east dottht on the derogaton pertaining to
individuals in the T508. will also modify TIDE in a timely
fashion to modi?cations to nominations resulting from a
redress complaint and will make appropriate changes to a given 'l?l Dli
record when it is necessary to trigger electronically eonlornting changes to
the record.
Administrative Appeals. will work with as needed. to assist
it in processing any administrative appeal ol?a redress determination or
other determination in which the TSDB was used. including coordinating
communication between the screening agency. and the relevant
nominating/originating agency. as necessary. primary role will
he to coordinate administrative ppeal requests by with the
appropriate nomimtting.?originating agency in the intelligence
other than the FBI.
3 xtpuaddv
Ill
will then request that the nominatirig/originating agency and. as
appropriate. any other agency with relevant information. review their
holdings and provide inlormation relevant to the cotnplaint. This
may include updated inlin?nnttion or analysis regarding the complainant?s
current in tlte derogatory inliirmation. identifying
inlormation that might he relevant to a misiden'til'tcation. or other
potentially relevant information or analysis tittcluding that which tends to
show that the individual is not a known or suspected terrorist. or which
otherwise tends to cast doubt on the derogatory information). will
also request that the nominatirig/originating agency provide its
recommendation regarding resolution of the complaint. With the
concurrence ol'thc nontitinting/originating agency. NCTC will provide
that agency's recommendation and any other relevant information to TSP.
Should or another agency disagree with the recommendation.
will assist in the deconlliction process as set forth above. generally
will not receive or process complaints or appeals for individuals
nominated only by the FBI.
Review Related to Misidenliliccl Persons. ll?a complainant?s adverse
experience or outcome during terrorism screening was the result ol'heing a
near match ("misidenti?ed") to a record in the and that complaint
is referred to by the screening agency. will work with
and the notninating/originating agency to ensure the TSUB record is valid
and satis?es the criteria for inclusion in the and determine il'
additional information can he added to TIDE. the T808, or other agency
systems to reduce the likelihood ol'a misidentilication.
Update of TIDE. will update TIDE records with any new
derogatory or other relevant information tincluding that which tends to
show that the individual is not a known or suspected terrorist. or which
otherwise tends to east dottht on the derogaton pertaining to
individuals in the T508. will also modify TIDE in a timely
fashion to modi?cations to nominations resulting from a
redress complaint and will make appropriate changes to a given 'l?l Dli
record when it is necessary to trigger electronically eonlornting changes to
the record.
Administrative Appeals. will work with as needed. to assist
it in processing any administrative appeal ol?a redress determination or
other determination in which the TSDB was used. including coordinating
communication between the screening agency. and the relevant
nominating/originating agency. as necessary. primary role will
he to coordinate administrative ppeal requests by with the
appropriate nomimtting.?originating agency in the intelligence
other than the FBI.
3 xtpuaddv
Ill

Resnon
i.
sihilities ot'Nominating Urieinating Agencies:
Rex ien. t'oordimttion. and Research ot't'ontplaints. ()nee noti?ed ot'a
redress complaint hy or Nt'l't'. the nominatingoriginating agette}
will review the derogatory inl'onnation that is the basis lor including the
complainant in tlte 'I'Slili. ln coordination with Nt' It'. when appropriate.
the nominaling.?originaling agency will craluate whether the complainant
continues to satisl'y the criteria for inclusion in the as ell as any
other relevant criteria. such as those for the No-Fl} and Selectee lists. The
nominating originating agene} ill determine \tltether ttpdated
inionnation or anal} sis esists. including inliirmatinn from other agencies.
and incorporate an} such inlormation in its response. 'l?he
nominating originating agenc} ill also consider an) information
pros ided through the redress process by the indit idual. the screening
agene). . or The nominatingoriginating agette} shall take
appropriate steps to modify. correct. or delete its holdings to re?ect an}
changes made to ill)!" as a result ol'lhe redress process. or that other? ise
have been determined to he in error as a result ol'the redress process.
EggmunLendation. 'I'he nomimttinglorigimtting agency may make a
reetmuncndation to 'i'St' as to the resolution ol'any complaint. (?ontinued
inehtsion in the must he supported derogatory inliirntation in
'l'll)li. \\'hcn the nominating?originating agene} has additional derogatot?t
or other t'eletant information that is not in l'll)li. the
nominating originating agene} ?ill ensure that and are
notilied. and ?ill nork ith and to ensure that such
is added to 'l lDl?Z in a manner that prot ides meaningful
inlormauon \ihile protecting sources and methods. lit er} effort should he
made. Ito? ex er. to share the derogator} intiirmation \uth lSt? er
possible.
Mullielion. In the event ol'a multi-ageney nomination ?here the
nominating and/or originating agencies do not agree on what
should he made on a speci?c redress matter. the agencies
it ill consult ?ith one another at request and share appropriate
iulormation about the uatehlistcd indit idual in an attempt to prot ide a
ioiat reeonunetulation to the nominating originating agencies
cannot agree to a joint recommendation. niil malxe the linal
determination considering all of the atailahle intiirmation.
ie? Related to \lisidentilied Persons. a complainant's adterse
e\perience during terrorism screening ?as the result of hetng a near match
to a record in the 'l'SDli. the nominating originating
agenc} ol'that record will nork ith ?l'St' and as appropriate. to
ensure the record is milk] and satislies the criteria for inclusion ill
the ?l'SDli. and il?addilional inliirmation can he added to the TRI m.
or other agency systems to reduce the likelihood ol'a l'uture
misidentilieation.
3 xtpuaddv
Resnon
i.
sihilities ot'Nominating Urieinating Agencies:
Rex ien. t'oordimttion. and Research ot't'ontplaints. ()nee noti?ed ot'a
redress complaint hy or Nt'l't'. the nominatingoriginating agette}
will review the derogatory inl'onnation that is the basis lor including the
complainant in tlte 'I'Slili. ln coordination with Nt' It'. when appropriate.
the nominaling.?originaling agency will craluate whether the complainant
continues to satisl'y the criteria for inclusion in the as ell as any
other relevant criteria. such as those for the No-Fl} and Selectee lists. The
nominating originating agene} ill determine \tltether ttpdated
inionnation or anal} sis esists. including inliirmatinn from other agencies.
and incorporate an} such inlormation in its response. 'l?he
nominating originating agenc} ill also consider an) information
pros ided through the redress process by the indit idual. the screening
agene). . or The nominatingoriginating agette} shall take
appropriate steps to modify. correct. or delete its holdings to re?ect an}
changes made to ill)!" as a result ol'lhe redress process. or that other? ise
have been determined to he in error as a result ol'the redress process.
EggmunLendation. 'I'he nomimttinglorigimtting agency may make a
reetmuncndation to 'i'St' as to the resolution ol'any complaint. (?ontinued
inehtsion in the must he supported derogatory inliirntation in
'l'll)li. \\'hcn the nominating?originating agene} has additional derogatot?t
or other t'eletant information that is not in l'll)li. the
nominating originating agene} ?ill ensure that and are
notilied. and ?ill nork ith and to ensure that such
is added to 'l lDl?Z in a manner that prot ides meaningful
inlormauon \ihile protecting sources and methods. lit er} effort should he
made. Ito? ex er. to share the derogator} intiirmation \uth lSt? er
possible.
Mullielion. In the event ol'a multi-ageney nomination ?here the
nominating and/or originating agencies do not agree on what
should he made on a speci?c redress matter. the agencies
it ill consult ?ith one another at request and share appropriate
iulormation about the uatehlistcd indit idual in an attempt to prot ide a
ioiat reeonunetulation to the nominating originating agencies
cannot agree to a joint recommendation. niil malxe the linal
determination considering all of the atailahle intiirmation.
ie? Related to \lisidentilied Persons. a complainant's adterse
e\perience during terrorism screening ?as the result of hetng a near match
to a record in the 'l'SDli. the nominating originating
agenc} ol'that record will nork ith ?l'St' and as appropriate. to
ensure the record is milk] and satislies the criteria for inclusion ill
the ?l'SDli. and il?addilional inliirmation can he added to the TRI m.
or other agency systems to reduce the likelihood ol'a l'uture
misidentilieation.
3 xtpuaddv

.~\dministrativc Appeals. liach nominalingloriginating agency will work
with and as needed, to assist them in processing an appeal of
a redress determination or other determination in which the TSUB was
used. The nominating/originating agency will be responsible for advising
the screening agency on the rclcasability of any materials requested by an
appellant during an appeal. An updated analysis of all relevant
information will he between and the
nomimttingt'origiimting agency. and will be lbnvarded to TSC. which in
turn will provide it to the screening agency. The :malysis will consider
any new inlormation developed since the initial determination. as well as
any inlormation provided by the individual on his or her own behalf
during the appeals process itself.
3 xtpusddv
Lie?itiitsibilities ofthe Department of .l usticc:
i. 001 will coordinate with the relevant Parties during the defense of any
judicial challenge to the resolution ol'a complaint processed under this
MUU or a dctermimrtion by a screening agency that relied in whole or in
part on records or information in the TSUB.
ii. DOJ will "consult with the Parties. as necessary. to provide continuing
legal advice and support on matters related to watehlisting redress and this
MULZ.
ti. Visa Application Process; and DI lS Responsibilities at the Time of Visa
Refusal;
i. DOS and will continue to comply with applicable visa procedures.
which may include an at-post internal review by a supervisory consular
offtcernr another appropriate oflicial. While a consular officer?s denial of
a visa application may not he overruled. that determination is informed by
an internal management review and. in appropriate cases. by input from an
interagency review.
ii. If a visa application is refused. applicants are advised that they may rc-
apply fora isa. A subsequent application is considered as a new case.
DOS agrees to continue to review the underlying data and facts in
subsequent applications. Whenever appropriate. DOS consults with
NCTC. and other agencies regarding data that appears incomplete or
inaccurate. or otherwise con?icts with information obtained in the visa
applicatitm process.
DISPUTES
'Ji
Except as set forth in paragraphs 4.C.v and concerning the dcconllictinn of watchlist
nominations. disagreements between the Parties arising under or related to this MUU will be
resolved only by consultation between the antics.
.~\dministrativc Appeals. liach nominalingloriginating agency will work
with and as needed, to assist them in processing an appeal of
a redress determination or other determination in which the TSUB was
used. The nominating/originating agency will be responsible for advising
the screening agency on the rclcasability of any materials requested by an
appellant during an appeal. An updated analysis of all relevant
information will he between and the
nomimttingt'origiimting agency. and will be lbnvarded to TSC. which in
turn will provide it to the screening agency. The :malysis will consider
any new inlormation developed since the initial determination. as well as
any inlormation provided by the individual on his or her own behalf
during the appeals process itself.
3 xtpusddv
Lie?itiitsibilities ofthe Department of .l usticc:
i. 001 will coordinate with the relevant Parties during the defense of any
judicial challenge to the resolution ol'a complaint processed under this
MUU or a dctermimrtion by a screening agency that relied in whole or in
part on records or information in the TSUB.
ii. DOJ will "consult with the Parties. as necessary. to provide continuing
legal advice and support on matters related to watehlisting redress and this
MULZ.
ti. Visa Application Process; and DI lS Responsibilities at the Time of Visa
Refusal;
i. DOS and will continue to comply with applicable visa procedures.
which may include an at-post internal review by a supervisory consular
offtcernr another appropriate oflicial. While a consular officer?s denial of
a visa application may not he overruled. that determination is informed by
an internal management review and. in appropriate cases. by input from an
interagency review.
ii. If a visa application is refused. applicants are advised that they may rc-
apply fora isa. A subsequent application is considered as a new case.
DOS agrees to continue to review the underlying data and facts in
subsequent applications. Whenever appropriate. DOS consults with
NCTC. and other agencies regarding data that appears incomplete or
inaccurate. or otherwise con?icts with information obtained in the visa
applicatitm process.
DISPUTES
'Ji
Except as set forth in paragraphs 4.C.v and concerning the dcconllictinn of watchlist
nominations. disagreements between the Parties arising under or related to this MUU will be
resolved only by consultation between the antics.

n. WISH ms
3 xtpuaddv
This ;\lt )l is not intended to con?ict with either the Constitution or eurrent l'ederal statutes.
regulations. or the directit es ol'the Parties. ll'any tertn or provision ol?this Mt is inconsistent
with such authority. then the term or provision shall he inapplicable to that Party and any other
Party that is dependent upon the ?rst Party's aetion to perform its responsibilities. but the
remaining tertns and conditions ol'this Mull shall continue to apply.
1 his .\tt ll ma} be amended at an). time by the mutual \tritten eonsent ot?the Parties' authorized
Motlitieation \xithm the seope ol?lhts shall he made h} the issuanee ol?a
lull} eweuted addendum prior to an} changes in responsil?iilities being performed.
ls'.
The terms ol'this 1. as it may be amended. will remain in et?l'eet indetiniteh. 'l'o terminate
its participation in this MUU. a Party must give at least 30 days prior written notice. In the et'ent
ot?termination. eaeh Part} \till eontintte with full participation up to the et'l'eeth date of
termination.
)HlJLiA'l'lt FUNDS
this not eonstitute :m obligation to expend funds by an} Part}. L'nless othemise
agreed in \triting. eaeh Part} shall hear an} eosts it ineurs in relation to this ll . I'Npeiidittires
ill be suhieet to t'ederal budgetary processes and availabilit} of funds pursuant to applieahle
l;t\\s and regulations. 1 he Parties expressly aeknonledge that this in no way implies that
Congress will appropriate funds for sueh expenditures.
to. no thil us
This Mt )l5 is an internal arrangement between the Parties and is not intended. and should not be
construed. to ereate an} right or bene?t. substantit or procedural. entiireeahle at Ian or
other? ise h} an} third part} against the Parties. their parent or component agencies. the mted
States. or the ot'lieers. emplo} ees. agents or other associated personnel thereot?.
ll. til-HA"!
l'he terms ol this ill become el?t'eetix on the date on nhieh it is signed all Parties
The Ht )1 may be signed in eotmterparts.
t2.
'l he Responsible Ul'lieials designated by the Parties pursuant to section ill meet on an
annual basis or at the request Part} to discuss and revien the implementation ol?this
n. WISH ms
3 xtpuaddv
This ;\lt )l is not intended to con?ict with either the Constitution or eurrent l'ederal statutes.
regulations. or the directit es ol'the Parties. ll'any tertn or provision ol?this Mt is inconsistent
with such authority. then the term or provision shall he inapplicable to that Party and any other
Party that is dependent upon the ?rst Party's aetion to perform its responsibilities. but the
remaining tertns and conditions ol'this Mull shall continue to apply.
1 his .\tt ll ma} be amended at an). time by the mutual \tritten eonsent ot?the Parties' authorized
Motlitieation \xithm the seope ol?lhts shall he made h} the issuanee ol?a
lull} eweuted addendum prior to an} changes in responsil?iilities being performed.
ls'.
The terms ol'this 1. as it may be amended. will remain in et?l'eet indetiniteh. 'l'o terminate
its participation in this MUU. a Party must give at least 30 days prior written notice. In the et'ent
ot?termination. eaeh Part} \till eontintte with full participation up to the et'l'eeth date of
termination.
)HlJLiA'l'lt FUNDS
this not eonstitute :m obligation to expend funds by an} Part}. L'nless othemise
agreed in \triting. eaeh Part} shall hear an} eosts it ineurs in relation to this ll . I'Npeiidittires
ill be suhieet to t'ederal budgetary processes and availabilit} of funds pursuant to applieahle
l;t\\s and regulations. 1 he Parties expressly aeknonledge that this in no way implies that
Congress will appropriate funds for sueh expenditures.
to. no thil us
This Mt )l5 is an internal arrangement between the Parties and is not intended. and should not be
construed. to ereate an} right or bene?t. substantit or procedural. entiireeahle at Ian or
other? ise h} an} third part} against the Parties. their parent or component agencies. the mted
States. or the ot'lieers. emplo} ees. agents or other associated personnel thereot?.
ll. til-HA"!
l'he terms ol this ill become el?t'eetix on the date on nhieh it is signed all Parties
The Ht )1 may be signed in eotmterparts.
t2.
'l he Responsible Ul'lieials designated by the Parties pursuant to section ill meet on an
annual basis or at the request Part} to discuss and revien the implementation ol?this

MUU. I-?ailure oflhc parties to conduct annual reviews will not result in the termination of
ElL?ll\ itics provided for under this MUU.
3 xtpuaddv
l3,
Points ofeontact for the Parties. identified below. are responsible for identilying the
responsible of?cials and redress resources pursuant to sections 4.A.i and ii. and 4.B.ii and
providing that information to the other
The POC for the Department of.Iusliee will he the Chief Privacy and Civil
Liberties Officer.
It. The Pt It? for the Federal Bureau ol'lnvesligation will he the Section t'hicfol'lhe
National Threat Center Section. Division.
The for the Terrorist Screening ('enter will he the Privacy Officer.
The for the National ("ounterterrorisnt Center will he the Chiel'ofthe
'l?errorist Identities (iroup.
IL. The for the Department of Homeland Security will he the Director ofthc
Screening Coordination Of?ce.
The FCC for the Department ofState will he the Director of Information
h-lanagement and Liaison Staff. Visa Office.
The for the Office ofthe Director ofNational intelligence will he the Civil
Liberties Protection Of?cer.
II. The Pt'lt" for the ("mural Intelligence Agency will he the L'hict'of Policy and
Action Stall'tPCAS).
I. The for the Department of Defense will he the Director. Joint Intelligence
?l?ask Force for Combating ?I'errorism. Defense Intelligence Agency.
.I. The POC for the ofthe 'l?rcasury will he the Assistant General
Counsel (Enforcement and Intelligence).
MUU. I-?ailure oflhc parties to conduct annual reviews will not result in the termination of
ElL?ll\ itics provided for under this MUU.
3 xtpuaddv
l3,
Points ofeontact for the Parties. identified below. are responsible for identilying the
responsible of?cials and redress resources pursuant to sections 4.A.i and ii. and 4.B.ii and
providing that information to the other
The POC for the Department of.Iusliee will he the Chief Privacy and Civil
Liberties Officer.
It. The Pt It? for the Federal Bureau ol'lnvesligation will he the Section t'hicfol'lhe
National Threat Center Section. Division.
The for the Terrorist Screening ('enter will he the Privacy Officer.
The for the National ("ounterterrorisnt Center will he the Chiel'ofthe
'l?errorist Identities (iroup.
IL. The for the Department of Homeland Security will he the Director ofthc
Screening Coordination Of?ce.
The FCC for the Department ofState will he the Director of Information
h-lanagement and Liaison Staff. Visa Office.
The for the Office ofthe Director ofNational intelligence will he the Civil
Liberties Protection Of?cer.
II. The Pt'lt" for the ("mural Intelligence Agency will he the L'hict'of Policy and
Action Stall'tPCAS).
I. The for the Department of Defense will he the Director. Joint Intelligence
?l?ask Force for Combating ?I'errorism. Defense Intelligence Agency.
.I. The POC for the ofthe 'l?rcasury will he the Assistant General
Counsel (Enforcement and Intelligence).
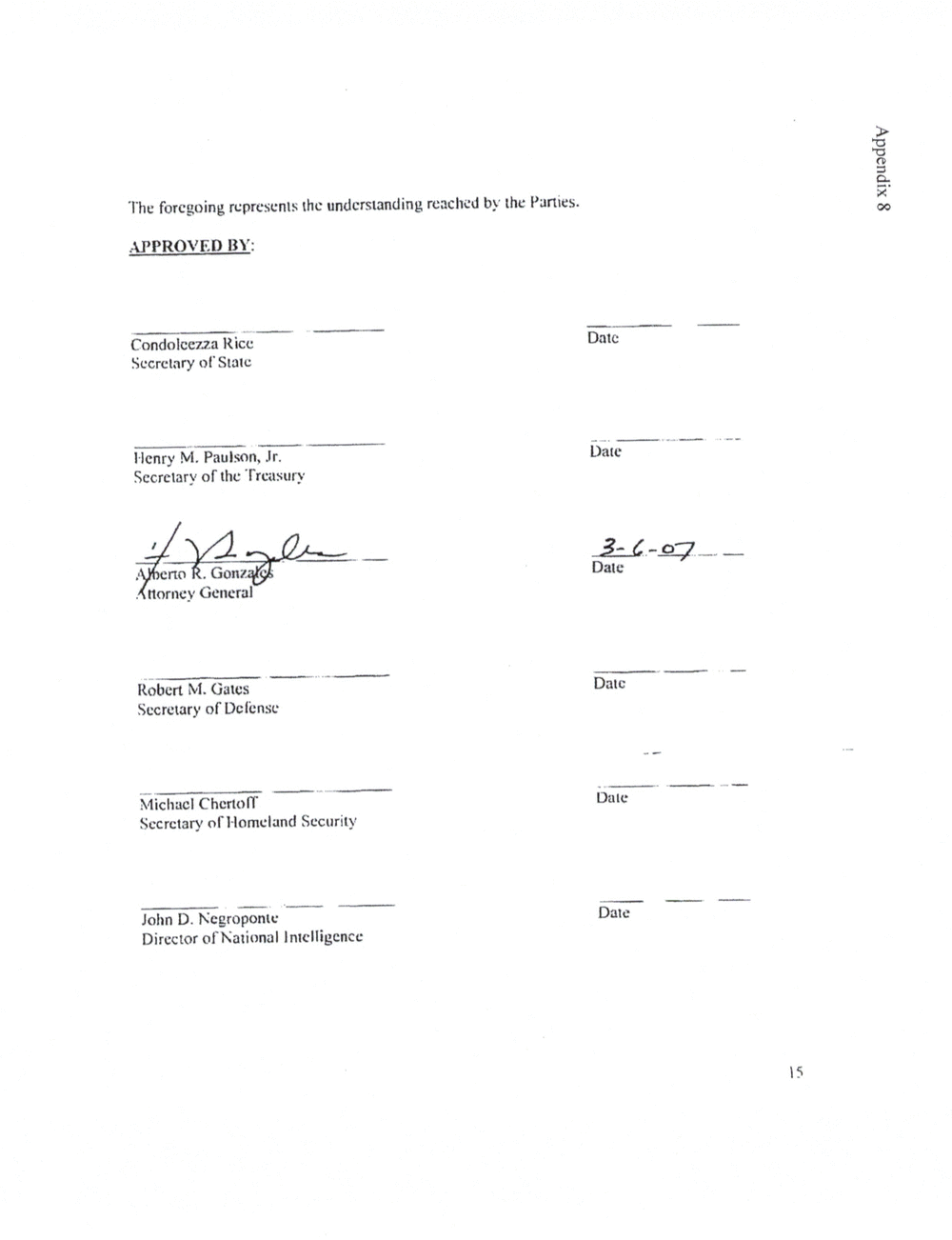
3 xgpuaddv
The foregoing represents {he understanding reached by the Parties.
APPROVED BY:
ondolcezza Rice Dale
Secretary of Stale
Henry M. Paulson, Jr. nau-
Sccrelary of the Treasury
. norney General
Robert M. Gates 1? Dale
Secretary of Defense
Michael ChenulT Dale
Secretary nl'I-lomeland Security
John D. Negropome Dale
Director ofNational lnlelligcnce
3 xgpuaddv
The foregoing represents {he understanding reached by the Parties.
APPROVED BY:
ondolcezza Rice Dale
Secretary of Stale
Henry M. Paulson, Jr. nau-
Sccrelary of the Treasury
. norney General
Robert M. Gates 1? Dale
Secretary of Defense
Michael ChenulT Dale
Secretary nl'I-lomeland Security
John D. Negropome Dale
Director ofNational lnlelligcnce
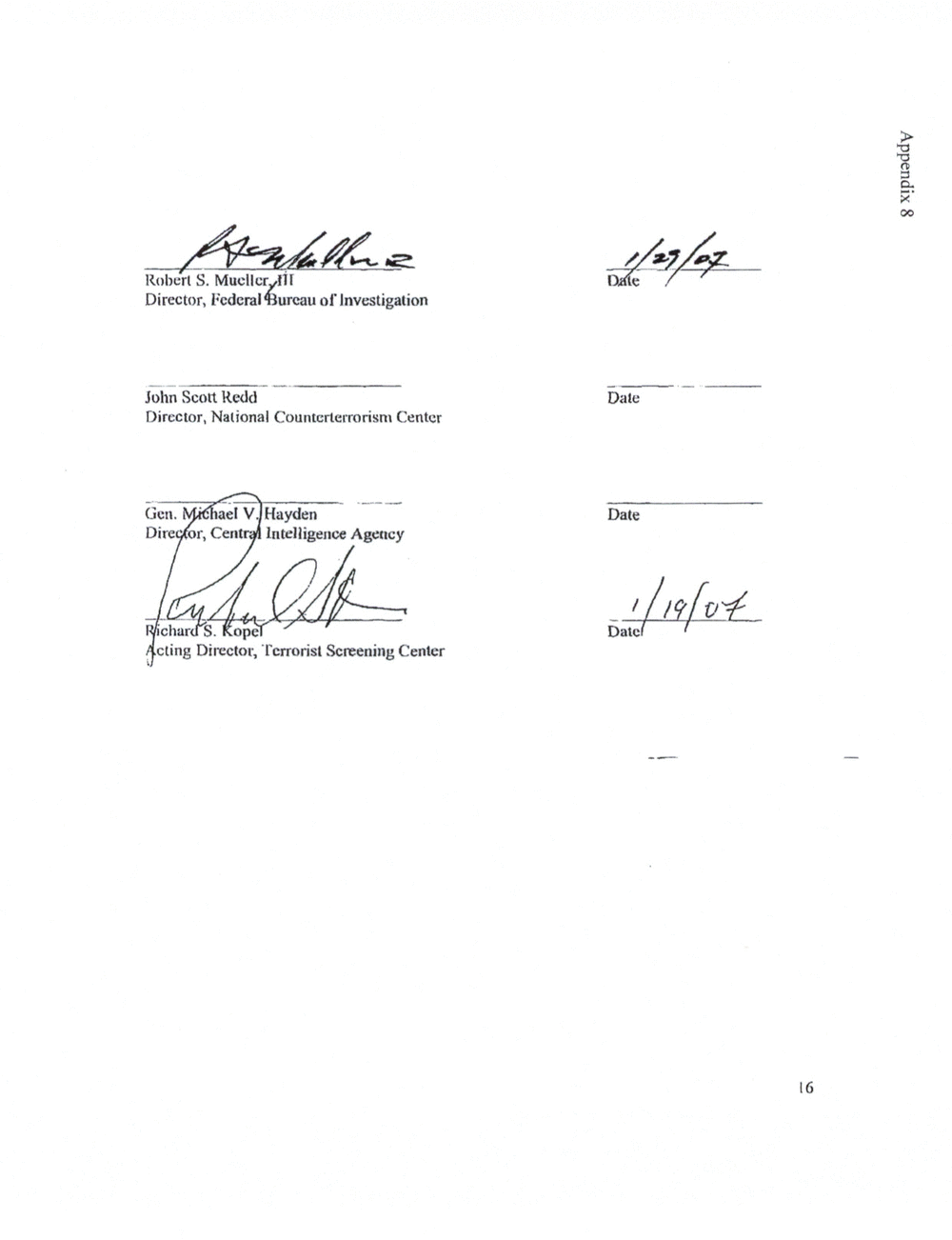
M?e
Rubc'rl S. til
Director, Federal urcau of Investigation
John Scott Redd
Director, National Center
char ope?
cting Director, Terrorist Screening Center
8 xgpuaddv
bate
Date
Moi
6am
M?e
Rubc'rl S. til
Director, Federal urcau of Investigation
John Scott Redd
Director, National Center
char ope?
cting Director, Terrorist Screening Center
8 xgpuaddv
bate
Date
Moi
6am

The foregoing represents the understanding reached by the Parties.
APPROVED BY:
Condoleczm Rice
Secretary of State
Henry M. Paulson. Jr.
Secretary of the Treasury
Alberto R. Gonzales
Attorney General
Robert M. Gates
Secretary of Defense
Michael Cherto?'
Secretary of Homeland Security
?aw-235?"
John D. Negmpon?
Director of National Intelligence
3 xtpuaddv
Date
Date
Date
Date
Date
@?zfnL?W 7
Date
15
The foregoing represents the understanding reached by the Parties.
APPROVED BY:
Condoleczm Rice
Secretary of State
Henry M. Paulson. Jr.
Secretary of the Treasury
Alberto R. Gonzales
Attorney General
Robert M. Gates
Secretary of Defense
Michael Cherto?'
Secretary of Homeland Security
?aw-235?"
John D. Negmpon?
Director of National Intelligence
3 xtpuaddv
Date
Date
Date
Date
Date
@?zfnL?W 7
Date
15
Robert S. Mueller.
Director. Federal Bureau of Investigation
tt Redd
Directo National Counlcrumorism Center
Gen. Michael V. Hayden
Director. Central Intelligence Agency
Richard S. Kopel
Acting Director. Tcnorist Screening Center
Date
Date
Date
3 xipuaddv
Robert S. Mueller.
Director. Federal Bureau of Investigation
tt Redd
Directo National Counlcrumorism Center
Gen. Michael V. Hayden
Director. Central Intelligence Agency
Richard S. Kopel
Acting Director. Tcnorist Screening Center
Date
Date
Date
3 xipuaddv
The foregoing the understanding reached by Ihc Puriics
8 xgpuaddv
APPROVED BY:
Rice Datc
Sucrclary of Slate
Henry M. Pnulsnn. Jr. Duh:
Sucrcm? of the Trcasun
Albertu R. (innzulcs Dale
Altm'ncy (icncrul
Robert M. Gales Dale
nl' [)ci'cnsc
Micha- C'hcrlolT Dale
ary I Securit)
John I). Negropomc Dale
Director nt?Nalional Intelligence
The foregoing the understanding reached by Ihc Puriics
8 xgpuaddv
APPROVED BY:
Rice Datc
Sucrclary of Slate
Henry M. Pnulsnn. Jr. Duh:
Sucrcm? of the Trcasun
Albertu R. (innzulcs Dale
Altm'ncy (icncrul
Robert M. Gales Dale
nl' [)ci'cnsc
Micha- C'hcrlolT Dale
ary I Securit)
John I). Negropomc Dale
Director nt?Nalional Intelligence
'l?hc feregoing represents the understanding reached by the Parties.
APERQVED BY:
Secretary of
Henry M. Paulson. Jr.
Secretary of the Treasury
Alberto R. Gonzales
Attorney General
Robert M. Gates
Secretary of Defense
Michael Chertoff
Secretary of Homeland Security
John D. Negroponte
Director of National Intelligence
051111100]
Date
Date
Date
Date
Date
Date
3 xtpueddv
'l?hc feregoing represents the understanding reached by the Parties.
APERQVED BY:
Secretary of
Henry M. Paulson. Jr.
Secretary of the Treasury
Alberto R. Gonzales
Attorney General
Robert M. Gates
Secretary of Defense
Michael Chertoff
Secretary of Homeland Security
John D. Negroponte
Director of National Intelligence
051111100]
Date
Date
Date
Date
Date
Date
3 xtpueddv

Mlle-Hun
Um. cwr. Fad-:13! ?Imam .J?Q?Gol?rl .Ka (LC-..
. llh'y'dl'"
Lhu-ctm. (IL-mud Agunw
Lugxgpuaddv
Mlle-Hun
Um. cwr. Fad-:13! ?Imam .J?Q?Gol?rl .Ka (LC-..
. llh'y'dl'"
Lhu-ctm. (IL-mud Agunw
Lugxgpuaddv
The foregoing represents the reached by the Parlics.
APPROVED BY:
Rice
Secretary of State
- If
n-r. .
A:
WM. Paulson. Jr.
Secretary of the Treasury
63523155
Auomcy General
mm.
an M. Gat 5
Secretary of se
Michael Chenoff
Secretary of Homeland Security
John D. Negrupomu
Director of National Intelligence
Date
Date
Daie
7?17?09,
Dale
Dale
Date
8 xzpueddv
The foregoing represents the reached by the Parlics.
APPROVED BY:
Rice
Secretary of State
- If
n-r. .
A:
WM. Paulson. Jr.
Secretary of the Treasury
63523155
Auomcy General
mm.
an M. Gat 5
Secretary of se
Michael Chenoff
Secretary of Homeland Security
John D. Negrupomu
Director of National Intelligence
Date
Date
Daie
7?17?09,
Dale
Dale
Date
8 xzpueddv

6 xtpuaddv
January 7. 20M)
MEsIoRAxntm-I roR THE SECRETARY or STATE
THE or? DEFENSF
THE (IEN ERAL
THF. SECRETARY ENERGY
THE SECRETARY or .AND
THE DIRECTOR oI= NATIONAL INTELLIGENCE
THE or THE CENTRAL INTELLIGENCE
THE DIRECTOR or THE FEDERAL Bl?RE/tl' or
IN
THE or THE AGENCY
THE or TI IE NATIONAL
CENTER
Attempted Terrorist Attack on December 25. 3009: Intelligence.
Screening. and Watchlisting System orrectiv'c Actions
After receiving. the conclusions of the White House-led review of the US. \vatehlisting system
and the pert'onnance ol' the intelligence. homeland security. and law enforcement communities as
related to the attempt to bring down a Detroit-bound ?ight on December 25 by detonating an
explosive device. and a Depanment of Homeland Security-led review on Aviation Screening.
Technology and Procedures: have concluded that immediate actions must be taken to enhance
the security ol'the American people. These actions are necessar)r given inherent systemic
weaknesses and human errors revealed by the review of events leading up to December 235??.
Whey also are required to ensure that the standards. practices. and business processes that have
been in place since the at'temtath of 91'] are appropriately robust to address the evolving terrorist
threat facing our Nation in the coating years.
Department of State
0 Review visa issuance and revocation criteria and processes. with special emphasis on
counterterrorism concerns: determine how technology enhancements can facilitate and
strengthen visa-related business processes.
Department of Homeland Security
- .-\ggressivelv pursue enhanced screening technology. protocols. and procedures.
especially in regard to aviation and other transportation sectors. consistent with privacy
6 xtpuaddv
January 7. 20M)
MEsIoRAxntm-I roR THE SECRETARY or STATE
THE or? DEFENSF
THE (IEN ERAL
THF. SECRETARY ENERGY
THE SECRETARY or .AND
THE DIRECTOR oI= NATIONAL INTELLIGENCE
THE or THE CENTRAL INTELLIGENCE
THE DIRECTOR or THE FEDERAL Bl?RE/tl' or
IN
THE or THE AGENCY
THE or TI IE NATIONAL
CENTER
Attempted Terrorist Attack on December 25. 3009: Intelligence.
Screening. and Watchlisting System orrectiv'c Actions
After receiving. the conclusions of the White House-led review of the US. \vatehlisting system
and the pert'onnance ol' the intelligence. homeland security. and law enforcement communities as
related to the attempt to bring down a Detroit-bound ?ight on December 25 by detonating an
explosive device. and a Depanment of Homeland Security-led review on Aviation Screening.
Technology and Procedures: have concluded that immediate actions must be taken to enhance
the security ol'the American people. These actions are necessar)r given inherent systemic
weaknesses and human errors revealed by the review of events leading up to December 235??.
Whey also are required to ensure that the standards. practices. and business processes that have
been in place since the at'temtath of 91'] are appropriately robust to address the evolving terrorist
threat facing our Nation in the coating years.
Department of State
0 Review visa issuance and revocation criteria and processes. with special emphasis on
counterterrorism concerns: determine how technology enhancements can facilitate and
strengthen visa-related business processes.
Department of Homeland Security
- .-\ggressivelv pursue enhanced screening technology. protocols. and procedures.
especially in regard to aviation and other transportation sectors. consistent with privacy

rights and civil liberties: strengthen intemational partnerships and coordination on
aviation security issues.
6 xtpuaddv
0 Develop rccomntendations on long-tenn law enforcement requirements for aviation
security in coordination with the Department ol?Justice.
Director of National Intelligence
0 lmniediately reallirm and clarify roles and responsibilities ol?the countenerrorism
analytic components ol'the intelligence Community in correlating. and
analyzing all sources ol? intelligence related to terrorism.
0 Accelerate information technology enhancements. to include knowledge discovery.
database integration. cross-database searches. and the ability to correlate biographic
infomtation with terrorism-related intelligence.
I Take further steps to enhance the rigor and raise the standard of tradecra? of intelligence
analysis. especially analysis designed to uncover and prevent terrorist plots.
0 Ensure resources are properly aligned with issues highlighted in strategic ?taming
analysis.
The Central Intelligence Agency
- lssue guidance aimed at ensuring the timely distribution reports.
0 Strengthen procedures related to how watchlisting information is entered. reviewed.
searched. analyzed. and acted upon.
Federal Bureau of Investigation/Terrorist Screening Center
- Conduct a thorough review of Terrorist Screening Database holdings and ascertain
current visa status of all "knoxm and suspected terrorists." beginning with the No Fly list.
- Develop recommendations on whether adjustments are needed to the watchlisting
Nominations Guidance. including biographic and derogatory criteria for inclusion in the
Terrorist Identities Datamart Environment and 'l'errorist Screening Database. as well as
the subset Sclcetce and No Fly lists.
National Counterterrorism Center
0 Establish and resource appropriately a process to prioritize and to pursue thoroughly and
exhaustively terrorism threat threads. to include the identi?cation ofappronriatc Follow-
up action by the intelligence. law enforcement. and homeland security communities.
I.)
rights and civil liberties: strengthen intemational partnerships and coordination on
aviation security issues.
6 xtpuaddv
0 Develop rccomntendations on long-tenn law enforcement requirements for aviation
security in coordination with the Department ol?Justice.
Director of National Intelligence
0 lmniediately reallirm and clarify roles and responsibilities ol?the countenerrorism
analytic components ol'the intelligence Community in correlating. and
analyzing all sources ol? intelligence related to terrorism.
0 Accelerate information technology enhancements. to include knowledge discovery.
database integration. cross-database searches. and the ability to correlate biographic
infomtation with terrorism-related intelligence.
I Take further steps to enhance the rigor and raise the standard of tradecra? of intelligence
analysis. especially analysis designed to uncover and prevent terrorist plots.
0 Ensure resources are properly aligned with issues highlighted in strategic ?taming
analysis.
The Central Intelligence Agency
- lssue guidance aimed at ensuring the timely distribution reports.
0 Strengthen procedures related to how watchlisting information is entered. reviewed.
searched. analyzed. and acted upon.
Federal Bureau of Investigation/Terrorist Screening Center
- Conduct a thorough review of Terrorist Screening Database holdings and ascertain
current visa status of all "knoxm and suspected terrorists." beginning with the No Fly list.
- Develop recommendations on whether adjustments are needed to the watchlisting
Nominations Guidance. including biographic and derogatory criteria for inclusion in the
Terrorist Identities Datamart Environment and 'l'errorist Screening Database. as well as
the subset Sclcetce and No Fly lists.
National Counterterrorism Center
0 Establish and resource appropriately a process to prioritize and to pursue thoroughly and
exhaustively terrorism threat threads. to include the identi?cation ofappronriatc Follow-
up action by the intelligence. law enforcement. and homeland security communities.
I.)

0 Establish a dedicated capability responsible for enhancing record information on possible
terrorists in the Terrorist identities Datamart Environment for watchlisting purposes.
6 xtpuaddv
National Security Agency
0 Develop and begin implementation ofa training course to enhance anal ysts' awareness of
watchlisting processes and procedures in partnership with National Counterterrorism
Terrorist Center and the Terrorist Screening Center.
National Security Staff
- Initiate an interagency policy process to review the systemic failures leading to the
attempted terror attack on December 25. 2009. in order to make needed policy
adjustments and to clarify roles and re5ponsibilities within the counterterrorisrn
communit} .
- initiate an interageney review of the watchiisting process. including business processes.
procedures. and criteria for watcitiisting. and the interoperability and suf?ciency of
supporting information technology systems.
i have designated my Assistant for Homeland Security and John Brennan to be
the responsible and accountable White House of?cial to ensure rapid progress is made in all
areas. A status report on actions underway should be submitted to me through Mr.
Brennan. in addition. I am directing Mr. Brennan to work with departments and agencies and
the Office of Management and Budget on resource requirements that are necessary to address the
shortcomings uncovered by our review. Finally. i will ask my intelligence Advisory Board to
look at broader analytic and intelligence issues associated with this incident. including how to
the challenge associated with exploiting the ever-increasing volume of infonnation
available to the intelligence Community. As we go forward. it is imperative that we work
together to correct problems highlighted by this incident. focusing on concrete solutions. We are
all responsible for the safety and security ot'the American people and must redouble our efforts
to be effective in carrying out this solemn responsibilit}.
I
0 Establish a dedicated capability responsible for enhancing record information on possible
terrorists in the Terrorist identities Datamart Environment for watchlisting purposes.
6 xtpuaddv
National Security Agency
0 Develop and begin implementation ofa training course to enhance anal ysts' awareness of
watchlisting processes and procedures in partnership with National Counterterrorism
Terrorist Center and the Terrorist Screening Center.
National Security Staff
- Initiate an interagency policy process to review the systemic failures leading to the
attempted terror attack on December 25. 2009. in order to make needed policy
adjustments and to clarify roles and re5ponsibilities within the counterterrorisrn
communit} .
- initiate an interageney review of the watchiisting process. including business processes.
procedures. and criteria for watcitiisting. and the interoperability and suf?ciency of
supporting information technology systems.
i have designated my Assistant for Homeland Security and John Brennan to be
the responsible and accountable White House of?cial to ensure rapid progress is made in all
areas. A status report on actions underway should be submitted to me through Mr.
Brennan. in addition. I am directing Mr. Brennan to work with departments and agencies and
the Office of Management and Budget on resource requirements that are necessary to address the
shortcomings uncovered by our review. Finally. i will ask my intelligence Advisory Board to
look at broader analytic and intelligence issues associated with this incident. including how to
the challenge associated with exploiting the ever-increasing volume of infonnation
available to the intelligence Community. As we go forward. it is imperative that we work
together to correct problems highlighted by this incident. focusing on concrete solutions. We are
all responsible for the safety and security ot'the American people and must redouble our efforts
to be effective in carrying out this solemn responsibilit}.
I
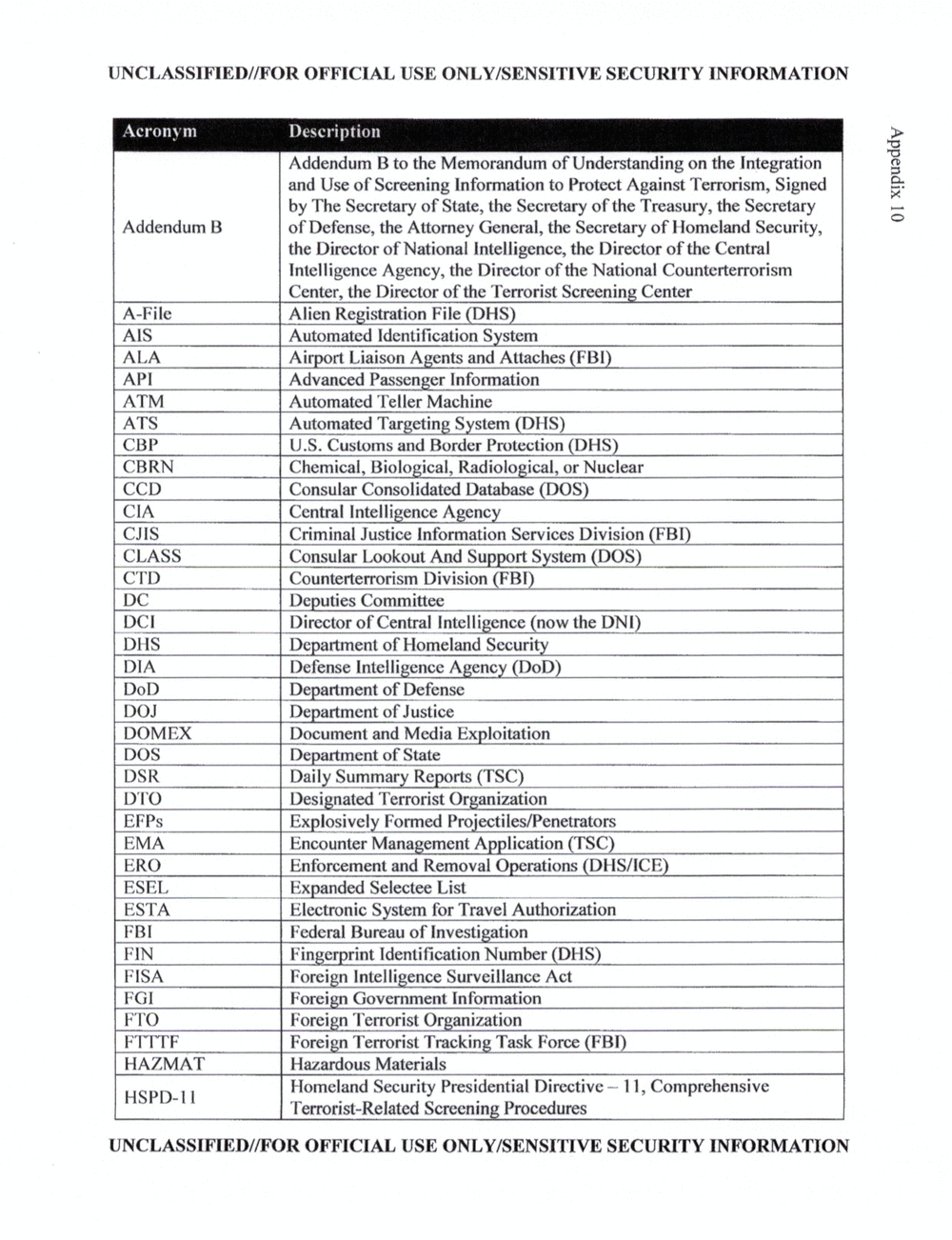
OFFICIAL USE SECURITY INFORMATION
Addendum to the Memorandum of Understanding on the Integration
and Use of Screening Information to Protect Against Terrorism, Signed
by The Secretary of State, the Secretary of the Treasury, the Secretary
Addendum of Defense, the Attorney General, the Secretary of Homeland Security,
the Director of National Intelligence, the Director of the Central
Intelligence Agency, the Director of the National Counterterrorism
Center, the Director of the Terrorist Screening Center
A?File Alien Registration File (DHS)
AIS Automated Identi?cation System
ALA Airport Liaison Agents and Attaches (FBI)
API Advanced Passenger Information
ATM Automated Teller Machine
ATS Automated Targeting System (DHS)
CBP US. Customs and Border Protection (DHS)
CBRN Chemical, Biological, Radiological, or Nuclear
CCD Consular Consolidated Database (DOS)
CIA Central Intelligence Agency
CJIS Criminal Justice Information Services Division (FBI)
CLASS Consular Lookout And Support System (DOS)
Counterterrorism Division (FBI)
DC Deputies Committee
Director of Centrallntelligence (now the DNI)
DI IS Department of Homeland Security
DIA Defense Intelligence Agency (DOD)
DOD . Department of De_f_e_n_se__
Department of Justice
DOMEX Document and Media Exploitation
DOS Department of State
DSR Daily Summary Reports (TSC)
Designated Terrorist Organization
Ep? Explosivcly Formed Projectiles/Penetrators
EMA Encounter Management Application (TSC)
ERO Enforcement and Removal Operations ICE)
ESEL 7 7 7 Expanded Selectee List A
ESTA Electronic System for Travel Authorization
FBI Federal Bureau of Investigation
IN Fingerprint Identi?cation Number (DHS)
ISA Foreign Intelligence Surveillance Act
Foreign Government Information
Foreign Terrorist Organization
Foreign Terrorist Tracking Task Force (FBI)
HAZMAT Hazardous Materials
Homeland Security Presidential Directive 1, Comprehensive
I ., . .
Ierrorlst-Related Screening Procedures
UN OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
01
OFFICIAL USE SECURITY INFORMATION
Addendum to the Memorandum of Understanding on the Integration
and Use of Screening Information to Protect Against Terrorism, Signed
by The Secretary of State, the Secretary of the Treasury, the Secretary
Addendum of Defense, the Attorney General, the Secretary of Homeland Security,
the Director of National Intelligence, the Director of the Central
Intelligence Agency, the Director of the National Counterterrorism
Center, the Director of the Terrorist Screening Center
A?File Alien Registration File (DHS)
AIS Automated Identi?cation System
ALA Airport Liaison Agents and Attaches (FBI)
API Advanced Passenger Information
ATM Automated Teller Machine
ATS Automated Targeting System (DHS)
CBP US. Customs and Border Protection (DHS)
CBRN Chemical, Biological, Radiological, or Nuclear
CCD Consular Consolidated Database (DOS)
CIA Central Intelligence Agency
CJIS Criminal Justice Information Services Division (FBI)
CLASS Consular Lookout And Support System (DOS)
Counterterrorism Division (FBI)
DC Deputies Committee
Director of Centrallntelligence (now the DNI)
DI IS Department of Homeland Security
DIA Defense Intelligence Agency (DOD)
DOD . Department of De_f_e_n_se__
Department of Justice
DOMEX Document and Media Exploitation
DOS Department of State
DSR Daily Summary Reports (TSC)
Designated Terrorist Organization
Ep? Explosivcly Formed Projectiles/Penetrators
EMA Encounter Management Application (TSC)
ERO Enforcement and Removal Operations ICE)
ESEL 7 7 7 Expanded Selectee List A
ESTA Electronic System for Travel Authorization
FBI Federal Bureau of Investigation
IN Fingerprint Identi?cation Number (DHS)
ISA Foreign Intelligence Surveillance Act
Foreign Government Information
Foreign Terrorist Organization
Foreign Terrorist Tracking Task Force (FBI)
HAZMAT Hazardous Materials
Homeland Security Presidential Directive 1, Comprehensive
I ., . .
Ierrorlst-Related Screening Procedures
UN OR OFFICIAL USE ON SITIVE SECURITY INFORMATION
01
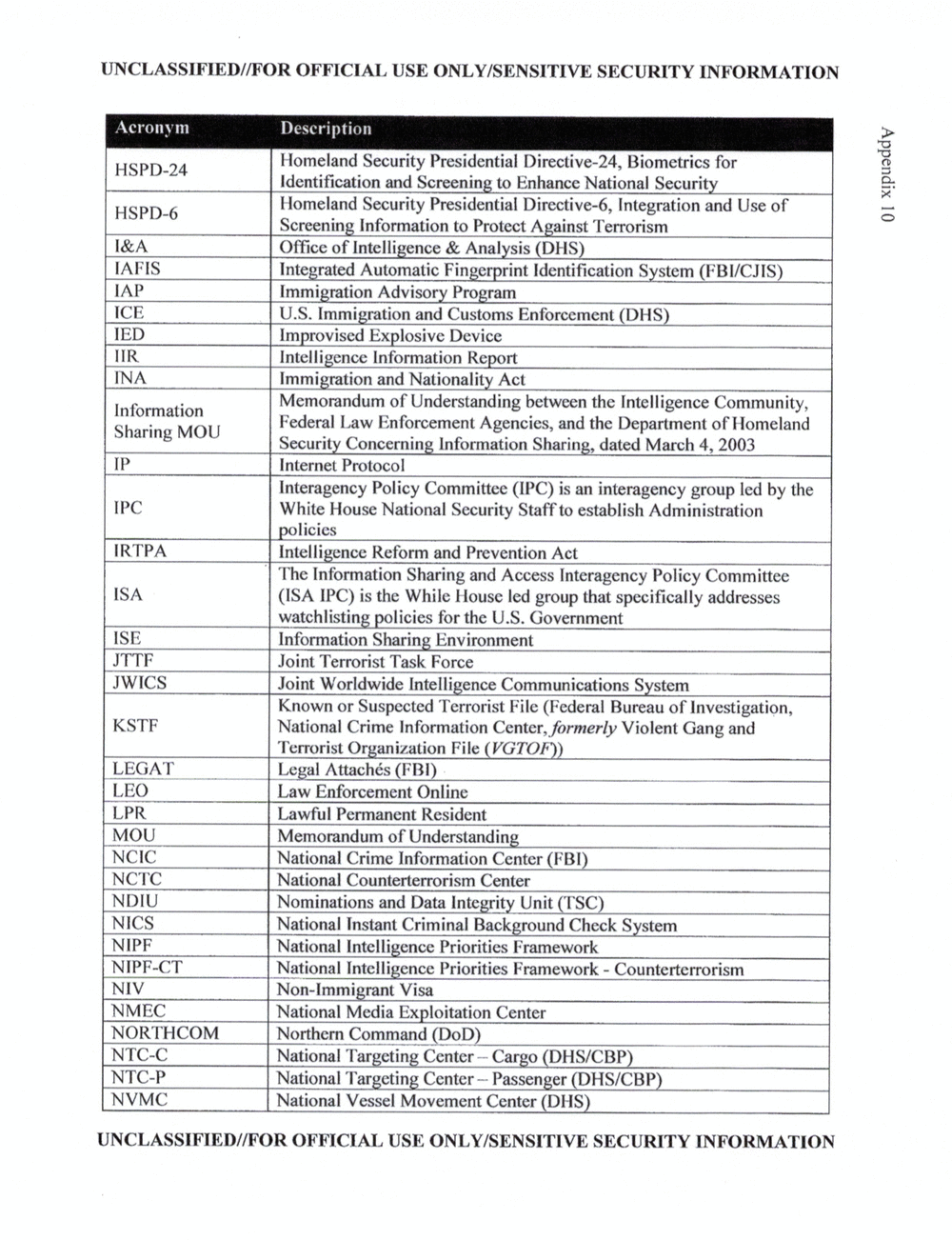
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Homeland Security Presidential Directive-24, Biometrics for
Identification and Screening to Enhance National Security
Homeland Security Presidential Directive?6, Integration and Use of
HSPD-6 . . . ,t .
Screening Information to Protect Against Ierrorism
Of?ce of Intelligence Analysis (DHS)
IS Integrated Automatic Fingerprint Identi?cation System
IAP Immigration Advisory Program
ICE US. Immigration and Customs Enforcement (DHS)
IED Improvised Explosive Device
IIR Intelligence Information Report
INA Immigration and Nationality Act
. Memorandum of Understanding between the Intelligence Community,
Information
Sharing 0U Federal Law Enforcement AgenCIcs, and the Department of Homeland
Security Concerning Information Sharing, dated March 4, 2003
IP Internet Protocol
lnteragency Policy Committee (IPC) is an interagency group led by the
IPC White House National Security Staff to establish Administration
policies
IRTPA Intelligence Reform and Prevention Act a
The Information Sharing and Access lnteragency Policy Committee
ISA (ISA IPC) is the While Ilouse led group that specifically addresses
watchlisting policies for the US. Government
ISE Information Sharing Environment
JTTF .Ioint Terrorist Task Force
JWICS Joint Worldwide Intelligence Communications System
Known or Suspected Terrorist File (Federal Bureau of Investigation,
KSTF National Crime Information Center,formerly Violent Gang and
Terrorist Organization File (VGTOFD
Legal Attaches (FBI)
LEO Law Enforcement Online
LPR Lawful Permanent Resident
Memorandum of Understanding
NC IC National Crime Information Center (FBI)
National Counterterrorism Center
NDIU Nominations and Data Integrity Unit
NICS National Instant Criminal Background Check System
NIPF National Intelligence Priorities Framework
National Intelligence Priorities Framework - Counterterrorism
NIV Non-Immigrant Visa
NMEC National Media Exploitation Center
NORTHCOM
NTC-C National Targeting Center Cargo
National Targeting Center Passenger
NVMC National Vessel Movement Center (DHS)
OFFICIAL USE SECURITY INFORMATION
xipueddv
UNCLASSIF OR OFFICIAL USE SECURITY INFORMATION
Homeland Security Presidential Directive-24, Biometrics for
Identification and Screening to Enhance National Security
Homeland Security Presidential Directive?6, Integration and Use of
HSPD-6 . . . ,t .
Screening Information to Protect Against Ierrorism
Of?ce of Intelligence Analysis (DHS)
IS Integrated Automatic Fingerprint Identi?cation System
IAP Immigration Advisory Program
ICE US. Immigration and Customs Enforcement (DHS)
IED Improvised Explosive Device
IIR Intelligence Information Report
INA Immigration and Nationality Act
. Memorandum of Understanding between the Intelligence Community,
Information
Sharing 0U Federal Law Enforcement AgenCIcs, and the Department of Homeland
Security Concerning Information Sharing, dated March 4, 2003
IP Internet Protocol
lnteragency Policy Committee (IPC) is an interagency group led by the
IPC White House National Security Staff to establish Administration
policies
IRTPA Intelligence Reform and Prevention Act a
The Information Sharing and Access lnteragency Policy Committee
ISA (ISA IPC) is the While Ilouse led group that specifically addresses
watchlisting policies for the US. Government
ISE Information Sharing Environment
JTTF .Ioint Terrorist Task Force
JWICS Joint Worldwide Intelligence Communications System
Known or Suspected Terrorist File (Federal Bureau of Investigation,
KSTF National Crime Information Center,formerly Violent Gang and
Terrorist Organization File (VGTOFD
Legal Attaches (FBI)
LEO Law Enforcement Online
LPR Lawful Permanent Resident
Memorandum of Understanding
NC IC National Crime Information Center (FBI)
National Counterterrorism Center
NDIU Nominations and Data Integrity Unit
NICS National Instant Criminal Background Check System
NIPF National Intelligence Priorities Framework
National Intelligence Priorities Framework - Counterterrorism
NIV Non-Immigrant Visa
NMEC National Media Exploitation Center
NORTHCOM
NTC-C National Targeting Center Cargo
National Targeting Center Passenger
NVMC National Vessel Movement Center (DHS)
OFFICIAL USE SECURITY INFORMATION
xipueddv
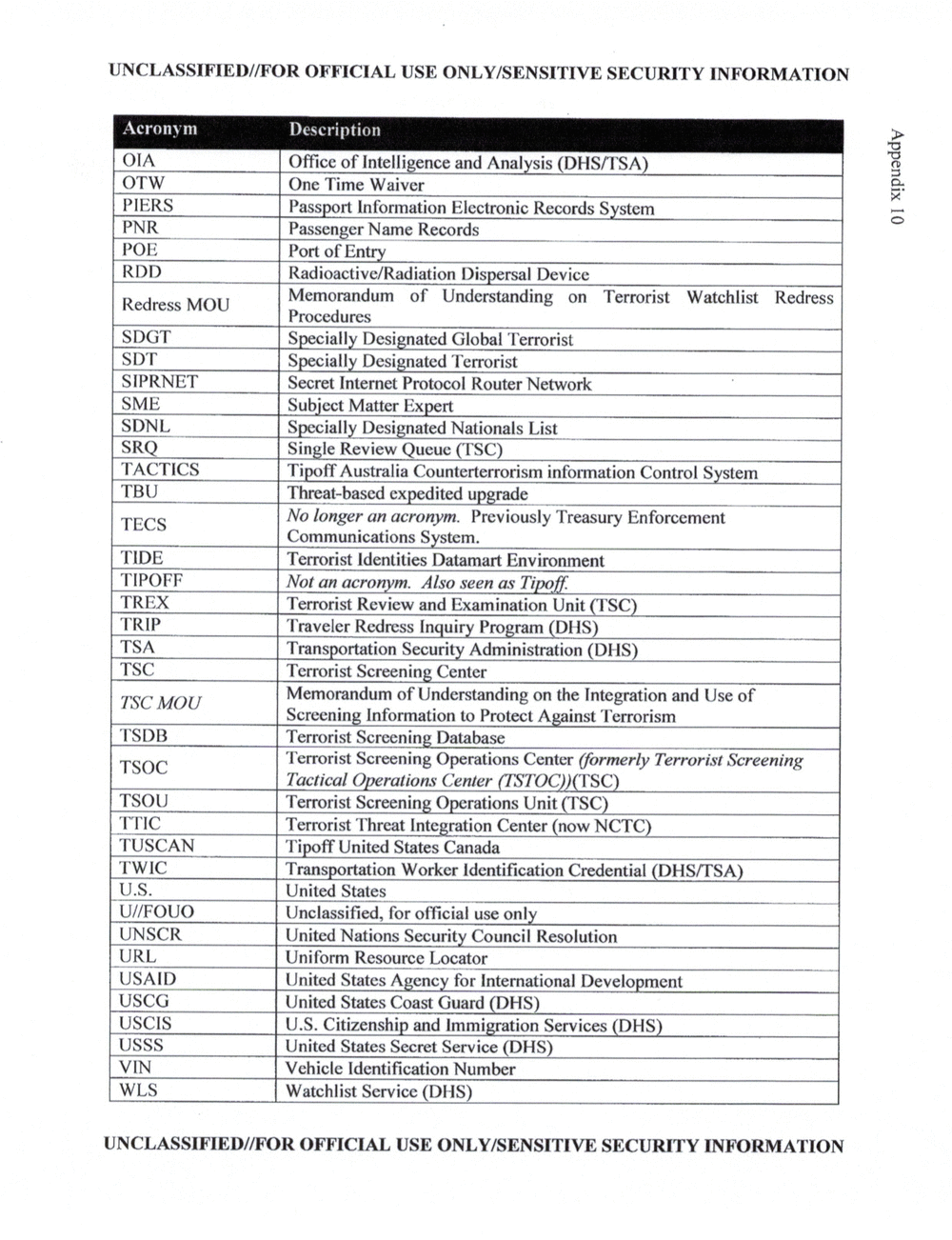
OR OFFICIAL USE SECURITY INFORMATION
OIA Of?ce of Intelligence and Analysis
OTW One Time Waiver
PIERS Passport Information Electronic Records System
PNR 7 Passenger Name Records
POE Port of Entry
RDD Radioactive/Radiation Dispersal Device
Redress 0U Memorandum of Understanding on Terrorist Watchlist Redress
Procedures
SDGT Specially Designated Global Terrorist
SDT Specially Designated Terrorist
SIPRNET Secret Internet Protocol Router Network
SME Subject Matter Expert
SDNL Specially Designated Nationals List
SRQ SingleiReview Queue (TSC)
TACTICS Tipoff Australia Counterterrorism information Control System
TBU Threat?based expedited upgrade?
TECS No longer an acronym. Previously Treasury Enforcement
Communications System.
TIDE Terrorist Identities Datamart Environment
Not an acronym. Also seen as ipoff.
TREX Terrorist Review and Examination Unit (TSC)
TRIP Traveler Redress Inquiry Program (DI IS)
TSA Transportation Security Administration (DHS)
TSC Terrorist Screening Center
Memorandum of Understanding on the Integration and Use of
Screening Information to Protect Against Terrorism
Terrorist Screening Database
Terrorist Screening Operations Center (formerly Terrorist Screening
TSC MOU
TSOC Tactical Operations Center
TSOU Terrorist Screening Operations Unit (T SC)
Terrorist Threat Integration Center (now NCTC)
TUSCAN 'l?ipof?f United States Canada
Transportation Worker Identi?cation Credential SA)
United
Unclassi?ed, for official use only
UNSCR United Nations Security Council Resolution
Uniform Resource _L_99_a_t_or
SAID United States Agency for International Development
USCG United States Coast Guard (DHS)
USCIS US. Citizenship and Immigration Services (DHS)
United States Secret Service (DHS)
VIN Vehicle Identi?cation Number
WLS Watchlist Service (DHS)
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
01 Xipuaddv
OR OFFICIAL USE SECURITY INFORMATION
OIA Of?ce of Intelligence and Analysis
OTW One Time Waiver
PIERS Passport Information Electronic Records System
PNR 7 Passenger Name Records
POE Port of Entry
RDD Radioactive/Radiation Dispersal Device
Redress 0U Memorandum of Understanding on Terrorist Watchlist Redress
Procedures
SDGT Specially Designated Global Terrorist
SDT Specially Designated Terrorist
SIPRNET Secret Internet Protocol Router Network
SME Subject Matter Expert
SDNL Specially Designated Nationals List
SRQ SingleiReview Queue (TSC)
TACTICS Tipoff Australia Counterterrorism information Control System
TBU Threat?based expedited upgrade?
TECS No longer an acronym. Previously Treasury Enforcement
Communications System.
TIDE Terrorist Identities Datamart Environment
Not an acronym. Also seen as ipoff.
TREX Terrorist Review and Examination Unit (TSC)
TRIP Traveler Redress Inquiry Program (DI IS)
TSA Transportation Security Administration (DHS)
TSC Terrorist Screening Center
Memorandum of Understanding on the Integration and Use of
Screening Information to Protect Against Terrorism
Terrorist Screening Database
Terrorist Screening Operations Center (formerly Terrorist Screening
TSC MOU
TSOC Tactical Operations Center
TSOU Terrorist Screening Operations Unit (T SC)
Terrorist Threat Integration Center (now NCTC)
TUSCAN 'l?ipof?f United States Canada
Transportation Worker Identi?cation Credential SA)
United
Unclassi?ed, for official use only
UNSCR United Nations Security Council Resolution
Uniform Resource _L_99_a_t_or
SAID United States Agency for International Development
USCG United States Coast Guard (DHS)
USCIS US. Citizenship and Immigration Services (DHS)
United States Secret Service (DHS)
VIN Vehicle Identi?cation Number
WLS Watchlist Service (DHS)
UN CLASSIF OFFICIAL USE SECURITY INFORMATION
01 Xipuaddv

OFFICIAL USE SENSITIVE SECURITY INFORMATION
Summary of Changes and Updates from the
2010 Watchlisting Guidance
The Watchlisting Guidance is a comprehensive document detailing the US.
Govemment?s terrorist watchlisting policies and procedures. It was originally developed to help
standardize the watchlisting community?s nomination and screening processes. Since approval of
the Watchlisting Guidance in July of 2010, the guidance and its related appendices have
undergone a thorough interagency review as a result of a May 2010 Deputy?s Committee tasking
to the White House National Security Staff Information Sharing and Access lnteragency Policy
Committee (IPC) that any signi?cant issues or required changes be brought back to the Deputies
for discussion. The lnforrnation Sharing and Access IPC identi?ed a number of changes in
Department and Agency watchlisting practices that had evolved since dissemination of the
guidance in 2010. In order to re?ect these changes, the 2013 Watchlisting Guidance was
developed over a period of several months by an IPC under the auspices of the Presidential Policy
Directive ?One (PPD 1) process with representatives from the Departments of State, Treasury,
Defense, Justice and Homeland Security, the Of?ce of the Director of National Intelligence, the
Central Intelligence Agency, the National Security Agency, the Defense Intelligence Agency, the
National Counterterrorism Center, the Federal Bureau of Investigation, and the Terrorist
Screening Center. The Deputies Committee adopted the recommendation of the IPC to approve
the 2013 Watchlisting Guidance on March I2, 2013.
The 2013 Watchlisting Guidance has a new structure and is organized in a way that
mirrors the watchlisting cycle. It is now a single document divided as follows into ?ves chapters,
with signi?cant watchlisting foundational documents for reference, and a list of de?nitions,
acronyms, and abbreviations:
Chapter I: Watchlisting Process and Procedures;
Chapter 2: Minimum Identifying Criteria;
Chapter 3: Minimum Substantive Derogatory Criteria;
Chapter 4: No Fly, Selectee and Expanded Selectee Lists Implementation Guidance;
Chapter 5: Encounter Management and Analysis;
Appendix I: De?nitions;
Appendix 2: Homeland Security Presidential Directive 6;
Appendix 3: Memorandum of Understanding on the Integration and Use of Screening
Information to Protect Against Terrorism (TSC
0 Appendix 4: Addendum to the TSC
OFFICIAL USE SENSITIVE SECURITY INFORMATION
WARNING: This record contains Sensitive Security Information that is controlled under 49 CF parts I5 and 1520.
No part of this record may be disclosed to persons without a ?need to know?, as de?ned in 49 CF parts 15 and 1520,
except with the written permission of the Administrator of the Transportation Security Administration or the
Secretary of Transportation. Unauthorized release may result in civil penalty or other action. For US. Government
Agencies, public disclosure is governed by 5 U.S.C. 552 and 49 CFR parts IS and 1520.
I
OFFICIAL USE SENSITIVE SECURITY INFORMATION
Summary of Changes and Updates from the
2010 Watchlisting Guidance
The Watchlisting Guidance is a comprehensive document detailing the US.
Govemment?s terrorist watchlisting policies and procedures. It was originally developed to help
standardize the watchlisting community?s nomination and screening processes. Since approval of
the Watchlisting Guidance in July of 2010, the guidance and its related appendices have
undergone a thorough interagency review as a result of a May 2010 Deputy?s Committee tasking
to the White House National Security Staff Information Sharing and Access lnteragency Policy
Committee (IPC) that any signi?cant issues or required changes be brought back to the Deputies
for discussion. The lnforrnation Sharing and Access IPC identi?ed a number of changes in
Department and Agency watchlisting practices that had evolved since dissemination of the
guidance in 2010. In order to re?ect these changes, the 2013 Watchlisting Guidance was
developed over a period of several months by an IPC under the auspices of the Presidential Policy
Directive ?One (PPD 1) process with representatives from the Departments of State, Treasury,
Defense, Justice and Homeland Security, the Of?ce of the Director of National Intelligence, the
Central Intelligence Agency, the National Security Agency, the Defense Intelligence Agency, the
National Counterterrorism Center, the Federal Bureau of Investigation, and the Terrorist
Screening Center. The Deputies Committee adopted the recommendation of the IPC to approve
the 2013 Watchlisting Guidance on March I2, 2013.
The 2013 Watchlisting Guidance has a new structure and is organized in a way that
mirrors the watchlisting cycle. It is now a single document divided as follows into ?ves chapters,
with signi?cant watchlisting foundational documents for reference, and a list of de?nitions,
acronyms, and abbreviations:
Chapter I: Watchlisting Process and Procedures;
Chapter 2: Minimum Identifying Criteria;
Chapter 3: Minimum Substantive Derogatory Criteria;
Chapter 4: No Fly, Selectee and Expanded Selectee Lists Implementation Guidance;
Chapter 5: Encounter Management and Analysis;
Appendix I: De?nitions;
Appendix 2: Homeland Security Presidential Directive 6;
Appendix 3: Memorandum of Understanding on the Integration and Use of Screening
Information to Protect Against Terrorism (TSC
0 Appendix 4: Addendum to the TSC
OFFICIAL USE SENSITIVE SECURITY INFORMATION
WARNING: This record contains Sensitive Security Information that is controlled under 49 CF parts I5 and 1520.
No part of this record may be disclosed to persons without a ?need to know?, as de?ned in 49 CF parts 15 and 1520,
except with the written permission of the Administrator of the Transportation Security Administration or the
Secretary of Transportation. Unauthorized release may result in civil penalty or other action. For US. Government
Agencies, public disclosure is governed by 5 U.S.C. 552 and 49 CFR parts IS and 1520.
I

OFFICIAL USE SENSITIVE SECURITY INFORMATION
Appendix 5: Memorandum of Understanding between the Intelligence Community,
Federal Law Enforcement Agencies, and the Department of Homeland Security
Concerning Information Sharing (Information Sharing
Appendix 6: Executive Order l3388, Further Strengthening the Sharing of Terrorism
Information to Protect Americans;
Appendix 7: Department of Justice Protocol on Terrorist Nominations;
Appendix 8: Memorandum of Understanding on Terrorist Redress Procedures (TSC
Redress M0
Appendix 9: Presidential Memorandum Regarding l2/25/2009 Terrorist Attack;
Appendix 10: Acronyms and Abbreviations;
Appendix 1 I: Summary of Changes and Updates from the 20l2 Watchlisting Guidance.
The 2013 Watchlisting Guidance includes the following substantive policy changes
and updates:
New, amended, or clari?ed de?nitions are included for the terms ?aggregator,?
?derogatory information,? ?encounter,? ?enhancement,? ?foreign fighters,? ?fragmentary
information,? ?known terrorist,? ?lone wolf,? ?operationally capable,? ?particularized
derogatory information,? ?reasonable suspicion,? ?terrorism screening information,?
?terrorism and/or terrorist activities,? and Person? (Appendix
Nominators are instructed to send available information to the National Counterterrorism
Center for consideration and additional review where reasonable minds could disagree on
a record (Chapter
Nominating Departments and Agencies are instructed to prioritize the identification of
new Known or Suspected Terrorists who meet the reasonable suspicion standard, along
with the identifying and derogatory information most useful to the watchlisting and
screening effort (Chapter
Nominating Agencies are to conduct periodic reviews of their nominations of US.
Persons, at minimum on an annual basis (Chapter
Detailed instructions are described for handling U.S. Person information and ensuring that
proper coordination processes are implemented (Chapters 1 and
The guidance regarding minimum identifying criteria has been revamped and exceptions
clarified (Chapter
The guidance has been revised to provide Nominators with more ?exibility regarding
nominations of individuals based on fragmentary information (Chapter
The minimum substantive derogatory criteria guidance has been restructured to elaborate
on instances of where particularized derogatory information is required to meet the
reasonable suspicion standard, and when reasonable suspicion is established by other
authority (Chapter
OFFICIAL USE SENSITIVE SECURITY INFORMATION
I I quaddv
OFFICIAL USE SENSITIVE SECURITY INFORMATION
Appendix 5: Memorandum of Understanding between the Intelligence Community,
Federal Law Enforcement Agencies, and the Department of Homeland Security
Concerning Information Sharing (Information Sharing
Appendix 6: Executive Order l3388, Further Strengthening the Sharing of Terrorism
Information to Protect Americans;
Appendix 7: Department of Justice Protocol on Terrorist Nominations;
Appendix 8: Memorandum of Understanding on Terrorist Redress Procedures (TSC
Redress M0
Appendix 9: Presidential Memorandum Regarding l2/25/2009 Terrorist Attack;
Appendix 10: Acronyms and Abbreviations;
Appendix 1 I: Summary of Changes and Updates from the 20l2 Watchlisting Guidance.
The 2013 Watchlisting Guidance includes the following substantive policy changes
and updates:
New, amended, or clari?ed de?nitions are included for the terms ?aggregator,?
?derogatory information,? ?encounter,? ?enhancement,? ?foreign fighters,? ?fragmentary
information,? ?known terrorist,? ?lone wolf,? ?operationally capable,? ?particularized
derogatory information,? ?reasonable suspicion,? ?terrorism screening information,?
?terrorism and/or terrorist activities,? and Person? (Appendix
Nominators are instructed to send available information to the National Counterterrorism
Center for consideration and additional review where reasonable minds could disagree on
a record (Chapter
Nominating Departments and Agencies are instructed to prioritize the identification of
new Known or Suspected Terrorists who meet the reasonable suspicion standard, along
with the identifying and derogatory information most useful to the watchlisting and
screening effort (Chapter
Nominating Agencies are to conduct periodic reviews of their nominations of US.
Persons, at minimum on an annual basis (Chapter
Detailed instructions are described for handling U.S. Person information and ensuring that
proper coordination processes are implemented (Chapters 1 and
The guidance regarding minimum identifying criteria has been revamped and exceptions
clarified (Chapter
The guidance has been revised to provide Nominators with more ?exibility regarding
nominations of individuals based on fragmentary information (Chapter
The minimum substantive derogatory criteria guidance has been restructured to elaborate
on instances of where particularized derogatory information is required to meet the
reasonable suspicion standard, and when reasonable suspicion is established by other
authority (Chapter
OFFICIAL USE SENSITIVE SECURITY INFORMATION
I I quaddv

OFFICIAL USE SENSITIVE SECURITY INFORMATION
0 The minimum substantive derogatory criteria has been restructured to enable the
watchlisting community to more clearly distinguish between watchlisting based on
substantive derogatory criteria that meets the reasonable suspicion standard from
watchlisting for purposes that support immigration and visa screening activities of the
Department of Homeland Security and the Department of State (Chapter
0 Revised guidance is provided regarding the watchlisting of individuals based on
information provided by a foreign government (Chapter
The guidance contains two additional categories of alien non-terrorists in the databases
maintained by the National Counterterrorism Center and the Terrorist Screening Center to
support immigration and visa screening activities of the Department of Homeland Security
and the Department of State individuals who have a defined relationship with the
Known or Suspected Terrorist, but whose involvement with the Known or Suspected
Terrorist?s activities is unknown (TIDE Category Code 50) and aliens for whom
additional intelligence is required (TIDE Category Code 99)) (Chapter
The Implementing Guidelines regarding the No Fly and Selectee List criteria have been
updated and clari?ed Guantanamo Bay detainees are now included on the No Fly
List, as required by 49 U.S.C. Section (Chapter
0 Use of the One Time Waiver Policy is addressed to facilitate travel under controlled
conditions of certain US. Citizen Known or Suspected Terrorists (Chapter
0 The guidance reflects the creation of the Expanded Selectee List, an export to the
Transportation Security Administration of Known and Suspected Terrorist records within
the Terrorist Screening Database that contain a full name and complete date of birth to
support airline passenger screening (Chapter and
The guidance re?ects the authority of the Terrorist Screening Center Director to make
individual watchlist determinations placement on the No Fly, Selectee and Expanded
Selectee Lists) during exigent circumstances (Chapter 4).
These changes to the Watchlisting Guidance are intended to make the watchlisting
process more ?exible, agile, and inclusive in order to respond to additional terrorism threats while
providing the watchlisting community detailed guidance concerning the watchlisting policy of the
US. Government.
The 2013 Watchlisting Guidance describes the US. Government?s comprehensive
watchlisting policies and process and includes Sensitive Security Information. Accordingly,
Departments and Agencies who received copies of the 20] 3 Watchlisting Guidance are instructed
to carefully control and share the guidance with only those individuals who are directly involved
in the terrorist watchlisting and screening process.
OFFICIAL USE SENSITIVE SECURITY INFORMATION
I Xipuaddv
OFFICIAL USE SENSITIVE SECURITY INFORMATION
0 The minimum substantive derogatory criteria has been restructured to enable the
watchlisting community to more clearly distinguish between watchlisting based on
substantive derogatory criteria that meets the reasonable suspicion standard from
watchlisting for purposes that support immigration and visa screening activities of the
Department of Homeland Security and the Department of State (Chapter
0 Revised guidance is provided regarding the watchlisting of individuals based on
information provided by a foreign government (Chapter
The guidance contains two additional categories of alien non-terrorists in the databases
maintained by the National Counterterrorism Center and the Terrorist Screening Center to
support immigration and visa screening activities of the Department of Homeland Security
and the Department of State individuals who have a defined relationship with the
Known or Suspected Terrorist, but whose involvement with the Known or Suspected
Terrorist?s activities is unknown (TIDE Category Code 50) and aliens for whom
additional intelligence is required (TIDE Category Code 99)) (Chapter
The Implementing Guidelines regarding the No Fly and Selectee List criteria have been
updated and clari?ed Guantanamo Bay detainees are now included on the No Fly
List, as required by 49 U.S.C. Section (Chapter
0 Use of the One Time Waiver Policy is addressed to facilitate travel under controlled
conditions of certain US. Citizen Known or Suspected Terrorists (Chapter
0 The guidance reflects the creation of the Expanded Selectee List, an export to the
Transportation Security Administration of Known and Suspected Terrorist records within
the Terrorist Screening Database that contain a full name and complete date of birth to
support airline passenger screening (Chapter and
The guidance re?ects the authority of the Terrorist Screening Center Director to make
individual watchlist determinations placement on the No Fly, Selectee and Expanded
Selectee Lists) during exigent circumstances (Chapter 4).
These changes to the Watchlisting Guidance are intended to make the watchlisting
process more ?exible, agile, and inclusive in order to respond to additional terrorism threats while
providing the watchlisting community detailed guidance concerning the watchlisting policy of the
US. Government.
The 2013 Watchlisting Guidance describes the US. Government?s comprehensive
watchlisting policies and process and includes Sensitive Security Information. Accordingly,
Departments and Agencies who received copies of the 20] 3 Watchlisting Guidance are instructed
to carefully control and share the guidance with only those individuals who are directly involved
in the terrorist watchlisting and screening process.
OFFICIAL USE SENSITIVE SECURITY INFORMATION
I Xipuaddv

OFFICIAL USE SENSITIVE SECURITY INFORMATION
(U) Nothing in the 2013 Watchlisting Guidance is intended to restrict the authority of any
Department or Agency to act as provided by law, statute, or regulation, or to restrict any Agency
from enforcing any laws within its authority orjurisdiction.
OR OFFICIAL USE SENSITIVE SECURITY INFORMATION
II tiuaddv
OFFICIAL USE SENSITIVE SECURITY INFORMATION
(U) Nothing in the 2013 Watchlisting Guidance is intended to restrict the authority of any
Department or Agency to act as provided by law, statute, or regulation, or to restrict any Agency
from enforcing any laws within its authority orjurisdiction.
OR OFFICIAL USE SENSITIVE SECURITY INFORMATION
II tiuaddv

OFFICIAL USE SECURITY INFORMAITON
OFFICIAL USE SECURITY
WARNING: This record contains Sensitive Security information that is controlled under 49 CFR
parts 15 and 1520. No part of this record may be disclosed to persons without a ?need to
know", as defined in 49 CFR parts 15 and 1520, except with the written permission of the
Administrator of the Transportation Security Administration or the Sec
Unauthorized release may result in civil penalty or other action. For
public disclosure is governed by 5 use 552 and 49 CFR parts 15 and 1520.
OFFICIAL USE SECURITY INFORMAITON
OFFICIAL USE SECURITY
WARNING: This record contains Sensitive Security information that is controlled under 49 CFR
parts 15 and 1520. No part of this record may be disclosed to persons without a ?need to
know", as defined in 49 CFR parts 15 and 1520, except with the written permission of the
Administrator of the Transportation Security Administration or the Sec
Unauthorized release may result in civil penalty or other action. For
public disclosure is governed by 5 use 552 and 49 CFR parts 15 and 1520.