Documents
Computer Network Exploitation Classification Guide
Oct. 10, 2014
TOP T0 USA, FVEY
(U) CLASSIFICATION GUIDE Computer Network Exploitation
(CNE) Classi?cation Guide 2-59
(U) PUBLICATION DATE: 1 March 2010
(U) OFFICE OF ORIGIN: Tailored Access Operations (T
(U) POC: TAO Classi?cation Advisory Of?cer
(U) PHONE:
ORIGINAL CLASSIFICATION AUTHORITY:
Description of Information I Classi?cation/Markings I Reason I Declass I Remarks
A. (U) GENERAL
1. (U) The fact that or UNCLASSIFIED (U) Details indicating
TAO performs computer speci?c targets, level of
network exploitation (CNE) success or capabilities remain
classi?ed.
2. The fact that TO USA, See 1.4(c) *25 years (U) Details indicating
or TAO, as part of FVEY speci?c targets, level of
CNE operations, performs success or capabilities may
remote subversion raise the classi?cation level
and/or require
compartrnentation.
(U) Foreign releasability
decisions on speci?c details
relating to remote subversion
are handled on a case-by-case
basis. Contact TAO CAO for
further guidance.
3. Identi?cation of TO USA, Sec 1.4(c) *25 years (U) Details indicating
speci?c remote subversion FVEY speci?c targets, level of
methods used by or success or capabilities may
TAO, to include: raise the classi?cation level
- Endpoint access, exploitation, and/or require
or operations compartmentation.
On?net access, exploitation, or
operations (U) Foreign releasability
- Software implant access, decisions on speci?c details
exploitation, or operations relating to remote subversion
- Accessing or exploiting data are handled on a case-by-case
at rest basis. Contact TAO CAO for
further guidance.
4. The fact that TO USA, Sec 1.4 *25 years (U) Details indicating
or TAO, as part of FVEY speci?c targets, level of
CNE operations, performs success or capabilities may
physical subversion, to include: raise the classi?cation and
TOP TO USA, FVEY
TOP T0 USA, FVEY
(U) CLASSIFICATION GUIDE Computer Network Exploitation
(CNE) Classi?cation Guide 2-59
(U) PUBLICATION DATE: 1 March 2010
(U) OFFICE OF ORIGIN: Tailored Access Operations (T
(U) POC: TAO Classi?cation Advisory Of?cer
(U) PHONE:
ORIGINAL CLASSIFICATION AUTHORITY:
Description of Information I Classi?cation/Markings I Reason I Declass I Remarks
A. (U) GENERAL
1. (U) The fact that or UNCLASSIFIED (U) Details indicating
TAO performs computer speci?c targets, level of
network exploitation (CNE) success or capabilities remain
classi?ed.
2. The fact that TO USA, See 1.4(c) *25 years (U) Details indicating
or TAO, as part of FVEY speci?c targets, level of
CNE operations, performs success or capabilities may
remote subversion raise the classi?cation level
and/or require
compartrnentation.
(U) Foreign releasability
decisions on speci?c details
relating to remote subversion
are handled on a case-by-case
basis. Contact TAO CAO for
further guidance.
3. Identi?cation of TO USA, Sec 1.4(c) *25 years (U) Details indicating
speci?c remote subversion FVEY speci?c targets, level of
methods used by or success or capabilities may
TAO, to include: raise the classi?cation level
- Endpoint access, exploitation, and/or require
or operations compartmentation.
On?net access, exploitation, or
operations (U) Foreign releasability
- Software implant access, decisions on speci?c details
exploitation, or operations relating to remote subversion
- Accessing or exploiting data are handled on a case-by-case
at rest basis. Contact TAO CAO for
further guidance.
4. The fact that TO USA, Sec 1.4 *25 years (U) Details indicating
or TAO, as part of FVEY speci?c targets, level of
CNE operations, performs success or capabilities may
physical subversion, to include: raise the classi?cation and
TOP TO USA, FVEY
To USA.
- Close access enabling. require protection.
exploitation. or operations
- Off-net enabling. exploitation. (U) Foreign releasability
or operations decisions on speci?c details
- Supply chain enabling. relating to physical
exploitation. or intervention subversion are handled on a
operations case-by-case basis. Contact
- Hardware implant enabling. TAO CAO for further
exploitationI or 9mm gui_da_nce.
S. (U) The association of any UNCLASSIFIEDIIFOR FOIA 3 NIA
speci?c ECI name or trigraph. OFFICIAL USE ONLY
with ECI. SIGINT.
or intelligence
6. (U) The association of a TO Sec. 1.4(c) NIA
speci?c TAO name or USA. FVEY
Mb with CNE ar_idlor TAO
7. (U) The fact that a speci?c UNCLASSIFIEIMFOR (U) If the details of the
individual is cleared for a OFFICIAL USE ONLY association reveal the fact
speci?c TAO ECI. when there that the ECI is TAO's. then it
is no msociation between the would be
BC I and TAO CONFIDENTIAUIREL T0
USA. FVEY. in accordance
with entry 5.
8. (U) The fact that NSAJCSS or UNCLASSIFIED NIA
TAO conducts CNE for foreign
intelligence collection.
9. (U) The fact that NSAJCSS or UNCLASSIFIED NIA (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. performs CN to success or capabilities remain
support US. Government CNA classi?ed.
efforts
IO. (U) The fact that or UNCLASSIFIED NIA (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. trains. equips. and success or capabilities remain
organizes the US. classi?ed.
System to support the CNE.
CNA. and CND requirements
needs of its customers
(U) The fact that NSAICSS or UNCLASSIFIED NIA (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. provides CNO- success or capabilities remain
related military tugeting classi?ed.
support
12. (U) The fact that NSAJCSS or UNCLASSIFIED NM NM (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. provides success or capabilities remain
intelligence gainfloss classi?ed.
assessments in response to
Combatant Commander
CNO tam
l3. (U) The fact that NSAICSS or UNCLASSIFIED NIA NIA (U) Details indicating
TAO. as part of CNE
operations. develops and
supports analytic modeling and
simulation techniques to
support CNEJCNA efforts
speci?c targets. level of
success or capabilities remain
classi?ed.
TOP To USA. FVEY
To USA.
- Close access enabling. require protection.
exploitation. or operations
- Off-net enabling. exploitation. (U) Foreign releasability
or operations decisions on speci?c details
- Supply chain enabling. relating to physical
exploitation. or intervention subversion are handled on a
operations case-by-case basis. Contact
- Hardware implant enabling. TAO CAO for further
exploitationI or 9mm gui_da_nce.
S. (U) The association of any UNCLASSIFIEDIIFOR FOIA 3 NIA
speci?c ECI name or trigraph. OFFICIAL USE ONLY
with ECI. SIGINT.
or intelligence
6. (U) The association of a TO Sec. 1.4(c) NIA
speci?c TAO name or USA. FVEY
Mb with CNE ar_idlor TAO
7. (U) The fact that a speci?c UNCLASSIFIEIMFOR (U) If the details of the
individual is cleared for a OFFICIAL USE ONLY association reveal the fact
speci?c TAO ECI. when there that the ECI is TAO's. then it
is no msociation between the would be
BC I and TAO CONFIDENTIAUIREL T0
USA. FVEY. in accordance
with entry 5.
8. (U) The fact that NSAJCSS or UNCLASSIFIED NIA
TAO conducts CNE for foreign
intelligence collection.
9. (U) The fact that NSAJCSS or UNCLASSIFIED NIA (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. performs CN to success or capabilities remain
support US. Government CNA classi?ed.
efforts
IO. (U) The fact that or UNCLASSIFIED NIA (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. trains. equips. and success or capabilities remain
organizes the US. classi?ed.
System to support the CNE.
CNA. and CND requirements
needs of its customers
(U) The fact that NSAICSS or UNCLASSIFIED NIA (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. provides CNO- success or capabilities remain
related military tugeting classi?ed.
support
12. (U) The fact that NSAJCSS or UNCLASSIFIED NM NM (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. provides success or capabilities remain
intelligence gainfloss classi?ed.
assessments in response to
Combatant Commander
CNO tam
l3. (U) The fact that NSAICSS or UNCLASSIFIED NIA NIA (U) Details indicating
TAO. as part of CNE
operations. develops and
supports analytic modeling and
simulation techniques to
support CNEJCNA efforts
speci?c targets. level of
success or capabilities remain
classi?ed.
TOP To USA. FVEY
To USA.
I4. (U) The fact that NSAJCSS or UNCLASSIFIED (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. targets. collects and success or capabilities remain
processes computers. computer classi?ed.
networks and computer-to-
cornputer (C2C)
communications without
reference to a speci?c
operation. activity or target
l5. The fact that NSA TO USA. Sec 1.4(c) ?25 years (U) Details indicating
or TAO. as part of CNE speci?c targets. level of
operations. targets. collects and success or capabilities may
processes specific computer raise the classi?cation level
protocols (such as email. instant to TOP SECRET.
messaging. ?le transfer
protocols) (U) Details may also be
protected by one or more
ECls andlor a different level
of foreign releasability
(including NOPORN).
l6. The fact that T0 USA. See 1.4(c) ?25 years (U) Details indicating
NSAICSS or TAO. as part of speci?c targets. level of
CNE operations. remotely success or capabilities may
introduces code into tuget raise the classification level
computer networks to facilitate to TOP SECRET.
foreign intelligence collection
(U) Details may also be
protected by one or more
andlor a different level
of foreign releasability
(including NOFORN).
l7. The fact that TOP TO Sec 1.4(c) ?25 years (U) Details may also be
NSAICSS or TAO. as part of USA. FVEY protected by one or more
CNE operations. conducts off- ECls andlor a different level
net ?eld operations to develop. of foreign releasability
deploy. exploit. or maintain (including NOFORN).
intrusive access. without further
detail
l8. The fact that TOP Sec 1.4(c) ?25 years (U) Details may also be
NSAICSS or TAO. as part of protected by an
CNE operations. conducts off- See remarks for foreign
net activities at speci?ed releasability. (U) Foreign releasability
locations other than NSAICSS decisions handled on a case-
facilities by-case basis. Contact TAO
CAO for further guidance.
l9. (U) TAO project names. in WIA (3) NIA
association with CNE or TAO. OFFICIAL USE ONLY
with no lif details
20. The fact that CONFIDENTIAUIREL T0 Sec 1.4(c. d) ?25 years (U) Details indicating
NSAICSS or TAO. as part of USA. speci?c targets. level of
CNE operations. collaborates success or capabilities may
with Second Party Partners to raise the classi?cation level.
conduct CNE activities
(U) Details may also be
protected by one or more
To USA.
To USA.
I4. (U) The fact that NSAJCSS or UNCLASSIFIED (U) Details indicating
TAO. as part of CNE speci?c targets. level of
operations. targets. collects and success or capabilities remain
processes computers. computer classi?ed.
networks and computer-to-
cornputer (C2C)
communications without
reference to a speci?c
operation. activity or target
l5. The fact that NSA TO USA. Sec 1.4(c) ?25 years (U) Details indicating
or TAO. as part of CNE speci?c targets. level of
operations. targets. collects and success or capabilities may
processes specific computer raise the classi?cation level
protocols (such as email. instant to TOP SECRET.
messaging. ?le transfer
protocols) (U) Details may also be
protected by one or more
ECls andlor a different level
of foreign releasability
(including NOPORN).
l6. The fact that T0 USA. See 1.4(c) ?25 years (U) Details indicating
NSAICSS or TAO. as part of speci?c targets. level of
CNE operations. remotely success or capabilities may
introduces code into tuget raise the classification level
computer networks to facilitate to TOP SECRET.
foreign intelligence collection
(U) Details may also be
protected by one or more
andlor a different level
of foreign releasability
(including NOFORN).
l7. The fact that TOP TO Sec 1.4(c) ?25 years (U) Details may also be
NSAICSS or TAO. as part of USA. FVEY protected by one or more
CNE operations. conducts off- ECls andlor a different level
net ?eld operations to develop. of foreign releasability
deploy. exploit. or maintain (including NOFORN).
intrusive access. without further
detail
l8. The fact that TOP Sec 1.4(c) ?25 years (U) Details may also be
NSAICSS or TAO. as part of protected by an
CNE operations. conducts off- See remarks for foreign
net activities at speci?ed releasability. (U) Foreign releasability
locations other than NSAICSS decisions handled on a case-
facilities by-case basis. Contact TAO
CAO for further guidance.
l9. (U) TAO project names. in WIA (3) NIA
association with CNE or TAO. OFFICIAL USE ONLY
with no lif details
20. The fact that CONFIDENTIAUIREL T0 Sec 1.4(c. d) ?25 years (U) Details indicating
NSAICSS or TAO. as part of USA. speci?c targets. level of
CNE operations. collaborates success or capabilities may
with Second Party Partners to raise the classi?cation level.
conduct CNE activities
(U) Details may also be
protected by one or more
To USA.
To USA. FVEY
ECls.
21. The fact that TO (U) Foreign releasability
NSAICSS or TAO. as part of USA. decisions handled on a case-
CNE operations. collaborates See remarks for foreign by-case basis. Contact TAO
with speci?c Second Party releasability. CAO for further guidance.
partners on speci?c
22. Details of the CNE SECRETIISI at a minimum (U) Details indicating
collaboration between speci?c targets. level of
or TAO and Second See remarks for foreign success or capabilities may
Party partners releasability. raise the classi?cation level
to TOP
(U) Details may also be
protected by one or more
ECls.
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further guidance.
23. The fact that T0 USA. See 1.4(c.d) ?25 years (U) Details may also be
NSAICSS or TAO. as part of PVEY protected by an Contact
CNE operations. collaborates TAO CAO for further
with unspeci?ed Third Party guidance.
Partners in support and conduct
of Chili activities
24. The fact that TOP Sec 1.4(c. d) ?25 years (U) Foreign releasability
NSAICSS or TAO. as part of decisions handled on a case-
CNE operations. collaboratm See remarks for foreign by-case basis. Contact TAO
with speci?ed Third Party releasability. CAO for further guidance.
Partners in support and conduct
of Chili activities (U) Details may also be
protected by an E131. Contact
TAO CAO for further
guidance.
25. (UIIFOUO) The fact that POIA (3) NIA (U) Details indicating
or TAO. as part of OFFICIAL USE ONLY speci?c targets. level of
CNE operations. collaborates success or capabilities may
with a speci?c US raise the classi?cation level.
GovernmenUIC entity
(U) Details may also be
protected by one or more
ECls a different level
of foreign releasability
(including NOFORN).
26. The fact that TO Sec. l.4(c) ?25 years (U) Details indicating
or TAO. as part of USA. FVEY speci?c targets. level of
CNE operations. collaborates success or capabilities may
with a speci?c US
Government/1C entity on a
speci?c
raise the classi?cation level.
(U) Details may also be
protected by one or more
ECls andfor a different level
of foreign releasability
(including NOFORN).
To USA. FVEY
To USA. FVEY
ECls.
21. The fact that TO (U) Foreign releasability
NSAICSS or TAO. as part of USA. decisions handled on a case-
CNE operations. collaborates See remarks for foreign by-case basis. Contact TAO
with speci?c Second Party releasability. CAO for further guidance.
partners on speci?c
22. Details of the CNE SECRETIISI at a minimum (U) Details indicating
collaboration between speci?c targets. level of
or TAO and Second See remarks for foreign success or capabilities may
Party partners releasability. raise the classi?cation level
to TOP
(U) Details may also be
protected by one or more
ECls.
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further guidance.
23. The fact that T0 USA. See 1.4(c.d) ?25 years (U) Details may also be
NSAICSS or TAO. as part of PVEY protected by an Contact
CNE operations. collaborates TAO CAO for further
with unspeci?ed Third Party guidance.
Partners in support and conduct
of Chili activities
24. The fact that TOP Sec 1.4(c. d) ?25 years (U) Foreign releasability
NSAICSS or TAO. as part of decisions handled on a case-
CNE operations. collaboratm See remarks for foreign by-case basis. Contact TAO
with speci?ed Third Party releasability. CAO for further guidance.
Partners in support and conduct
of Chili activities (U) Details may also be
protected by an E131. Contact
TAO CAO for further
guidance.
25. (UIIFOUO) The fact that POIA (3) NIA (U) Details indicating
or TAO. as part of OFFICIAL USE ONLY speci?c targets. level of
CNE operations. collaborates success or capabilities may
with a speci?c US raise the classi?cation level.
GovernmenUIC entity
(U) Details may also be
protected by one or more
ECls a different level
of foreign releasability
(including NOFORN).
26. The fact that TO Sec. l.4(c) ?25 years (U) Details indicating
or TAO. as part of USA. FVEY speci?c targets. level of
CNE operations. collaborates success or capabilities may
with a speci?c US
Government/1C entity on a
speci?c
raise the classi?cation level.
(U) Details may also be
protected by one or more
ECls andfor a different level
of foreign releasability
(including NOFORN).
To USA. FVEY
TOP To USA. FVEY
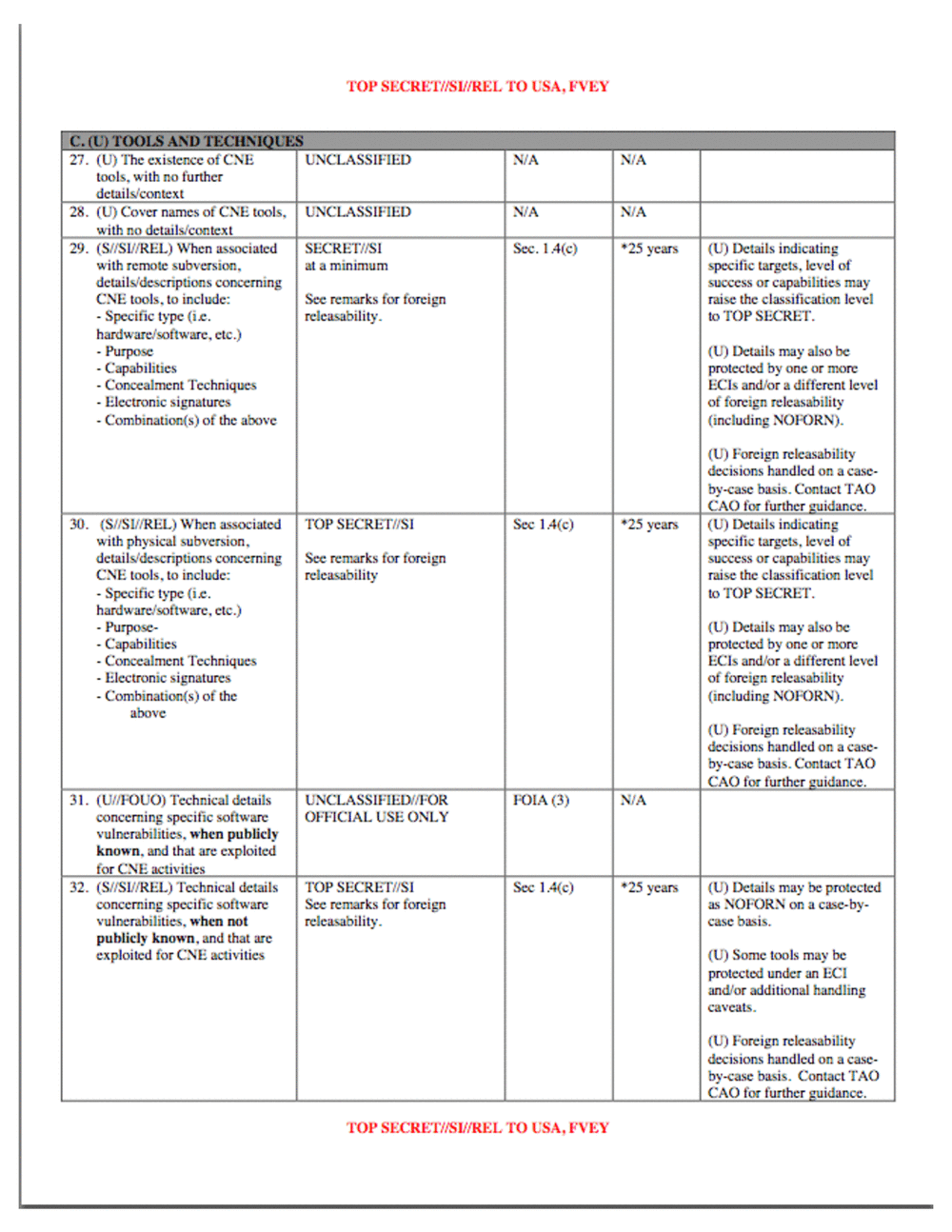
27. (U) The existence of CNE UNCLASSIFIED
tools. with no further
details?cnntext
28. (U) Cover names of CNE tools. UNCLASSIFIED NIA
with no detailsicontext
29. When associated Sec. l.4(c) ?25 years (U) Details indicating
with remote subversion. at a minimum specific targets. level of
details/descriptions concerning success or capabilities may
CNE tools. to include: See remarks for foreign raise the classification level
- Speci?c type (ie. releasability. to TOP SECRET.
hardwarelsoftware. etc.)
- Purpose (U) Details may also be
- Capabilities protected by one or more
- Conualment Techniques ECIs andlor a different level
- Electronic signatures of foreign releasability
- Combination?) of the above (including NOFORN).
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further guiiance.
30. (SIISWREL) When associated TOP Sec 1.4(c) ?25 years (U) Details indicating
with physical subversion. specific targets. level of
details/descriptions concerning See remarks for foreign mess or capabilities may
CNE tools. to include: releasability raise the classi?cation level
- Speci?c type (ie. to TOP SECRET.
hardwarelsoftwarc. etc.)
- Purpose- (U) Details may also be
- Capabilities protected by one or more
- Corncealment Techniques ECls andlor a different level
- Electronic signatures of foreign releasability
- Combination?) of the (including NOFORN).
above
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further ggdance.
31. (UIIFOUO) Technical details UNCLASSIFIEIMFOR FOIA (3)
concerning specific software OFFICIAL USE ONLY
vulnerabilities. when publicly
known. and that are exploited
for (IN gctivities
32. Technical details TOP Sec l.4(c) ?25 years (U) Details maybe protected
concerning specific software See for foreign as NOFORN on a case-by-
vuInerabilities. when not releasability. case basis.
publicly known. and that re
exploited for CNE activities (U) Some tools may be
protected under an
and/or additional handling
caveats.
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further guidance.
TOP TO USA. FVEY
TOP To USA. FVEY
27. (U) The existence of CNE UNCLASSIFIED
tools. with no further
details?cnntext
28. (U) Cover names of CNE tools. UNCLASSIFIED NIA
with no detailsicontext
29. When associated Sec. l.4(c) ?25 years (U) Details indicating
with remote subversion. at a minimum specific targets. level of
details/descriptions concerning success or capabilities may
CNE tools. to include: See remarks for foreign raise the classification level
- Speci?c type (ie. releasability. to TOP SECRET.
hardwarelsoftware. etc.)
- Purpose (U) Details may also be
- Capabilities protected by one or more
- Conualment Techniques ECIs andlor a different level
- Electronic signatures of foreign releasability
- Combination?) of the above (including NOFORN).
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further guiiance.
30. (SIISWREL) When associated TOP Sec 1.4(c) ?25 years (U) Details indicating
with physical subversion. specific targets. level of
details/descriptions concerning See remarks for foreign mess or capabilities may
CNE tools. to include: releasability raise the classi?cation level
- Speci?c type (ie. to TOP SECRET.
hardwarelsoftwarc. etc.)
- Purpose- (U) Details may also be
- Capabilities protected by one or more
- Corncealment Techniques ECls andlor a different level
- Electronic signatures of foreign releasability
- Combination?) of the (including NOFORN).
above
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further ggdance.
31. (UIIFOUO) Technical details UNCLASSIFIEIMFOR FOIA (3)
concerning specific software OFFICIAL USE ONLY
vulnerabilities. when publicly
known. and that are exploited
for (IN gctivities
32. Technical details TOP Sec l.4(c) ?25 years (U) Details maybe protected
concerning specific software See for foreign as NOFORN on a case-by-
vuInerabilities. when not releasability. case basis.
publicly known. and that re
exploited for CNE activities (U) Some tools may be
protected under an
and/or additional handling
caveats.
(U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further guidance.
TOP TO USA. FVEY
TOP To USA.
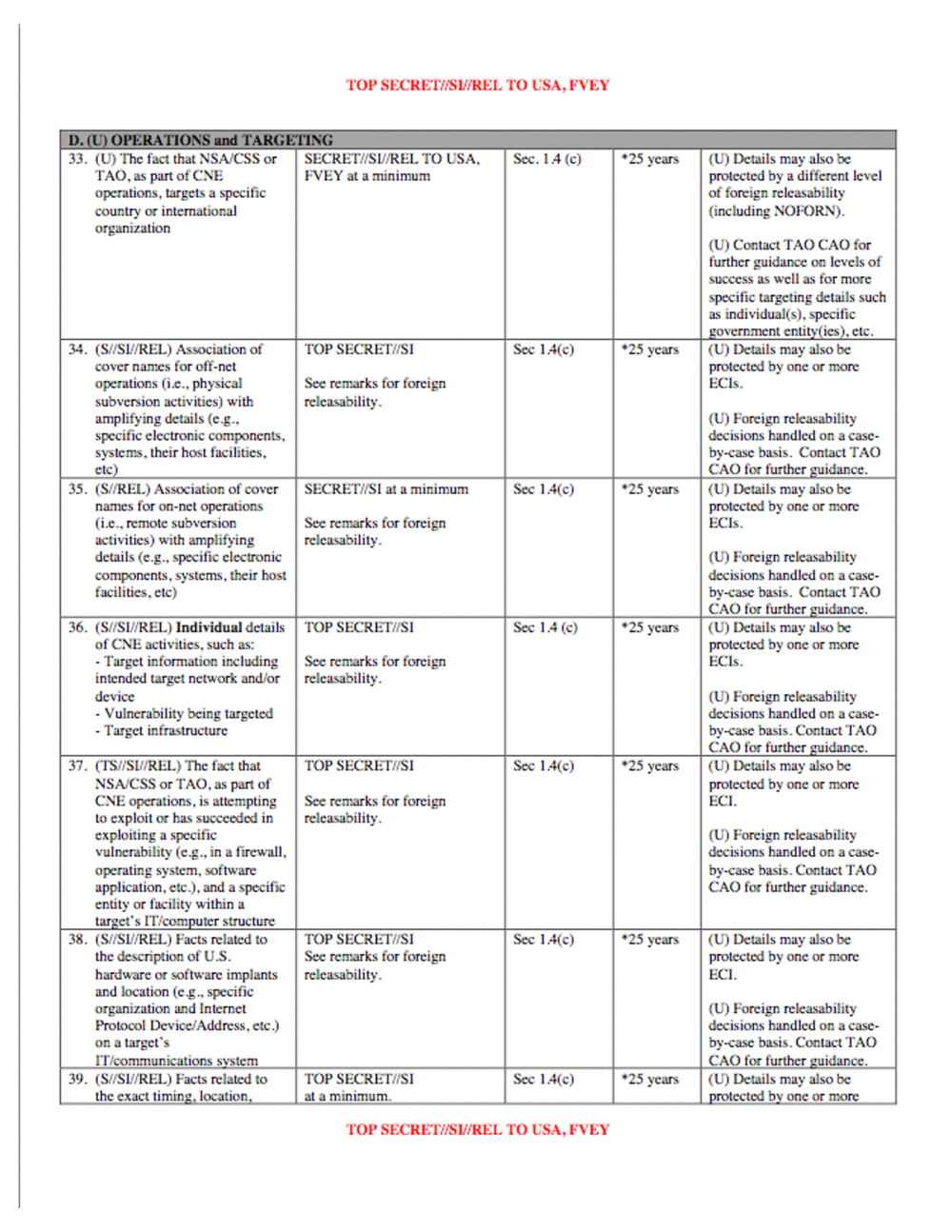
33. (U) The fact that or TO USA. Sec. 1.4 ?25 years (U) Details may also be
TAO. as part of CNE PVEY at a minimum protected by a different level
operations. targets a specific of foreign releasability
country or international (including NOFORN).
organization
(U) Contact TAO CAO for
further guidance on levels of
success as well as for more
speci?c targeting details such
as individual(s). specific
government entity(ics). etc.
34. Association of TOP Sec l.4(c) ?25 years (U) Details may also be
cover names for off-net protected by one or more
operations physical See remarks for foreign ECls.
subversion activities) with releasability.
amplifying details (U) Foreign releasability
speci?c electronic components. decisions handled on a case-
systems. their host facilities. by-case basis. Contact TAO
etc) CAO for further guidance.
35. Association of cover at a minimum Sec l.4(c) ?25 years (U) Details may also be
names for on-net operatiom protected by one or more
remote subversion See remarks for foreign ECls.
activities) with amplifying releasability.
details speci?c electronic (U) Foreign releasability
components. systems. their best decisions handled on a case-
facilities. etc) by-case basis. Contact TAO
CAO for further guidance.
36. Individual details TOP Sec 1.4 ?25 years (U) Details may also be
of CNE such as: protected by one or more
- Target information including See remarks for foreign ECls.
intended target network andlor releasability.
device (U) Foreign releasability
- Vulnerability being targeted decisions handled on a case-
- Target infrastructure by-case basis. Contact TAO
CAO for further guidance.
37. The fact that TOP Sec l.4(c) ?25 years (U) Details may also be
NSAICSS or TAO. as part of protected by one or more
CNE operations. is attempung See remarks for foreign E131.
to exploit or has succeeded in releasability.
exploiting a speci?c (U) Foreign releasability
vulnerability in a fuewall. decisions handled on a case-
operating system. software by-case basis. Contact TAO
application. etc.). and a speci?c CAO for further guidance.
entity or facility within a
target's lT/computer structure
38. l-?acts related to TOP Sec l.4(c) ?25 years (U) Details may also be
the description ofUS. See remarks for foreign protected by oneorrnore
hardware or software implants releasability.
and location (eg. specific
organization and lntemet (U) Foreign releasability
Protocol Des'icelAddress. etc.) decisions handled on a case-
on a target's by-case basis. Contact TAO
lTIeommunications system CAO for further m'dance.
39. Facts related to TOP Sec l.4(c) ?25 years (U) Details may also be
the exact timing, location, at a minimum. protected by one or more
TOP To USA. FVEY
TOP To USA.
33. (U) The fact that or TO USA. Sec. 1.4 ?25 years (U) Details may also be
TAO. as part of CNE PVEY at a minimum protected by a different level
operations. targets a specific of foreign releasability
country or international (including NOFORN).
organization
(U) Contact TAO CAO for
further guidance on levels of
success as well as for more
speci?c targeting details such
as individual(s). specific
government entity(ics). etc.
34. Association of TOP Sec l.4(c) ?25 years (U) Details may also be
cover names for off-net protected by one or more
operations physical See remarks for foreign ECls.
subversion activities) with releasability.
amplifying details (U) Foreign releasability
speci?c electronic components. decisions handled on a case-
systems. their host facilities. by-case basis. Contact TAO
etc) CAO for further guidance.
35. Association of cover at a minimum Sec l.4(c) ?25 years (U) Details may also be
names for on-net operatiom protected by one or more
remote subversion See remarks for foreign ECls.
activities) with amplifying releasability.
details speci?c electronic (U) Foreign releasability
components. systems. their best decisions handled on a case-
facilities. etc) by-case basis. Contact TAO
CAO for further guidance.
36. Individual details TOP Sec 1.4 ?25 years (U) Details may also be
of CNE such as: protected by one or more
- Target information including See remarks for foreign ECls.
intended target network andlor releasability.
device (U) Foreign releasability
- Vulnerability being targeted decisions handled on a case-
- Target infrastructure by-case basis. Contact TAO
CAO for further guidance.
37. The fact that TOP Sec l.4(c) ?25 years (U) Details may also be
NSAICSS or TAO. as part of protected by one or more
CNE operations. is attempung See remarks for foreign E131.
to exploit or has succeeded in releasability.
exploiting a speci?c (U) Foreign releasability
vulnerability in a fuewall. decisions handled on a case-
operating system. software by-case basis. Contact TAO
application. etc.). and a speci?c CAO for further guidance.
entity or facility within a
target's lT/computer structure
38. l-?acts related to TOP Sec l.4(c) ?25 years (U) Details may also be
the description ofUS. See remarks for foreign protected by oneorrnore
hardware or software implants releasability.
and location (eg. specific
organization and lntemet (U) Foreign releasability
Protocol Des'icelAddress. etc.) decisions handled on a case-
on a target's by-case basis. Contact TAO
lTIeommunications system CAO for further m'dance.
39. Facts related to TOP Sec l.4(c) ?25 years (U) Details may also be
the exact timing, location, at a minimum. protected by one or more
TOP To USA. FVEY
TOP USA.
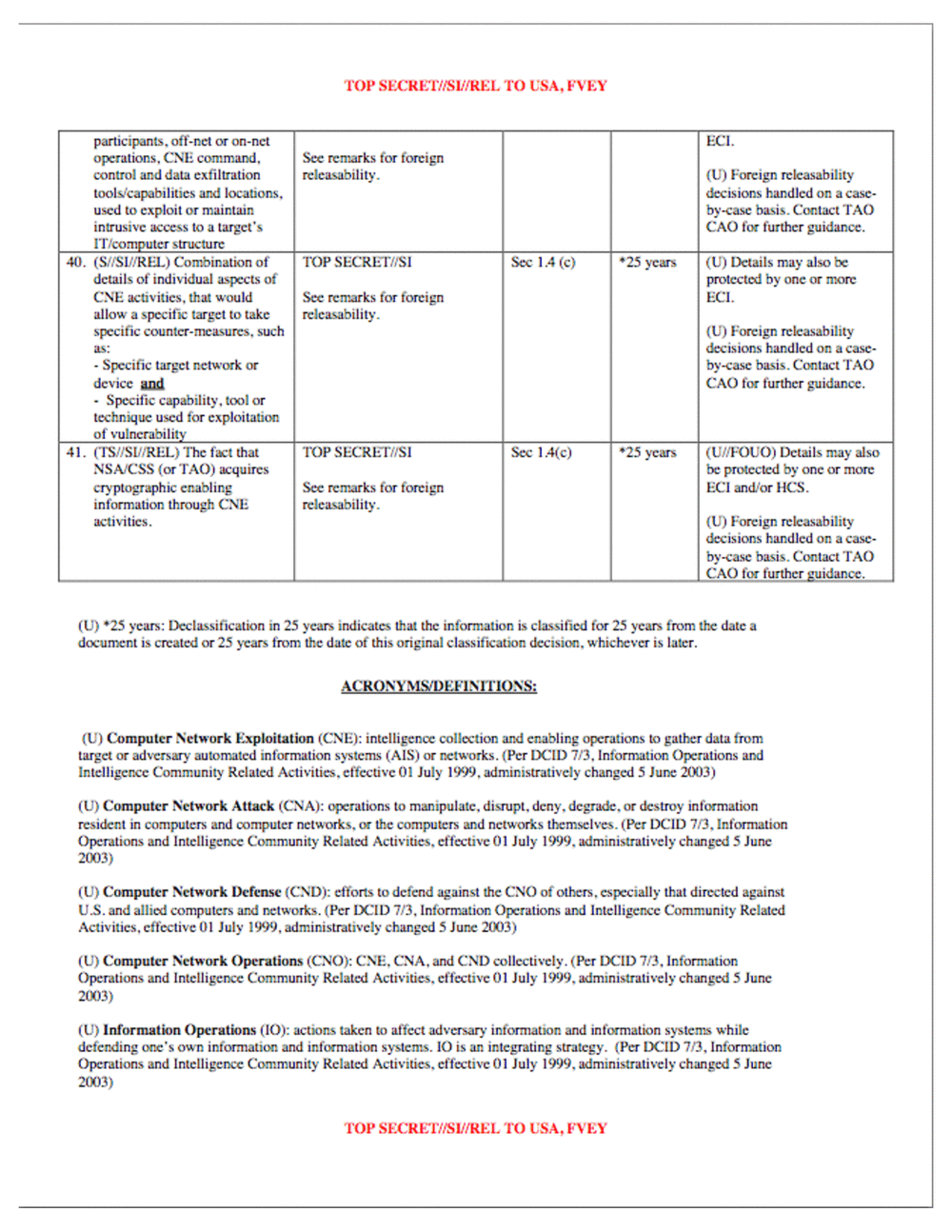
participants. off-net or on-net ECI.
operations. CNE command. See remarks for foreign
control and data exfiltration releasability. (U) Foreign releasability
toolsfcapabilities and locations. decisions handled on a case-
used to exploit or maintain by-case basis. Contact TAO
intrusive access to a target's CAO for further guidance.
lTIoomputer structure
40. Combination of TOP Sec 1.4 ?25 years (U) Details may also be
details of individual aspects of protected by one or more
CNE activities. that would See remarks for foreign
allow a speci?c target to take releasability.
specific counter-measures. such (U) Foreign releasability
as: decisions handled on a case-
- Specific target network or by-case basis. Contact TAO
device CAO for further guidance.
- Specific capability. tool or
technique used for exploitation
of vulnerability
4l. The fact that TOP SBCRETIISI Sec 1.4(c) ?25 years Details may also
(or TAO) acquires be protected by one or more
enabling See for foreign ECI and/or HCS.
information through CNE releasability.
activities. (U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further ggidance.
(U) ?25 years: Declassification in 25 years indicates that the information is classi?ed for 25 years from the date a
document is created or 25 years from the date of this original classification decision. whichever is later.
(U) Computer Network Exploitation (CNE): intelligence collection and enabling operations to gather data from
target or adversary automated information systems (AIS) or networks. (Per DCID 713. Information Operations and
Intelligence Community Related Activities. effective 0 July I999. administratively changed 5 June 21113)
(U) Computer Network Attack (CNA): operations to manipulate. disrupt. deny. degrade. or destroy information
resident in computers and computer networks. or the computers and networks themselves. (Per 78. Information
Operations and Intelligence Community Related Activities. effective 0] July 1999. administratively changed 5 June
2GB)
(U) Computer Network Defense efforts to defend against the CNO of others. especially that directed against
US. and allied computers and networks. (Per Information Operations and Intelligence Community Related
Activities. effective 01 July 1999. administratively changed 5 June 2N3)
(U) Computer Network Operations (CNO): CNE. CNA. and CND collectively. (Per DCID 713. Information
Operations and Intelligence Community Related Activities. effective 01 July 1999. administratively changed 5 June
2M3)
(U) Information Operations (IO): actions taken to affect adversary information and information systems while
defending one?s own infatuation and information systems. 10 is an integrating strategy. (Per 7/3. Information
Operations and Intelligence Community Related Activities. effective 01 July 1999. administratively changed 5 June
2M3)
TOP To USA. FVEY
TOP USA.
participants. off-net or on-net ECI.
operations. CNE command. See remarks for foreign
control and data exfiltration releasability. (U) Foreign releasability
toolsfcapabilities and locations. decisions handled on a case-
used to exploit or maintain by-case basis. Contact TAO
intrusive access to a target's CAO for further guidance.
lTIoomputer structure
40. Combination of TOP Sec 1.4 ?25 years (U) Details may also be
details of individual aspects of protected by one or more
CNE activities. that would See remarks for foreign
allow a speci?c target to take releasability.
specific counter-measures. such (U) Foreign releasability
as: decisions handled on a case-
- Specific target network or by-case basis. Contact TAO
device CAO for further guidance.
- Specific capability. tool or
technique used for exploitation
of vulnerability
4l. The fact that TOP SBCRETIISI Sec 1.4(c) ?25 years Details may also
(or TAO) acquires be protected by one or more
enabling See for foreign ECI and/or HCS.
information through CNE releasability.
activities. (U) Foreign releasability
decisions handled on a case-
by-case basis. Contact TAO
CAO for further ggidance.
(U) ?25 years: Declassification in 25 years indicates that the information is classi?ed for 25 years from the date a
document is created or 25 years from the date of this original classification decision. whichever is later.
(U) Computer Network Exploitation (CNE): intelligence collection and enabling operations to gather data from
target or adversary automated information systems (AIS) or networks. (Per DCID 713. Information Operations and
Intelligence Community Related Activities. effective 0 July I999. administratively changed 5 June 21113)
(U) Computer Network Attack (CNA): operations to manipulate. disrupt. deny. degrade. or destroy information
resident in computers and computer networks. or the computers and networks themselves. (Per 78. Information
Operations and Intelligence Community Related Activities. effective 0] July 1999. administratively changed 5 June
2GB)
(U) Computer Network Defense efforts to defend against the CNO of others. especially that directed against
US. and allied computers and networks. (Per Information Operations and Intelligence Community Related
Activities. effective 01 July 1999. administratively changed 5 June 2N3)
(U) Computer Network Operations (CNO): CNE. CNA. and CND collectively. (Per DCID 713. Information
Operations and Intelligence Community Related Activities. effective 01 July 1999. administratively changed 5 June
2M3)
(U) Information Operations (IO): actions taken to affect adversary information and information systems while
defending one?s own infatuation and information systems. 10 is an integrating strategy. (Per 7/3. Information
Operations and Intelligence Community Related Activities. effective 01 July 1999. administratively changed 5 June
2M3)
TOP To USA. FVEY

TOP To USA. FVEY
Intrusive Access: Refers to CNE operations involving remote manipulation. hardwarelsoftware
modi?cations. or sensing of environment changes in a computer device or system. andfor occasionally the facilities that
house the systems.
Off-Net Operations: Refers to covert or clandestine ?eld activities of personnel carried out in support of
(ENE activities.
Physical subversion: Subverts with physical access to a device or host facility. Other terms sometimes
used to connotc physical subversion are close access enabling. exploitation. or operations; off-net enabling.
exploitation. or operations: supply-chain enabling. exploitation. or operations: or hardware implant enabling.
exploitation. or operations.
Remote subversion: Subverts without physical access to a device or host facility: obtains unauthorized
permission. Other terms sometimes used to connote remote subversion are computer network exploitation: endpoint
access. exploitation. or operations: on-net access. exploitation. or operations: software implant access. exploitation. or
operations: or accessing or exploiting data at rest.
Supply Chin Operatio: lnterdiction activities that focus on modifying equipment in a target?s supply
chain.
TOP To USA. FVEY
TOP To USA. FVEY
Intrusive Access: Refers to CNE operations involving remote manipulation. hardwarelsoftware
modi?cations. or sensing of environment changes in a computer device or system. andfor occasionally the facilities that
house the systems.
Off-Net Operations: Refers to covert or clandestine ?eld activities of personnel carried out in support of
(ENE activities.
Physical subversion: Subverts with physical access to a device or host facility. Other terms sometimes
used to connotc physical subversion are close access enabling. exploitation. or operations; off-net enabling.
exploitation. or operations: supply-chain enabling. exploitation. or operations: or hardware implant enabling.
exploitation. or operations.
Remote subversion: Subverts without physical access to a device or host facility: obtains unauthorized
permission. Other terms sometimes used to connote remote subversion are computer network exploitation: endpoint
access. exploitation. or operations: on-net access. exploitation. or operations: software implant access. exploitation. or
operations: or accessing or exploiting data at rest.
Supply Chin Operatio: lnterdiction activities that focus on modifying equipment in a target?s supply
chain.
TOP To USA. FVEY